Understanding Azure Virtual Network Architecture
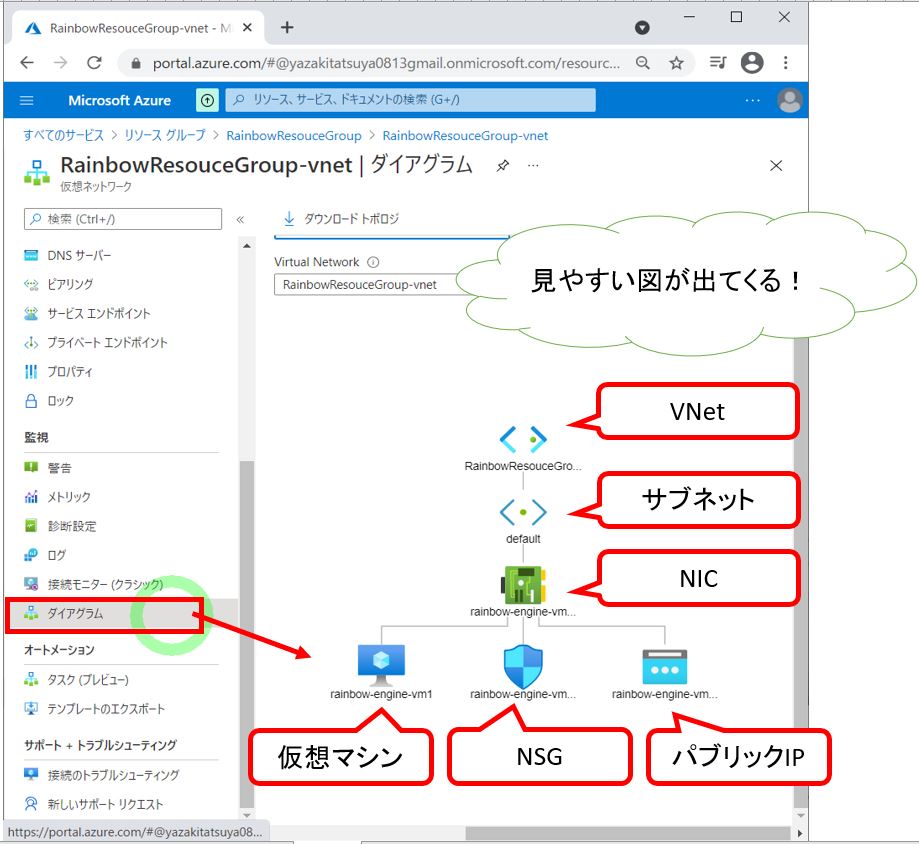
To grasp the nuances of azure firewall vnet requirements, it’s crucial to first understand the fundamental components of an Azure Virtual Network (VNet). An Azure VNet is essentially a logically isolated network within the Azure cloud, allowing you to provision and manage virtual machines and other Azure resources in a secure and private manner. It is the foundational element for any infrastructure deployed within Azure, providing a dedicated space for your resources. A VNet is divided into subnets, which are smaller logical divisions within the VNet. Subnets enable you to further segregate your resources and control traffic flow between them. Each subnet is assigned a unique address range, further increasing resource isolation. Network Security Groups (NSGs) are utilized at the subnet or virtual machine level to provide basic traffic filtering based on ports and protocols. They control both inbound and outbound traffic by defining rules that either allow or deny packets based on their source and destination. However, while NSGs offer a good starting point for network security, they have limitations when it comes to more granular control and advanced security features. A visual representation of a typical Azure network, including VNets, subnets, and NSGs, would clearly highlight how resources are logically separated and secured at a basic level.
The interaction between VNets, subnets, and NSGs form the base for your cloud networking. A VNet provides the overarching isolation while subnets allow for further compartmentalization within that space. NSGs, while providing security, are stateful and typically applied at the interface level. This basic structure establishes the need for more advanced solutions for azure firewall vnet requirements. Considering these requirements, implementing a more robust method for traffic management such as an Azure Firewall is typically needed to manage traffic and enforce security policies across resources in a more comprehensive way. It provides granular control over the traffic entering and exiting the VNet, something NSGs by themselves cannot achieve. Understanding this foundation clarifies the need for a detailed security strategy, with the inclusion of elements that provide greater control and granular oversight.
A basic example might include a VNet that has three subnets; one for web servers, one for application servers, and one for database servers. Each of these subnets will have an NSG to manage traffic to their resources, but overall the VNet lacks an overall firewall. This is where azure firewall vnet requirements come into play. The importance of the firewall’s role becomes apparent as you move from managing basic security via NSGs to the need for detailed inspection and control of traffic. This fundamental understanding of VNets and their basic security capabilities sets the stage for a discussion on why an Azure Firewall is often required for a more complete security model. Incorporating an Azure Firewall gives you the capability to centralize network traffic management and policy enforcement across all your subnets within a VNet, a significant advantage over the limited capabilities of NSGs alone.
Why You Need a Firewall in Your Azure VNet
Securing your Azure Virtual Network (VNet) is paramount, and while Network Security Groups (NSGs) offer a basic level of protection, they often fall short in addressing the sophisticated threats prevalent in today’s digital landscape. A VNet, without a dedicated firewall, is susceptible to a range of security risks, including Distributed Denial of Service (DDoS) attacks designed to overwhelm resources and disrupt services. Unauthorized access attempts, both from external sources and potentially compromised internal systems, can lead to data breaches and significant financial losses. Furthermore, without a robust firewall, lateral movement within the VNet by malicious actors is significantly easier, allowing them to compromise more systems and sensitive information. NSGs primarily operate at the subnet level, controlling traffic based on IP addresses and ports, which provides a foundational security layer but lacks the in-depth packet inspection and application-aware controls a firewall delivers. Understanding these limitations makes the need for an azure firewall vnet requirements quite evident. Therefore, implementing an azure firewall is not just an option but a necessity for creating a more robust security posture.
The value proposition of an azure firewall extends beyond the basic security offered by NSGs. An azure firewall provides advanced threat protection capabilities including intrusion detection and prevention systems (IDPS), which actively monitor network traffic for malicious patterns and can automatically block or quarantine suspicious activity. Unlike NSGs, firewalls can perform deep packet inspection, examining the content of network traffic to identify and block threats that might otherwise go unnoticed. This granularity allows for more precise control over network traffic, ensuring only legitimate communication is permitted. Furthermore, an azure firewall simplifies security management by centralizing rule configurations and providing enhanced logging and monitoring capabilities, enabling security teams to quickly identify and respond to security incidents. The inclusion of a firewall also facilitates the establishment of more complex routing scenarios, enabling the segmentation of networks and enhancing control over the flow of traffic across different zones and subnets, crucial for enterprises with stringent compliance requirements. The complexity of securing a modern virtual network highlights why adhering to the azure firewall vnet requirements is critical for every organization.
In conclusion, relying solely on NSGs for VNet security is akin to having a lock on your door but not a security system. While NSGs play an important role in network micro-segmentation, an azure firewall is critical in addressing a broader spectrum of threats and enabling advanced security functionality. It adds a necessary layer of protection, helping to enforce stringent security policies and ensure compliance standards are met. The implementation of an azure firewall strengthens the overall security framework of an Azure VNet, ensuring protection against both internal and external threats and provides the capabilities to detect, respond to, and mitigate potential incidents. It is a critical piece of any well-designed security architecture for organizations utilizing Azure virtual networks, fulfilling critical azure firewall vnet requirements.
Azure Firewall Deployment Options: Choosing the Right Approach
Deploying an Azure firewall to meet your azure firewall vnet requirements involves several strategic choices, each with its own implications for cost, scalability, and management. One common approach is to deploy the Azure firewall as a standalone component within a dedicated subnet of your virtual network. This method provides a clear separation of concerns, allowing for centralized management and monitoring of all network traffic. The firewall acts as a dedicated security appliance, inspecting and controlling both inbound and outbound traffic. This is often ideal for environments requiring granular control and maximum security. However, this method can incur higher costs due to the dedicated resources for the firewall and its associated infrastructure. Alternatively, Azure Firewall can be integrated with other Azure security services, such as Azure Virtual WAN. This integration allows for centralized network security management across multiple virtual networks and hybrid cloud environments, simplifying the overall architecture and reducing operational overhead, ideal for larger, distributed networks that have complex azure firewall vnet requirements. This approach reduces the complexity of managing multiple firewalls in multiple VNets but may have higher infrastructure costs.
Another deployment consideration revolves around the level of integration with Azure security services. For example, you might choose to integrate Azure Firewall with Azure Monitor and Azure Log Analytics for enhanced logging and monitoring, gaining insights into traffic patterns and security events that are critical to maintaining robust security. The level of integration also affects the operational workload; deeper integrations provide enhanced security but may require a more skilled operational team. Each of these options presents a trade-off between cost, scalability, and the level of integration needed. For instance, a standalone deployment might be more cost-effective for a smaller environment with simpler network needs, while integrating with Virtual WAN could be more efficient for large-scale or enterprise-level deployments. Therefore, when deciding on how to implement your azure firewall vnet requirements, consider your environment’s size, traffic patterns, and security requirements, to guide the selection process.
Additionally, it’s crucial to evaluate your team’s expertise and available resources. A standalone deployment might require more in-depth knowledge of firewall configuration, while integrating with other services could be easier to manage but could also limit flexibility. The best approach to fulfill your azure firewall vnet requirements depends on a balanced consideration of all of these factors, and a clear understanding of the operational and cost implications that come with each option. By understanding the different deployment models and their inherent trade-offs, users can effectively plan and execute a firewall strategy that best aligns with their organization’s specific needs. Therefore, a careful evaluation of current and future needs, alongside a cost-benefit analysis, is crucial for selecting the most suitable Azure firewall deployment strategy.
How to Configure Azure Firewall for Your VNet
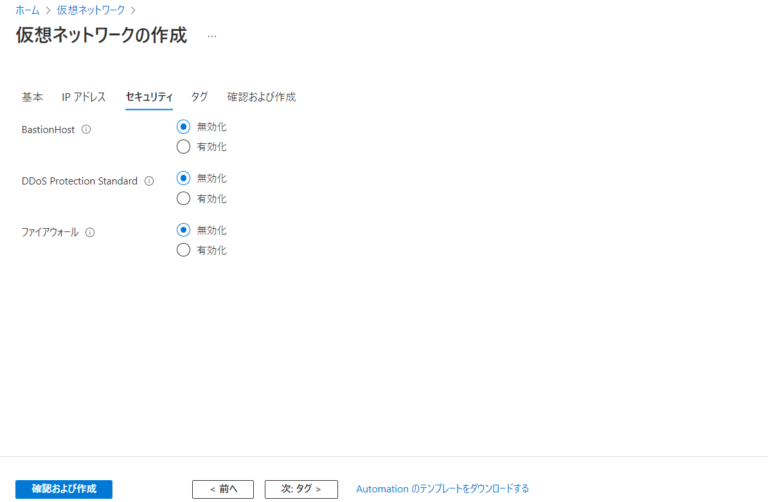
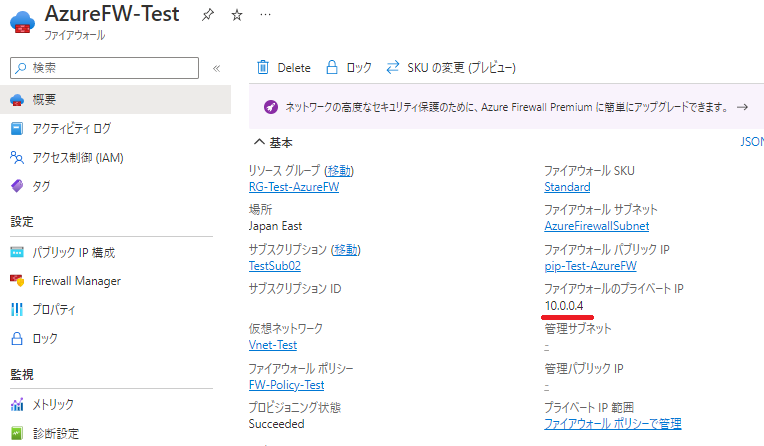
Configuring an Azure firewall for your Virtual Network (VNet) is a crucial step in securing your Azure resources. This process involves several key configurations to ensure your network is protected against unauthorized access and potential threats. First, you’ll need to create an Azure Firewall resource within your subscription. This involves navigating to the Azure portal, selecting “Create a resource,” and searching for “Firewall.” During the creation process, you’ll need to specify the resource group, region, and a name for your firewall. A key part of the setup is choosing a network configuration, which will typically involve creating a dedicated subnet within your VNet for the firewall. This subnet, often named AzureFirewallSubnet, should have a minimum size of /26, and it should be exclusively for the firewall. After the firewall resource is created, the next step involves defining the firewall policy. This policy dictates how the firewall handles network traffic. It includes rule collections that define allow and deny rules based on source IP addresses, destination IP addresses, ports, and protocols. These rules are essential in managing both inbound and outbound traffic. Proper understanding of network addresses is paramount to implement appropriate azure firewall vnet requirements, so be precise to avoid potential connectivity issues.
Once your firewall is deployed, and the policies are in place, the next key step is to configure routing. This is done by creating a user-defined route (UDR) table and associating it with the subnets that host your workloads. These UDRs force traffic to go through the firewall, which allows the policies to inspect traffic as it enters and leaves the network. For inbound traffic, you will configure DNAT (Destination Network Address Translation) rules to forward traffic coming from a public IP to the specific IP address of your resources in your VNet. This is where a deep understanding of the azure firewall vnet requirements is paramount for a safe configuration. Outbound traffic routing will often leverage the default route that sends traffic to the Internet via the Azure firewall itself. The setup will also involve ensuring that resources within the VNet have their DNS settings pointing to the Azure firewall’s private IP address, which allows the firewall to resolve names and enforce policies. Remember, this configuration can require precise attention to detail, as incorrect rules can cause service disruptions. Carefully planning and testing these configurations will avoid future complications. Monitoring the Azure Firewall logs to verify proper functionality and compliance with azure firewall vnet requirements is an ongoing activity that contributes to a stable environment.
Furthermore, creating network rules within the firewall policy involves defining both allow and deny rules. An “Allow” rule typically specifies source IP, destination IP, port, and protocol, permitting matching traffic to proceed. Conversely, a “Deny” rule blocks traffic that matches the defined criteria. When configuring these rules, prioritize the most specific rules first, as they are evaluated in order. This ensures that the correct rule is applied to each traffic flow. Managing inbound and outbound traffic requires setting rules that are precisely aligned with your security needs and azure firewall vnet requirements. For example, to allow access to a web server from the internet, you would create a DNAT rule for inbound traffic to the webserver’s private address and make the respective firewall rules for outbound. This process of configuring an Azure firewall is crucial in enforcing your security policies and safeguarding your Azure infrastructure.
Essential Network Security Group (NSG) Considerations
While an Azure Firewall provides robust protection for your Azure Virtual Network, Network Security Groups (NSGs) play a crucial, complementary role in a layered security strategy. Understanding how NSGs interact with the firewall is paramount for ensuring comprehensive security. NSGs function as stateful packet inspection firewalls, operating at the subnet or virtual network interface level. Unlike the Azure Firewall, which handles traffic based on central policies, NSGs offer a more granular approach. The key is to avoid overlaps and to use them strategically to supplement the broader protection of the firewall. For example, an NSG can enforce a strict set of rules for traffic within a particular subnet, acting as an extra layer of defense. This is particularly useful when you need to control traffic between virtual machines within a subnet, regardless of the firewall’s broader policies. The integration of NSGs and Azure Firewall is a fundamental component when dealing with azure firewall vnet requirements. By combining their strengths, your overall security posture is substantially enhanced. NSGs should be designed to work with the firewall, not as replacements for it, and must be properly configured to prevent conflicts and vulnerabilities.
Best practices for integrating NSGs with an Azure Firewall emphasize a “least privilege” approach. Inbound rules for NSGs should typically be very restrictive, allowing only necessary traffic from specific sources. This ensures that even if a threat manages to bypass the firewall, the NSGs provide an additional layer of defense. Outbound rules should also be crafted carefully, only permitting required connections. It’s essential to regularly review and update both your Azure Firewall rules and NSG rules. Avoid overly permissive NSG configurations that could counteract the effectiveness of the Azure Firewall. When considering the azure firewall vnet requirements, remember that proper planning and testing of NSG configurations alongside your Azure Firewall are vital to establish a reliable security approach. One of the benefits of this security integration is the reduced complexity by avoiding redundant rules in your Azure Firewall while making full use of NSG’s more granular nature. Proper integration of NSGs and the Azure Firewall can create a significantly more secure and resilient architecture.
In practice, consider a scenario where an Azure Firewall manages traffic entering and leaving the VNet. NSGs then manage traffic within specific subnets. For example, a web server subnet might have an NSG allowing only inbound HTTP/HTTPS traffic and limiting outbound access to specific IP addresses. This provides a secondary layer of protection even if the firewall rules are compromised. This segmented approach to security, with NSGs working alongside an Azure Firewall, provides a robust method to meet the diverse azure firewall vnet requirements. Properly integrated NSGs enhance visibility into specific subnet traffic while the firewall manages broader policy and security enforcement. Think of NSGs as the ‘inner doors’ that offer additional localized protection complementing the Azure Firewall, which is the main gate of your network. This two-layered approach provides a greater chance of preventing intrusions and safeguarding your resources, which is a cornerstone when understanding the azure firewall vnet requirements.
Integrating Azure Firewall with Other Azure Security Services
Azure Firewall’s capabilities extend significantly when integrated with other Azure security services. This integration enables comprehensive security monitoring, threat detection, and response, enhancing the overall security posture of your Azure VNet. By leveraging Azure Monitor, for instance, detailed logs and metrics from the firewall are collected, providing valuable insights into network traffic patterns and potential security incidents. This data is crucial for identifying anomalies and understanding the effectiveness of the implemented security rules. Furthermore, integrating with Azure Log Analytics allows for centralized logging and analysis, enabling efficient querying and reporting on security events related to the azure firewall vnet requirements. This capability facilitates proactive threat identification and allows for the timely mitigation of potential security breaches.
Azure Sentinel, Microsoft’s cloud-native SIEM (Security Information and Event Management) solution, offers another powerful integration option. By connecting Azure Firewall logs to Azure Sentinel, security analysts gain a comprehensive view of security events across the entire Azure environment. This consolidated view simplifies threat hunting, incident response, and security compliance efforts. Real-time threat detection capabilities within Azure Sentinel are significantly enhanced by the detailed traffic logs provided by the Azure Firewall. The ability to correlate firewall data with other security logs helps to identify sophisticated attacks that might otherwise go unnoticed. This correlation is key to understanding the full context of a security event and taking appropriate action. The azure firewall vnet requirements for effective security monitoring are thus significantly streamlined through the use of these integrated services.
Effective integration with these services allows for the automation of security responses based on predefined rules and alerts. For example, upon detection of a suspicious activity flagged by Azure Sentinel based on Azure Firewall logs, automated actions such as blocking malicious IP addresses or triggering security alerts can be initiated. This automated response capability reduces the response time to security threats and minimizes potential damage. The overall benefit of integrating Azure Firewall with these complementary security services is a more robust, responsive, and efficient security infrastructure. This layered approach enhances the overall security of the Azure VNet and ensures compliance with various security standards and regulations. The proper configuration and utilization of these integrated tools are crucial in meeting the azure firewall vnet requirements for a truly secure environment.
Troubleshooting Common Azure Firewall Configuration Issues
Encountering issues while configuring an Azure firewall within a virtual network (VNet) is not uncommon, and addressing these problems effectively is crucial for maintaining a secure and functional environment. One of the most frequent challenges is connectivity problems. These often manifest as an inability for resources within the VNet to reach external services or other resources within different subnets, often related to incorrect network rules. When troubleshooting, first verify the firewall’s network rules to make sure that traffic is allowed and that no implicit deny rules are blocking the intended communication path. This includes checking source and destination IP addresses, ports, and protocols. Ensure the correct rule priority is set, as rules are processed in order of priority, so a higher priority rule might be overriding the intended rules. Examine the Azure Firewall logs and the network diagnostics tools for any specific errors and use them as a guide to pinpoint the root cause. Another aspect that is essential is the careful configuration of custom routes, making certain that traffic is being correctly routed to the firewall.
Rule conflicts can also lead to unexpected behavior, with different sets of configurations causing contradictory outcomes. This can occur when you have complex environments with numerous network rules, therefore a clear and well-planned firewall policy is essential for managing large deployments and avoid rule overlapping. When conflicting rules arise, it’s vital to review each one carefully and consider which rules might be overlapping, and then adjust priorities or modify them to prevent conflicts. In some instances, this might require creating more specific rules or combining similar rules to simplify the policy and avoid rule conflict scenarios. Performance bottlenecks are another issue, and it can surface as slow or intermittent connections. To address this, review the overall health of your azure firewall vnet requirements. Check Azure Firewall metrics using Azure Monitor and look out for high CPU or bandwidth usage, to identify resource limitations. This can be solved by scaling up the firewall deployment by selecting a more powerful instance type or making sure that all components of your Azure architecture are adequately sized. Make sure that the size of the firewall is adequate for the workload that it is intended to process.
Furthermore, misconfigured Network Security Groups (NSGs) can cause problems. An incorrectly set NSG rule might hinder network flow even when the Azure Firewall rules are correct, so review NSG configurations to ensure that they do not inadvertently block traffic that the firewall is intended to allow. It is also very important to verify DNS settings for proper name resolution and check that DNS servers configured in Azure Virtual Network are functional and that are correctly directing names to IP address translation. Another important point to consider is the maintenance of the Azure Firewall to make sure that it is upgraded to the last version and patched against known vulnerabilities. Finally, when in doubt, using Azure’s connectivity troubleshooting tools for network issues can assist in identifying if the issue is firewall related or stems from other areas of your virtual network setup, such as VPN connections or peered networks. Effective troubleshooting requires a methodical approach and attention to detail, and keeping in mind the azure firewall vnet requirements is key for a successful deployment.
Best Practices for Secure Azure VNet Design with Firewall
Designing a secure Azure Virtual Network (VNet) with a robust azure firewall vnet requirements demands careful planning and adherence to established best practices. It’s crucial to begin with a well-defined network segmentation strategy, dividing your VNet into multiple subnets based on function and security needs. Each subnet should be treated as a separate security zone, allowing for granular control over traffic flow. Implement a principle of least privilege, granting only the necessary access to resources. Avoid wide-open rules that permit unrestricted communication between subnets. Network Security Groups (NSGs) should be configured at the subnet level to provide a first layer of defense, controlling traffic based on source, destination, and port. Ensure that NSGs work in concert with the Azure Firewall, establishing a strong defense-in-depth approach. Regularly review your security policies and rules to prevent misconfigurations or unnecessary permissions. Furthermore, make use of tags to organize and categorize your resources, facilitating efficient management and policy enforcement. Remember, a secure Azure VNet is not a static entity; it’s an ongoing process that requires continuous monitoring and adaptation.
Optimizing your azure firewall vnet requirements also involves utilizing the full capabilities of the Azure Firewall. The firewall should be the central point of control for all inbound and outbound network traffic, replacing any reliance on individual NSG rules for core firewall functionality. Implement a layered approach to firewall rules, beginning with the most specific and moving towards more general rules. Employ threat intelligence feeds to proactively block traffic from known malicious sources. Regularly analyze firewall logs using Azure Monitor and Log Analytics to identify anomalies and potential security breaches. Actively use the firewall’s capabilities to create and enforce application rules to govern the specific kinds of applications that are permitted in your environment. Pay close attention to egress traffic, ensuring that only authorized traffic is leaving the VNet. Proper outbound control helps protect your VNet from data exfiltration and compliance violations. A well-structured firewall policy significantly enhances your security posture.
Adopting secure coding practices is also integral to overall VNet security. Regular vulnerability scanning of all applications deployed within your VNet is essential. Educate your development teams about secure coding principles and encourage a culture of security awareness. Always utilize the most recent versions of all software and operating systems to mitigate known vulnerabilities. Properly configured azure firewall vnet requirements also includes establishing robust monitoring and alerting. Set up alerts to inform you of any unusual or suspicious activity. This proactive approach empowers you to respond swiftly to threats and prevent significant security incidents. By integrating your Azure Firewall with Azure Sentinel, you can proactively detect and respond to sophisticated attacks that may otherwise go unnoticed. Remember that securing your Azure VNet is an ongoing commitment and requires consistent effort. By implementing these best practices, you can significantly reduce your attack surface and establish a highly secure cloud environment.
Understanding Azure Firewall VNet Requirements: A Deep Dive
Successfully securing an Azure Virtual Network (VNet) necessitates a solid grasp of fundamental networking concepts, especially concerning the role of an Azure firewall. The foundation of any secure cloud architecture begins with understanding what a VNet is—a logically isolated section of the Azure cloud where resources, such as virtual machines and databases, are placed. Subnets, subdivisions within the VNet, allow for further organization and segmentation. Network Security Groups (NSGs), acting as basic firewall rules, filter traffic at the subnet level. While NSGs provide essential protection, they have limitations, particularly in managing complex network traffic and sophisticated threats, underscoring the need for a more robust security solution such as the Azure firewall. Therefore, before deploying any application inside the VNet, a crucial initial step revolves around identifying the specific azure firewall vnet requirements. Planning these aspects carefully, understanding the fundamental architecture, and the role of the firewall are paramount for establishing strong security measures. Proper subnet segmentation, in conjunction with carefully defined firewall rules, ensures that any cloud-based infrastructure will have strong security and be able to face a wide array of threats.
The selection of an appropriate Azure firewall deployment strategy is critical, depending on specific azure firewall vnet requirements. Options range from deploying an Azure Firewall as a standalone component for a dedicated security solution to integrating it with other Azure security services for a more holistic approach. Each has its advantages and disadvantages, impacting cost, scalability, and management complexity. A standalone deployment provides dedicated resources, potentially enhancing performance, while integrated solutions leverage existing Azure services, streamlining management but possibly affecting cost efficiency. Configurations involve defining policies, setting up network rules, and managing both inbound and outbound traffic. Azure Firewall configurations should be thoughtfully constructed to minimize security risks. Network security groups, although fundamental, should never be the sole means of protection, instead, when integrated with the Azure Firewall, they provide a layered defense mechanism, increasing the overall security posture. For optimal security, it’s imperative to tailor both NSG and firewall settings to align with the specific application demands and organizational risk profile. In addition, it is key to monitor the firewall settings through Azure Monitor and integrate with Azure Log Analytics and Azure Sentinel for improved threat detection.
Configuring an Azure Firewall is essential for fulfilling the azure firewall vnet requirements. This process involves setting up firewall policies, network rules, and managing traffic efficiently. Often, users may encounter issues like connectivity problems or rule conflicts that hinder traffic flow. Troubleshooting steps should include an in-depth examination of the rule configuration, the specific network flows, and the associated logs, so that these issues are resolved promptly. To ensure a secure and efficient Azure VNet design, best practices must be followed consistently. This means deploying the firewall to control the ingress and egress of the VNet, minimizing the attack surface, and regularly reviewing firewall configurations. Compliance with industry standards also needs to be considered, so that the cloud environment remains secure and compliant. Therefore, adopting a security-centric design early in the planning process, involving a carefully designed firewall configuration, along with NSGs, significantly fortifies the Azure VNet against potential threats. By consistently adhering to these principles, organizations can ensure robust protection for their cloud resources, thereby maintaining the integrity and availability of their services.