Understanding AWS VPC: A Key Component of AWS Networking
Amazon Web Services Virtual Private Cloud (AWS VPC) is a fundamental networking component in the AWS cloud that provides users with the ability to securely manage and scale their virtual networks. By creating a VPC, users can define a virtual network topology that closely resembles a traditional on-premises network, with features such as subnets, route tables, network gateways, and security controls. This article aims to provide a comprehensive overview of AWS VPC, including its key concepts, benefits, and best practices for creating and configuring a secure and scalable virtual network infrastructure.
At its core, AWS VPC is a logical network abstraction that allows users to define and manage their virtual network resources within the AWS cloud. By creating a VPC, users can isolate their network resources from the public internet, providing an additional layer of security and control over their network traffic. Moreover, AWS VPC enables users to create multiple isolated networks within the same AWS account, allowing for the creation of separate network environments for development, testing, and production workloads.
One of the primary benefits of using AWS VPC is its ability to provide users with a high degree of control and customization over their network infrastructure. For example, users can define their own IP address ranges, create subnets for different network purposes, and configure route tables to control the flow of network traffic. Additionally, users can implement security controls such as network access control lists (NACLs) and security groups to restrict access to their network resources, providing an additional layer of security and control.
In summary, AWS VPC is a powerful networking component in the AWS cloud that provides users with the ability to create and manage secure and scalable virtual network infrastructures. By understanding the key concepts and best practices associated with AWS VPC, users can take full advantage of its features and capabilities, enabling them to build and deploy highly available and secure network environments for their workloads.
Key Concepts and Terminologies in AWS VPC
To fully understand and effectively use AWS VPC, it is essential to familiarize oneself with the key concepts and terminologies associated with it. This section will define and explain some of the most important terms related to AWS VPC, including VPC, subnet, route table, Internet Gateway, NAT Gateway, security group, and network access control list (NACL).
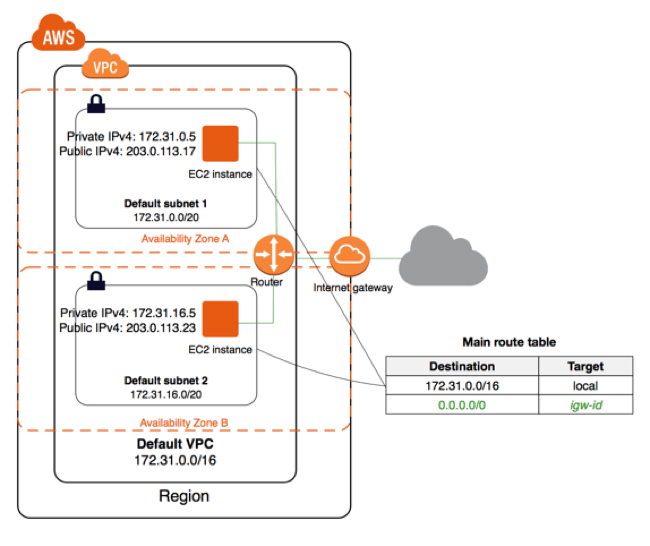
VPC
A Virtual Private Cloud (VPC) is a logical network abstraction that allows users to define and manage their virtual network resources within the AWS cloud. A VPC can be thought of as a virtual data center that provides users with complete control and customization over their network infrastructure.
Subnet
A subnet is a smaller network segment within a VPC that allows users to group and isolate their network resources. Subnets can be used for different network purposes, such as isolating development, testing, and production workloads, or grouping resources based on their security requirements.
Route Table
A route table is a set of rules that determine how network traffic is routed within a VPC. Route tables can be associated with one or more subnets and contain rules that specify which network traffic should be forwarded to which network destination.
Internet Gateway
An Internet Gateway is a network component that allows users to connect their VPC to the public internet. By attaching an Internet Gateway to a VPC, users can enable their network resources to communicate with the public internet and receive inbound traffic from the internet.
NAT Gateway
A NAT (Network Address Translation) Gateway is a network component that allows users to enable instances within a private subnet to communicate with the public internet, while preventing inbound traffic from the internet. NAT Gateways are typically used to enable instances to download updates or access external resources, while maintaining a secure network environment.
Security Group
A security group is a virtual firewall that controls inbound and outbound traffic to and from network resources within a VPC. Security groups can be associated with one or more instances and contain rules that specify which network traffic is allowed or denied.
Network Access Control List (NACL)
A network access control list (NACL) is a set of rules that control inbound and outbound traffic to and from a subnet within a VPC. NACLs are similar to security groups, but operate at the subnet level, rather than the instance level. NACLs can be used to provide an additional layer of security and control over network traffic within a VPC.
In summary, understanding the key concepts and terminologies associated with AWS VPC is crucial for effectively using and managing virtual network resources within the AWS cloud. By familiarizing oneself with terms such as VPC, subnet, route table, Internet Gateway, NAT Gateway, security group, and network access control list (NACL), users can take full advantage of the features and capabilities of AWS VPC, enabling them to build and deploy highly available and secure network environments for their workloads.
Creating and Configuring an AWS VPC: A Step-by-Step Guide
In this section, we will provide a detailed, hands-on guide on how to create and configure an AWS VPC using the AWS Management Console. We will emphasize best practices for setting up VPCs, such as creating multiple subnets for different purposes, configuring route tables, and setting up security groups.
Step 1: Create a VPC
To create a new VPC, navigate to the VPC dashboard in the AWS Management Console and click on the “Create VPC” button. Enter a name and IP address range for your VPC, and then click “Create”.
Step 2: Create Subnets
Once you have created your VPC, you can create one or more subnets within it. To create a subnet, navigate to the “Subnets” section of the VPC dashboard and click on the “Create subnet” button. Select the VPC you created in step 1, enter a name and IP address range for your subnet, and then click “Create”.
Step 3: Configure Route Tables
Next, you will need to configure route tables for your VPC. Route tables determine how network traffic is routed within your VPC. To create a new route table, navigate to the “Route Tables” section of the VPC dashboard and click on the “Create route table” button. Select the VPC you created in step 1, enter a name for your route table, and then click “Create”.
Step 4: Create Security Groups
Security groups act as virtual firewalls for your VPC, controlling inbound and outbound traffic to and from your network resources. To create a new security group, navigate to the “Security Groups” section of the VPC dashboard and click on the “Create security group” button. Select the VPC you created in step 1, enter a name and description for your security group, and then click “Create”.
Step 5: Associate Subnets with Route Tables
Once you have created your route tables and security groups, you will need to associate them with your subnets. To do this, navigate to the “Subnets” section of the VPC dashboard, select the subnet you want to associate with a route table, and then click on the “Actions” button. Select “Edit subnet settings” and then select the route table you want to associate with the subnet. Click “Save” to apply the changes.
Step 6: Configure Security Group Rules
Finally, you will need to configure the rules for your security groups. To do this, navigate to the “Security Groups” section of the VPC dashboard, select the security group you want to configure, and then click on the “Actions” button. Select “Edit inbound rules” or “Edit outbound rules” to configure the rules for your security group. Be sure to follow best practices for securing your VPC, such as only allowing inbound traffic from trusted sources and limiting outbound traffic to only what is necessary.
In summary, creating and configuring an AWS VPC involves several steps, including creating a VPC, creating subnets, configuring route tables, creating security groups, associating subnets with route tables, and configuring security group rules. By following best practices for setting up VPCs, such as creating multiple subnets for different purposes and configuring route tables and security groups, you can ensure that your virtual network is secure, scalable, and highly available.
Securing Your AWS VPC: Strategies and Best Practices
When it comes to securing your AWS VPC, there are several strategies and best practices you can follow to ensure that your virtual network is secure, scalable, and highly available. In this section, we will discuss some of the most important security measures you can take, including using security groups and network access control lists (NACLs) to control inbound and outbound traffic, enabling flow logs for monitoring and troubleshooting, and using VPC peering to connect multiple VPCs securely.
Using Security Groups and NACLs to Control Traffic
Security groups and NACLs are two of the most important tools you can use to control traffic in and out of your VPC. Security groups act as virtual firewalls for your network resources, allowing you to control inbound and outbound traffic based on rules that you define. NACLs, on the other hand, are more like traditional network firewalls, operating at the subnet level and providing an additional layer of security for your network.
When creating security groups and NACLs, it’s important to follow best practices such as only allowing inbound traffic from trusted sources, limiting outbound traffic to only what is necessary, and regularly reviewing and updating your rules to ensure that they are still relevant and effective.
Enabling Flow Logs for Monitoring and Troubleshooting
Flow logs are a powerful tool for monitoring and troubleshooting network traffic in your VPC. By enabling flow logs, you can capture information about the IP traffic going in and out of your network interfaces, including the source and destination IP addresses, ports, protocols, and packet and byte counts. This information can be invaluable for identifying and resolving network issues, as well as for detecting and responding to security threats.
When enabling flow logs, it’s important to consider factors such as the log destination (e.g., Amazon S3, Amazon CloudWatch Logs), the log format (e.g., JSON, CSV), and the log retention period. You should also ensure that you have the necessary permissions and access controls in place to protect your log data from unauthorized access or modification.
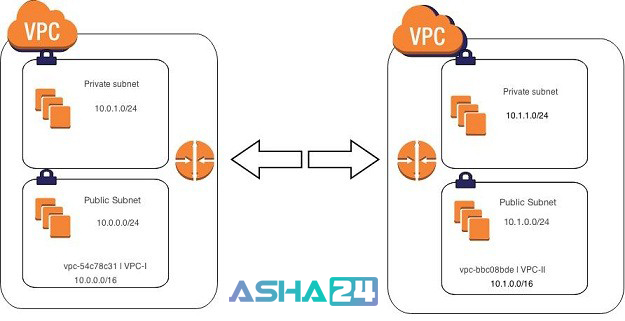
Using VPC Peering to Connect Multiple VPCs Securely
If you need to connect multiple VPCs together, VPC peering is a powerful and secure way to do so. With VPC peering, you can create a direct, private connection between two VPCs, allowing them to communicate with each other as if they were part of the same network. This can be especially useful for organizations that need to maintain separate VPCs for different purposes, such as development, testing, and production.
When setting up VPC peering, it’s important to follow best practices such as using unique peering connection names, enabling encryption for data in transit, and regularly reviewing and updating your peering connection settings to ensure that they are still relevant and effective.
In summary, securing your AWS VPC involves several key strategies and best practices, including using security groups and NACLs to control traffic, enabling flow logs for monitoring and troubleshooting, and using VPC peering to connect multiple VPCs securely. By following these strategies and best practices, you can ensure that your virtual network is secure, scalable, and highly available, and that your network resources are protected from unauthorized access or modification.
Integrating AWS VPC with Other AWS Services: A Practical Guide
One of the key benefits of using AWS VPC is its seamless integration with other AWS services. By integrating your VPC with services such as Amazon EC2, Amazon RDS, and Amazon S3, you can create highly available, scalable, and secure applications and workloads in the cloud. In this section, we will provide practical examples and use cases for integrating your AWS VPC with these and other AWS services.
Setting Up a Highly Available Web Application Using EC2 Instances in Multiple Availability Zones
Amazon EC2 is a popular AWS service for running and scaling web applications in the cloud. By launching EC2 instances in multiple availability zones within your VPC, you can create a highly available and fault-tolerant web application that can withstand the failure of a single availability zone. To set this up, you can follow these steps:
- Create a new VPC or select an existing VPC in which to launch your EC2 instances.
- Create a new subnet in each availability zone you want to use for your web application.
- Launch one or more EC2 instances in each subnet, making sure to use an Amazon Machine Image (AMI) that is optimized for web serving, such as the Amazon Linux 2 AMI with Apache, Nginx, or another web server pre-installed.
- Configure your load balancer to distribute traffic evenly across all of your EC2 instances, using either the Application Load Balancer or the Network Load Balancer, depending on your needs.
- Set up an Auto Scaling group to automatically replace any failed EC2 instances and maintain the desired capacity for your web application.
Creating a Secure Database Instance Using RDS
Amazon RDS is a managed database service that makes it easy to set up, operate, and scale a relational database in the cloud. By launching an RDS instance within your VPC, you can create a secure and isolated database environment that is protected from unauthorized access. To set this up, you can follow these steps:
- Create a new VPC or select an existing VPC in which to launch your RDS instance.
- Create a new subnet in which to launch your RDS instance, making sure to follow best practices for subnet design and placement.
- Launch a new RDS instance in your subnet, making sure to choose the database engine, instance type, and storage options that are appropriate for your workload.
- Configure your RDS instance to use a security group that allows inbound traffic only from trusted sources, such as your web application or other authorized IP addresses.
- Enable encryption for your RDS instance, if desired, to protect your data at rest and in transit.
Storing and Accessing Data Securely Using Amazon S3
Amazon S3 is a highly scalable and durable object storage service that can be used for a wide variety of use cases, from storing backups and archives to serving static assets and hosting websites. By using Amazon S3 with your VPC, you can create a secure and private storage environment that is accessible only from within your VPC. To set this up, you can follow these steps:
- Create a new VPC or select an existing VPC in which to use Amazon S3.
- Create a new VPC endpoint for Amazon S3, which allows you to securely access S3 resources from within your VPC without traversing the public internet.
- Configure your S3 bucket policies and access control lists (ACLs) to allow access only from your VPC endpoint and any other trusted sources.
- Use Amazon S3 Transfer Acceleration or Amazon CloudFront to optimize the performance and availability of your S3-based applications and workloads.
In summary, integrating your AWS VPC with other AWS services, such as Amazon EC2, Amazon RDS, and Amazon S3, can help you create highly available, scalable, and secure applications and workloads in the cloud. By following best practices and using the right tools and techniques, you can ensure that your VPC is optimized for performance, security, and integration with other AWS services.
Scaling and Optimizing Your AWS VPC: Tips and Tricks
As your AWS VPC grows and evolves, it’s important to ensure that it is optimized for performance, scalability, and cost-effectiveness. In this section, we’ll discuss some tips and tricks for scaling and optimizing your AWS VPC, including using Elastic IPs for static IP addresses, using Amazon CloudWatch for monitoring and alerting, and using AWS Direct Connect for dedicated network connectivity.
Using Elastic IPs for Static IP Addresses
An Elastic IP is a static IP address that can be associated with an EC2 instance or a network interface in your VPC. By using Elastic IPs, you can ensure that your applications and workloads are accessible from the internet using a consistent IP address, even if you stop, start, or replace your EC2 instances. To use Elastic IPs in your VPC, you can follow these steps:
- Allocate one or more Elastic IPs from the AWS Management Console or the AWS CLI.
- Associate the Elastic IP with an EC2 instance or a network interface in your VPC, making sure to choose the correct region and availability zone.
- Configure your security groups and network ACLs to allow inbound and outbound traffic to and from your Elastic IP.
- Test your Elastic IP to ensure that it is accessible from the internet and that your applications and workloads are functioning as expected.
Using Amazon CloudWatch for Monitoring and Alerting
Amazon CloudWatch is a monitoring and observability service that provides real-time visibility into your AWS resources and applications. By using CloudWatch with your VPC, you can monitor key metrics such as network traffic, CPU utilization, and memory usage, and set up alarms and notifications to alert you when thresholds are exceeded. To use CloudWatch in your VPC, you can follow these steps:
- Enable CloudWatch monitoring for your EC2 instances, RDS instances, and other AWS resources in your VPC.
- Configure CloudWatch metrics and alarms to monitor key performance indicators (KPIs) and trigger alerts when necessary.
- Use CloudWatch dashboards and visualizations to gain insights into your VPC performance and identify trends and anomalies.
- Integrate CloudWatch with other AWS services, such as AWS Lambda, to automate remediation actions and improve your VPC resilience and reliability.
Using AWS Direct Connect for Dedicated Network Connectivity
AWS Direct Connect is a network service that allows you to establish a dedicated network connection between your on-premises infrastructure and your AWS VPC. By using Direct Connect, you can reduce your network latency, increase your bandwidth, and improve your network security and performance. To use Direct Connect in your VPC, you can follow these steps:
- Create a new Direct Connect connection from the AWS Management Console or the AWS CLI.
- Configure your network devices and routing tables to route traffic through your Direct Connect connection.
- Verify that your Direct Connect connection is established and functioning as expected.
- Monitor your Direct Connect connection using CloudWatch metrics and alarms, and optimize your network performance and cost-effectiveness using Direct Connect best practices.
In summary, scaling and optimizing your AWS VPC involves using tools and techniques such as Elastic IPs, Amazon CloudWatch, and AWS Direct Connect to ensure that your VPC is performing at its best and meeting your business needs. By following best practices and using the right tools and techniques, you can create a scalable, secure, and cost-effective network infrastructure that supports your applications and workloads in the cloud.
Troubleshooting Common AWS VPC Issues: A Practical Guide
As with any complex system, AWS VPC can sometimes experience issues that can affect the performance, security, and availability of your virtual network infrastructure. In this section, we’ll discuss some common AWS VPC issues and provide practical solutions for troubleshooting them. We’ll also provide best practices for preventing these issues in the future.
Connectivity Problems
Connectivity problems are one of the most common issues that can affect AWS VPC. These problems can be caused by a variety of factors, such as misconfigured security groups, incorrect route tables, or network congestion. To troubleshoot connectivity problems in AWS VPC, you can follow these steps:
- Check your security groups and network ACLs to ensure that they are allowing inbound and outbound traffic to and from your resources.
- Verify that your route tables are correctly configured and that they are pointing to the correct network gateways and endpoints.
- Use tools such as ping, traceroute, and MTR to diagnose network latency, packet loss, and other connectivity issues.
- Check your VPC flow logs to identify any unusual or unexpected network traffic patterns, and take corrective action as necessary.
Security Group Misconfigurations
Security group misconfigurations can expose your AWS VPC resources to security risks and vulnerabilities. To prevent security group misconfigurations, you can follow these best practices:
- Use the principle of least privilege when configuring your security groups, allowing only the minimum necessary traffic to and from your resources.
- Regularly review and audit your security group rules to ensure that they are up-to-date and aligned with your security policies and requirements.
- Use tools such as AWS Security Hub and AWS Config to monitor and enforce your security group configurations, and to identify and remediate any misconfigurations.
Routing Errors
Routing errors can cause network traffic to be misdirected or dropped, leading to connectivity problems and other issues. To prevent routing errors in AWS VPC, you can follow these best practices:
- Use the AWS VPC route table propagation feature to automatically propagate route table updates to your VPC resources.
- Use the AWS VPC route table static routes feature to manually configure static routes to specific destinations.
- Use tools such as AWS CloudTrail and AWS Config to monitor and audit your route table configurations, and to identify and remediate any misconfigurations.
In summary, troubleshooting common AWS VPC issues involves using tools and techniques such as ping, traceroute, and MTR to diagnose connectivity problems, reviewing and auditing your security group and route table configurations, and using tools such as AWS Security Hub and AWS Config to monitor and enforce your VPC configurations. By following best practices and using the right tools and techniques, you can ensure that your AWS VPC is performing at its best and meeting your business needs.
Advanced AWS VPC Features: Exploring the Possibilities
Amazon Virtual Private Cloud (AWS VPC) offers a range of advanced features that can help organizations improve their network security and performance. This article explores some of these advanced features, including VPC endpoints, VPC sharing, and VPC traffic mirroring.
VPC Endpoints
VPC endpoints allow organizations to create a private connection between their VPC and AWS services without using public internet gateways or NAT devices. This can help improve network security and reduce latency. With VPC endpoints, organizations can securely access services such as Amazon S3, Amazon DynamoDB, and Amazon SNS without exposing their traffic to the public internet.
VPC Sharing
VPC sharing allows organizations to share their VPC resources with other AWS accounts within the same organization. This can help reduce costs and simplify network management. With VPC sharing, organizations can share resources such as subnets, route tables, and security groups with other AWS accounts, while maintaining control over who can access them.
VPC Traffic Mirroring
VPC traffic mirroring allows organizations to monitor and inspect network traffic in real-time. With VPC traffic mirroring, organizations can create copies of network traffic and send them to security appliances or other tools for analysis. This can help improve network security and compliance by enabling organizations to detect and respond to threats more quickly.
Use Cases
There are many use cases for these advanced AWS VPC features. For example, organizations can use VPC endpoints to create a secure connection to their Amazon S3 buckets, reducing the risk of data breaches. They can use VPC sharing to share resources with other teams or departments within their organization, improving collaboration and reducing costs. And they can use VPC traffic mirroring to monitor network traffic for signs of suspicious activity, improving their security posture and compliance.
Conclusion
AWS VPC offers a range of advanced features that can help organizations improve their network security and performance. By using VPC endpoints, VPC sharing, and VPC traffic mirroring, organizations can create a more secure and efficient network infrastructure. Whether you’re looking to reduce costs, improve collaboration, or enhance security, these advanced features can help you achieve your goals.