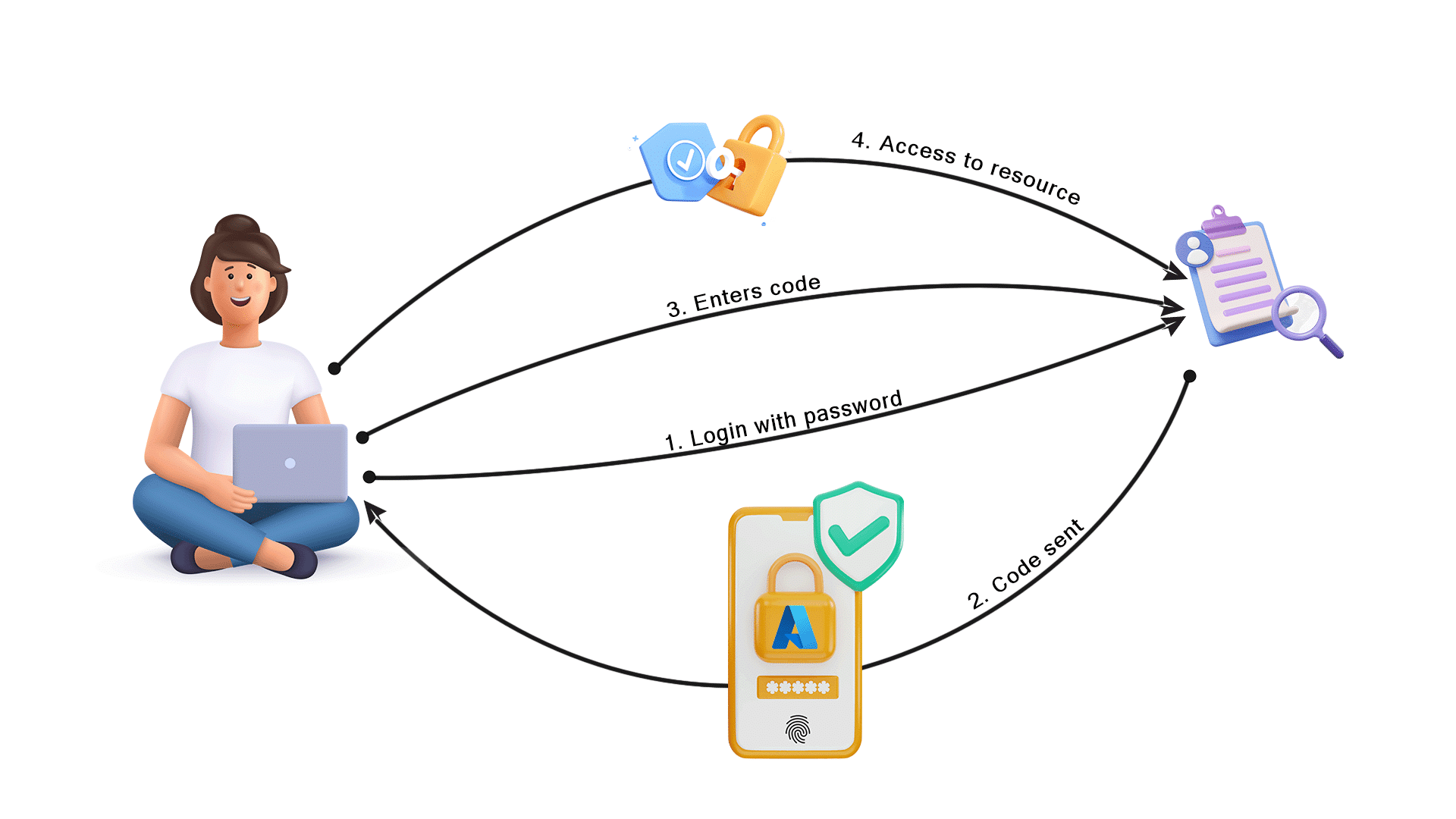
Overview of Azure Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a crucial security measure within Azure. It significantly enhances the security posture of Azure resources by requiring multiple verification steps beyond a simple password. Implementing MFA adds an extra layer of protection, making unauthorized access considerably more difficult. Azure offers a variety of MFA options, providing flexibility to organizations in aligning security needs with specific use cases. Understanding the core principles of MFA, alongside the available azure mfa options, is vital for securing your Azure environment.
This multi-layered approach to authentication is becoming increasingly important in today’s threat landscape. The core principle of MFA revolves around requiring more than one factor to verify a user’s identity. This is often a combination of something you know (password), something you have (a phone, authenticator app), and something you are (biometrics, if applicable). Implementing MFA for your Azure environment is a proactive measure to protect against unauthorized access and potential data breaches. Choosing appropriate azure mfa options directly correlates with the level of security an organization needs to maintain.
Effective security relies on the selection of suitable azure mfa options tailored to specific security and scalability needs. Understanding the trade-offs in ease of use, reliability, and security is critical. A comprehensive security strategy must incorporate various factors, including the specific vulnerabilities an organization might face, the sensitive data they handle, and regulatory compliance requirements. Choosing the right azure mfa options is crucial for successful implementation.
Comparing Azure MFA Options for Security and Scalability
Azure MFA offers a range of authentication methods, each with its own set of strengths and weaknesses. Understanding these differences is crucial for selecting the optimal approach for your specific needs. Different security and scalability requirements dictate the choice of method. Consider the security posture of your organization and its unique requirements when selecting from the azure mfa options.
Phone calls, SMS messages, and authenticator apps represent common options. Phone calls provide a strong second factor, but reliance on phone service can present reliability challenges. SMS messages are simpler to implement, but they introduce vulnerabilities related to SIM swapping. Authenticator apps offer a more secure and convenient alternative, reducing reliance on external services. Choose the method that best suits your organization’s security and operational needs. When evaluating azure mfa options, factor in the trade-offs between security, ease of use, and reliability. This comprehensive overview allows organizations to make informed decisions.
The relative security of each azure mfa option varies significantly. SMS messages, though convenient, are vulnerable to interception and SIM swapping attacks, making them less secure compared to other options. Phone calls, while more secure than SMS, require a functional phone line and might not be as reliable in areas with poor cellular coverage. Authenticator apps are highly secure, offering a robust second factor, especially for remote employees or users who prefer self-service options. Thorough security planning is crucial when selecting the right authentication method for azure mfa options. Organizations should consider their specific security needs to determine the optimal method. Analyze various factors to find the most suitable option.
How to Secure Your Azure Resources with MFA
Setting up and configuring different Azure MFA options requires a methodical approach. Proper enrollment of users and management of MFA policies are crucial for optimal security. This section provides actionable instructions for securing your Azure environment with various authentication methods. Implementing robust security measures with Azure MFA options is paramount for organizations to maintain a strong defense against unauthorized access.
The initial step involves enrolling users in the Azure MFA program. Navigate to the Azure portal and select the appropriate user accounts. Choose the desired authentication method—phone call, SMS message, or authenticator app—and follow the specific prompts. Each method has distinct setup procedures, ensuring correct configuration and user acceptance. Once enrolled, manage MFA policies to determine the enforcement frequency and types of authentication required. Understanding these policies is essential for effective security administration. Review and update these policies periodically as needed, given evolving security threats and compliance requirements. Regular reviews are vital for maintaining the robustness of Azure MFA options for your Azure environment. Implementing these policies will safeguard sensitive data and critical systems.
Efficient management of Azure MFA options requires consistent monitoring of user activity. Regularly review logs to identify any unusual or suspicious activity. Analyze user behavior patterns to detect possible vulnerabilities and potential threats. Promptly respond to any detected anomalies and escalate critical issues as needed. Regular security audits are recommended to review Azure MFA policies and identify areas needing enhancement. By systematically configuring and managing the Azure MFA options, organizations proactively enhance their overall security posture. This ensures a strong defense against potential threats and maintains a secure digital environment.
Evaluating Azure MFA Options for User Experience
User experience significantly influences the adoption and success of Azure Multi-Factor Authentication (MFA) solutions. Assessing the usability and ease of access of each method is critical. Users must find the chosen MFA method intuitive and straightforward to ensure long-term compliance and security within Azure environments. Ease of use minimizes frustration and encourages consistent adherence to security protocols. Evaluating user acceptance rates and satisfaction metrics helps ascertain the optimal Azure MFA options.
Different Azure MFA options offer varying levels of user experience. Phone calls, while reliable, might pose accessibility challenges for users in regions with limited or expensive call services. SMS messages, while widely accessible, rely on network connectivity, introducing potential delays or disruptions. Authenticator apps provide a convenient, secure, and often seamless experience, assuming user familiarity with app-based authentication. Choosing the optimal Azure MFA option involves balancing security, scalability, and usability. A crucial aspect is ensuring the selected method aligns with the technical proficiency of the user base, as well as any existing company policies.
Analyzing user feedback and conducting usability testing for various Azure MFA methods is essential. Gathering data on user acceptance, satisfaction, and perceived ease of use can guide selection decisions. The ideal Azure MFA method fosters a smooth user experience while promoting security practices. Thorough testing, including user feedback surveys and focus groups, provides critical insights into user perceptions and usability challenges. This information, along with usability data, can highlight potential difficulties and suggest adjustments for a smoother user journey with Azure MFA options.
Analyzing Azure MFA Options for Cost-Effectiveness
Evaluating the financial implications of different Azure MFA options is crucial for organizations. Careful consideration of ongoing charges and licensing constraints associated with various Azure MFA methods is essential. This analysis considers cost-effectiveness alongside a robust security posture. Different authentication methods have diverse price points. Organizations must weigh these costs against the value proposition of improved security. Understanding the potential costs of each Azure MFA option is a fundamental aspect of informed decision-making.
Analyzing the cost-effectiveness of Azure MFA options involves comparing the relative costs of different methods. For instance, SMS-based authentication might have lower upfront costs but could incur higher recurring charges due to message volume. Conversely, authenticator apps generally have lower recurring costs, offering a potentially more cost-effective solution for the long term. Factors such as the expected user base and usage patterns must inform the final choice. Organizations should consider the potential licensing requirements that specific Azure MFA solutions might necessitate. Implementing a cost-effective Azure MFA solution requires careful planning and ongoing monitoring to maintain a balance between security and budget.
Minimizing costs while maintaining a robust security posture requires a strategic approach. Organizations can explore strategies such as leveraging free trials or evaluating potential volume discounts offered for higher user counts. Understanding which Azure MFA methods align with projected usage patterns and security requirements is vital. Evaluating the total cost of ownership (TCO) of each approach, incorporating both upfront and recurring expenses, is critical. Thorough planning allows a balance between robust security and judicious budget allocation when choosing the right Azure MFA option for an organization’s needs.
Best Practices for Selecting the Right Azure MFA Method
Selecting the optimal Azure MFA option hinges on careful consideration of various factors. Prioritizing security, user experience, and cost-effectiveness is crucial. A tailored approach is key, considering the specific needs and resources of each organization. Organizations need to thoroughly assess their unique circumstances to identify the ideal Azure MFA options for their environment.
A key element in selecting the right Azure MFA method is understanding user location and device availability. If users primarily access Azure resources from specific geographical regions, certain MFA methods might be more practical than others. Similar logic applies to device accessibility; ensure the chosen method aligns with the typical devices used by employees. Evaluate the reliability and availability of communication channels for each chosen option. Robust networks and dependable service providers enhance the overall user experience, bolstering user adoption. Consider integrating the Azure MFA method with existing security infrastructure and systems. Seamless integration minimizes disruption and enhances overall security posture.
Security policies should strongly influence the selection process. Organizations must weigh the potential risks associated with different Azure MFA options. Thorough analysis of security threats is essential to selecting appropriate protection measures. Compliance requirements, both internal and external, must be reflected in the chosen solution. Consider the potential cost implications of different Azure MFA options. Long-term cost-effectiveness must be balanced with initial costs and ongoing maintenance fees. Evaluate different Azure MFA options to understand their potential impact on user experience and productivity. A method that is easily integrated and used without significant disruption enhances employee satisfaction and overall organizational efficiency. Carefully consider how Azure MFA options may affect different Azure services; evaluate the chosen method’s compatibility with various Azure services. Understanding which method seamlessly integrates with storage, virtual machines, and active directory is essential for a streamlined approach.
MFA Options for Different Azure Services
Choosing the right Azure MFA method is crucial for securing various Azure services. Different authentication methods have varying implications for access to services like storage, virtual machines, and Active Directory. Understanding these implications helps organizations select the most effective solution.
For instance, authenticator apps often offer a more secure and convenient way to access Azure Virtual Machines compared to phone calls. This is because authenticator apps typically employ stronger encryption protocols and reduce reliance on potentially vulnerable SMS channels. However, for Azure storage, the ease and speed of SMS verification might prove advantageous for less technically savvy users. This accessibility can influence user adoption rates. The security implications, particularly for sensitive data, should be a primary consideration. Evaluating the specific needs of each service within your Azure environment will assist in selecting the optimal Azure MFA options. A robust security posture requires carefully considering the risks associated with each option. Organizations should prioritize strong authentication for accessing sensitive resources and data.
The selection of Azure MFA options also depends on how different Azure services are configured. Certain services might enforce specific authentication requirements, dictating which Azure MFA methods are permissible. Consider the unique access needs of each service and prioritize the most robust security measures available. An organization’s policy regarding the acceptance of particular authentication methods is crucial to maintaining data security. Careful assessment of the compatibility between the various Azure MFA options and the specifics of each Azure service will significantly impact the overall security posture. For example, phone calls might not be the most suitable method for accessing virtual machines needing rapid response, where authenticator apps often prove more efficient. Thus, understanding the interplay between different Azure services and authentication methods is key to building a strong, secure Azure environment.
Security Considerations When Choosing Azure MFA
Selecting the appropriate Azure MFA options is crucial for bolstering the overall security posture of Azure resources. A well-chosen authentication method can significantly mitigate potential threats, enhancing compliance with industry standards and internal security policies. This careful consideration directly impacts the ability of malicious actors to access sensitive data or compromised systems.
The security implications of various Azure MFA options extend beyond the immediate access point. Robust authentication methods prevent unauthorized access to critical data and applications. The right Azure mfa options significantly reduce the risk of data breaches and minimize the potential for system compromise. Implementing strong authentication also often enhances the organization’s compliance with industry regulations and internal security standards. For example, careful consideration should be given to the security posture of choosing methods that enable two-factor authentication (2FA) for all users. This additional layer of security can drastically limit the potential impact of stolen credentials. Consider the potential for phishing attacks and man-in-the-middle attacks when assessing the security posture of different authentication methods.
Analyzing the potential attack vectors associated with different Azure MFA options is essential. Carefully evaluate the potential vulnerabilities of each authentication method. For instance, phone-based authentication methods can be susceptible to SIM swapping. On the other hand, authenticator apps provide a more secure alternative. This analysis should include both the internal security policies and externally enforced compliance standards. A thorough understanding of the potential risks enables the selection of a strong security architecture that is resilient to various threats. The selection of the right Azure MFA method directly reflects the level of security required to protect the organization’s assets and sensitive information.
When choosing Azure MFA options, security should be paramount. Robust authentication strengthens the overall security posture of Azure deployments. Employing proactive security measures ensures the integrity of Azure resources and the protection of sensitive data. Carefully vet each option against known security risks and ensure your chosen option aligns with the organization’s overall security strategy. Prioritizing a robust security approach is essential for maintaining a secure and reliable Azure infrastructure.