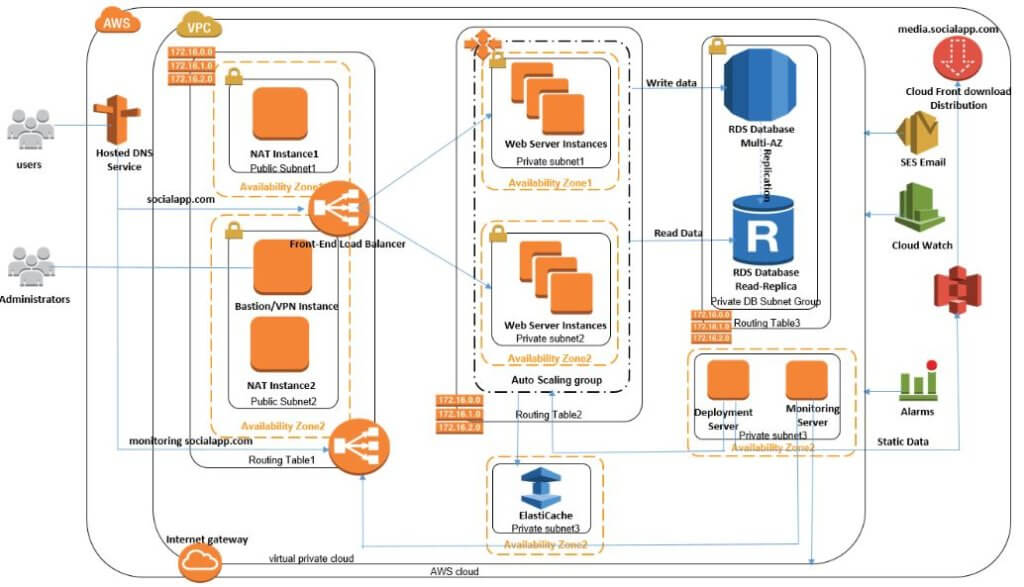
What is AWS Trusted Advisor and How Can It Benefit You?
AWS Trusted Advisor is a powerful tool designed to help AWS customers optimize their cloud infrastructure. It provides best practice recommendations, ensuring security, cost-efficiency, and adherence to AWS best practices. By utilizing AWS Trusted Advisor, users can access a wide range of features and benefits, including checks for underutilized resources, monitoring security vulnerabilities, and identifying cost-saving opportunities. These capabilities empower users to maintain a well-optimized and secure cloud environment, ultimately leading to enhanced cloud management and improved overall performance.
How to Leverage AWS Trusted Advisor for Improved Cloud Management
To effectively utilize AWS Trusted Advisor, users should first enable the service and familiarize themselves with its core categories. AWS Trusted Advisor can be accessed through the AWS Management Console, AWS CLI, or AWS SDKs. Once enabled, users can explore the following categories:
- Cost Optimization: This category helps users identify underutilized resources, such as idle EC2 instances, unattached EBS volumes, and unused snapshots, enabling them to right-size their resources and save on costs.
- Performance: The performance category offers checks for overloaded resources, ensuring high availability and scalability by monitoring for overloaded resources, enabling multi-AZ deployments, and ensuring proper load balancing.
- Security: The security category emphasizes the importance of following security best practices in the cloud, helping users identify security vulnerabilities, such as open ports, insecure Amazon S3 buckets, and unencrypted Amazon RDS instances.
- Fault Tolerance: This category focuses on maintaining high availability and scalability by providing checks for overloaded resources, enabling multi-AZ deployments, and ensuring proper load balancing.
- Service Limits: AWS Trusted Advisor helps users avoid hitting resource limits by monitoring service limits and recommending adjustments to resource usage, preventing potential service disruptions.
By addressing each category, users can ensure a well-optimized and secure cloud environment, enhancing their overall cloud management experience.
A Deep Dive into AWS Trusted Advisor Categories
AWS Trusted Advisor offers five core categories, each with its unique set of checks and recommendations. Addressing each category is essential for maintaining a well-optimized and secure cloud environment. Here’s a detailed look at each category:
Cost Optimization
The cost optimization category helps users identify underutilized resources, such as idle EC2 instances, unattached EBS volumes, and unused snapshots. By right-sizing resources, users can save on costs and optimize their infrastructure. Key checks include:
- Low Utilization EC2 Instances
- Unattached EBS Volumes
- Idle Load Balancers
- Unused Elastic IP Addresses
Performance
The performance category focuses on ensuring high availability and scalability. Users can monitor for overloaded resources, enable multi-AZ deployments, and ensure proper load balancing. Key checks include:
- High Utilization EC2 Instances
- High CPU Utilization
- High Network In/Out
- Overloaded DynamoDB Tables
Security
The security category emphasizes the importance of following security best practices in the cloud. Users can identify security vulnerabilities, such as open ports, insecure Amazon S3 buckets, and unencrypted Amazon RDS instances. Key checks include:
- Security Groups – Open Ports
- IAM Access Key Rotation
- Amazon S3 Bucket Permissions
- MFA on Root Account
Fault Tolerance
The fault tolerance category focuses on maintaining high availability and scalability. Users can ensure proper load balancing and multi-AZ deployments. Key checks include:
- EBS Volume Protection
- Auto Scaling Group Health
- Multi-AZ RDS Instances
- ELB Connection Draining
Service Limits
The service limits category helps users avoid hitting resource limits. Users can monitor service limits and adjust resource usage accordingly to prevent potential service disruptions. Key checks include:
- RDS DB Instance Limits
- IAM User Limits
- SNS Topic Limits
- SQS Queue Limits
By addressing each category, users can ensure a well-optimized and secure cloud environment, enhancing their overall cloud management experience.
Cost Optimization with AWS Trusted Advisor: Identifying Underutilized Resources
AWS Trusted Advisor’s cost optimization category is a powerful tool for identifying underutilized resources, enabling users to save on costs. By focusing on this category, users can:
- Optimize resource usage
- Eliminate waste
- Ensure cost-efficiency
Key checks within the cost optimization category include:
- Low Utilization EC2 Instances: AWS Trusted Advisor can detect instances with low CPU utilization, allowing users to consider downsizing or terminating them. Users can also consider using Spot Instances or Reserved Instances for cost savings.
- Unattached EBS Volumes: Unused EBS volumes can lead to unnecessary costs. AWS Trusted Advisor can identify unattached EBS volumes, enabling users to review and delete them to avoid extra charges.
- Idle Load Balancers: Trusted Advisor can detect idle load balancers, which may not be serving any traffic. Users can review these load balancers and consider deleting them to save on costs.
- Unused Elastic IP Addresses: AWS Trusted Advisor can identify Elastic IP addresses not associated with a running instance. Users can review these IP addresses and release them to avoid unnecessary charges.
To optimize costs, users should regularly review and take action on the recommendations provided by AWS Trusted Advisor’s cost optimization category. By addressing underutilized resources, users can ensure a cost-efficient and well-optimized cloud environment.
Security Best Practices: Enhancing Cloud Infrastructure Protection with AWS Trusted Advisor
Security is a top priority for AWS customers, and AWS Trusted Advisor offers a security category to help users maintain a secure cloud environment. By focusing on this category, users can:
- Identify security vulnerabilities
- Follow security best practices
- Protect sensitive data and systems
Key checks within the security category include:
- Security Groups – Open Ports: AWS Trusted Advisor can detect open ports in security groups, allowing users to review and restrict access to only necessary sources. This helps prevent unauthorized access to instances and data.
- IAM Access Key Rotation: Trusted Advisor can identify IAM access keys not rotated within the recommended period. Regular rotation of access keys enhances security by limiting the time an access key is exposed, reducing the risk of compromise.
- Amazon S3 Bucket Permissions: AWS Trusted Advisor can detect S3 buckets with open permissions, enabling users to review and restrict access to only authorized users. This helps prevent unauthorized access to sensitive data stored in S3 buckets.
- MFA on Root Account: Trusted Advisor can check if multi-factor authentication (MFA) is enabled on the root AWS account. Enabling MFA adds an extra layer of security, making it harder for unauthorized users to gain access to the account.
To maintain a secure cloud environment, users should regularly review and take action on the recommendations provided by AWS Trusted Advisor’s security category. By addressing security vulnerabilities, users can ensure a secure and compliant cloud infrastructure.
Performance and Fault Tolerance: Ensuring High Availability and Scalability with AWS Trusted Advisor
AWS Trusted Advisor offers performance and fault tolerance categories to help users maintain high availability and scalability in their cloud infrastructure. By focusing on these categories, users can:
- Monitor for overloaded resources
- Enable multi-AZ deployments
- Ensure proper load balancing
Key checks within the performance and fault tolerance categories include:
- High Utilization EC2 Instances: AWS Trusted Advisor can detect EC2 instances with high CPU or network utilization, allowing users to review and consider adding more resources or scaling horizontally to distribute the load.
- Overloaded Amazon RDS DB Instances: Trusted Advisor can identify RDS instances with high CPU or memory usage, enabling users to review and consider scaling up, scaling out, or optimizing their database workload.
- ELB Connection Draining: AWS Trusted Advisor can check if connection draining is enabled for ELB load balancers. Connection draining ensures that in-flight requests are completed before instances are deregistered from the load balancer, preventing service disruptions.
- Multi-AZ RDS Instances: Trusted Advisor can detect RDS instances not configured for multi-AZ deployments. Enabling multi-AZ deployments ensures high availability by automatically creating a synchronous standby replica in a different Availability Zone.
To maintain high availability and scalability, users should regularly review and take action on the recommendations provided by AWS Trusted Advisor’s performance and fault tolerance categories. By addressing performance and fault tolerance concerns, users can ensure a highly available and scalable cloud infrastructure.
Service Limits: Staying Ahead of AWS Resource Limitations with AWS Trusted Advisor
AWS Trusted Advisor offers a service limits category to help users monitor and manage their AWS resource limits. By focusing on this category, users can:
- Avoid hitting resource limits
- Prevent potential service disruptions
- Plan resource usage and scaling strategies
Key checks within the service limits category include:
- RDS DB Instance Limits: AWS Trusted Advisor can detect if the number of RDS DB instances in an account is close to the service limit. Users can review and request a limit increase or adjust their resource usage accordingly.
- IAM User Limits: Trusted Advisor can identify if the number of IAM users in an account is close to the service limit. Users can review and manage their IAM users or request a limit increase if needed.
- SNS Topic Limits: AWS Trusted Advisor can check if the number of SNS topics in an account is close to the service limit. Users can review and manage their SNS topics or request a limit increase if necessary.
- SQS Queue Limits: Trusted Advisor can detect if the number of SQS queues in an account is close to the service limit. Users can review and manage their SQS queues or request a limit increase if required.
To maintain a smooth cloud infrastructure operation, users should regularly review and take action on the recommendations provided by AWS Trusted Advisor’s service limits category. By monitoring and managing resource limits, users can ensure a stable and scalable cloud environment.
Integrating AWS Trusted Advisor with Other AWS Services: Enhancing Cloud Management
AWS Trusted Advisor can be integrated with various AWS services to provide a seamless cloud management experience. By leveraging these integrations, users can:
- Optimize resource usage
- Enhance security and compliance
- Monitor and control costs
Key integrations include:
- AWS CloudFormation: Users can create AWS CloudFormation templates with Trusted Advisor checks embedded, ensuring best practices and security for their infrastructure stack deployments.
- AWS Management Pack for Microsoft System Center Operations Manager: By integrating Trusted Advisor with Microsoft System Center Operations Manager, users can monitor their AWS resources directly from their existing on-premises management console.
- AWS Cost Explorer: Trusted Advisor integrates with AWS Cost Explorer to provide users with a more comprehensive cost optimization experience. Users can identify cost-saving opportunities and analyze their resource usage patterns to optimize their infrastructure further.
By integrating AWS Trusted Advisor with other AWS services, users can create a cohesive and efficient cloud management strategy. These integrations enable users to maintain a well-optimized, secure, and cost-effective cloud infrastructure.