Boomi: An Overview
Dell Boomi is a leading integration platform that empowers businesses to seamlessly connect cloud and on-premises applications, ensuring efficient data exchange and streamlined workflows. Understanding the underlying Boomi architecture is crucial for successful implementation and optimization. This comprehensive guide offers an in-depth look at the key components of Boomi architecture and best practices for designing, managing, and securing integrations.
Key Components of Boomi Architecture
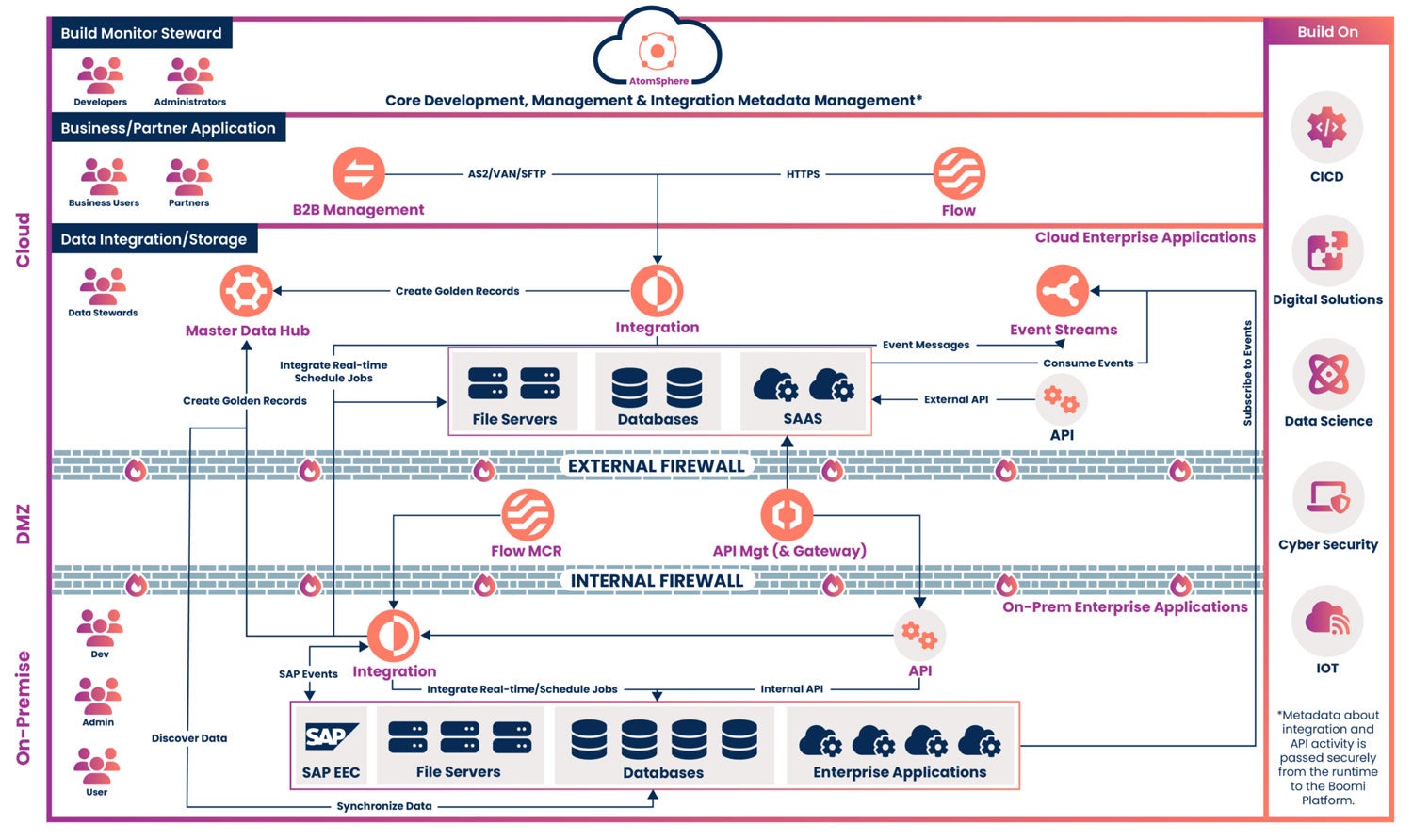
At the heart of Boomi architecture lies a powerful combination of components that work in harmony to provide seamless integration. These components include Atoms, the Boomi Platform, and connectors. Atoms serve as runtime engines for executing processes, while the Boomi Platform offers centralized management and monitoring. Connectors, on the other hand, facilitate secure and efficient communication between applications.
Boomi Atoms: The Backbone of Boomi Architecture
Atoms are the runtime engines of Boomi architecture, responsible for executing processes, data mapping, and transformation. They can be deployed on-premises, in the cloud, or in hybrid environments, providing flexibility for various use cases. Boomi Atoms communicate with the Boomi Platform, which manages and monitors their activities, ensuring seamless integration.
The Boomi Platform: Centralized Management and Monitoring
The Boomi Platform serves as the central nervous system of Boomi architecture, allowing users to design, manage, and monitor integrations with ease. Key features of the Boomi Platform include the process library, configuration management, and analytics. The process library offers a collection of pre-built integration processes, while configuration management enables users to control settings and preferences. Analytics provide valuable insights into integration performance, ensuring optimal efficiency and scalability.
Connectors: Bridging the Gap Between Applications
Connectors play a vital role in Boomi architecture, enabling secure and efficient communication between applications. Boomi offers an extensive library of pre-built connectors for popular enterprise applications, databases, and services. These connectors simplify the integration process, reducing the need for custom development. Additionally, users can create custom connectors for proprietary or specialized applications, ensuring seamless integration across the enterprise.
How to Design an Effective Boomi Architecture
Designing a Boomi architecture tailored to specific business needs is crucial for successful integration. Begin by understanding your enterprise’s unique requirements and mapping out the applications, data sources, and services involved. Next, follow these best practices for process design, data mapping, and testing:
- Process Design: Create well-structured, modular processes with clear entry and exit points. Utilize Boomi’s visual interface to design processes, and ensure they align with your business objectives.
- Data Mapping: Map data fields accurately between applications, considering data types, formats, and any necessary transformations. Boomi’s data mapping tools simplify this process, enabling you to create robust mappings with ease.
- Testing: Thoroughly test your Boomi processes to ensure they function as intended. Utilize Boomi’s testing tools to validate your integrations, and address any issues before deploying to production.
Optimizing Boomi Architecture for Scalability and Performance
Optimizing your Boomi architecture is essential for ensuring scalability and high performance. Consider these topics when fine-tuning your Boomi environment:
- Load Balancing: Distribute workloads evenly across multiple Boomi Atoms to maximize performance and minimize latency. Utilize Boomi’s load balancing capabilities to distribute processes and data efficiently.
- Error Handling: Implement robust error handling mechanisms to minimize disruptions and maintain system stability. Boomi’s visual interface simplifies error handling, enabling you to create custom error handling processes and notifications.
- Logging: Monitor your Boomi processes with detailed logs, providing insights into process execution, data transformations, and error events. Utilize Boomi’s logging capabilities to diagnose and resolve issues quickly.
Security Best Practices in Boomi Architecture
Implementing robust security measures is crucial for protecting sensitive data and maintaining system integrity within your Boomi architecture. Consider these guidelines when designing and managing your Boomi environment:
- Access Control: Implement strict access control policies, ensuring that only authorized users can access Boomi components and data. Utilize Boomi’s role-based access control (RBAC) capabilities to manage user permissions effectively.
- Data Encryption: Encrypt data at rest and in transit to protect sensitive information. Boomi supports various encryption standards, ensuring the secure exchange of data between applications and services.
- Secure Communication: Establish secure communication channels between Boomi components and external systems. Utilize industry-standard protocols such as HTTPS, SFTP, and VPN to ensure secure data transmission.