Getting Started: Setting Up Your AWS Interface
To begin using the AWS Command Line Interface (CLI), the initial step involves its installation on your local machine. The process varies slightly depending on your operating system. For Windows users, the installation typically involves downloading the MSI installer from the AWS website and following the on-screen instructions. macOS users can leverage the provided package installer or utilize package managers like Homebrew. Similarly, Linux distributions often have the AWS CLI available through their respective package managers, such as `apt` for Debian-based systems or `yum` for Red Hat-based systems. Once installed, the core functionality of the cli aws is enabled. Post-installation, the critical next phase is configuring your AWS credentials, essential for secure access to your AWS resources. This is achieved through the Identity and Access Management (IAM) service within the AWS console. IAM allows for the creation of users, groups, and roles, each with specific permissions. Generating access keys (an access key ID and a secret access key) for an IAM user is vital; these keys are then configured locally using the `aws configure` command. This process securely stores your credentials and enables the cli aws to interact with your AWS environment on your behalf.
Securing your AWS environment through IAM is paramount. Rather than using the root account credentials, which possess unrestricted access, it’s best practice to create dedicated IAM users with specific permissions for each purpose. This practice adheres to the principle of least privilege, limiting the potential damage from compromised credentials. When configuring your AWS credentials with the cli aws, the `aws configure` command will prompt for the Access Key ID, Secret Access Key, the default region name (e.g., us-east-1, eu-west-1) which corresponds to the geographic region where you prefer to create your infrastructure and the default output format (json, text, table). The provided access keys must be handled carefully, avoiding hardcoding them directly into scripts or sharing them insecurely. It’s crucial to store these credentials securely and rotate them regularly, enhancing the security of your cloud infrastructure. Moreover, consider using IAM roles for instances to avoid distributing access keys which is a more secure approach to credential management. Proper configuration of credentials with the AWS CLI empowers developers and operators to interact with AWS services, manage infrastructure, and automate tasks efficiently and safely. Therefore, understanding how to set up the cli aws is a fundamental skill for effectively managing your AWS resources via the command line.
How to Navigate Your AWS Environment with the Command Line
The command line interface (CLI) provides a powerful way to explore and manage your AWS environment. Understanding basic commands is crucial for efficiently interacting with AWS services. To begin, the `aws s3 ls` command is fundamental for listing all S3 buckets associated with your account. This command quickly displays the names of your buckets, providing a starting point for managing your storage. Similarly, to examine your compute resources, the command `aws ec2 describe-instances` will present a detailed list of your EC2 instances, including their instance IDs, types, and current statuses. The `aws ec2 describe-vpcs` command is invaluable for understanding your virtual private cloud (VPC) configurations, listing crucial details about your networking setup. These initial commands are essential building blocks for mastering the AWS CLI, allowing you to quickly discover and understand your existing infrastructure. Exploring these commands will make you more comfortable with how the cli aws operates and how they help you manage resources.
Expanding upon the foundational commands, the CLI allows for more granular exploration and management of AWS services. For example, adding options to the `aws ec2 describe-instances` command, you can filter results to show only running instances by using filters with the `aws ec2 describe-instances –filters “Name=instance-state-name,Values=running”`. Furthermore, you can examine specific aspects of your instances by adding the –query parameter to show just the instance IDs by using `aws ec2 describe-instances –query ‘Reservations[*].Instances[*].InstanceId’ –output text`. Similar customization options are available for other commands, allowing precise control over the information presented. The command `aws ec2 describe-subnets` is used to show all of your available subnets along with their network configurations and availabilities zones, essential to understand where your resources are deployed. Also, the command `aws s3api list-objects –bucket your-bucket-name` can be used to display all the objects within a particular S3 bucket. This level of granularity is a key advantage of using the cli aws, providing flexibility over the web console. Understanding these parameters and exploring other commands in the cli aws will significantly enhance your ability to work with AWS.
Effective use of the AWS CLI often involves combining different commands and understanding their outputs. For instance, listing your S3 buckets using `aws s3 ls` and then detailing a specific bucket’s content with `aws s3 ls s3://your-bucket-name` demonstrates the command hierarchy and how you navigate through your resources. Similarly, examining your VPCs, subnets, and security groups via the `aws ec2` command set provides a deeper understanding of your network topology. This ability to explore, filter, and dissect the complex configurations of your AWS environment through simple and intuitive commands is one of the most practical benefits of the cli aws. Understanding how to combine these cli aws commands efficiently will help you better navigate and understand your AWS environment.
Managing EC2 Instances Using the AWS CLI
The command line interface, or cli aws, provides robust capabilities for managing EC2 instances, offering a level of control and automation that surpasses the AWS Management Console. To launch a new EC2 instance using the cli aws, the `aws ec2 run-instances` command is employed. This command requires several parameters, including the AMI (Amazon Machine Image) ID, which specifies the operating system and pre-installed software. Other vital parameters are the instance type, determining the hardware configuration like CPU and memory, and the security groups, acting as virtual firewalls for your instance. Moreover, a key pair is necessary for secure SSH access to the instance. For example, a typical command might look like `aws ec2 run-instances –image-id ami-xxxxxxxxxxxxxxxxx –instance-type t2.micro –security-group-ids sg-xxxxxxxxxxxxxxxxx –key-name my-keypair`. These initial parameters configure the basic instance; further configuration such as storage, user data, and IAM roles can be specified within the same command or by using additional commands following the launch. Mastering these parameters provides the flexibility to launch a wide variety of instances tailored to specific application needs, which is a primary reason to use the cli aws.
Once instances are running, the aws cli facilitates comprehensive management. The `aws ec2 start-instances` and `aws ec2 stop-instances` commands are used to control the power state of instances, allowing for efficient resource allocation and cost management. The command `aws ec2 describe-instances` can be used to retrieve detailed information about the current status of all instances in a specified region or by filtering the results by instance ID. To terminate instances, the command `aws ec2 terminate-instances` can be used by passing one or more instance IDs; it’s crucial to use this command with care since terminated instances cannot be recovered. Instance lifecycle management through the cli aws is more efficient through automation, making scripting repetitive tasks possible, such as scaling and maintenance. The aws cli allows fine-grained control that the console cannot readily offer, thereby enhancing overall infrastructure management.
The cli aws also enables the user to specify instance profiles for different use cases. For example, an instance profile can give permissions to the ec2 instance to access other aws services without the need to use hardcoded credentials. This is also essential for adhering to security best practices by leveraging instance roles to provide access to various services, like S3, DynamoDB, and others. Further, network configurations, such as placement in specific subnets and the assignment of public or private IP addresses, can be configured through the cli. Such deep configurations through command lines provide a robust method for configuring very complex network setups, where parameters can be changed and applied more precisely. By effectively using the commands and parameters provided by the cli aws, you gain the tools necessary for robust and efficient EC2 instance lifecycle management.
Working with S3 Buckets and Objects via AWS CLI
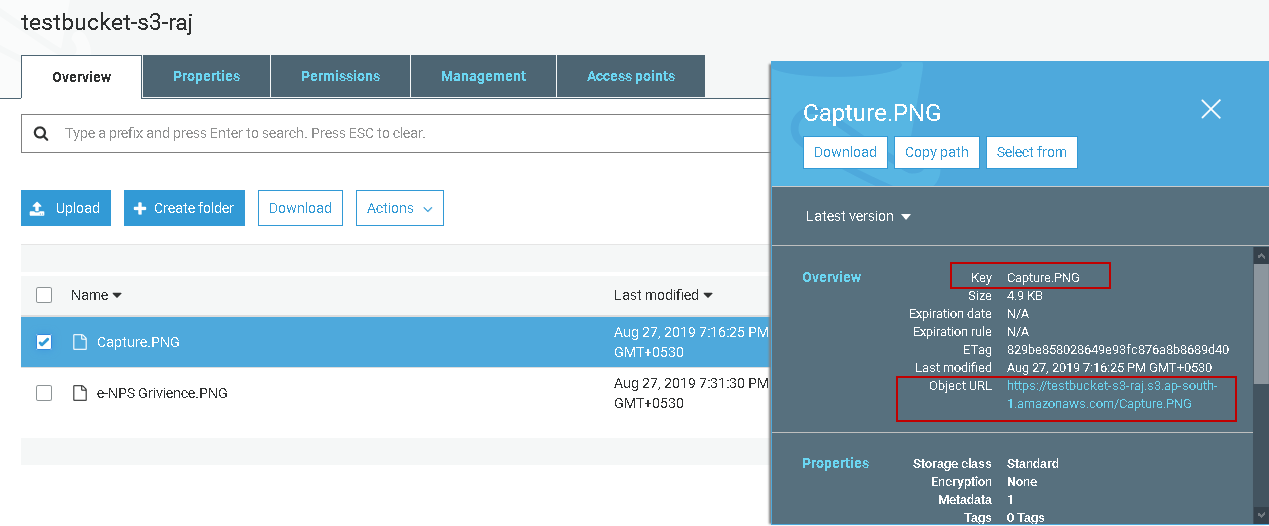
Managing Amazon S3 buckets and objects through the command line interface, or cli aws, offers powerful control over cloud storage. The cli aws enables users to perform a range of operations, starting with bucket management. Creating a new bucket is accomplished using the `aws s3 mb s3://your-bucket-name` command, replacing “your-bucket-name” with the desired name. To delete a bucket, the command `aws s3 rb s3://your-bucket-name` can be used, though the bucket must be empty before removal. Uploading files to S3 is straightforward, for example `aws s3 cp localfile.txt s3://your-bucket-name/`, which copies the local file to the specified bucket. Similarly, downloading is performed with the reverse operation: `aws s3 cp s3://your-bucket-name/file-on-s3.txt localfile.txt`. Managing object permissions via the cli aws involves manipulating access control lists (ACLs) and policies. These can be modified with specific cli aws commands to grant or revoke access to different users or groups. Practical everyday tasks, such as creating backups, are easily handled by scripting these commands. For example, a script can automatically upload database dumps or log files to S3 regularly using `aws s3 cp` in a loop or as part of a scheduled process. The flexibility of the cli aws enhances the ability to integrate backup processes into existing workflows.
The cli aws also allows working with different S3 storage classes, which can optimize costs depending on the frequency of access to data. Options such as Standard, Intelligent-Tiering, Standard-IA, One Zone-IA, Glacier, and Glacier Deep Archive are available. When uploading files, the storage class is specified using the `–storage-class` parameter with the copy command, for instance, `aws s3 cp localfile.txt s3://your-bucket-name/ –storage-class STANDARD_IA`. This capability lets users align their storage infrastructure with specific needs for access frequency and cost. Managing storage classes directly through the cli aws allows for a fine-grained approach to storage management and provides significant cost savings by utilizing the most suitable tier for different data. Furthermore, the cli aws makes it easy to explore the contents of S3 buckets, manage versions, and set up lifecycle policies. The ability to script and automate these actions makes the cli aws a powerful tool for any user of Amazon S3.
Automating Tasks with the AWS Command Line Interface
The true power of the AWS CLI lies in its ability to automate repetitive tasks, significantly enhancing efficiency and reducing the potential for human error. By leveraging scripting languages like bash, python, or PowerShell, users can chain together multiple `cli aws` commands to perform complex operations with a single execution. For instance, consider the process of backing up EC2 instance data to S3. A simple bash script could first create a snapshot of the EC2 volume, then use the `aws s3 cp` command to copy the snapshot data to a designated S3 bucket, and finally, use another command to remove the old snapshots. This level of automation is vital for organizations managing large AWS infrastructures. With the `cli aws`, such scripts can be scheduled to run at regular intervals, ensuring consistent backups without manual intervention. Further, automating tasks is not just about backups; it’s also about managing instances. A script could be written to start all EC2 instances every morning and stop them in the evening, optimizing compute costs without constant monitoring or the use of the console. This is crucial for environments where resource usage fluctuates, showcasing the `cli aws` versatility and its pivotal role in cost management and operational agility. These scripts can also be placed under version control to track changes.
Another crucial area where automation with `cli aws` shines is in deployment pipelines. The `cli aws` facilitates the programmatic creation and management of entire application stacks. By writing scripts that utilize commands to launch EC2 instances, configure load balancers, and set up databases, developers can create complex environments with a single command. This infrastructure-as-code approach not only speeds up deployment but also ensures consistency and repeatability, reducing the risk of configuration drift. Moreover, the `cli aws` allows for the automation of security updates, compliance checks, and log management, crucial components of a robust AWS infrastructure. It’s all about creating automated workflows that enable scaling of operations while maintaining consistency and security. Consider automating the process of patching vulnerable ec2 instances using a scheduled script; this script can check for updates, install patches, and then reboot the instances ensuring the system’s security with no manual interaction. The cli provides a powerful mechanism to create and manage aws resources and to maintain them.
Furthermore, automation with `cli aws` is not just for large enterprises. Small teams can also greatly benefit from automating common tasks. For instance, a user can write a script that checks the status of all their EC2 instances and sends a summary email, or that cleans old logs from s3 storage. It all comes down to identifying repeatable actions, then implementing a script with the appropriate `cli aws` commands to automate them. The key is to develop robust, reusable scripts, which not only save time but also promote consistency and efficiency in AWS management. By automating these routine tasks, users can focus on higher-value activities such as developing new applications, enhancing user experience, and tackling other strategic goals. Therefore, automation with `cli aws` empowers users to manage AWS more efficiently, irrespective of scale or size.
Troubleshooting Common AWS CLI Issues
Encountering issues with the AWS CLI is a common part of the learning process. When working with the cli aws, permissions are a frequent culprit. Errors like “AccessDenied” usually indicate that the IAM user or role you are using does not have the necessary permissions to perform the requested action. Verify the IAM policies attached to the user or role in question. Double-check if the policies allow actions related to the service you are attempting to use and the specific resources involved. Additionally, ensure the correct region is configured, as AWS resources are generally region specific. Errors that indicate a mismatch between the requested region and where the resource is located can be perplexing if overlooked. Command syntax is another common area where users may encounter errors. The cli aws demands very precise syntax, and typos or incorrect argument ordering can lead to command failures. Always double-check the command you’re entering against the official AWS CLI documentation and note the required or optional arguments. If you still have issues, using the ‘–debug’ option in your command will provide very valuable insights by showing detailed information about the command execution and any issues that might be present.
Connectivity problems can also cause failures when working with the cli aws. If the command seems to hang or you are getting timeout errors, you should check if your machine can reach AWS endpoints. Issues with network configurations, firewalls or proxy settings can impact how the cli aws interacts with the remote servers. You can test your connectivity using basic networking tools, such as `ping` or `traceroute`, to determine if the AWS endpoints are reachable. Furthermore, errors may also stem from outdated CLI versions. Keeping your cli aws up to date ensures that you have access to the latest features, bug fixes and support for new services. Periodically updating the CLI using the appropriate installation method for your operating system can reduce issues related to software version compatibility. When faced with an error message, carefully read through it. These messages provide valuable information that guides you toward resolving the issue. If you are unsure about a particular error or command, consulting the comprehensive AWS CLI documentation should be your next step. The documentation offers a wealth of information on each command and its potential issues and usage scenarios, significantly aiding in troubleshooting. Remember that consistent practice with the cli aws and a structured approach to problem solving will make you a more efficient user.
The Benefits of Using the AWS CLI
The command line interface, or CLI aws, offers distinct advantages over the AWS web console, particularly for users seeking efficiency and control over their cloud resources. One of the most significant benefits is the capability for automation. The CLI enables users to script a series of commands, thus automating complex tasks that would otherwise be time-consuming and error-prone if executed manually through the console. This automation potential allows for repeatable and predictable processes, critical for infrastructure management and deployment. Consider, for example, the process of launching multiple EC2 instances with specific configurations: with the web console, this might require navigating through various menus and forms. However, with the CLI aws, a single script can handle this operation, thus reducing human intervention and associated risks, and saving precious time. The flexibility offered by the CLI is also substantial. It provides direct access to a wide range of AWS services and configurations not always easily accessible via the graphical console. This granularity allows for highly customized setups that meet specific technical requirements or operational needs. Furthermore, the CLI is ideal for environments where system administrators need command-line driven tools and workflows.
Another notable advantage of using the CLI aws is its suitability for integration with version control systems. Infrastructure configurations managed through CLI commands can be easily saved as text files and stored in version control repositories like Git. This enables collaborative management and ensures that changes can be tracked, audited, and rolled back if necessary. The web console, on the other hand, doesn’t offer this version control capability. This aspect also enhances auditability, allowing organizations to maintain a history of all infrastructure changes. Furthermore, the speed of execution with the CLI is typically faster than the web console. Since the CLI operates directly on a command line, processing times are reduced significantly, making it a better choice for users working with large datasets or in real-time environments. It eliminates the latency associated with interacting with a web interface, meaning commands are executed more quickly and efficiently. In essence, the CLI aws empowers more advanced and efficient use of AWS services by facilitating automation, granular control, version control, and faster execution speeds, all vital factors for professional and efficient cloud resource management.
Best Practices for Secure AWS CLI Usage
Securing your interactions with the AWS cloud through the command line interface is paramount to preventing unauthorized access and maintaining data integrity. A crucial aspect is avoiding the direct embedding of AWS access keys and secret keys within scripts or configuration files. Instead, employing IAM roles for EC2 instances and other AWS resources is strongly advised. These roles grant temporary permissions to services, eliminating the need for long-lived credentials. This dynamic approach to access control significantly reduces the risk of credentials being compromised. Another layer of security can be added by using Multi-Factor Authentication (MFA) to protect the root user account and any IAM user accounts which possess administrative access. Further, establishing a regular rotation schedule for credentials including access keys is vital to limit the potential damage caused by exposed credentials. Consider using the `aws configure` command responsibly, ensuring that your credentials are securely stored and managed. Proper configuration of the cli aws tool is important for securing cloud assets.
Implementing the principle of least privilege is another foundational security practice within the context of cli aws use. IAM policies should be precisely tailored to grant users and services only the necessary permissions to perform their intended actions. Overly permissive policies, granting wide-ranging access, can create vulnerabilities if compromised. Using IAM Policy Simulator and the AWS CLI itself to validate IAM policies before they are implemented is a critical security safeguard to make sure users and resources only have the needed access. For example, if an application only needs read access to an S3 bucket, it should never be granted broader access to other resources or write access. It’s also beneficial to monitor AWS CloudTrail logs regularly, which track API calls made through the AWS CLI, to detect any suspicious activities.
When working with the cli aws, consider also employing secure configuration practices, such as storing configuration data and credentials using the AWS Systems Manager Parameter Store. This service enables the secure management of secrets, like passwords and API keys, separate from the CLI’s configuration. Encrypting sensitive data when at rest or during transit, and using encrypted storage options for CLI configurations and temporary access keys adds an additional layer of safety. Thoroughly understanding and implementing these security best practices helps to ensure your AWS CLI usage remains secure, reducing the chance of unauthorized access and protecting your AWS infrastructure. By being meticulous about these principles, users are taking the necessary steps in ensuring the security of their data when using the cli aws.