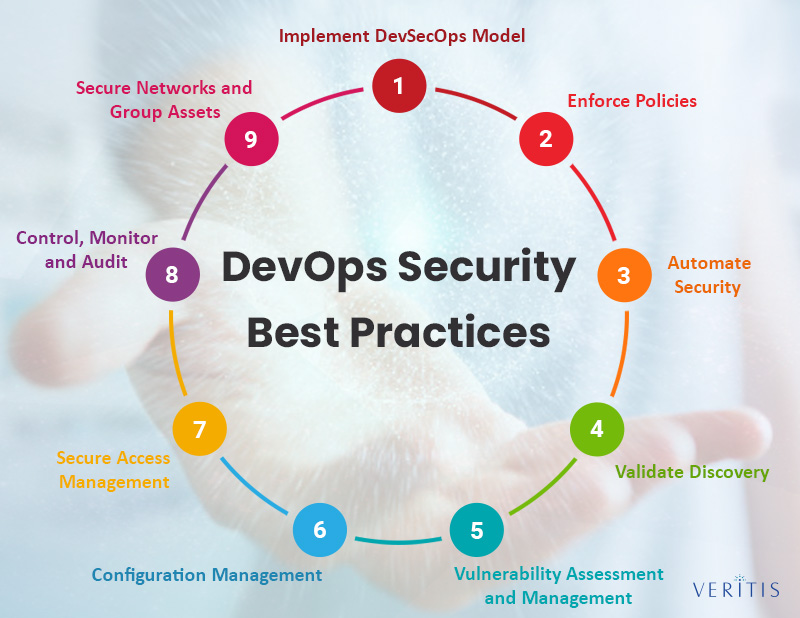
Azure DevOps Security Best Practices: An Overview
Azure DevOps has become an essential tool for modern development processes, enabling teams to collaborate, build, test, and deploy software efficiently. However, as with any cloud-based platform, security remains a top concern. Implementing robust Azure DevOps security best practices can help organizations mitigate potential threats, protect sensitive data, and maintain compliance with regulations. In this article, we will discuss the key aspects of securing Azure DevOps environments, including access control, code repository protection, monitoring, incident response, and continuous security.
Understanding Security Threats in Azure DevOps
Azure DevOps, like other cloud-based platforms, faces various security threats that can compromise sensitive data, disrupt development processes, and damage an organization’s reputation and financial stability. Some common security threats in Azure DevOps include unauthorized access, data breaches, and misconfigurations. Unauthorized access occurs when malicious actors gain access to Azure DevOps resources without proper authorization, potentially stealing or tampering with data. Data breaches can result from insufficient security measures, allowing unauthorized users to exfiltrate sensitive information. Misconfigurations, such as leaving resources open to public access or mismanaging permissions, can lead to security vulnerabilities and expose organizations to potential attacks.
Implementing Access Control and Authentication Best Practices
Access control and authentication are crucial components of Azure DevOps security best practices. Implementing strong access control and authentication measures can help organizations prevent unauthorized access, data breaches, and other security threats. Here are some recommendations for access control and authentication in Azure DevOps:
- Use strong passwords: Encourage users to create complex passwords that include a mix of uppercase and lowercase letters, numbers, and special characters. Consider implementing password policies that enforce password complexity and expiration.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security by requiring users to provide at least two forms of identification before accessing Azure DevOps resources. MFA can significantly reduce the risk of unauthorized access and data breaches.
- Follow the principle of least privilege: Assign users the minimum permissions necessary to perform their tasks. Regularly review and update user permissions to ensure they are appropriate and up-to-date.
- Manage user roles effectively: Azure DevOps provides several built-in user roles, such as administrator, contributor, and reader. Assign users to the appropriate role based on their responsibilities and tasks.
Securing Code Repositories and Build Pipelines in Azure DevOps
Code repositories and build pipelines are critical components of any software development process, and securing them is essential to prevent security threats and maintain the integrity of the development process. Here are some best practices for securing code repositories and build pipelines in Azure DevOps:
- Enable branch policies: Branch policies in Azure DevOps allow organizations to enforce security measures, such as required code reviews and automated build validation, before merging code changes. Enforcing branch policies can help prevent unauthorized code changes and maintain the integrity of the codebase.
- Use secret variables: Secret variables in Azure DevOps allow organizations to securely store and manage sensitive information, such as API keys and passwords, used in build and release pipelines. Using secret variables can help prevent unauthorized access to sensitive information and reduce the risk of data breaches.
- Integrate security testing tools: Integrating security testing tools, such as static application security testing (SAST) and dynamic application security testing (DAST), into build pipelines can help organizations identify and remediate security vulnerabilities early in the development process. Automating security testing can help ensure that security best practices are consistently applied throughout the development lifecycle.
- Conduct regular code reviews: Regular code reviews can help organizations identify and remediate security vulnerabilities and maintain the integrity of the codebase. Code reviews can also help ensure that developers are following security best practices and coding standards.
- Perform threat modeling: Threat modeling is the process of identifying and mitigating potential security threats to an application. Performing threat modeling early in the development process can help organizations identify and remediate potential security vulnerabilities before they become a problem.
Monitoring and Auditing Azure DevOps Environments: Best Practices
Monitoring and auditing Azure DevOps environments is crucial to maintaining the security and integrity of your development processes. Regular monitoring and auditing can help you detect and respond to security threats, ensure compliance with regulations, and improve your overall security posture. Here are some best practices for monitoring and auditing Azure DevOps environments:
- Set up alerts: Azure DevOps allows you to set up alerts for various events, such as failed builds, security vulnerabilities, and policy violations. Setting up alerts can help you quickly detect and respond to security threats and maintain the integrity of your development processes.
- Review activity logs: Azure DevOps provides activity logs that record all user actions, such as creating a new branch, changing permissions, or deleting a file. Regularly reviewing activity logs can help you detect suspicious activity, investigate security incidents, and ensure compliance with regulations.
- Use third-party tools: Third-party tools, such as security information and event management (SIEM) systems, can help you monitor and audit Azure DevOps environments more effectively. SIEM systems can aggregate and analyze log data from multiple sources, providing real-time alerts and reports on security threats and compliance violations.
- Conduct regular security assessments: Regular security assessments can help you identify and remediate security vulnerabilities in your Azure DevOps environments. Security assessments can include vulnerability scanning, penetration testing, and code review. Conducting regular security assessments can help you maintain a strong security posture and ensure compliance with regulations.
How to Respond to Security Incidents in Azure DevOps
Despite implementing robust security best practices, security incidents can still occur in Azure DevOps environments. Here’s how to respond to security incidents in Azure DevOps:
- Report vulnerabilities: If you discover a vulnerability in Azure DevOps, report it to Microsoft immediately. Microsoft has a responsible disclosure policy and will work with you to address the vulnerability and protect Azure DevOps users.
- Contain breaches: If a security breach occurs, contain it as quickly as possible to minimize the damage. This may involve disabling compromised accounts, changing passwords, and isolating affected systems.
- Conduct post-incident reviews: After a security incident, conduct a post-incident review to identify the root cause and prevent similar incidents from occurring in the future. This may involve reviewing logs, interviewing staff, and testing incident response plans.
- Incident response teams: Establish an incident response team responsible for responding to security incidents. The team should include representatives from IT, security, legal, and communications. The incident response team should have a clear plan for responding to security incidents, including communication plans and procedures for reporting incidents to management and regulators.
Best Practices for Compliance and Regulations in Azure DevOps
As organizations increasingly adopt Azure DevOps for their development processes, ensuring compliance and adhering to regulations is becoming more critical. Here are some best practices for compliance and regulations in Azure DevOps:
- Data protection: Ensure that sensitive data, such as personal identifiable information (PII) and intellectual property, is protected in Azure DevOps. Use encryption, access controls, and other security measures to safeguard data at rest and in transit.
- Retention policies: Establish retention policies for data in Azure DevOps, including code repositories, build pipelines, and work items. Retention policies can help organizations comply with data retention requirements and reduce the risk of data breaches.
- Vendor management: Ensure that vendors and third-party service providers comply with regulations and adhere to security best practices. This may involve conducting vendor assessments, reviewing vendor contracts, and establishing service-level agreements (SLAs) for security and compliance.
- Regulations: Understand the regulations that apply to your organization and ensure that Azure DevOps environments comply with them. For example, if your organization operates in the European Union (EU), you must comply with the General Data Protection Regulation (GDPR). If you operate in the healthcare industry, you must comply with the Health Insurance Portability and Accountability Act (HIPAA).
- Compliance reporting: Use Azure DevOps compliance reporting features to generate reports on compliance status, security incidents, and other compliance-related activities. Compliance reporting can help organizations demonstrate compliance to auditors, regulators, and other stakeholders.
Continuous Security in Azure DevOps: Integrating Security into DevOps Practices
In today’s fast-paced development environment, security cannot be an afterthought. Instead, it must be integrated into DevOps practices from the beginning. This approach, known as DevSecOps, emphasizes collaboration between development, security, and operations teams to ensure that security is built into every stage of the development lifecycle. Here are some best practices for implementing continuous security in Azure DevOps:
- Automate security testing: Use automated security testing tools, such as static application security testing (SAST) and dynamic application security testing (DAST), to identify and remediate vulnerabilities early in the development process. Automated security testing can help organizations save time and reduce the risk of introducing vulnerabilities into production environments.
- Integrate security into CI/CD pipelines: Integrate security tools and processes into continuous integration and continuous delivery (CI/CD) pipelines to ensure that security is built into every stage of the development process. This may involve using security gates in CI/CD pipelines to prevent code with known vulnerabilities from being deployed to production environments.
- Adopt a security-first culture: Encourage a security-first culture by providing security training and awareness programs for developers, operations, and security teams. This may involve providing training on secure coding practices, threat modeling, and secure deployment configurations.
- Monitor and audit Azure DevOps environments: Regularly monitor and audit Azure DevOps environments to detect and respond to security threats. This may involve setting up alerts for security events, reviewing activity logs, and using third-party tools for security monitoring and assessment.
- Collaborate across teams: Encourage collaboration between development, security, and operations teams to ensure that security is built into every stage of the development lifecycle. This may involve establishing cross-functional teams responsible for security or using collaboration tools, such as Azure DevOps boards and backlogs, to facilitate communication and collaboration.