Unleashing the Power of IaC with AWS and Terraform
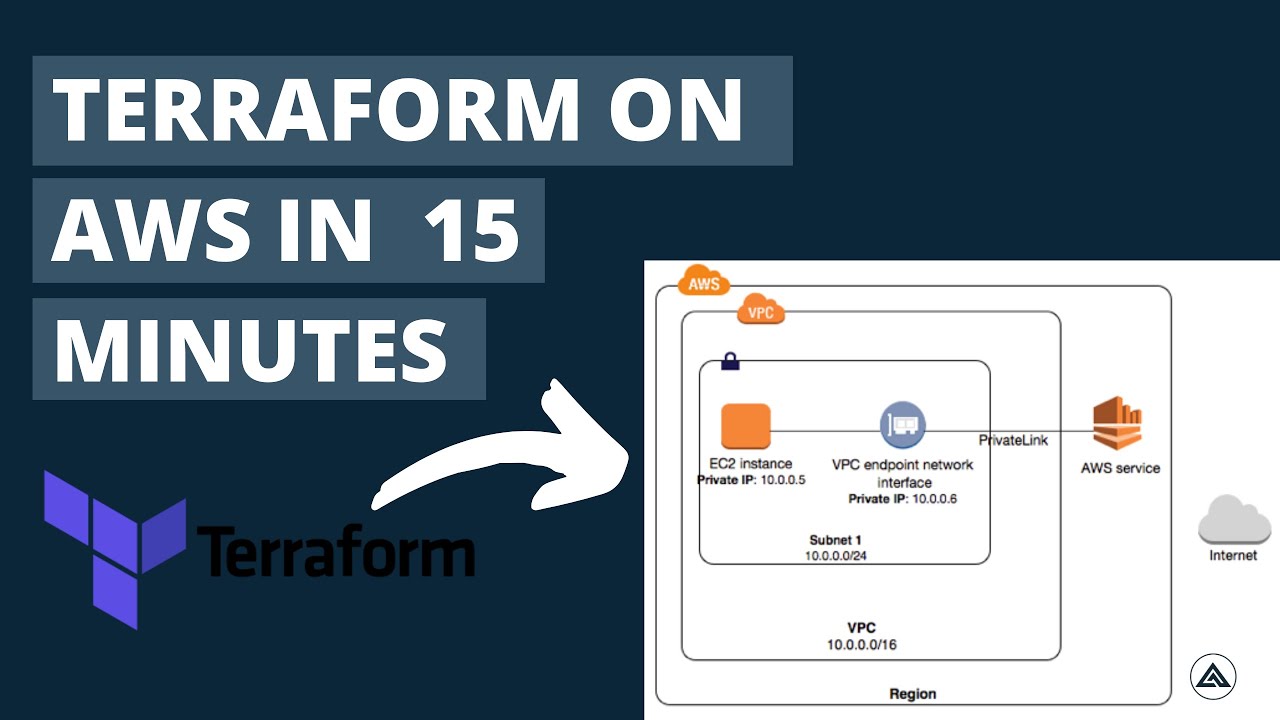
Infrastructure as Code (IaC) has revolutionized the way businesses manage their cloud resources. By treating infrastructure as software, IaC enables organizations to automate the provisioning, configuration, and management of resources in a scalable, predictable, and repeatable manner. AWS and Terraform, a popular IaC tool, have collaborated to provide a seamless experience for managing AWS resources.
The significance of AWS Terraform examples lies in their ability to illustrate the practical implementation of Terraform with AWS. These examples cater to various levels of expertise and use cases, making them an invaluable resource for both beginners and seasoned professionals. By studying these examples, users can gain a deeper understanding of how to effectively manage their AWS infrastructure using Terraform.
AWS Terraform Examples: A Comprehensive Showcase
AWS Terraform examples serve as a rich resource for users looking to understand and implement IaC principles in their AWS infrastructure management. These examples cater to a wide range of use cases and expertise levels, ensuring that everyone can find something valuable to learn from.
For beginners, simple examples that demonstrate basic Terraform concepts and AWS resource deployment are essential. These examples typically focus on creating and managing a single resource, such as an Amazon Elastic Compute Cloud (EC2) instance or an Amazon Simple Storage Service (S3) bucket. By studying these examples, new users can quickly grasp the fundamentals of Terraform and start managing their AWS resources with confidence.
Intermediate and advanced users will benefit from more complex examples that showcase how to build and manage sophisticated AWS infrastructure. These examples may include the deployment of multiple resources, such as Virtual Private Clouds (VPCs), subnets, security groups, and load balancers. They may also demonstrate how to implement advanced features like Terraform modules and workspaces, enabling users to build scalable, secure, and cost-effective infrastructure.
In addition to catering to different expertise levels, AWS Terraform examples also cover a wide variety of use cases. Examples may focus on specific AWS services, such as Amazon Relational Database Service (RDS), Amazon Elastic Kubernetes Service (EKS), or Amazon Aurora. They may also address common infrastructure management scenarios, such as multi-region deployments, disaster recovery, and hybrid cloud architectures. By providing examples that cover various use cases, users can easily find resources that align with their specific needs and requirements.
Getting Started with AWS and Terraform: A ‘How-To’ Guide
To begin your journey with AWS and Terraform, follow this step-by-step guide to set up your environment and configure your tools. This guide assumes that you have a basic understanding of AWS services and infrastructure concepts.
Prerequisites
Ensure you have the following prerequisites in place:
- An AWS account with appropriate permissions
- Terraform installed on your local machine or a CI/CD pipeline
- A text editor or Integrated Development Environment (IDE) for writing Terraform configuration files
Installation Procedures
Follow these steps to install and configure Terraform:
- Download the latest version of Terraform from the official website (https://www.terraform.io/downloads.html).
- Unzip the downloaded file and move the Terraform binary to a directory in your system’s PATH.
- Verify the installation by running
terraform --versionin your terminal or command prompt.
Configuration Steps
To configure Terraform for AWS, follow these steps:
- Create a new directory for your Terraform configuration files.
- Create a file named
provider.tfin the new directory and add the following content:provider "aws" { region = "us-west-2" }Replace
"us-west-2"with the AWS region you want to use. - Configure your AWS credentials by creating a file named
.aws/credentialsin your home directory with the following content:[default] aws_access_key_id = "YOUR_ACCESS_KEY" aws_secret_access_key = "YOUR_SECRET_KEY"Replace
"YOUR_ACCESS_KEY"and"YOUR_SECRET_KEY"with your actual AWS access key and secret key. - Test your configuration by running
terraform initin the directory containing your Terraform configuration files.
Building Scalable AWS Infrastructure with Terraform Modules
Terraform modules are reusable components that enable users to build scalable AWS infrastructure. By encapsulating common infrastructure patterns, modules simplify the management and deployment of resources. This section showcases examples that utilize modules to deploy resources like Virtual Private Clouds (VPCs), Amazon Elastic Compute Cloud (EC2) instances, and Amazon Simple Storage Service (S3) buckets.
Example 1: Creating a VPC with Public and Private Subnets
The following example demonstrates how to create a VPC with public and private subnets using the href=”https://registry.terraform.io/modules/terraform-aws-modules/vpc/aws/latest” target=”_blank” rel=”noopener noreferrer”>terraform-aws-modules/vpc/aws module:
module "vpc" { source = "terraform-aws-modules/vpc/aws" version = "3.0.0" name = "my-vpc"
cidr = "10.0.0.0/16"
azs = ["us-west-2a", "us-west-2b", "us-west-2c"]
public_subnets = ["10.0.1.0/24", "10.0.2.0/24", "10.0.3.0/24"]
private_subnets = ["10.0.101.0/24", "10.0.102.0/24", "10.0.103.0/24"]
enable_nat_gateway = true
enable_vpn_gateway = true
}
Example 2: Deploying EC2 Instances
The following example demonstrates how to deploy EC2 instances using the terraform-aws-modules/ec2-instance/aws module:
module "ec2_instances" { source = "terraform-aws-modules/ec2-instance/aws" version = "2.0.0" name = "my-ec2-instances"
instance_count = 2
ami = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
key_name = "my-key-pair"
subnet_id = module.vpc.public_subnets
0
vpc_security_group_ids = [module.vpc.default_security_group]
}
Example 3: Creating an S3 Bucket
The following example demonstrates how to create an S3 bucket using the href=”https://registry.terraform.io/modules/terraform-aws-modules/s3-bucket/aws/latest” target=”_blank” rel=”noopener noreferrer”>terraform-aws-modules/s3-bucket/aws module:
module "s3_bucket" { source = "terraform-aws-modules/s3-bucket/aws" version = "2.0.0" bucket = "my-s3-bucket"
acl = "private"
versioning = {
enabled = true
}
}
Automating AWS Infrastructure Deployment with Terraform Workspaces
Terraform workspaces provide an efficient way to manage and automate AWS infrastructure deployment. They enable users to create, configure, and manage multiple environments, such as development, staging, and production, within a single Terraform configuration. This section showcases examples that demonstrate the use of workspaces for managing AWS infrastructure.
Example 1: Creating Workspaces for Development, Staging, and Production Environments
The following example demonstrates how to create workspaces for development, staging, and production environments:
provider "aws" { region = "us-west-2" } terraform {
backend "s3" {
bucket = "my-terraform-state-bucket"
key = "terraform.tfstate"
region = "us-west-2"
}
}
variable "environment" {
type = string
default = "development"
}
resource "aws_vpc" "example" {
cidr_block = "10.0.0.0/16"
tags = {
Name = "${var.environment}-vpc"
}
}
resource "aws_subnet" "example" {
vpc_id = aws_vpc.example.id
cidr_block = "10.0.1.0/24"
tags = {
Name = "${var.environment}-subnet"
}
}
resource "aws_security_group" "example" {
name = "${var.environment}-security-group"
description = "Allow TLS inbound traffic"
vpc_id = aws_vpc.example.id
ingress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_instance" "example" {
ami = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
subnet_id = aws_subnet.example.id
vpc_security_group_ids = [aws_security_group.example.id]
user_data = <<-EOF
#!/bin/bash
echo "Hello, World from ${var.environment}!"
EOF
tags = {
Name = "${var.environment}-instance"
}
}
To create workspaces, run the following commands:
terraform init terraform workspace new development terraform plan terraform apply terraform workspace new staging
terraform plan
terraform apply
terraform workspace new production
terraform plan
terraform apply
Example 2: Using Workspace Variables to Manage Environment-Specific Configuration
The previous example can be further optimized by using workspace variables to manage environment-specific configuration:
variable "cidr\_block" { type = string default = "10.0.0.0/16" } variable "instance_type" {
type = string
default = "t2.micro"
}
resource "aws_vpc" "example" {
cidr_block = var.cidr_block
tags = {
Name = "${var.environment}-vpc"
}
}
resource "aws_subnet" "example" {
vpc_id = aws_vpc.example.id
cidr_block = var.cidr_block
tags = {
Name = "${var.environment}-subnet"
}
}
resource "aws_security_group" "example" {
name = "${var.environment}-security-group"
description = "Allow TLS inbound traffic"
vpc_id = aws_vpc.example.id
ingress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
Monitoring and Managing AWS Infrastructure with Terraform and CloudWatch
Monitoring and managing AWS infrastructure is crucial for ensuring optimal performance and security. Terraform integrates with AWS CloudWatch, enabling users to create, configure, and manage CloudWatch alarms, logs, and metrics. This section showcases examples that utilize CloudWatch to monitor and manage AWS infrastructure.
Example 1: Creating a CloudWatch Alarm for EC2 Instance Monitoring
The following example demonstrates how to create a CloudWatch alarm to monitor the CPU utilization of an EC2 instance:
provider "aws" { region = "us-west-2" } resource "aws_instance" "example" {
ami = "ami-0c94855ba95c574c
Terraform AWS Security Best Practices: Examples and Recommendations
Security is a top priority in AWS infrastructure management. Terraform enables users to implement security best practices when managing AWS resources. This section showcases examples that adhere to AWS security best practices, including least privilege access, data encryption, and security audits.
Example 1: Implementing Least Privilege Access with IAM Policies
The following example demonstrates how to create an IAM policy that grants least privilege access to an S3 bucket:
provider "aws" { region = "us-west-2" } resource "aws_iam_policy" "example" {
name = "s3-read-only-access"
description = "An example IAM policy that grants read-only access to an S3 bucket"
policy = <
Example 2: Encrypting Data with AWS Key Management Service (KMS)
The following example demonstrates how to create an S3 bucket with KMS-encrypted data:
provider "aws" { region = "us-west-2" } resource "aws_kms_key" "example" {
description = "Example KMS key"
key_usage = "ENCRYPT_DECRYPT"
customer_master_keys = []
deletion_window_in_days = 7
}
resource "aws_s3_bucket" "example" {
bucket = "example-bucket"
server_side_encryption_configuration {
rule {
apply_server_side_encryption_by_default {
kms_master_key_id = aws_kms_key.example.arn
sse_algorithm = "aws:kms"
}
}
}
}
Example 3: Performing Security Audits with AWS Config and AWS Systems Manager Parameter Store
The following example demonstrates how to create a custom AWS Config rule that checks for the presence of an IAM password policy and stores the result in AWS Systems Manager Parameter Store:
provider "aws" { region = "us-west-2" } resource "aws_config_config_rule" "example" {
name = "iam-password-policy"
description = "Check for the presence of an IAM password policy"
source {
owner = "AWS"
source_identifier = "IAM_PASSWORD_POLICY"
}
}
resource "aws_ssm_parameter" "example" {
name = "/config/iam-password-policy"
type = "String"
value = aws_config_config_rule.example.arn
}
Optimizing AWS Costs with Infrastructure as Code: Terraform Examples
Optimizing AWS costs is crucial for businesses that want to maintain a cost-effective infrastructure. Infrastructure as Code (IaC) enables organizations to manage their infrastructure efficiently, reducing the risk of human error and ensuring consistent resource allocation. This section showcases Terraform examples that demonstrate cost-effective resource allocation, scaling, and decommissioning.
Example 1: Implementing Auto Scaling with AWS Auto Scaling Groups
The following example demonstrates how to create an Auto Scaling group that automatically scales the number of Amazon Elastic Compute Cloud (EC2) instances based on CloudWatch alarms:
provider "aws" { region = "us-west-2" } resource "aws_launch_configuration" "example" {
image_id = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
security_groups = [aws_security_group.example.id]
}
resource "aws_security_group" "example" {
name = "example-security-group"
description = "An example security group