Exploring Microsoft Entra ID: A Deep Dive into User Management
Microsoft Entra ID, formerly known as Azure Active Directory, stands as the cornerstone of identity and access management for Microsoft’s expansive cloud ecosystem. This service acts as a central hub, orchestrating the intricate processes of user provisioning, authentication, and authorization. Understanding how to effectively manage azure active directory users is not merely an administrative task; it is a fundamental requirement for any organization leveraging Microsoft’s cloud services. Entra ID streamlines the creation and management of user identities, granting or restricting access to various resources based on defined roles and permissions. The goal is to ensure that the right users have the right level of access to the right resources, enhancing both security and operational efficiency. The management of azure active directory users is pivotal for maintaining a secure and well-organized digital environment. Without a firm grasp on the principles and practices of user management within Entra ID, organizations may face increased security risks, inefficiencies, and compliance issues. This article will provide a comprehensive overview of how to add, manage, and secure azure active directory users, providing you with the knowledge to maintain a well managed environment.
The importance of effectively managing azure active directory users cannot be overstated. In today’s complex cloud landscape, user identities serve as the primary gateway to sensitive information and applications. Microsoft Entra ID is designed to provide a flexible and scalable solution for handling these identities, making it possible to manage large numbers of azure active directory users. A deep understanding of the underlying concepts and the best practices for user management is important for any organization. Effective user management starts with a solid grasp of how to properly provision new user accounts, setting strong and secure passwords, and implementing multi-factor authentication protocols to fortify the security posture of the entire organization. Ignoring the importance of proper user management can expose an organization to numerous security vulnerabilities. Therefore, a strategic, well-implemented approach to azure active directory users ensures that only authorized personnel access vital data.
Furthermore, proper user management ensures operational efficiency by providing an easier way to organize your digital workspace. For example, user attributes can be utilized to organize users by department, job title, and other relevant criteria, simplifying the processes of locating, managing and reporting users. Effective management also entails ensuring that user accounts are handled properly when employees leave, with robust processes for deactivating or deleting accounts in a secure and timely manner. This minimizes the risk of unauthorized access by former employees. Efficient group management in Entra ID is also an essential skill as it can reduce management time when assigning permissions or access rights. Regular auditing and reporting of user activity is another key aspect of maintaining good security protocols. Ultimately, understanding how to manage azure active directory users effectively translates to more efficient operations, reduced security risks, and enhanced regulatory compliance, which are crucial for modern organizations.
How to Add New Users to Your Azure Entra ID Tenant
Adding new users to your Azure Entra ID tenant, formerly known as Azure Active Directory, is a straightforward process achievable through several methods catering to various administrative needs. One common approach involves manual user creation directly within the Azure portal. This method offers granular control, allowing administrators to specify all user attributes individually. To begin, navigate to the Azure portal and locate the Azure Active Directory service. Then, select “Users,” followed by “All users,” and finally click “New user.” A form will appear prompting for necessary details such as the user’s name, display name, user principal name (UPN), and contact information. Remember to assign a strong password, or opt for passwordless authentication methods for enhanced security. Once completed, the newly created user will appear in the list of all users within your Azure Active Directory users management section. This manual approach is ideal for adding a small number of users. Efficient management of azure active directory users is crucial for maintaining a secure and productive environment.
For organizations needing to onboard numerous users simultaneously, bulk import via CSV file is a significantly more efficient method. This approach involves creating a CSV file adhering to a specific format, containing all the necessary user attributes. Azure Active Directory provides detailed documentation outlining the required format and acceptable attribute values. After preparing the CSV file, return to the Azure portal’s user management section. Instead of manually creating individual users, select the option to import users from a CSV file. Upload the prepared file, and Azure Active Directory will process it, creating user accounts based on the provided data. This method significantly reduces administrative overhead, particularly beneficial for organizations with frequent user onboarding processes. This streamlined approach ensures consistency and accuracy when adding multiple azure active directory users at once. Careful attention to data integrity during CSV preparation is paramount to avoid errors and ensure all users are successfully added to the tenant.
Finally, for advanced users and automation enthusiasts, the Microsoft Graph API offers programmatic control over user provisioning. Using this API, you can integrate user creation into existing workflows or scripts, ensuring seamless integration with other systems. This method requires a basic understanding of REST APIs and authentication protocols. The Microsoft Graph API documentation provides comprehensive details on available endpoints and required permissions. This programmatic approach allows for highly customized and automated user provisioning, fitting seamlessly into sophisticated IT infrastructures. Organizations leveraging the Microsoft Graph API can build robust and scalable solutions for managing azure active directory users, ensuring agility and efficiency in user management. Remember that proper authentication and authorization are vital when using the API to prevent unauthorized access and maintain the security of your Azure Active Directory users.
User Attributes: Customizing User Profiles in Microsoft Entra ID
Microsoft Entra ID, formerly known as Azure Active Directory, offers a rich set of user attributes that allow for detailed customization of user profiles. These attributes go beyond basic information like name and email address, providing a powerful mechanism for organizing, searching, and reporting on azure active directory users. Understanding and effectively utilizing these attributes is crucial for efficient user management and maintaining a well-organized directory. Attributes such as department, job title, location, manager, cost center, and various contact details can be readily configured. The ability to add custom attributes further enhances the flexibility, enabling organizations to tailor their user profiles to their specific needs and workflows. Properly configured user attributes significantly improve the effectiveness of searching for specific users or groups of users, streamlining processes like assigning permissions or generating reports based on specific criteria. For instance, a company might utilize custom attributes to track employee certifications, allowing for easy identification of individuals qualified for particular projects or roles. This level of detail empowers organizations to make informed decisions based on comprehensive user data.
Accurate user attributes are paramount for maintaining a well-organized directory and ensuring the success of various organizational processes. Efficient searching and filtering of azure active directory users depend heavily on the completeness and accuracy of these attributes. Imagine the difficulty of finding a specific employee without a clearly defined department or location. Inaccurate or missing attributes hamper reporting capabilities, making it challenging to generate meaningful insights about the workforce. Furthermore, appropriate attribute management is pivotal for compliance with internal policies and external regulations. Maintaining consistent and reliable user information minimizes discrepancies and ensures accurate reporting for auditing purposes. Consider a scenario where a company needs to generate a report on all employees in a specific geographical location; precise location attributes are essential for accurate reporting. Similarly, accurate job title information is necessary for effective resource allocation and project management. Therefore, the importance of meticulous attention to detail when managing user attributes cannot be overstated.
Beyond the core attributes, Microsoft Entra ID allows administrators to add custom attributes to further enhance the granularity and specificity of user profiles. This empowers organizations to tailor their user management system to their specific requirements, enriching the data available for analysis and reporting. For example, an organization might use custom attributes to track employee skills, project assignments, or security clearances. This flexibility allows for creating detailed user profiles that cater to the unique needs of various business functions. By leveraging the full potential of user attributes within Microsoft Entra ID, organizations can significantly improve their operational efficiency, enhance reporting capabilities, and ensure better compliance with internal policies and external regulations. The ability to define and manage these attributes effectively is a cornerstone of successful user management for azure active directory users and overall organizational success. Careful planning and consistent maintenance of user attributes are vital for maximizing the benefits offered by the comprehensive user profile capabilities within Microsoft Entra ID.
Managing User Passwords and Security Settings in Microsoft Entra ID
Robust password management is paramount for securing Azure Active Directory users and the entire Microsoft cloud environment. Microsoft Entra ID offers several features to enhance password security and control. Password policies can be customized to enforce complexity requirements, such as minimum length, character types (uppercase, lowercase, numbers, symbols), and password expiration periods. Regularly reviewing and updating these policies is crucial to maintaining a strong security posture. For example, enforcing a minimum password length of 12 characters and requiring a mix of character types significantly reduces the risk of brute-force attacks. Moreover, integrating Microsoft Entra ID with other security solutions can further improve password management. This includes leveraging tools that provide password monitoring and alerting, helping detect and respond to potential compromises effectively.
Multi-factor authentication (MFA) is a critical security layer that adds an extra level of protection beyond just a password. Enabling MFA for all Azure Active Directory users significantly reduces the risk of unauthorized access, even if passwords are compromised. Microsoft Entra ID supports various MFA methods, including authenticator apps, security keys, and phone calls, allowing organizations to choose the most suitable options for their users. The configuration of MFA is relatively straightforward within the Entra ID administration portal, and implementing it should be a top priority for all organizations. Properly configured MFA drastically reduces the impact of phishing and other social engineering attacks that target user credentials. By enforcing MFA, organizations demonstrate their commitment to robust security practices, thereby protecting sensitive data and maintaining user trust.
Beyond password policies and MFA, Azure Active Directory users benefit from other security features. Regular security reviews and audits are essential to identify vulnerabilities and implement necessary mitigations. This includes regularly checking for inactive or compromised accounts, and promptly disabling or deleting those that are no longer needed. Furthermore, leveraging conditional access policies allows organizations to define granular access controls based on various factors like location, device, and user risk. This ensures that only authorized users can access resources from approved locations and devices, preventing unauthorized access attempts. Properly managing user accounts and applying these security features are key elements in establishing and maintaining a robust and secure environment for Azure Active Directory users. This proactive approach to security significantly minimizes risks, protects valuable data, and enhances overall organizational security posture.
User Lifecycle: Disabling, Deleting, and Restoring User Accounts
The management of azure active directory users extends beyond their creation; it also includes their lifecycle management, specifically disabling, deleting, and restoring accounts. Disabling a user account is often the first step when an employee leaves an organization or their access needs to be temporarily revoked. This action prevents the user from logging in, while maintaining their user data and account information. It is important to understand the difference between disabling and deleting an account. A disabled account is inactive but can be easily reactivated with its data intact. The process for disabling an azure active directory users account is straightforward through the Azure portal or via PowerShell commands. Navigating to the user’s profile, an administrator can change the sign-in status to ‘blocked’, effectively stopping the user from accessing any organization resources. This allows administrators to take time to review access permissions before a permanent deletion.
Deleting an azure active directory users account, on the other hand, removes the user and their associated data from the tenant after a waiting period. This action is usually irreversible; therefore, caution should always be exercised, and it is advised to back up any critical user data before initiating deletion. When an account is deleted, its resources and associated data are permanently removed from the active directory system after 30 days. This process ensures that all information is completely removed after a reasonable retention period, providing a security measure to prevent data breaches or accidental access to a former employee’s data. It’s also crucial for compliance with company data policies and legal regulations. Understanding the nuances of deactivation versus deletion for azure active directory users is vital for maintaining a clean, efficient and secure environment.
Restoring a deleted azure active directory users account is possible within the 30-day grace period before its permanent removal. If a deleted account needs to be restored, administrators can easily find the deleted user within the ‘deleted users’ section in the Azure portal. This action will restore the user, along with all previous user information, including their associated groups and application access. However, if the 30-day period has expired, the user account will be permanently purged, and it cannot be recovered. For scenarios where the account has been permanently deleted, a new user account would need to be created. This would require setting up the account with the necessary permissions and reconfiguring the access to organization resources. Therefore, the restoration feature serves as a critical safeguard, enabling recovery from accidental deletions while also reinforcing best practices of account management within Microsoft cloud services, further emphasizing the need for careful azure active directory users administration.
Utilizing Groups for Efficient User Administration
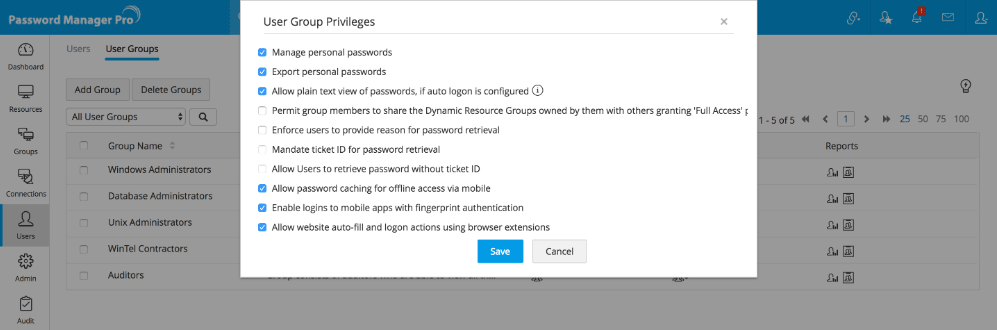
Microsoft Entra ID, formerly known as Azure Active Directory, provides powerful features for managing not only individual azure active directory users but also user groups, significantly streamlining administrative tasks. Groups in Entra ID allow administrators to manage permissions and access rights for multiple users simultaneously, rather than managing each user separately. This method of user management reduces the administrative workload and ensures consistency in access control. Entra ID supports both static and dynamic groups. Static groups are manually populated with users, requiring ongoing manual updates to add or remove members. This approach is suitable when membership changes are infrequent and based on specific criteria. Dynamic groups, on the other hand, automatically add or remove users based on defined rules, such as department or location attributes. This eliminates the need for manual updates and ensures that group membership is always accurate and reflects the current user attributes. Dynamic groups are especially beneficial in large organizations or those with frequent personnel changes, where managing azure active directory users can become an overwhelming task. Employing groups facilitates easier management of permissions across all applications and resources, improving operational efficiency and reducing the risk of errors.
Creating and managing groups effectively is a critical skill for efficient Entra ID administration. When creating a group, administrators must carefully plan the criteria for membership, as this choice will impact the maintenance of user access rights. For instance, a group can be configured to include all users within a specific department, automatically granting them access to the resources and applications required for that group. When a new user joins the department, they are automatically added to the group, and inherit the associated permissions, removing a step in the onboarding process. Similarly, leaving the department will also remove permissions automatically, thereby simplifying de-provisioning. By assigning permissions to groups instead of individual azure active directory users, administrators reduce the complexity of permission management. Group-based permission management ensures that user access remains aligned with their organizational role, improving compliance and governance. Using groups promotes consistent application of security policies, reducing the risk of security gaps and unauthorized access. The ability to manage many azure active directory users through a single group interface enhances the overall management experience. This streamlined approach to permissions and group management offers a far more efficient system than having to configure the same permissions individually across numerous user profiles.
Reporting and Auditing User Activities in Microsoft Entra
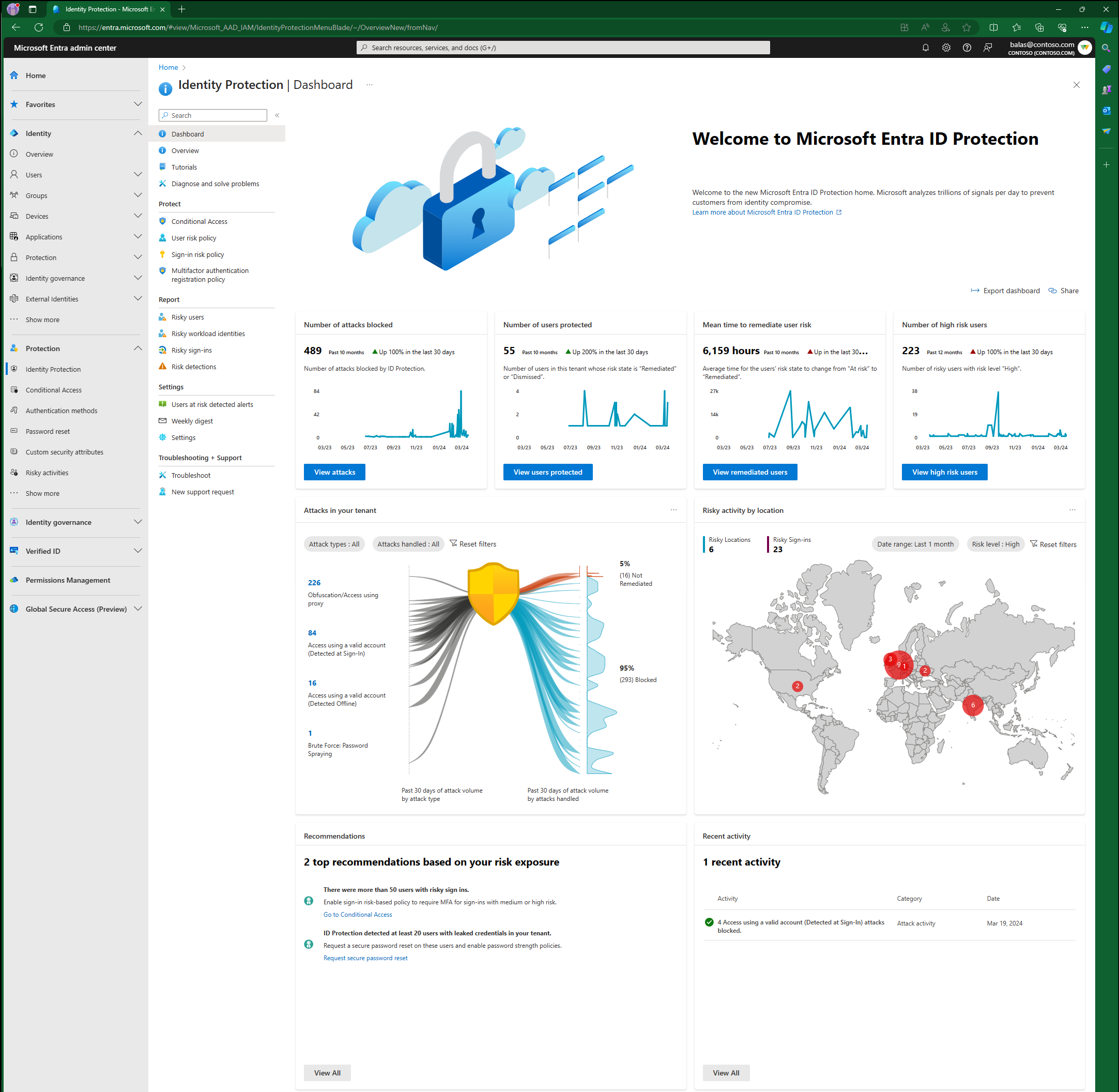
Microsoft Entra ID (formerly Azure Active Directory) offers robust auditing capabilities to monitor user activities and maintain a secure environment. Administrators can leverage these audit logs to track various events related to azure active directory users, including login attempts, password resets, group membership changes, and modifications to user profiles. This comprehensive audit trail is invaluable for security monitoring, compliance efforts, and troubleshooting. Regularly reviewing these logs helps identify potential security threats, such as unauthorized access attempts or suspicious account modifications. By analyzing the data within the audit logs, organizations can proactively address vulnerabilities and improve their overall security posture. The ability to filter and search audit logs based on specific criteria allows for efficient investigation of security incidents and provides crucial data for security incident response processes. Understanding the available audit log data is critical for effectively managing azure active directory users and maintaining a secure and compliant environment. The detailed information recorded helps pinpoint the source of security breaches and prevents future incidents.
Accessing and interpreting Microsoft Entra ID audit logs is straightforward. The Azure portal provides a user-friendly interface to navigate and filter the audit logs. Administrators can easily view a detailed history of user activities, including timestamps, user identities, and the specific actions performed. This allows for granular analysis of user behavior and the identification of anomalous patterns. Key features such as the ability to download audit logs in various formats (like CSV) facilitate further analysis using external security information and event management (SIEM) systems. Analyzing this data alongside other security logs can provide a holistic view of the organization’s security posture, highlighting potential threats and vulnerabilities. For example, a spike in failed login attempts from a specific IP address could indicate a potential brute-force attack. This information is crucial for taking prompt action to mitigate the threat and protect azure active directory users and sensitive organizational data. Effective use of the audit logs significantly enhances the organization’s ability to detect and respond to security incidents, minimizing their impact and upholding compliance standards. The granular level of detail available empowers informed decision-making and contributes to a robust security strategy.
Beyond simply reacting to security events, proactive monitoring of audit logs in Microsoft Entra ID helps optimize user management processes. By tracking changes in password policies and user account modifications, administrators can identify areas for improvement. For example, an unusually high number of password reset requests might indicate a need to review and refine password complexity policies. Similarly, analyzing user account creation and deletion patterns can reveal areas for process optimization. Moreover, the audit logs play a vital role in demonstrating compliance with various regulatory frameworks that mandate the tracking and auditing of user activities. By maintaining thorough and accessible audit logs, organizations can confidently demonstrate their adherence to relevant compliance standards and regulations, protecting both azure active directory users and the organization from potential legal and financial repercussions. Regular review and analysis of these logs are essential for a proactive and robust security posture.
Troubleshooting Common User Management Issues in Azure Active Directory
Managing Azure Active Directory users often presents challenges. One common issue is login failures. These can stem from incorrect passwords, account lockouts due to multiple failed login attempts, or problems with multi-factor authentication (MFA). To troubleshoot login failures, first verify the user’s password using the password reset functionality. If the password is correct, check for MFA enrollment and ensure the user has properly configured their MFA method. If MFA is enabled and the user is experiencing issues, review the MFA settings and troubleshoot the specific MFA method being used. Account lockouts can be resolved by unlocking the account through the Azure portal, ensuring the user can then log in with the correct credentials. Examining the Azure AD audit logs can pinpoint the exact cause of the login failure, offering valuable insights for future prevention. Understanding these processes is crucial for efficient management of azure active directory users.
Another frequent problem involves password resets. Users may forget their passwords, requiring administrators to intervene. Azure AD provides self-service password reset capabilities, empowering users to reset their passwords independently, reducing the administrative burden. However, administrators should carefully configure self-service password reset policies, ensuring they adhere to security best practices and organizational guidelines. This includes setting appropriate password complexity requirements and configuring suitable password reset options. If self-service password reset is unavailable or fails, administrators can intervene by manually resetting the user’s password, carefully documenting this action for auditing purposes. Remember to enforce strong password policies and regularly communicate password security best practices to users to minimize the frequency of password-related issues. Effective management of azure active directory users necessitates strong password policies coupled with readily available reset mechanisms. Proper configuration of self-service password reset is a critical aspect of this.
Finally, challenges can arise with group assignments. Incorrect group memberships can lead to access issues, where users lack permissions to access necessary resources. To resolve these issues, administrators should thoroughly review group memberships using the Azure AD portal or PowerShell. Verifying that users belong to the correct groups is paramount. If a user is missing from a required group, add them accordingly. Conversely, remove users from groups they no longer need to access. Regularly auditing group memberships and ensuring accuracy is essential for maintaining a secure and efficient environment. This proactive approach to group management significantly contributes to the smooth operation of the organization and prevents access-related problems for azure active directory users. Furthermore, understanding the dynamics of group management and its impact on permissions is a key skill for efficient user administration.