Understanding Azure Private DNS Zones
Azure Private DNS Zones offer a secure and efficient way to manage internal name resolution within a virtual network. Unlike public DNS, which is accessible globally, Private DNS zones are confined to your Azure virtual network. This isolation enhances security by preventing unauthorized access to internal DNS records. Using Private DNS simplifies management. It eliminates the need for managing separate DNS servers for your internal network. Azure Private DNS provides several benefits, including improved security, simplified management, and enhanced performance. Consider scenarios such as microservices communication and internal application access. In these situations, Private DNS is crucial for maintaining a secure and efficient internal network. Adding an A record, a fundamental step in managing DNS records within Azure Private DNS Zones, is essential for establishing internal name resolution. The process of adding an az network private-dns record-set a add-record is straightforward and provides a foundational understanding of managing DNS within Azure’s ecosystem. Efficiently managing your az network private-dns record-set a add-record ensures secure internal communication.
Private DNS zones are particularly valuable for organizations operating multiple applications and services within an Azure virtual network. They allow for the creation of a consistent and secure naming scheme, thereby improving the overall manageability of the environment. The ability to control access to DNS records is another significant advantage. This helps to prevent unauthorized access and maintain the security of the internal network. When designing your network, careful consideration should be given to how you will integrate Private DNS with other Azure services and resources. Understanding how Private DNS interacts with other Azure services is key to efficiently managing and securing your internal infrastructure. Successfully integrating Private DNS into your Azure environment requires proper planning and an understanding of best practices. Adding an az network private-dns record-set a add-record is a common task in this process, and understanding the nuances is vital for a smoothly operating internal network.
The ability to manage DNS records securely and efficiently is a critical aspect of maintaining a healthy and secure internal Azure environment. Azure Private DNS provides the necessary tools and functionality to achieve this goal. Consider the security implications of exposing internal DNS records to the public internet. The use of Private DNS mitigates these risks by restricting access to authorized users and services within your Azure Virtual Network. Organizations using multiple virtual networks can leverage virtual network links to connect their Private DNS zones. This allows for consistent and secure name resolution across multiple virtual networks. Mastering the process of adding an az network private-dns record-set a add-record, alongside other DNS record management tasks, is a vital skill for Azure network administrators. Properly managing your DNS records ensures reliable communication between internal services and applications, improving overall network efficiency and security.
How to Add an A Record to Your Azure Private DNS Zone
Adding an A record to your Azure Private DNS zone is a straightforward process. First, access the Azure portal. Navigate to your resource group, then locate the Private DNS zone you wish to modify. Click on the zone. You’ll then see a list of DNS records. Click the “+ Add” button to create a new record. Select “A” as the record type. The “az network private-dns record-set a add-record” command is useful in scripting this process, though this guide focuses on the portal method. Next, enter the fully qualified domain name (FQDN) for your A record. This is the name you want to resolve. For example, if you want to resolve `webserver.contoso.local`, you would enter that as the FQDN. Finally, specify the IP address that this FQDN should resolve to. Click “OK” or “Save” to finalize the changes. Azure will now propagate these changes.
Successful completion adds the new A record to your private DNS zone. Your internal applications and services can now resolve this FQDN to the specified IP address. Remember that improperly configuring your resource group or virtual network association can cause issues. Ensure your virtual network is properly linked to the private DNS zone for seamless internal name resolution. The `az network private-dns record-set a add-record` command provides an alternative method. While the portal offers a visual interface, this command is beneficial for automation and scripting. Always validate your configuration to prevent connectivity problems. Double-check your FQDN and IP address before saving your work.
Troubleshooting is simplified with careful attention to detail. If you encounter errors, review the FQDN and IP address for typos or inconsistencies. Ensure the virtual network is correctly associated with the private DNS zone. If resolution issues persist, check the network connectivity between your virtual machines and the DNS server. The `az network private-dns record-set a add-record` command, when used correctly, can greatly simplify the process and minimize potential errors. Moreover, understanding DNS propagation times is crucial; allow sufficient time for changes to take effect throughout your Azure environment. Efficient management involves regular record review and proactive maintenance. Properly managing your Azure Private DNS zones improves the reliability and security of your internal infrastructure. The `az network private-dns record-set a add-record` command helps streamline this process, promoting a more automated and efficient workflow for your organization’s DNS operations.
Choosing the Right Resource Group and Virtual Network
Selecting the appropriate resource group and virtual network is crucial for managing Azure Private DNS zones effectively. The resource group organizes related Azure resources. Choosing a logical grouping simplifies management and allows for easier deletion or movement of resources. For example, grouping all resources related to a specific application within one resource group improves organization. Incorrect resource group selection doesn’t directly impact DNS functionality but makes administration less efficient. The virtual network (VNet) is where the private DNS zone resolves names. The VNet provides the scope for name resolution. A private DNS zone created within a VNet only resolves names for resources within that VNet or VNets linked to it. This isolation is essential for security. Associating a private DNS zone with the incorrect VNet leads to connectivity issues. Internal applications might fail to resolve names. This can cause significant operational problems. Careful planning ensures seamless name resolution and optimized management of your az network private-dns record-set a add-record.
Consider the impact of scaling. As your environment grows, resource group and VNet choices influence scalability and manageability. Well-defined resource groups ensure that adding new resources, such as virtual machines, remains organized. The choice of virtual network impacts the scope of DNS resolution. If you need to resolve names across multiple VNets, you will need to consider using virtual network links or other connectivity solutions. Failing to account for these factors during initial setup can lead to complex and costly changes in the future. Selecting the correct virtual network is crucial when adding an az network private-dns record-set a add-record. Ensure the network is properly configured for DNS resolution. Incorrect configuration may result in failed DNS lookups. This will impact application functionality.
Properly configuring virtual network peering can extend the reach of your private DNS zone. This allows for name resolution across multiple VNets, improving efficiency and reducing complexity. However, misconfiguration can lead to security vulnerabilities. Carefully review security settings and access controls when configuring VNets and resource groups. This will safeguard your network and ensure that only authorized users can access sensitive information. Before adding any az network private-dns record-set a add-record, verify that the VNet is correctly peered with other VNets, if necessary, for seamless name resolution across your environment. This meticulous approach will ensure robust and secure name resolution within your Azure environment.
Best Practices for Private DNS Zone Management
Maintaining secure and efficient Azure Private DNS zones requires adherence to best practices. Employing a consistent naming convention simplifies management and reduces errors. This includes using descriptive names that clearly indicate the purpose of each record. Regularly reviewing existing records ensures accuracy and identifies outdated entries. Deleting unnecessary records minimizes complexity and improves performance. This proactive approach is crucial for preventing conflicts and maintaining optimal functionality. Remember to add the az network private-dns record-set a add-record command as part of your regular operational procedures.
Implementing robust access control lists (ACLs) is paramount for securing Private DNS zones. Restrict access to only authorized users and services. Leverage Azure role-based access control (RBAC) to grant granular permissions. This minimizes the risk of unauthorized modifications or deletions. Regularly audit these permissions to ensure they remain appropriate and effective. Using Azure Policy allows organizations to define and enforce consistent security and governance standards across multiple DNS zones. This automation feature helps maintain a high level of security and compliance while reducing the manual effort required for configuration and monitoring. Implementing these policies ensures consistent application of best practices and simplifies auditing processes. Efficient management of your az network private-dns record-set a add-record process contributes to overall security.
Proactive monitoring is essential for identifying and resolving potential issues. Regularly check DNS resolution times. Monitor for any anomalies in traffic patterns. This helps detect potential security breaches or performance degradation. Integrating monitoring tools with your existing infrastructure facilitates efficient problem identification and resolution. Using Azure Monitor allows you to collect and analyze logs, metrics, and traces. This provides valuable insights into the health and performance of your Private DNS zones, aiding in predictive maintenance and proactive issue resolution. The efficient use of az network private-dns record-set a add-record commands within a well-structured monitoring system is vital to ensure smooth operation and efficient troubleshooting. Consider implementing automated alerts to promptly address any identified issues or deviations from established baselines, which can significantly reduce downtime and maintain optimal system performance.
Troubleshooting Common Azure Private DNS Issues
Troubleshooting Azure Private DNS problems often involves verifying network connectivity and DNS configuration. DNS resolution failures frequently stem from incorrect record entries within the az network private-dns record-set a add-record process. Double-check that the FQDN and IP address are accurate. Ensure the virtual machine or service attempting resolution is properly connected to the virtual network associated with the private DNS zone. Network security groups (NSGs) can sometimes block DNS traffic; review NSG rules to ensure they permit DNS queries and responses on the appropriate ports (typically UDP port 53 and TCP port 53). Confirm that the virtual network is correctly linked to the private DNS zone. When adding an A record, remember that the ‘az network private-dns record-set a add-record’ command requires precise parameters. A wrongly configured record will cause resolution failures. Check the DNS server settings on your virtual machines. They should be configured to use the private DNS zone’s IP addresses. Review the Azure Private DNS zone’s integration with any connected virtual networks, ensuring proper propagation of DNS records.
Connectivity issues can originate from misconfigured virtual network peering or network security group rules. Verify that peering between relevant virtual networks is properly established and that appropriate NSG rules allow communication between them. Examine the routing tables of the virtual networks; incorrect routes can prevent DNS queries from reaching the intended DNS servers. Examine any load balancers that might be intercepting or modifying DNS traffic. If connectivity problems persist after verifying these elements, consider using network monitoring tools like Azure Network Watcher to pinpoint the source of the connectivity issue. Remember, correctly adding an A record using ‘az network private-dns record-set a add-record’ is crucial for resolving connectivity issues. Ensure the correct virtual network is linked to the Private DNS zone.
Authentication problems, less common, usually relate to virtual machine identity and access control. If a virtual machine cannot resolve names, check its identity and access settings. Confirm that the virtual machine has the necessary permissions to query the private DNS zone. Review any Azure Active Directory (Azure AD) configurations or role-based access control (RBAC) settings that might be restricting access. If using Azure AD authentication, ensure that the correct credentials are configured and that the virtual machine can authenticate successfully. Properly configured DNS settings are critical, especially when performing an az network private-dns record-set a add-record operation; problems with authentication can lead to resolution failures. Carefully check all authentication-related settings.
Integrating Private DNS with Other Azure Services
Azure Private DNS seamlessly integrates with various Azure services, simplifying management and enhancing security. When adding an A record to your az network private-dns record-set, consider how this impacts your overall Azure infrastructure. For instance, Azure Virtual Machines (VMs) readily leverage Private DNS for internal name resolution. Instead of using public IP addresses, VMs can resolve hostnames within the private DNS zone, improving security and manageability. This streamlined approach simplifies configurations and reduces the risk of exposing internal resources to the public internet. Efficiently managing the az network private-dns record-set a add-record process is crucial for smooth integration. Proper configuration ensures that VMs can easily communicate with each other and other internal services.
Similarly, Azure Kubernetes Service (AKS) benefits significantly from Private DNS. AKS clusters use Private DNS to resolve service names and pod names within the cluster. This improves the resilience and security of your AKS applications. The az network private-dns record-set a add-record command plays a vital role in defining internal services, enabling seamless communication between pods and services within the AKS cluster. This approach ensures that communication remains entirely internal, improving security and performance. The process of adding an A record to your az network private-dns record-set should be carefully planned to align with your AKS architecture.
Azure App Service also integrates well with Private DNS. Web apps and other App Service resources can use Private DNS for internal name resolution. This allows internal services to communicate securely with each other without exposure to the public internet. To add an A record to your az network private-dns record-set, developers must understand the naming conventions and configurations specific to App Service. This secure, internal communication method enhances the overall security posture of your application infrastructure and improves its resilience. Using Private DNS with App Service simplifies the management of complex applications by providing a consistent naming scheme and enabling internal communication.
Understanding DNS Record Types Beyond A Records
While A records are fundamental for mapping hostnames to IPv4 addresses, Azure Private DNS supports several other crucial record types. Understanding these expands the capabilities of your private DNS infrastructure and is key for comprehensive network management. Adding these records is similar to adding an A record, however, the record type selected determines the associated data. The az network private-dns record-set a add-record command focuses on A records; however, other commands exist for other record types.
CNAME (Canonical Name) records, for example, alias one domain name to another. This simplifies management, as changes to the target only need to be made in one place. This is particularly useful for managing multiple services under a single overarching name. PTR (Pointer) records map an IP address to a hostname, essential for reverse DNS lookups and security analysis. MX (Mail Exchanger) records specify mail servers for a domain, crucial for email routing within your private network. Proper use of these records, in conjunction with effectively managing A records using the az network private-dns record-set a add-record command, enhances the security and efficiency of your Azure Private DNS infrastructure. Consider these additional record types when designing your private DNS zone for optimal function.
Mastering various record types beyond the basic A record, including CNAME, PTR, and MX records, is crucial for building a robust and reliable private DNS infrastructure. Effective use of these records enhances the overall functionality and security of your network. Understanding the nuances of these record types, combined with skillful application of commands such as az network private-dns record-set a add-record for A records, allows for comprehensive and granular control of internal name resolution within Azure’s private DNS environment. This advanced knowledge contributes to a well-structured, secure, and efficient private network.
Advanced Private DNS Configurations and Scenarios
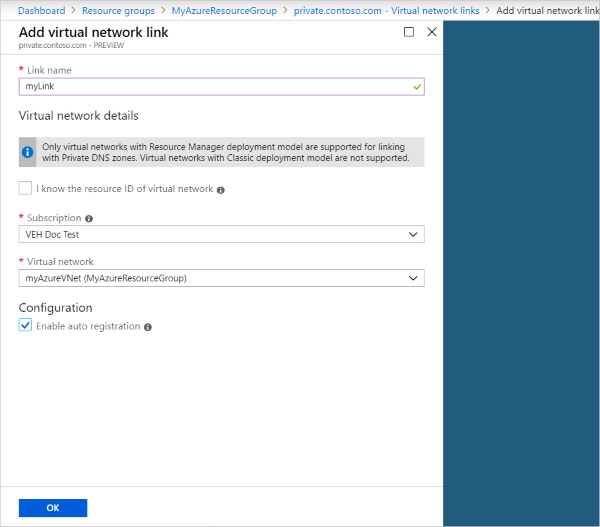
Azure Private DNS offers advanced features beyond basic record creation. Connecting multiple virtual networks, a common requirement in complex deployments, is simplified using virtual network links. This allows consistent name resolution across disparate network segments. Proper configuration of virtual network links is crucial for seamless communication and efficient resource management. Remember to carefully plan your virtual network topology before implementing these links to avoid connectivity issues. Adding an A record within this extended network requires navigating to the relevant zone within the linked network. This process is similar to adding an az network private-dns record-set a add-record in a single virtual network, but understanding the link’s configuration is essential for success. Using the Azure portal, or the Azure CLI, you can easily manage these links and associated record sets.
Enhanced security is achievable through Azure Private Endpoint. This feature allows secure access to Azure services, such as Azure SQL Database or Azure Storage, without exposing them to the public internet. Private Endpoint integrates seamlessly with Private DNS, enabling secure name resolution within your virtual network. The Private Endpoint leverages a private IP address, eliminating the need for public IP addresses and enhancing security. When integrating Private Endpoint with your Private DNS zone, you will utilize private IP addresses when configuring az network private-dns record-set a add-record. This ensures your applications only communicate with the service through the private network. This approach reduces the attack surface and adds an extra layer of security to your infrastructure. Properly configuring the Private Endpoint and ensuring it’s correctly linked to your Private DNS zone is key to gaining these benefits.
Another advanced scenario involves leveraging Azure Policy to enforce consistent naming conventions and security settings across multiple Private DNS zones. This ensures compliance and simplifies management. Azure Policy allows administrators to define rules that automatically govern the creation and modification of DNS records, thereby improving security and reducing human error. For example, you can use Azure Policy to restrict the creation of A records with certain IP address ranges or enforce specific naming conventions. This helps ensure consistency and reduces the risk of misconfigurations. When creating a new az network private-dns record-set a add-record, these policies provide an extra layer of validation to prevent potential issues. This proactive approach minimizes security vulnerabilities and enhances overall manageability across the Azure environment. The proper configuration of these policies is fundamental to successfully managing your Private DNS infrastructure.