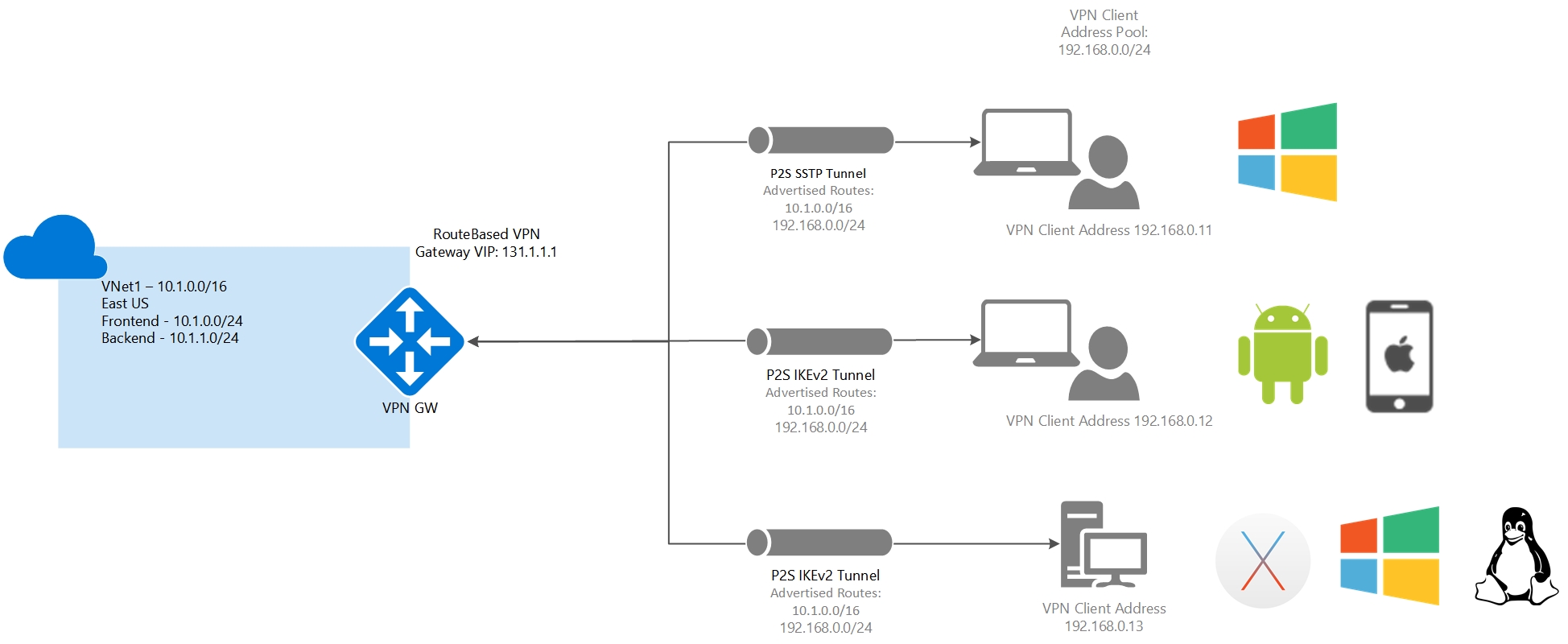
What is Azure VPN Gateway and Terraform?
Azure VPN Gateway is a cloud-based virtual private network (VPN) solution provided by Microsoft Azure. It enables secure and private connections between on-premises networks, virtual networks, and the internet. Azure VPN Gateway supports various VPN technologies, including site-to-site, point-to-site, and multi-site configurations. Terraform, on the other hand, is an open-source infrastructure as code (IaC) software tool developed by HashiCorp. It allows developers and infrastructure teams to define, provision, and manage infrastructure resources using a declarative configuration language. Terraform supports multiple cloud providers, including Azure, AWS, and Google Cloud Platform, and enables users to manage resources across different platforms in a consistent and automated way.
When used together, Azure VPN Gateway and Terraform simplify network infrastructure management by enabling users to define and deploy Azure VPN Gateway resources using Terraform configuration files. This approach offers several benefits, such as version control, modular infrastructure design, and ease of collaboration, which we will discuss in the following sections.
Benefits of Using Terraform for Azure VPN Gateway Deployment
Terraform offers several benefits for deploying and managing Azure VPN Gateway resources. Here are some of the advantages of using Terraform for Azure VPN Gateway deployment: Version Control: Terraform enables users to track changes to their infrastructure resources using version control systems, such as Git. This approach ensures that changes are auditable, traceable, and revertible, which is essential for maintaining infrastructure stability and reliability.
Modular Infrastructure Design: Terraform allows users to define infrastructure resources as modular components, which can be reused and shared across different projects and teams. This approach promotes code reuse, reduces duplication, and simplifies infrastructure management.
Ease of Collaboration: Terraform enables users to collaborate on infrastructure management tasks using shared configuration files and version control systems. This approach promotes collaboration, reduces errors, and ensures that infrastructure changes are consistent and predictable.
Automated Provisioning: Terraform automates the provisioning of Azure VPN Gateway resources, which reduces the time and effort required to deploy and manage infrastructure. This approach enables users to focus on higher-level tasks, such as application development and testing.
Consistency and Predictability: Terraform ensures that infrastructure resources are deployed consistently and predictably, which reduces the risk of errors and inconsistencies. This approach ensures that infrastructure resources are configured correctly, which is essential for maintaining security and compliance.
Infrastructure as Code: Terraform treats infrastructure as code, which enables users to manage infrastructure resources using the same tools and practices used for application development. This approach promotes best practices, such as version control, testing, and continuous integration and delivery (CI/CD), which are essential for modern infrastructure management.
In summary, Terraform offers several benefits for deploying and managing Azure VPN Gateway resources, including version control, modular infrastructure design, ease of collaboration, automated provisioning, consistency and predictability, and infrastructure as code. By using Terraform for Azure VPN Gateway deployment, users can simplify network infrastructure management, reduce errors, and improve infrastructure stability and reliability.
Prerequisites for Setting Up Azure VPN Gateway with Terraform
Before setting up Azure VPN Gateway with Terraform, there are some necessary steps and requirements that you should be aware of. Here are the prerequisites for setting up Azure VPN Gateway with Terraform: Azure Credentials: To set up Azure VPN Gateway with Terraform, you need to have Azure credentials, such as a subscription ID, tenant ID, and client ID. You can obtain these credentials by creating an Azure account or using an existing one. Once you have the credentials, you can store them in a secure location, such as Azure Key Vault or environment variables.
Terraform Installation: To use Terraform for Azure VPN Gateway deployment, you need to install Terraform on your local machine or a remote server. You can download the latest version of Terraform from the official HashiCorp website and follow the installation instructions for your operating system.
Terraform Configuration Files: To define Azure VPN Gateway resources using Terraform, you need to create Terraform configuration files using HashiCorp Configuration Language (HCL). These files define the desired state of the infrastructure resources, such as virtual networks, subnets, and VPN gateways.
Azure Resource Manager (ARM) API Access: To deploy Azure VPN Gateway resources using Terraform, you need to have ARM API access. You can enable ARM API access by creating an Azure service principal and granting it the necessary permissions to manage Azure resources.
Terraform Workspaces: Terraform workspaces enable you to manage multiple environments, such as development, staging, and production, using a single Terraform configuration. You can create Terraform workspaces using the Terraform CLI or Terraform Cloud.
Version Control: To manage changes to Terraform configuration files, you should use a version control system, such as Git. Version control enables you to track changes, collaborate with other team members, and revert to previous versions if necessary.
Testing: To ensure that Terraform configuration files are correct and free of errors, you should test them using tools, such as Terratest or kitchen-terraform. Testing enables you to catch errors early in the development process and ensure that infrastructure resources are deployed correctly.
In summary, to set up Azure VPN Gateway with Terraform, you need to have Azure credentials, install Terraform, create Terraform configuration files, enable ARM API access, create Terraform workspaces, use version control, and test your Terraform configuration files. By following these prerequisites, you can ensure that your Azure VPN Gateway deployment is successful and meets your infrastructure requirements.
How to Create an Azure VPN Gateway with Terraform
To create an Azure VPN Gateway using Terraform, you need to follow these steps: Step 1: Create a Terraform Configuration File
The first step is to create a Terraform configuration file that defines the desired state of the Azure VPN Gateway resources. Here is an example configuration file that creates a virtual network, subnet, and VPN gateway:
python
provider “azurerm” {
features {}
}
resource “azurerm_resource_group” “example” {
name = “example-resources”
location = “West Europe”
}
resource “azurerm_virtual_network” “example” {
name = “example-network”
resource_group_name = azurerm_resource_group.example.name
location = azurerm_resource_group.example.location
address_space = [“10.0.0.0/16”]
}
resource “az
Best Practices for Managing Azure VPN Gateway with Terraform
To get the most out of Terraform for managing your Azure VPN Gateway, here are some best practices to follow: Use Terraform Workspaces
Terraform workspaces allow you to manage multiple environments, such as development, staging, and production, using a single Terraform configuration. By using workspaces, you can keep your infrastructure resources organized, separate, and easy to manage.
Use Version Control
Version control is essential for managing changes to your Terraform configuration files. By using version control, you can track changes, collaborate with other team members, and revert to previous versions if necessary. Git is a popular version control system that integrates well with Terraform.
Test Your Terraform Configuration
Testing your Terraform configuration is essential for catching errors and ensuring that your infrastructure resources are deployed correctly. You can use tools, such as Terratest or kitchen-terraform, to test your Terraform configuration files.
Use Modular Infrastructure Design
Modular infrastructure design enables you to break down your infrastructure resources into smaller, reusable components. By using modular infrastructure design, you can simplify your Terraform configuration, reduce duplication, and promote code reuse.
Use Azure Policy
Azure Policy enables you to define and enforce policies for your Azure resources. By using Azure Policy, you can ensure that your Azure VPN Gateway resources comply with your organization’s policies and standards.
Use Azure Monitor and Azure Log Analytics
Azure Monitor and Azure Log Analytics enable you to monitor and analyze the performance and health of your Azure VPN Gateway resources. By using Azure Monitor and Azure Log Analytics, you can identify and troubleshoot issues, optimize performance, and ensure that your Azure VPN Gateway resources are available and secure.
In summary, to manage Azure VPN Gateway with Terraform, you should use Terraform workspaces, version control, testing, modular infrastructure design, Azure Policy, and Azure Monitor and Azure Log Analytics. By following these best practices, you can ensure that your Azure VPN Gateway deployment is successful, secure, and meets your organization’s requirements.
Troubleshooting Common Issues with Azure VPN Gateway and Terraform
When deploying and managing Azure VPN Gateway with Terraform, you may encounter some common issues. Here are some solutions for resolving these issues: Error: Authentication failed
If you encounter an authentication failed error when running Terraform, it may be due to incorrect Azure credentials. To resolve this issue, ensure that you have the correct Azure subscription ID, tenant ID, and client ID. You can also try regenerating the Azure client secret and updating your Terraform configuration file.
Error: Resource group not found
If you encounter a resource group not found error when running Terraform, it may be due to the resource group not existing in your Azure subscription. To resolve this issue, ensure that the resource group exists and that you have the necessary permissions to access it.
Error: Conflicting configurations
If you encounter a conflicting configurations error when running Terraform, it may be due to changes in your Azure VPN Gateway resources that conflict with your Terraform configuration. To resolve this issue, ensure that your Terraform configuration is up-to-date and reflects the current state of your Azure VPN Gateway resources.
Error: Timeout waiting for the resource group to be created
If you encounter a timeout waiting for the resource group to be created error when running Terraform, it may be due to network connectivity issues or Azure service availability. To resolve this issue, ensure that you have a stable network connection and that Azure services are available in your region.
Error: VPN Gateway already exists
If you encounter a VPN Gateway already exists error when running Terraform, it may be due to the VPN Gateway already existing in your Azure subscription. To resolve this issue, ensure that you are using a unique VPN Gateway name or delete the existing VPN Gateway before running Terraform.
Error: Unsupported API version
If you encounter an unsupported API version error when running Terraform, it may be due to an outdated version of the Azure provider. To resolve this issue, ensure that you are using the latest version of the Azure provider and that your Terraform configuration is up-to-date.
In summary, when deploying and managing Azure VPN Gateway with Terraform, you may encounter common issues, such as authentication failed, resource group not found, conflicting configurations, timeout waiting for the resource group to be created, VPN Gateway already exists, and unsupported API version. By following these solutions, you can resolve these issues and ensure a successful Azure VPN Gateway deployment with Terraform.
Comparing Terraform with Other Infrastructure as Code Tools for Azure VPN Gateway
When it comes to deploying and managing Azure VPN Gateway, there are several infrastructure as code tools available, including Terraform, Azure Resource Manager (ARM) templates, and PowerShell. Here’s a comparison of these tools and their pros and cons: Terraform
Terraform is an open-source infrastructure as code software tool that enables you to define and provide data center infrastructure using a declarative configuration language. Here are some pros and cons of using Terraform for Azure VPN Gateway:
Pros:
- Version control: Terraform enables you to keep track of changes to your infrastructure and roll back to previous versions if necessary.
- Modular infrastructure design: Terraform allows you to break down your infrastructure into smaller, reusable modules, making it easier to manage and maintain.
- Ease of collaboration: Terraform enables multiple team members to collaborate on infrastructure management, reducing errors and improving efficiency.
Cons:
- Learning curve: Terraform has a steeper learning curve compared to other infrastructure as code tools, requiring more time and effort to learn and master.
- Complexity: Terraform can be more complex to set up and configure compared to other infrastructure as code tools, especially for large-scale deployments.
Azure Resource Manager (ARM) Templates
Azure Resource Manager (ARM) templates are JSON files that define the resources you need to deploy for your solution. Here are some pros and cons of using ARM templates for Azure VPN Gateway:
Pros:
- Integration: ARM templates are natively integrated with Azure, making it easier to deploy and manage Azure resources.
- Simplicity: ARM templates are simpler to set up and configure compared to Terraform, especially for small-scale deployments.
Cons:
- Limited version control: ARM templates do not have built-in version control, making it harder to keep track of changes to your infrastructure.
- Limited modular infrastructure design: ARM templates do not support modular infrastructure design as well as Terraform, making it harder to manage and maintain large-scale deployments.
PowerShell
PowerShell is a command-line shell and scripting language built on the .NET Framework. Here are some pros and cons of using PowerShell for Azure VPN Gateway:
Pros:
- Integration: PowerShell is natively integrated with Azure, making it easier to deploy and manage Azure resources.
- Flexibility: PowerShell is a powerful scripting language, enabling you to automate complex tasks and workflows.
Cons:
- Complexity: PowerShell can be complex to learn and master, requiring more time and effort compared to other infrastructure as code tools.
- Limited version control: PowerShell does not have built-in version control, making it harder to keep track of changes to your infrastructure.
In summary, when it comes to deploying and managing Azure VPN Gateway, Terraform, ARM templates, and PowerShell are all viable options. Terraform offers version control, modular infrastructure design, and ease of collaboration, while ARM templates and PowerShell offer integration and simplicity. Ultimately, the choice of tool depends on your specific needs and requirements.
Future Trends and Developments for Azure VPN Gateway and Terraform
As cloud-based virtual private network solutions continue to evolve, so too will the tools and technologies used to manage and deploy them. Here are some future trends and developments to look out for when it comes to Azure VPN Gateway and Terraform: Improved Integration
One of the most significant trends in infrastructure as code is improved integration between tools and platforms. As Azure VPN Gateway and Terraform continue to mature, we can expect to see better integration between the two, making it easier to deploy and manage Azure VPN Gateway resources using Terraform.
New Features
Both Azure VPN Gateway and Terraform are regularly updated with new features and capabilities. For example, Azure VPN Gateway recently added support for Azure Private Link, enabling customers to access Azure VPN Gateway resources over a private network. Similarly, Terraform is regularly updated with new providers and resources, making it easier to manage a wider range of infrastructure components.
Community Support
As the use of infrastructure as code continues to grow, so too does the community of users and developers. This community plays a critical role in driving innovation and development, with many contributors creating and sharing new modules, providers, and resources. As the community around Azure VPN Gateway and Terraform continues to grow, we can expect to see more innovation and development in this space.
Conclusion
Azure VPN Gateway and Terraform are powerful tools for managing and deploying cloud-based virtual private network solutions. By using Terraform to manage Azure VPN Gateway resources, organizations can take advantage of version control, modular infrastructure design, and ease of collaboration, making it easier to manage and maintain their network infrastructure. As the use of infrastructure as code continues to grow, we can expect to see improved integration, new features, and continued community support for Azure VPN Gateway and Terraform.
About the Author
This article was written by [Your Name], a [Your Title] at [Your Company]. [Your Bio].