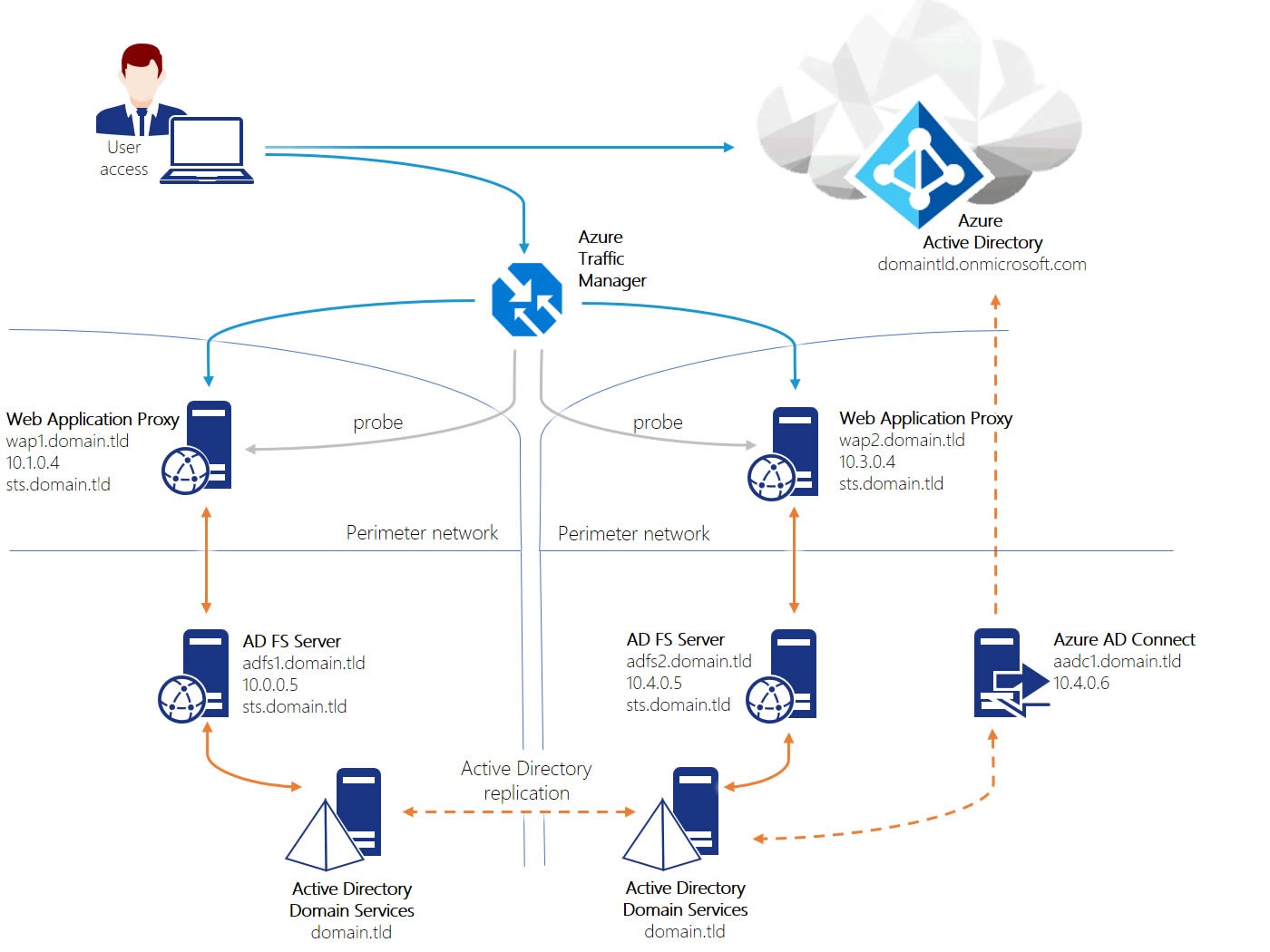
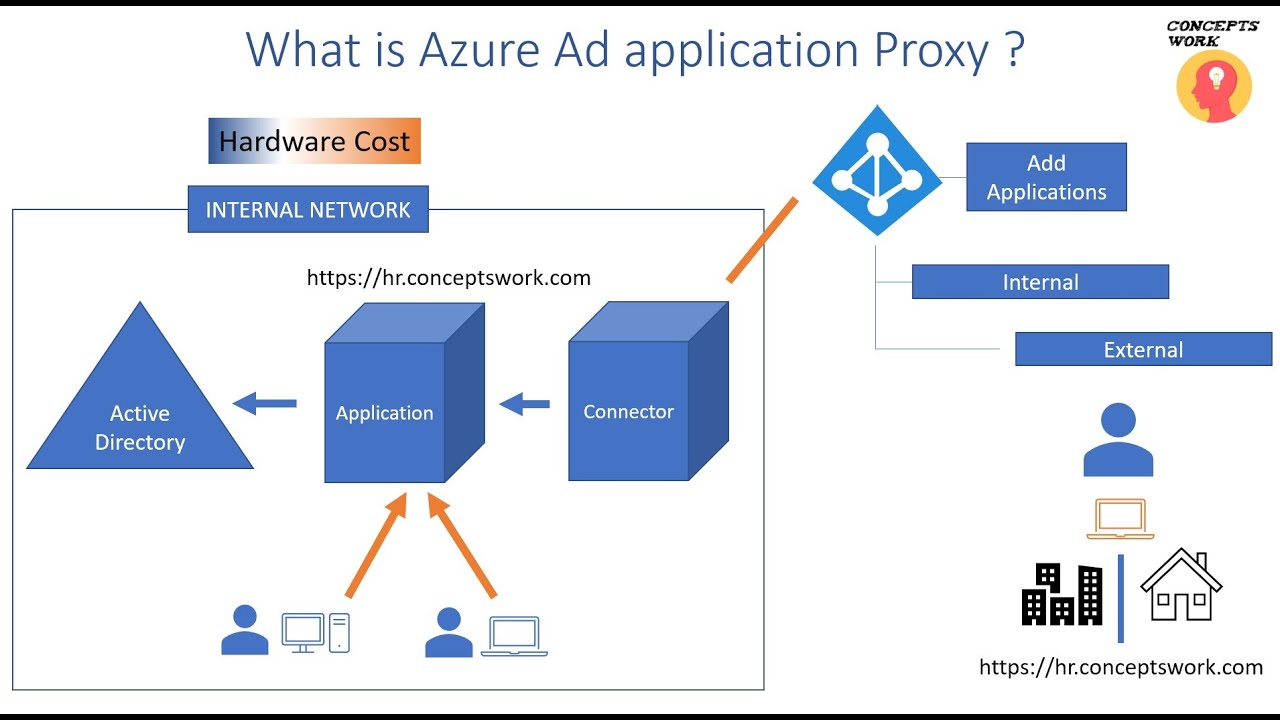
What are Azure AD Applications?
Azure Active Directory (Azure AD) applications are software programs that use Azure AD as their identity and access management solution. They are designed to operate in modern cloud-based architectures and offer numerous benefits over traditional applications. Azure AD applications enable organizations to manage user identities, authentication, and authorization in a centralized and secure manner. They support various authentication scenarios, including single sign-on, multi-factor authentication, and passwordless authentication. By using Azure AD applications, organizations can improve their security posture, reduce the risk of data breaches, and simplify user access to cloud-based resources.
Key Concepts and Terminologies
Azure AD applications are built on top of Azure AD, a cloud-based identity and access management service. Azure AD provides a set of core concepts and terminologies that are essential to understanding Azure AD applications. Authentication is the process of verifying the identity of a user or a device, while authorization is the process of granting or denying access to a resource based on the user’s or device’s identity and permissions. Conditional access is a security feature that uses access control policies to evaluate the risk level of a sign-in attempt and apply additional authentication requirements if necessary.
Azure AD applications support various authentication scenarios, including single sign-on (SSO), multi-factor authentication (MFA), and passwordless authentication. SSO enables users to access multiple applications with a single set of credentials, reducing the need to remember multiple passwords. MFA adds an extra layer of security by requiring users to provide a second form of authentication, such as a phone call, text message, or fingerprint. Passwordless authentication eliminates the need for passwords altogether, using alternative authentication methods such as biometrics or security keys.
Azure AD applications also support various authorization scenarios, including role-based access control (RBAC) and delegated permissions. RBAC enables organizations to assign roles and permissions to users based on their job responsibilities, while delegated permissions allow Azure AD applications to access specific resources on behalf of a user. By using RBAC and delegated permissions, organizations can ensure that users have the appropriate level of access to cloud-based resources and minimize the risk of data breaches.
How to Register an Azure AD Application
Registering an Azure AD application is a straightforward process that involves creating a new application, configuring redirect URIs, and generating client secrets. Here are the steps to register an Azure AD application:
-
Sign in to the Azure portal and navigate to the Azure Active Directory service.
-
Click on the “App registrations” section and then click on the “New registration” button.
-
Enter a name for the application, select the supported account types, and provide a redirect URI for the application.
-
Click on the “Register” button to create the application.
-
After the application is created, you can configure additional settings, such as adding credentials, creating client secrets, and configuring permissions.
Redirect URIs are used to specify the endpoint in the application that handles the response from Azure AD after the user is authenticated. Client secrets are used to authenticate the application with Azure AD when the application needs to access resources on behalf of a user. By configuring redirect URIs and generating client secrets, you can ensure that your Azure AD application is properly authenticated and authorized to access cloud-based resources.
Securing Azure AD Applications
Securing Azure AD applications is crucial to ensure the confidentiality, integrity, and availability of cloud-based resources. Here are some best practices for securing Azure AD applications:
-
Multi-factor authentication (MFA): MFA adds an extra layer of security to the authentication process by requiring users to provide a second form of authentication, such as a phone call, text message, or fingerprint.
-
Role-based access control (RBAC): RBAC enables organizations to assign roles and permissions to users based on their job responsibilities, reducing the risk of data breaches and unauthorized access.
-
Conditional access policies: Conditional access policies evaluate the risk level of a sign-in attempt and apply additional authentication requirements if necessary. For example, you can require users to authenticate using MFA when accessing sensitive resources from an untrusted network.
-
Least privilege principle: The principle of least privilege states that users should be granted the minimum level of access necessary to perform their job responsibilities. By following this principle, organizations can minimize the risk of data breaches and unauthorized access.
-
Monitoring and auditing: Monitoring and auditing Azure AD applications can help organizations detect and respond to security threats in a timely manner. Azure Monitor, Azure AD logs, and application insights can be used to monitor and troubleshoot Azure AD applications.
By following these best practices, organizations can ensure that their Azure AD applications are secure and compliant with industry standards and regulations. Additionally, regularly reviewing and updating security policies can help organizations stay ahead of emerging threats and maintain a strong security posture.
Integrating Azure AD Applications with Other Microsoft Services
Azure AD applications can be integrated with other Microsoft services to provide a seamless and secure user experience. Here are some ways to integrate Azure AD applications with other Microsoft services:
-
Microsoft Graph API: Microsoft Graph API is a unified API that enables developers to access Microsoft 365, Azure, and Enterprise Mobility + Security (EMS) data. By integrating Azure AD applications with Microsoft Graph API, developers can access user and group data, create and manage calendar events, and manage files and folders in SharePoint and OneDrive.
-
Microsoft Teams: Microsoft Teams is a collaboration platform that enables users to chat, meet, and collaborate on documents in real-time. By integrating Azure AD applications with Microsoft Teams, developers can create custom tabs, bots, and messaging extensions that can be used to automate workflows and enhance productivity.
-
SharePoint: SharePoint is a web-based collaboration platform that enables users to create and manage sites, documents, and lists. By integrating Azure AD applications with SharePoint, developers can create custom web parts, workflows, and event receivers that can be used to automate business processes and enhance collaboration.
Integrating Azure AD applications with other Microsoft services can provide numerous benefits, including increased productivity, improved security, and enhanced user experience. By using standard protocols such as OAuth 2.0 and OpenID Connect, developers can ensure that their Azure AD applications are secure and compliant with industry standards and regulations.
Monitoring and Troubleshooting Azure AD Applications
Monitoring and troubleshooting Azure AD applications is crucial to ensure their availability, performance, and security. Here are some tools and techniques for monitoring and troubleshooting Azure AD applications:
-
Azure Monitor: Azure Monitor is a monitoring service that enables developers to collect, analyze, and act on telemetry data from Azure resources. By integrating Azure AD applications with Azure Monitor, developers can monitor application performance, availability, and usage, and receive alerts when issues occur.
-
Azure AD logs: Azure AD logs provide detailed information about sign-in and audit activities in Azure AD. By analyzing Azure AD logs, developers can detect and respond to security threats, such as suspicious sign-in attempts, and investigate application issues, such as authentication failures.
-
Application Insights: Application Insights is a monitoring service that enables developers to monitor application performance, usage, and availability. By integrating Azure AD applications with Application Insights, developers can track user behavior, diagnose performance issues, and receive alerts when errors occur.
Monitoring and troubleshooting Azure AD applications can help developers identify and resolve issues in a timely manner, improve application performance and availability, and ensure a positive user experience. By using standard protocols such as OAuth 2.0 and OpenID Connect, developers can ensure that their Azure AD applications are secure and compliant with industry standards and regulations.
Real-World Examples of Azure AD Applications
Azure AD applications are used in various industries and scenarios to provide secure and seamless authentication and authorization. Here are some real-world examples of Azure AD applications:
-
Custom line-of-business applications: Azure AD applications can be used to build custom line-of-business applications that require user authentication and authorization. For example, a healthcare organization can build a custom application that enables doctors and nurses to access patient records securely.
-
SaaS applications: Azure AD applications can be used to integrate SaaS applications with Azure AD for single sign-on and user provisioning. For example, a company can use Azure AD to enable its employees to access Salesforce, Dropbox, and other SaaS applications with a single set of credentials.
-
Mobile applications: Azure AD applications can be used to authenticate and authorize users in mobile applications. For example, a retail company can build a mobile application that enables customers to browse and purchase products securely using Azure AD for authentication and authorization.
By using Azure AD applications, organizations can improve security, reduce IT costs, and enhance user experience. Azure AD applications provide a flexible and scalable solution for modern cloud-based architectures, enabling developers to build secure and innovative applications that meet the needs of their users and customers.
Future Trends and Developments in Azure AD Applications
Azure AD applications are constantly evolving to meet the changing needs of modern cloud-based architectures. Here are some future trends and developments in Azure AD applications:
-
Evolution of identity and access management: Identity and access management is becoming more complex with the increasing number of devices, users, and applications. Azure AD applications are expected to provide more sophisticated identity and access management features, such as adaptive authentication, risk-based access control, and biometric authentication.
-
Rise of zero trust security: Zero trust security is a security model that assumes that any user or device can be compromised. Azure AD applications are expected to adopt zero trust security principles, such as least privilege access, multi-factor authentication, and continuous monitoring, to provide more secure authentication and authorization.
-
Impact of emerging technologies: Emerging technologies, such as artificial intelligence and machine learning, are changing the way we interact with applications. Azure AD applications are expected to leverage these technologies to provide more personalized and intelligent user experiences, such as predictive analytics, natural language processing, and computer vision.
By staying up-to-date with the future trends and developments in Azure AD applications, developers can build innovative and secure applications that meet the needs of their users and customers. Azure AD applications provide a flexible and scalable solution for modern cloud-based architectures, enabling developers to build applications that are secure, intelligent, and user-friendly.