What are Azure Key Vault Roles?
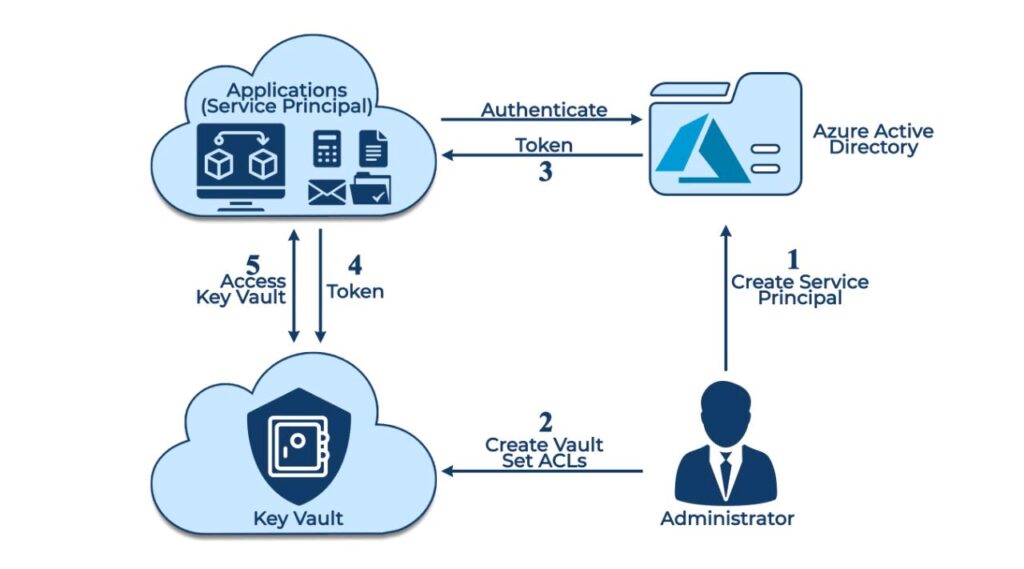
Azure Key Vault roles are built-in security identities within the Azure environment that help organizations manage and control access to key vaults and secrets. These roles are essential for enforcing security policies and maintaining compliance with various regulations and standards. By assigning specific roles to users, groups, or applications, organizations can ensure that only authorized individuals can access and manage key vaults and secrets, thereby reducing the risk of unauthorized access and data breaches.
Key Azure Key Vault Roles Explained
Azure Key Vault offers several built-in roles to manage and control access to key vaults and secrets. Here are the most important roles and their functions:
- Key Vault Contributor: This role allows users to create, delete, modify, and manage keys, secrets, and certificates within a key vault, but they cannot grant or revoke access to the key vault. It is ideal for administrators and developers who need to manage key vault resources.
- Key Vault Reader: This role enables users to view keys, secrets, and certificates in a key vault, but they cannot modify or delete any resources. It is suitable for users who need to monitor or read sensitive information without making any changes.
- Key Vault Secrets User: This role allows users to read, list, and delete secrets within a key vault, but they cannot create, update, or manage keys, certificates, or access policies. It is useful for applications or services that need to access secrets without modifying or managing other key vault resources.
- Key Vault Crypto Service Encryption Contributor: This role permits users to manage crypto service encryption keys in a key vault, but they cannot manage other keys, secrets, or access policies. It is essential for users who need to manage encryption keys for data at rest and in transit.
How to Assign Azure Key Vault Roles
Assigning Azure Key Vault roles is a crucial aspect of managing access to key vaults and secrets in the Azure environment. Here are the steps to assign roles using the Azure Portal, Azure PowerShell, Azure CLI, and REST API:
Azure Portal
To assign Azure Key Vault roles using the Azure Portal, follow these steps:
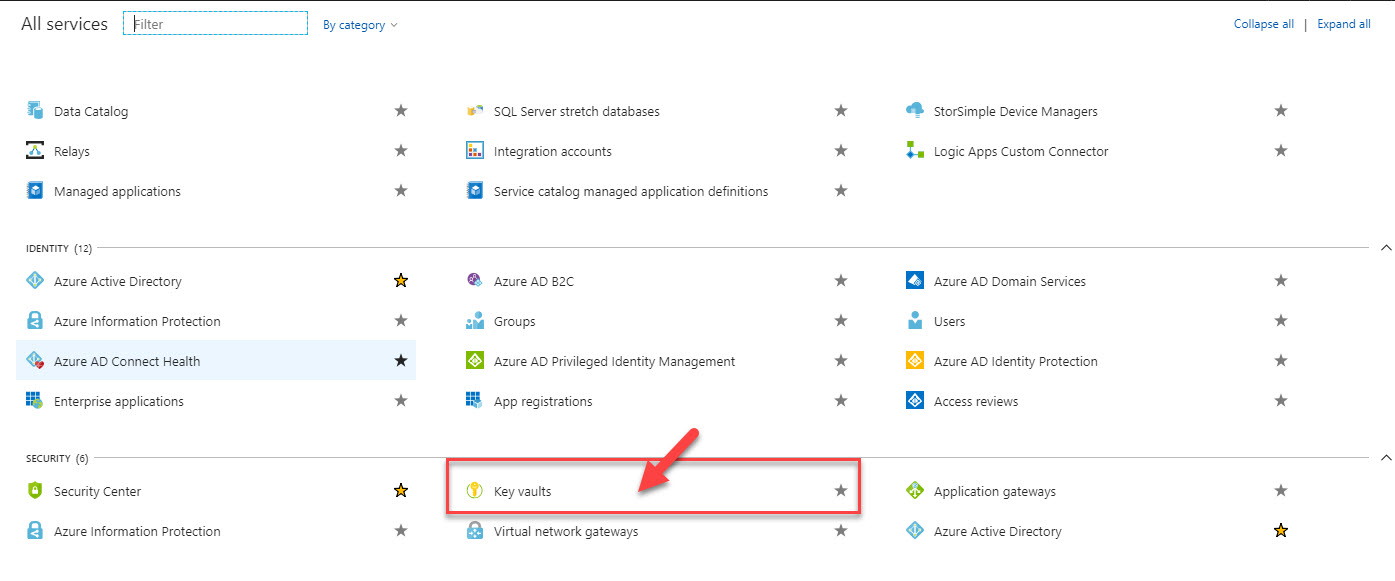
- Navigate to the Azure Portal and open the Key Vault resource.
- Click on “Access control (IAM)” and then “Add role assignment.”
- Select the desired role, such as “Key Vault Contributor” or “Key Vault Reader.”
- Enter the user, group, or application principal’s email address or object ID in the “Select” field.
- Click “Save” to assign the role.
Azure PowerShell
To assign Azure Key Vault roles using Azure PowerShell, use the following script:
# Set variables $resourceGroupName = "myResourceGroup" $keyVaultName = "myKeyVault" $roleDefinitionName = "Key Vault Contributor" $principalId = "userObjectId"
Get the Key Vault resource
$keyVault = Get-AzKeyVault -ResourceGroupName $resourceGroupName -Name $keyVaultName
Get the role definition
$roleDefinition = Get-AzRoleDefinition -Name $roleDefinitionName
Create a role assignment
New-AzRoleAssignment -ObjectId $principalId -RoleDefinitionId $roleDefinition.Id -Scope $keyVault.ResourceId
Azure CLI
To assign Azure Key Vault roles using Azure CLI, use the following command:
# Set variables resource_group_name="myResourceGroup" key_vault_name="myKeyVault" role_definition_id="" principal_id="userObjectId"
Create a role assignment
az role assignment create --assignee $principal_id --role "$role_definition_id" --scope "/subscriptions//resourceGroups/$resource_group_name/providers/Microsoft.KeyVault/vaults/$key_vault_name"
REST API
To assign Azure Key Vault roles using the REST API, send a PUT request to the following endpoint:
/subscriptions//resourceGroups//providers/Microsoft.Authorization/roleAssignments/" Include the following JSON payload in the request body:
{ "properties": { "roleDefinitionId": "/subscriptions//providers/Microsoft.Authorization/roleDefinitions/", "principalId": "", "scope": "/subscriptions//resourceGroups//providers/Microsoft.KeyVault/vaults/" } } Best Practices for Managing Azure Key Vault Roles
Effective management of Azure Key Vault roles is crucial for maintaining security and compliance in the Azure environment. Here are some best practices to help you manage Azure Key Vault roles:
- Regularly review role assignments: Regularly review role assignments to ensure that only the necessary users, groups, or applications have access to key vaults and secrets. Remove any unused or unnecessary role assignments to minimize the risk of unauthorized access.
- Implement least privilege access: Grant users, groups, or applications the minimum level of access required to perform their tasks. This practice reduces the risk of accidental or intentional misuse of sensitive information.
- Use role-based access control (RBAC) strategically: RBAC allows you to granularly control access to Azure resources. Use RBAC to create custom roles tailored to your organization’s needs, and assign these roles to users, groups, or applications as required.
- Monitor and audit Key Vault activities: Monitor and audit Key Vault activities to detect any suspicious or unauthorized access attempts. Use Azure Monitor, Azure Log Analytics, or Azure Security Center to gain insights into Key Vault activities and ensure that your security policies are enforced.
By following these best practices, you can effectively manage Azure Key Vault roles, maintain security and compliance, and protect sensitive information in your Azure environment.
Azure Key Vault Role-Based Access Control vs. Access Policies
Azure Key Vault offers two approaches for managing access to key vaults and secrets: Role-Based Access Control (RBAC) and Access Policies. Understanding the differences, strengths, and weaknesses of these approaches is crucial for effective access management.
Role-Based Access Control (RBAC)
RBAC is a powerful and flexible access management framework in Azure that allows you to control access to resources based on specific roles. RBAC is built on Azure Resource Manager (ARM) and enables you to assign roles at various scopes, such as the subscription, resource group, or resource level. RBAC supports built-in roles, such as “Key Vault Contributor” and “Key Vault Reader,” as well as custom roles tailored to your organization’s needs.
- Strengths: RBAC offers centralized access management, making it easy to assign and manage roles for multiple users, groups, or applications. It also supports fine-grained access control and auditing capabilities, enabling you to enforce security policies and maintain compliance.
- Weaknesses: RBAC might not provide the necessary level of granularity for some scenarios, as it assigns permissions at the resource level. Additionally, RBAC does not support permissions for individual secrets or keys within a key vault.
Access Policies
Access Policies are an alternative approach for managing access to Azure Key Vault resources. Access Policies allow you to grant permissions to specific secrets, keys, or certificates within a key vault. You can assign these permissions to users, groups, or applications, and you can use Azure Active Directory (AAD) or service principals for authentication.
- Strengths: Access Policies offer granular control over permissions for individual secrets, keys, or certificates within a key vault. They also support more advanced authentication options, such as multi-factor authentication and just-in-time access.
- Weaknesses: Access Policies can be challenging to manage at scale, as you need to assign permissions individually for each secret, key, or certificate. They also lack centralized access management capabilities, making it difficult to assign and manage roles for multiple users, groups, or applications.
When to Use Each Approach
Choose RBAC when you need centralized access management and fine-grained access control at the resource level. Opt for Access Policies when you require granular control over permissions for individual secrets, keys, or certificates and advanced authentication options.
In many scenarios, using a combination of both RBAC and Access Policies can provide the most effective access management solution for your Azure Key Vault resources.
Real-World Scenarios for Azure Key Vault Roles
Azure Key Vault roles play a critical role in various real-world scenarios, enabling organizations to manage access to sensitive information securely and efficiently. Here are three common scenarios where Azure Key Vault roles are essential:
Securing Application Secrets and Keys
In a modern application landscape, developers often rely on Azure Key Vault to securely store and manage application secrets, keys, and certificates. By assigning appropriate Azure Key Vault roles, such as “Key Vault Secrets User” or “Key Vault Contributor,” developers can access the necessary secrets and keys without being granted unnecessary permissions. This practice helps organizations enforce security policies and maintain compliance with regulations like GDPR, HIPAA, and PCI DSS.
Managing Encryption Keys for Data at Rest and in Transit
Azure Key Vault plays a vital role in managing encryption keys for data at rest and in transit. By assigning the “Key Vault Crypto Service Encryption Contributor” role to the appropriate users, groups, or applications, organizations can ensure that only authorized personnel can manage encryption keys. This approach helps maintain the confidentiality, integrity, and availability of sensitive data, while also simplifying key management and reducing the risk of data breaches.
Implementing Multi-Factor Authentication and Just-in-Time Access
Azure Key Vault supports advanced authentication options, such as multi-factor authentication (MFA) and just-in-time (JIT) access. By assigning the appropriate Azure Key Vault roles and configuring MFA and JIT access, organizations can further enhance their security posture. For instance, granting the “Key Vault Contributor” role to a user only when they need to perform a specific task and requiring MFA for authentication can minimize the risk of unauthorized access and data breaches.
By understanding these real-world scenarios, organizations can effectively leverage Azure Key Vault roles to secure sensitive information, enforce security policies, and maintain compliance with various regulations and standards.
Azure Key Vault Roles and Compliance
Azure Key Vault plays a crucial role in helping organizations comply with various regulations and standards, such as GDPR, HIPAA, and PCI DSS. By assigning appropriate Azure Key Vault roles, organizations can enforce security policies, manage access to sensitive information, and maintain compliance.
GDPR (General Data Protection Regulation)
GDPR is a regulation that requires businesses to protect the personal data and privacy of EU citizens. Azure Key Vault roles can help organizations comply with GDPR by providing secure storage and management for encryption keys, secrets, and certificates. By assigning the “Key Vault Contributor” or “Key Vault Secrets User” role to authorized personnel, organizations can ensure that only authorized individuals can access and manage sensitive information.
HIPAA (Health Insurance Portability and Accountability Act)
HIPAA is a US law that provides data privacy and security provisions for safeguarding medical information. Azure Key Vault roles can assist organizations in complying with HIPAA by managing encryption keys and secrets for protected health information (PHI). By assigning the “Key Vault Crypto Service Encryption Contributor” role to authorized personnel, organizations can ensure that only authorized individuals can manage encryption keys for PHI, thus maintaining the confidentiality, integrity, and availability of sensitive data.
PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS is a set of security standards designed to ensure that all companies that accept, process, store or transmit credit card information maintain a secure environment. Azure Key Vault roles can help organizations comply with PCI DSS by providing secure storage and management for encryption keys, secrets, and certificates related to payment card data. By assigning the “Key Vault Contributor” or “Key Vault Secrets User” role to authorized personnel, organizations can ensure that only authorized individuals can access and manage sensitive payment card data.
By understanding how Azure Key Vault roles contribute to compliance with various regulations and standards, organizations can effectively leverage these roles to meet their compliance requirements and maintain the security and privacy of sensitive information.
Trends and Future Developments for Azure Key Vault Roles
Azure Key Vault roles are continually evolving to meet the growing needs of organizations in managing access to key vaults and secrets in the Azure environment. Here are some trends and future developments related to Azure Key Vault roles:
Integration with Azure Policy
Azure Policy is a service that allows organizations to define and enforce consistent policies across their Azure resources. In the future, we can expect tighter integration between Azure Key Vault roles and Azure Policy, enabling organizations to create custom policies that automatically assign Azure Key Vault roles based on specific conditions and rules.
Enhanced Auditing and Monitoring Capabilities
Auditing and monitoring are critical components of any security strategy. As Azure Key Vault roles continue to evolve, we can expect enhanced auditing and monitoring capabilities, such as more detailed logs, improved alerting mechanisms, and better integration with Azure Security Center and Azure Monitor.
Support for More Granular Permissions
As organizations continue to adopt Azure Key Vault for managing secrets, keys, and certificates, there is a growing need for more granular permissions. In the future, we can expect Azure Key Vault roles to support more fine-grained permissions, allowing organizations to control access to specific secrets, keys, or certificates with greater precision.
Integration with Azure Active Directory (AAD) Conditional Access
Azure Active Directory (AAD) Conditional Access is a service that allows organizations to control access to Azure resources based on conditions such as user location, device compliance, and risk level. In the future, we can expect tighter integration between Azure Key Vault roles and AAD Conditional Access, enabling organizations to enforce more advanced access control policies for Azure Key Vault resources.
Improved Support for Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a critical security measure for protecting sensitive information. As Azure Key Vault roles continue to evolve, we can expect improved support for MFA, enabling organizations to require MFA for specific Azure Key Vault operations or for users accessing Azure Key Vault resources from specific locations.
By staying up-to-date with these trends and future developments, organizations can make the most of Azure Key Vault roles and ensure that they are using the latest features and best practices for managing access to key vaults and secrets in the Azure environment.