Understanding Azure Security: An Overview
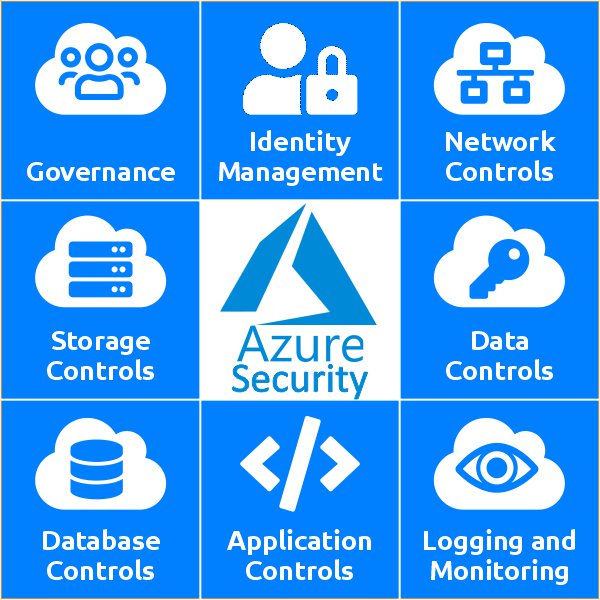
Azure security is a critical aspect of managing cloud-based workloads and applications in Microsoft’s Azure environment. With the increasing adoption of cloud services, ensuring robust security measures has become paramount for organizations to protect sensitive data and maintain regulatory compliance. This article will explore various strategies and best practices for strengthening Azure security, covering essential topics such as identity and access management, network security, data protection, threat detection, and compliance.
Implementing Strong Identity and Access Management
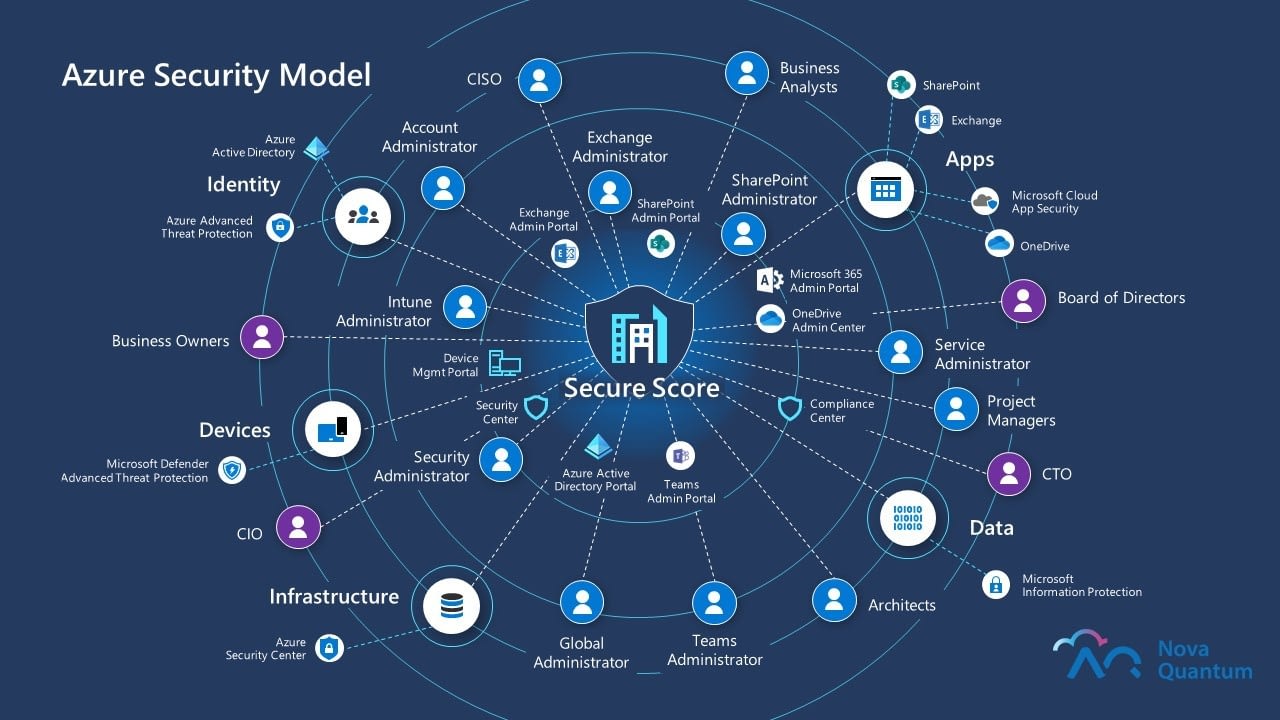
Identity and access management (IAM) is a fundamental aspect of Azure security, ensuring that only authorized users and applications can access resources. Properly configuring user access, multi-factor authentication, and role-based access control (RBAC) is essential to maintaining a secure environment. Azure provides several services to help manage IAM, including Azure Active Directory (Azure AD) and Conditional Access.
Azure AD is a cloud-based identity and access management service that offers centralized authentication and authorization for applications. By integrating Azure AD with your on-premises Active Directory, you can create a seamless experience for users accessing both cloud and on-premises resources. Azure AD also supports multi-factor authentication, which adds an additional layer of security by requiring users to provide at least two forms of identification before accessing resources.
RBAC is a method of controlling access to Azure resources based on specific roles. By assigning users to predefined roles, such as Owner, Contributor, or Reader, you can ensure that they only have the permissions necessary to perform their job functions. Additionally, you can create custom roles tailored to your organization’s unique requirements. Conditional Access, another Azure security feature, allows you to define access control policies based on conditions such as user location, device compliance, and application sensitivity. By combining RBAC and Conditional Access, you can create a robust IAM strategy that minimizes the risk of unauthorized access.
Securing Network Connections in Azure
Network security is a critical aspect of Azure security, ensuring that only authorized users and applications can access your resources. Azure provides several services to help secure network connections, including virtual networks, network security groups, and Azure Firewall. Additionally, configuring secure connections between on-premises networks and Azure, as well as encryption options for data in transit, is essential to maintaining a secure environment.
Virtual networks (VNets) allow you to create isolated network environments in Azure, enabling secure communication between Azure resources and on-premises networks. By configuring network security groups (NSGs), you can apply rules to control inbound and outbound traffic to resources within a VNet. Azure Firewall, a fully managed network security service, provides additional protection by inspecting and logging traffic, as well as enabling secure connections between on-premises networks and Azure using site-to-site VPN or ExpressRoute.
When configuring network security, it is essential to consider encryption options for data in transit. Azure provides several encryption options, including Azure ExpressRoute encryption, Virtual Network (VNet) encryption, and Secure Sockets Layer (SSL) and Transport Layer Security (TLS) encryption for data in transit between applications and resources. By implementing these encryption options, you can ensure that data remains secure while in transit, minimizing the risk of unauthorized access or data breaches.
Protecting Data and Applications with Azure Security Center
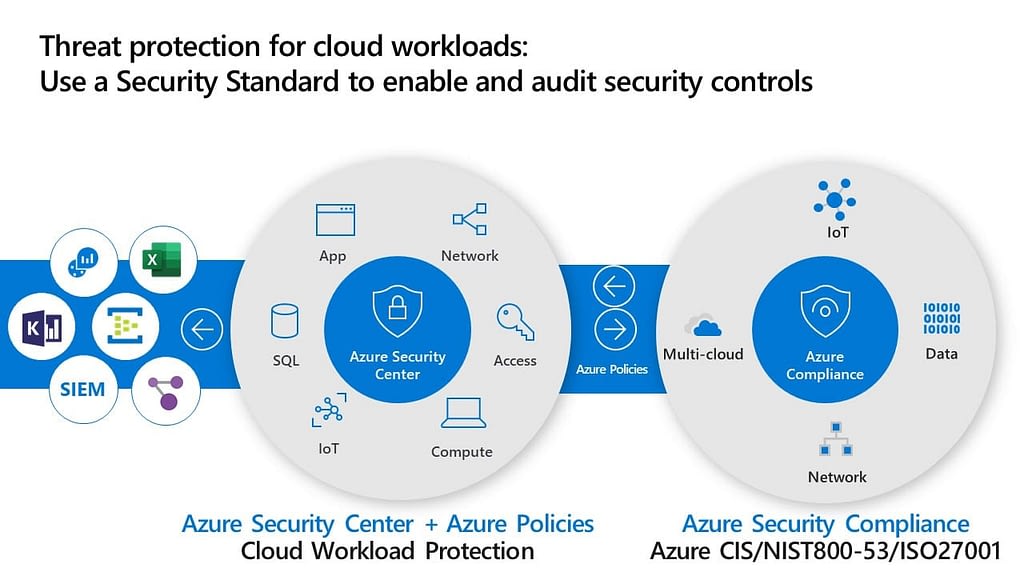
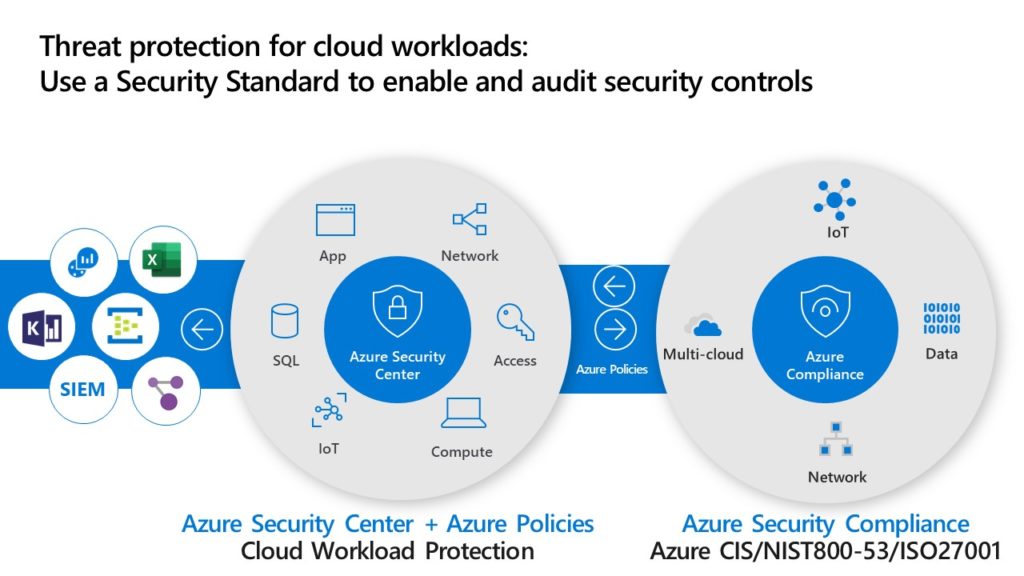
Azure Security Center is a unified security management and threat protection service that helps identify and remediate security vulnerabilities in workloads running in Azure, on-premises, and in other clouds. By providing continuous assessment, security recommendations, and threat protection, Azure Security Center enables organizations to strengthen their Azure security posture and protect their data and applications.
Azure Security Center offers several features to help protect your workloads, including adaptive application controls, just-in-time VM access, and SQL vulnerability assessment. Adaptive application controls allow you to define a list of trusted applications for your virtual machines, reducing the risk of unauthorized access and malware. Just-in-time VM access enables you to restrict inbound traffic to virtual machines, minimizing the attack surface and reducing the risk of unauthorized access. SQL vulnerability assessment helps you identify and remediate vulnerabilities in your SQL databases, ensuring that your data remains secure.
Azure Security Center also provides security analytics and threat intelligence, enabling you to detect and respond to threats quickly. By integrating with Azure Monitor, Azure Security Center provides a centralized view of your security posture, enabling you to monitor and manage security across your Azure, on-premises, and multi-cloud environments. Additionally, Azure Security Center integrates with third-party security information and event management (SIEM) systems, enabling you to leverage existing investments in security tools and processes.
How to Monitor and Respond to Security Threats in Azure
Monitoring and responding to security threats is a critical aspect of maintaining a secure environment in Azure. Azure provides several capabilities to help you monitor and respond to security threats, including Azure Monitor, Azure Log Analytics, and Azure Security Center’s threat protection. By setting up alerts, creating custom dashboards, and investigating security incidents, you can proactively identify and address security threats in your Azure environment.
Azure Monitor is a centralized monitoring service that provides a comprehensive view of your Azure resources. By integrating with Azure Log Analytics, Azure Monitor enables you to collect and analyze log data from your Azure resources, applications, and services. With Azure Monitor, you can create custom dashboards, alerts, and visualizations to monitor the health and performance of your Azure resources, as well as detect and respond to security threats.
Azure Security Center’s threat protection provides additional capabilities to help you monitor and respond to security threats. By continuously assessing your Azure resources, Azure Security Center can identify security vulnerabilities and provide recommendations to strengthen your security posture. Additionally, Azure Security Center can detect and respond to threats in real-time, providing you with actionable insights and recommendations to remediate security incidents.
To effectively monitor and respond to security threats in Azure, it is essential to integrate your Azure security solutions with third-party security information and event management (SIEM) systems. By integrating with SIEM systems, you can leverage existing investments in security tools and processes, enabling you to monitor and manage security across your Azure, on-premises, and multi-cloud environments.
Compliance and Regulatory Considerations in Azure
Compliance and regulatory considerations are critical aspects of Azure security. Azure provides several built-in compliance solutions, such as Azure Policy and Azure Security Center’s regulatory compliance dashboard, to help organizations meet specific compliance standards, such as GDPR, HIPAA, and PCI DSS. By using these solutions, organizations can ensure that their Azure workloads comply with relevant regulations and standards, reducing the risk of non-compliance penalties and reputational damage.
Azure Policy is a service that enables organizations to define and enforce consistent policies across their Azure resources. By using Azure Policy, organizations can ensure that their Azure resources comply with specific regulations and standards, such as GDPR, HIPAA, and PCI DSS. Azure Policy provides several built-in policies that organizations can use to enforce compliance, as well as the ability to create custom policies tailored to their specific requirements.
Azure Security Center’s regulatory compliance dashboard provides a centralized view of an organization’s compliance posture across their Azure workloads. By using the regulatory compliance dashboard, organizations can quickly identify compliance gaps and take action to remediate them. The regulatory compliance dashboard supports several compliance standards, including GDPR, HIPAA, and PCI DSS, and provides detailed guidance on how to achieve compliance with each standard.
In addition to Azure Policy and Azure Security Center’s regulatory compliance dashboard, Azure provides several other compliance solutions, such as Azure Secure Score, Azure Advisor, and Azure Monitor for containers. By using these solutions, organizations can gain a comprehensive view of their Azure security posture and take action to remediate compliance gaps and security vulnerabilities.
Securing Azure Virtual Machines and Containers
Securing Azure Virtual Machines (VMs) and containers is a critical aspect of Azure security. By following best practices for configuring network security, access control, and patch management, organizations can ensure that their Azure VMs and containers are secure and protected from potential threats.
Azure Security Center provides several features to help organizations secure their Azure VMs and containers. Adaptive application controls enable organizations to restrict which applications are allowed to run on their VMs, reducing the risk of unauthorized access and malware. Just-in-time VM access limits inbound traffic to VMs, minimizing the attack surface and reducing the risk of unauthorized access. SQL vulnerability assessment helps organizations identify and remediate vulnerabilities in their SQL databases, ensuring that their data remains secure.
Azure Monitor for containers provides monitoring and logging capabilities for container workloads running in Azure. By using Azure Monitor for containers, organizations can gain visibility into the performance and health of their container workloads, as well as detect and respond to security threats. Azure Policy for container security enables organizations to define and enforce consistent policies across their container workloads, ensuring that they comply with specific regulations and standards.
In addition to using Azure Security Center and Azure Monitor for containers, organizations should follow best practices for configuring network security, access control, and patch management for their Azure VMs and containers. This includes configuring network security groups to restrict inbound and outbound traffic, using role-based access control (RBAC) to control access to resources, and implementing patch management policies to ensure that VMs and containers are up-to-date with the latest security patches and updates.
Emerging Trends and Future Developments in Azure Security
As cyber threats continue to evolve and become more sophisticated, Azure security is also advancing to meet these challenges. In this section, we will discuss some of the emerging trends and future developments in Azure security, including artificial intelligence, machine learning, and zero trust security models.
Artificial intelligence (AI) and machine learning (ML) are being increasingly used in Azure security to detect and respond to threats more quickly and accurately. Azure Security Center uses AI and ML to analyze large volumes of data and identify potential security threats, enabling organizations to respond to incidents more quickly and effectively. Additionally, Azure Sentinel, a cloud-native SIEM and SOAR solution, uses AI and ML to correlate data from multiple sources and detect threats that might otherwise go unnoticed.
Zero trust security models are also becoming more important in Azure security. A zero trust security model assumes that all traffic is untrusted and requires verification before granting access to resources. Azure Active Directory (AAD) and Conditional Access are key components of Azure’s zero trust security model, enabling organizations to control access to resources based on user identity, location, and device.
To stay up-to-date with the latest Azure security features and best practices, organizations should regularly review Azure security documentation and resources, attend Azure security events and webinars, and engage with the Azure security community. By staying informed and adopting the latest Azure security features and best practices, organizations can ensure that their Azure workloads are secure and protected from potential threats.