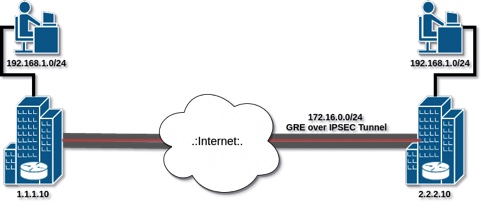
What is BGP over IPsec and Why is it Important?
BGP over IPsec, or Border Gateway Protocol over Internet Protocol Security, is a method of securing network routing by encrypting and authenticating data as it passes between BGP peers. This approach is essential for ensuring secure network communication, protecting sensitive information, and maintaining the integrity of data transfers. With the increasing number of cyber threats and the growing importance of network security, BGP over IPsec has become a critical component of modern network infrastructure. By implementing BGP over IPsec, organizations can protect their networks from unauthorized access, data breaches, and other security threats.
BGP over IPsec combines the power of BGP, which is responsible for routing data between autonomous systems, with the security features of IPsec, which provides encryption, authentication, and key management. This combination ensures that data is transmitted securely and that only authorized parties can access it.
In summary, BGP over IPsec is a powerful and essential technology for securing network routing. With the growing need for secure network communication, BGP over IPsec is a critical component of modern network infrastructure, providing organizations with the protection they need to keep their data safe and secure.
How to Implement BGP over IPsec: A Step-by-Step Guide
Implementing BGP over IPsec can seem like a daunting task, but with the right guidance, it can be a straightforward process. Here’s a step-by-step guide to help you get started:
-
Prerequisites: Before implementing BGP over IPsec, make sure you have the following:
- Two or more BGP-enabled routers
- A valid IPsec certificate and key
- A secure network connection between the routers
-
Configuration: Configure IPsec on both routers using the following steps:
- Generate a new IPsec key pair
- Configure the IPsec transform set
- Configure the IPsec crypto map
- Apply the crypto map to the interface
-
BGP Configuration: Configure BGP on both routers using the following steps:
- Enable BGP on the interface
- Configure the BGP neighbor relationship
- Configure the BGP network statements
- Verify the BGP configuration
-
Testing: Test the BGP over IPsec implementation using the following steps:
- Verify the IPsec connection
- Verify the BGP neighbor relationship
- Verify the BGP routes
By following these steps, you can successfully implement BGP over IPsec in your network. Remember to regularly maintain, monitor, and update your BGP over IPsec implementation to ensure optimal performance and security.
Key Components of BGP over IPsec: Understanding the Technology
BGP over IPsec is a powerful and secure networking solution that combines the best of both BGP and IPsec technologies. To understand how BGP over IPsec works, it’s important to break down its main components:
Encryption
Encryption is the process of converting plain text into a coded format that can only be deciphered by authorized parties. BGP over IPsec uses strong encryption algorithms, such as AES, to protect data as it passes between BGP peers. This ensures that even if data is intercepted, it cannot be read or understood without the proper decryption key.
Authentication
Authentication is the process of verifying the identity of a user or device. BGP over IPsec uses digital certificates and public key infrastructure (PKI) to authenticate BGP peers. This ensures that only authorized parties can establish a BGP session and exchange routing information.
Key Management
Key management is the process of generating, distributing, and managing cryptographic keys. BGP over IPsec uses robust key management protocols, such as IKE and ISAKMP, to securely generate and distribute encryption and authentication keys. This ensures that only authorized parties have access to the keys needed to decrypt and authenticate data.
How These Elements Work Together
By combining encryption, authentication, and key management, BGP over IPsec provides a secure and reliable networking solution. When two BGP peers establish a BGP session, they first authenticate each other using digital certificates. Once authenticated, they generate and exchange encryption and authentication keys using key management protocols. From this point on, all data exchanged between the BGP peers is encrypted and authenticated, ensuring secure network communication.
In conclusion, BGP over IPsec is a powerful and secure networking solution that combines the best of both BGP and IPsec technologies. By understanding its main components, such as encryption, authentication, and key management, network security professionals can effectively implement and maintain BGP over IPsec in their networks.
Real-World Applications of BGP over IPsec: Case Studies and Success Stories
BGP over IPsec is a powerful and secure networking solution that has been successfully implemented by organizations around the world. Here are a few real-world examples of organizations that have used BGP over IPsec to secure their network communication:
Case Study 1: Global Financial Institution
A global financial institution implemented BGP over IPsec to secure their network communication between geographically dispersed data centers. By using BGP over IPsec, the financial institution was able to ensure the confidentiality, integrity, and availability of their network communication. This helped the institution meet regulatory requirements and protect sensitive financial data from unauthorized access.
Case Study 2: Large Service Provider
A large service provider implemented BGP over IPsec to secure their network communication between their customers and their network. By using BGP over IPsec, the service provider was able to provide a secure and reliable networking solution to their customers. This helped the service provider meet customer expectations and differentiate themselves from their competitors.
Case Study 3: Government Agency
A government agency implemented BGP over IPsec to secure their network communication between different government departments. By using BGP over IPsec, the government agency was able to ensure the confidentiality, integrity, and availability of their network communication. This helped the agency meet security requirements and protect sensitive government data from unauthorized access.
These case studies demonstrate the real-world applications and benefits of BGP over IPsec. By implementing BGP over IPsec, organizations can secure their network communication, protect sensitive data, and meet regulatory and security requirements. Whether you’re a global financial institution, a large service provider, or a government agency, BGP over IPsec can provide a powerful and secure networking solution.
BGP over IPsec vs. Other Secure Networking Solutions: A Comparative Analysis
When it comes to secure networking solutions, BGP over IPsec is just one of many options available. Here’s a comparative analysis of BGP over IPsec with other secure networking solutions, such as VPNs and TLS:
BGP over IPsec vs. VPNs
VPNs (Virtual Private Networks) and BGP over IPsec are both secure networking solutions, but they serve different purposes. VPNs are typically used to provide secure remote access to a private network, while BGP over IPsec is used to secure network routing between different networks. BGP over IPsec provides a higher level of security and scalability compared to VPNs, but it can be more complex to implement and manage.
BGP over IPsec vs. TLS
TLS (Transport Layer Security) is a cryptographic protocol used to secure network communication between two endpoints. While TLS provides a high level of security for point-to-point communication, it is not designed to secure network routing between different networks. BGP over IPsec, on the other hand, provides a secure and scalable solution for network routing between different networks, making it a better choice for secure network routing.
When to Use BGP over IPsec vs. Other Solutions
The choice between BGP over IPsec and other secure networking solutions depends on the specific needs and requirements of your network. If you need to secure network routing between different networks, BGP over IPsec is the best choice. If you need to provide secure remote access to a private network, a VPN may be a better option. And if you need to secure point-to-point communication between two endpoints, TLS may be the best choice. It’s important to carefully evaluate your network requirements and choose the solution that best meets your needs.
Best Practices for Secure Network Routing with BGP over IPsec
BGP over IPsec is a powerful and secure networking solution, but it requires careful planning, implementation, and maintenance to ensure optimal performance and security. Here are some best practices for secure network routing with BGP over IPsec:
Regular Maintenance
Regular maintenance is essential for keeping your BGP over IPsec implementation secure and up-to-date. This includes regularly updating your software and firmware, monitoring your network for security threats, and testing your BGP over IPsec implementation to ensure it is working correctly.
Monitoring
Monitoring is critical for detecting and responding to security threats in a timely manner. This includes monitoring your network traffic, monitoring your BGP over IPsec implementation for signs of tampering or misconfiguration, and regularly reviewing your security logs.
Updates
Regular updates are essential for keeping your BGP over IPsec implementation secure and up-to-date. This includes updating your software and firmware, updating your encryption keys, and updating your security policies and procedures.
Troubleshooting Common Issues
Troubleshooting common issues is an important part of maintaining your BGP over IPsec implementation. This includes troubleshooting connectivity issues, troubleshooting performance issues, and troubleshooting security issues. By quickly identifying and resolving common issues, you can ensure optimal performance and security for your BGP over IPsec implementation.
Tips for Ensuring Optimal Performance
Here are some tips for ensuring optimal performance for your BGP over IPsec implementation:
- Use dedicated hardware for your BGP over IPsec implementation
- Use high-performance encryption algorithms
- Use redundant connections for increased availability
- Use load balancing to distribute traffic evenly across multiple connections
- Use traffic shaping to control the flow of traffic and prevent congestion
By following these best practices, you can ensure optimal performance and security for your BGP over IPsec implementation. Whether you’re a network security professional or a business owner, it’s important to take the time to properly implement and maintain your BGP over IPsec implementation to ensure the security and integrity of your network communication.
The Future of BGP over IPsec: Trends and Predictions
BGP over IPsec is a powerful and secure networking solution that has been widely adopted by organizations around the world. As network security threats continue to evolve and become more sophisticated, BGP over IPsec is likely to play an increasingly important role in secure network routing. Here are some trends and predictions for the future of BGP over IPsec:
Increased Adoption of BGP over IPsec
As network security threats continue to evolve, more and more organizations are expected to adopt BGP over IPsec as a secure networking solution. This is because BGP over IPsec provides a high level of security and flexibility, making it an ideal choice for organizations that need to secure their network communication.
Emergence of New Encryption Technologies
As network security threats continue to evolve, new encryption technologies are likely to emerge that will make BGP over IPsec even more secure. This includes the development of new encryption algorithms, new key management technologies, and new authentication methods.
Integration with Cloud and SDN Technologies
BGP over IPsec is expected to become increasingly integrated with cloud and software-defined networking (SDN) technologies. This will allow organizations to secure their network communication in a more flexible and scalable way, making it easier to manage and maintain their BGP over IPsec implementations.
New Challenges and Threats
As BGP over IPsec becomes more widely adopted, new challenges and threats are likely to emerge. This includes the risk of misconfiguration, the risk of insider threats, and the risk of advanced persistent threats (APTs). To address these challenges and threats, organizations will need to implement robust security policies and procedures, and regularly review and update their BGP over IPsec implementations.
The Role of AI and Machine Learning
Artificial intelligence (AI) and machine learning are expected to play an increasingly important role in the future of BGP over IPsec. This includes the use of AI and machine learning to detect and respond to security threats, the use of AI and machine learning to optimize network performance, and the use of AI and machine learning to automate network management and maintenance tasks.
In conclusion, BGP over IPsec is a powerful and secure networking solution that is likely to play an increasingly important role in the future of network security. By staying up-to-date with the latest trends and predictions, network security professionals can ensure that their BGP over IPsec implementations are secure, efficient, and effective. Whether you’re a network security professional or a business owner, it’s important to take the time to understand the future of BGP over IPsec and how it can benefit your organization.
Conclusion: The Importance of Secure Network Routing with BGP over IPsec
In today’s digital age, network security is more important than ever before. With the growing number of cyber threats and attacks, it’s essential for organizations to take a proactive approach to securing their network communication. BGP over IPsec is a powerful and secure networking solution that can help organizations achieve this goal. By implementing BGP over IPsec, organizations can secure their network routing and protect their sensitive data from unauthorized access and theft. BGP over IPsec provides a high level of security and flexibility, making it an ideal choice for organizations of all sizes and industries.
In this comprehensive guide, we have defined BGP over IPsec, its purpose, and the benefits of securing network routing using this approach. We have also provided a detailed, step-by-step guide on implementing BGP over IPsec, including prerequisites, configuration steps, and testing procedures. We have broken down the main components of BGP over IPsec, such as encryption, authentication, and key management, and explained how these elements work together to ensure secure network communication.
We have shared real-world examples of organizations that have successfully implemented BGP over IPsec, discussed the challenges they faced, the solutions they implemented, and the benefits they experienced as a result. We have compared BGP over IPsec with other secure networking solutions, such as VPNs and TLS, discussed the advantages and disadvantages of each approach, and provided guidance on when to use BGP over IPsec versus other solutions.
We have outlined best practices for secure network routing with BGP over IPsec, including regular maintenance, monitoring, and updates, and provided tips for troubleshooting common issues and ensuring optimal performance. We have discussed the future of BGP over IPsec, including emerging trends, new developments, and potential challenges, and provided insights into how this technology is likely to evolve and what that means for network security professionals.
In conclusion, BGP over IPsec is a powerful and secure networking solution that is essential for organizations that need to secure their network communication. By implementing BGP over IPsec, organizations can protect their sensitive data, ensure business continuity, and maintain compliance with industry regulations and standards. We encourage readers to take action and implement this technology in their own networks, and provide resources for further learning and exploration.
Don’t wait until it’s too late – secure your network routing with BGP over IPsec today!