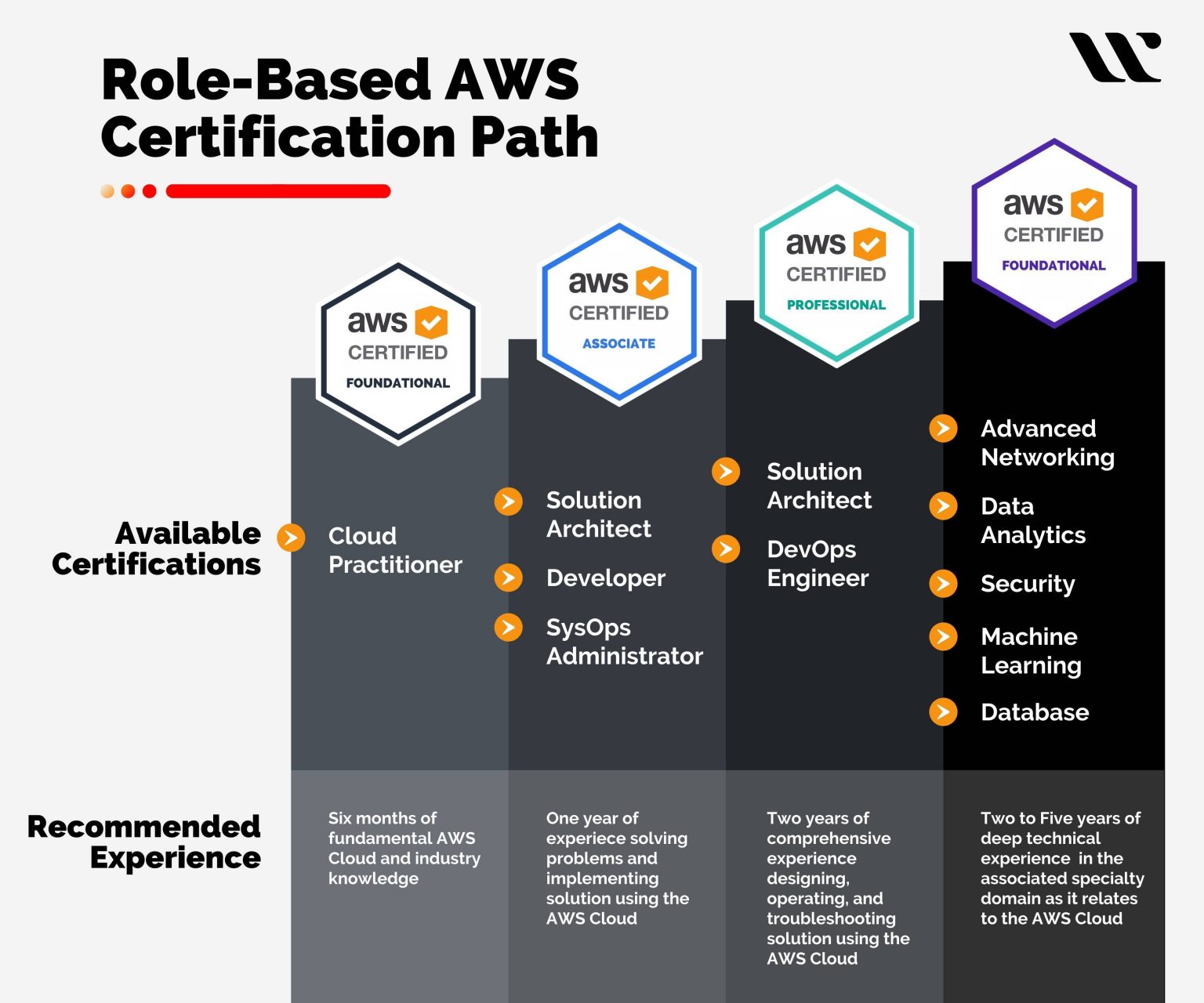
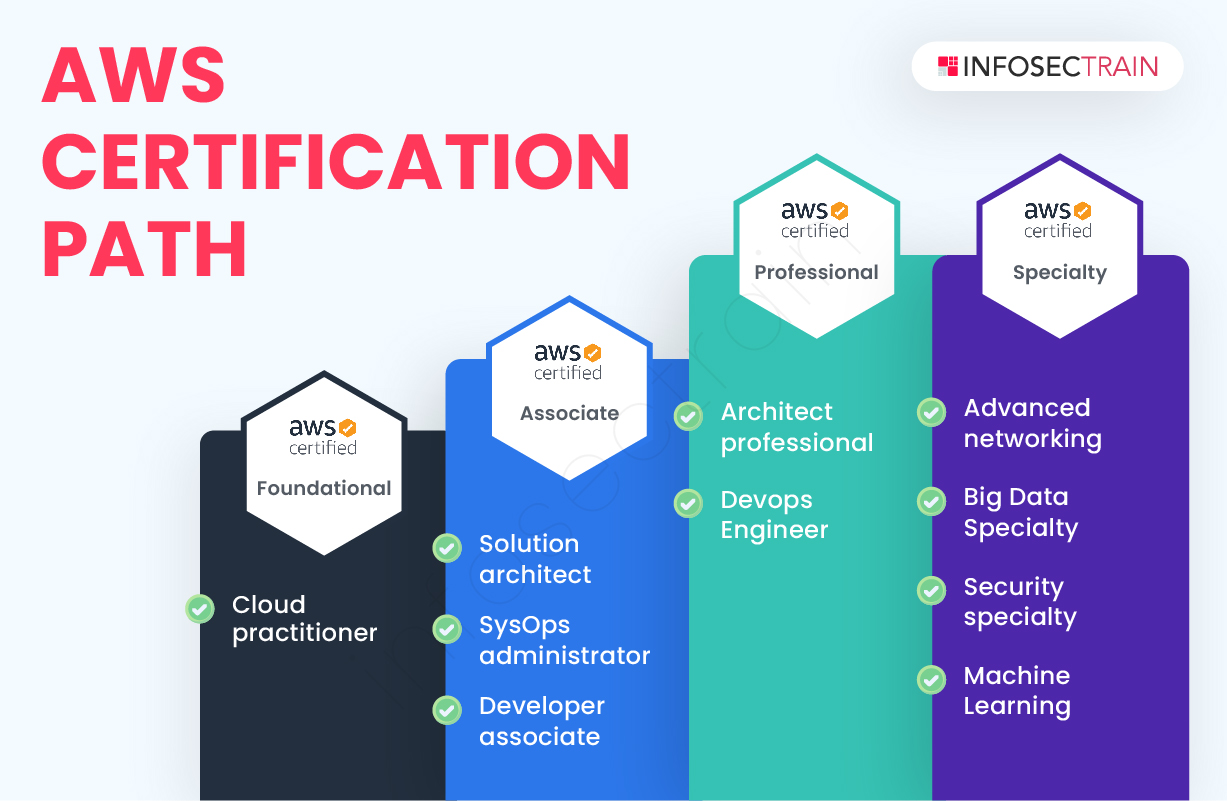
What are AWS Security Certificates?
AWS security certificates are digital certificates that provide secure communication between AWS services and client applications. These certificates play a crucial role in establishing trust and verifying the identity of both parties involved in the communication. By using valid and up-to-date security certificates, organizations can protect their AWS environments from potential security threats and maintain regulatory compliance.
AWS security certificates are based on industry-standard encryption algorithms, such as RSA and ECC, and are used to secure various types of communication, including web traffic, API requests, and data transfers. AWS provides several options for obtaining and managing security certificates, including AWS Certificate Manager, AWS Identity and Access Management, and AWS Key Management Service.
The importance of using valid and up-to-date security certificates cannot be overstated. Outdated or compromised certificates can lead to security vulnerabilities, data breaches, and regulatory violations. By implementing best practices for managing AWS security certificates, organizations can mitigate these risks and ensure the secure operation of their AWS environments.
How to Implement AWS Security Certificates
Implementing AWS security certificates is a crucial step in securing communication between AWS services and client applications. Here is a step-by-step guide on how to implement AWS security certificates:
-
Generate a certificate signing request (CSR) using a tool such as OpenSSL or the AWS Certificate Manager. The CSR should include details such as the domain name, organization name, and country.
-
Submit the CSR to a trusted certificate authority (CA) such as GlobalSign or DigiCert. The CA will validate the information in the CSR and issue a digital certificate.
-
Download the certificate files from the CA and install them in the AWS environment. The certificate files typically include a public key and a private key, which should be kept secure.
-
Configure the AWS services to use the security certificate. For example, in AWS Elastic Load Balancing, you can upload the certificate files and configure the load balancer to use them for HTTPS traffic.
-
Test the implementation to ensure that the AWS services and client applications are communicating securely using the security certificate.
Here are some screenshots and code examples to help you implement AWS security certificates:
-
Screenshot of generating a CSR using OpenSSL:

-
Code example of uploading a certificate to AWS Certificate Manager:
aws acm import-certificate --certificate file://my-certificate.pem --private-key file://my-private-key.pem --region us-east-1 -
Screenshot of configuring a load balancer to use a security certificate:

By following these steps and using the provided screenshots and code examples, you can successfully implement AWS security certificates in your environment.
Best Practices for Managing AWS Security Certificates
Managing AWS security certificates is essential to maintaining secure communication between AWS services and client applications. Here are some best practices for managing AWS security certificates:
-
Regularly rotate certificates: Rotating certificates on a regular basis can help reduce the risk of compromise. AWS Certificate Manager allows you to automatically rotate certificates on a schedule that you define.
-
Monitor certificate expiration dates: Expired certificates can cause communication failures and security vulnerabilities. Use tools such as AWS Systems Manager Parameter Store to store and manage certificate expiration dates, and set up alerts to notify you when a certificate is about to expire.
-
Implement proper access controls: Limit access to security certificates to only those who need it. Use AWS Identity and Access Management (IAM) to create and manage IAM users, groups, and roles, and to define permissions for accessing AWS resources.
-
Use AWS Certificate Manager: AWS Certificate Manager is a service that enables you to centrally manage, deploy, and renew SSL/TLS certificates for your AWS-based websites and applications. It eliminates the need to manually manage certificates and reduces the risk of errors and misconfigurations.
-
Regularly review certificate usage: Regularly review your AWS environment to ensure that all security certificates are being used as intended. Remove any unused or unnecessary certificates to reduce the risk of misuse or compromise.
By following these best practices, you can help ensure that your AWS environment is secure and compliant with regulatory requirements. Here are some real-world examples and case studies to illustrate the importance of these practices:
-
Case study: A financial services company used AWS Certificate Manager to manage their SSL/TLS certificates, reducing the risk of misconfiguration and improving compliance with regulatory requirements.
-
Real-world example: A healthcare provider used AWS Systems Manager Parameter Store to manage certificate expiration dates and set up alerts, ensuring that all certificates were up-to-date and reducing the risk of communication failures.
By implementing these best practices, you can help ensure that your AWS environment is secure and compliant with regulatory requirements.
Different Types of AWS Security Certificates
AWS offers several types of security certificates to meet the needs of different use cases and applications. Here are some of the most common types of AWS security certificates:
-
SSL/TLS certificates: SSL/TLS certificates are used to secure communication between web servers and client applications. AWS Certificate Manager (ACM) is a service that enables you to easily provision, manage, and deploy SSL/TLS certificates for your AWS-based websites and applications.
-
Server certificates: Server certificates are used to authenticate servers and establish secure communication channels. AWS Key Management Service (KMS) is a service that enables you to create and manage server certificates, as well as manage the encryption and decryption of data.
-
Code signing certificates: Code signing certificates are used to verify the authenticity and integrity of software code. AWS CodeSigning is a service that enables you to create and manage code signing certificates, as well as sign and distribute code.
Each type of AWS security certificate has its own unique use cases and benefits. For example, SSL/TLS certificates are essential for securing web traffic and protecting user data, while code signing certificates are critical for ensuring the authenticity and integrity of software code.
When choosing an AWS security certificate, it’s important to consider factors such as the type of application or service you’re securing, the level of security required, and any regulatory or compliance requirements. By selecting the right type of certificate for your needs, you can help ensure that your AWS environment is secure and compliant.
Here are some real-world examples and case studies to illustrate the importance of choosing the right type of AWS security certificate:
-
Case study: A healthcare provider used AWS Certificate Manager to manage their SSL/TLS certificates, improving compliance with regulatory requirements and reducing the risk of data breaches.
-
Real-world example: A financial services company used AWS Key Management Service to manage their server certificates, ensuring the secure transmission of sensitive data and reducing the risk of compromise.
By understanding the different types of AWS security certificates available, you can make informed decisions about which certificates to use in your AWS environment. This can help ensure that your applications and services are secure, compliant, and protected from potential threats and vulnerabilities.
AWS Security Certificate Management Tools
Managing AWS security certificates can be a complex and time-consuming process, but there are several tools available that can help simplify the process. Here are some of the most popular AWS security certificate management tools:
-
AWS Certificate Manager (ACM): ACM is a service that enables you to easily provision, manage, and deploy SSL/TLS certificates for your AWS-based websites and applications. With ACM, you can centrally manage all of your SSL/TLS certificates, and automatically renew them before they expire.
-
AWS Identity and Access Management (IAM): IAM is a service that enables you to manage access to AWS services and resources. With IAM, you can create and manage users, groups, and roles, and define permissions for accessing AWS resources. IAM also enables you to enforce least privilege access, ensuring that users only have access to the resources they need to perform their job functions.
-
AWS Key Management Service (KMS): KMS is a service that enables you to manage encryption keys and protect data at rest and in transit. With KMS, you can create and manage customer master keys (CMKs), and use them to encrypt and decrypt data. KMS also enables you to manage key policies, grants, and rotations, ensuring that your encryption keys are always up-to-date and secure.
By using these tools, you can simplify the management of AWS security certificates, and ensure that your AWS environment is secure and compliant. Here are some real-world examples and case studies to illustrate the importance of using AWS security certificate management tools:
-
Case study: A retail company used AWS Certificate Manager to manage their SSL/TLS certificates, reducing the risk of data breaches and improving compliance with regulatory requirements.
-
Real-world example: A healthcare provider used AWS Identity and Access Management to manage access to their AWS resources, ensuring that only authorized users had access to sensitive data.
By using AWS security certificate management tools, you can simplify the management of AWS security certificates, and ensure that your AWS environment is secure and compliant. This can help you save time and resources, and reduce the risk of data breaches and regulatory violations.
Common AWS Security Certificate Vulnerabilities and Threats
While AWS security certificates play a critical role in ensuring secure communication between AWS services and client applications, they can also be vulnerable to various threats and attacks. Here are some of the most common vulnerabilities and threats associated with AWS security certificates:
-
Certificate expiration: If an AWS security certificate is not renewed before it expires, it can result in service disruptions and security vulnerabilities. It’s essential to monitor certificate expiration dates and renew them before they expire to ensure uninterrupted service and maintain security.
-
Misconfiguration: Misconfigured AWS security certificates can expose sensitive data and increase the risk of data breaches. It’s crucial to follow best practices for configuring AWS security certificates, such as implementing proper access controls, limiting the use of wildcard certificates, and regularly reviewing certificate configurations.
-
Compromise: AWS security certificates can be compromised if they are stolen, intercepted, or tampered with. It’s essential to protect AWS security certificates from unauthorized access, use secure communication channels, and regularly monitor certificate usage and activity logs to detect any suspicious activity.
To mitigate these risks and protect AWS environments from potential attacks, it’s essential to follow best practices for managing AWS security certificates. This includes regularly rotating certificates, monitoring certificate expiration dates, implementing proper access controls, and using AWS security certificate management tools such as AWS Certificate Manager, AWS Identity and Access Management, and AWS Key Management Service.
Here are some real-world examples and case studies to illustrate the importance of addressing common AWS security certificate vulnerabilities and threats:
-
Case study: A financial services company experienced a service disruption due to an expired SSL/TLS certificate. By using AWS Certificate Manager to manage their SSL/TLS certificates, they were able to automate certificate renewals and prevent future service disruptions.
-
Real-world example: A healthcare provider had a misconfigured server certificate that exposed sensitive patient data. By following best practices for configuring server certificates and implementing proper access controls, they were able to prevent future data breaches.
By addressing common AWS security certificate vulnerabilities and threats, you can help ensure that your AWS environment is secure and compliant. This can help you save time and resources, and reduce the risk of data breaches and regulatory violations.
AWS Security Certificate Compliance and Regulations
When using AWS security certificates, it’s essential to comply with various regulations and standards to ensure the security and privacy of sensitive data. Here are some of the most common regulations and standards related to AWS security certificates:
-
PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure the safe handling of credit card information. AWS provides several tools and services to help organizations comply with PCI DSS, such as AWS Key Management Service (KMS) and AWS Identity and Access Management (IAM).
-
HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) is a set of regulations designed to protect the privacy and security of protected health information (PHI). AWS provides several tools and services to help organizations comply with HIPAA, such as AWS Key Management Service (KMS) and AWS Identity and Access Management (IAM).
-
GDPR: The General Data Protection Regulation (GDPR) is a set of regulations designed to protect the privacy and personal data of EU citizens. AWS provides several tools and services to help organizations comply with GDPR, such as AWS Key Management Service (KMS) and AWS Identity and Access Management (IAM).
To ensure AWS environments are compliant with these regulations and standards, it’s essential to follow best practices for managing AWS security certificates. This includes regularly rotating certificates, monitoring certificate expiration dates, implementing proper access controls, and using AWS security certificate management tools such as AWS Certificate Manager, AWS Identity and Access Management, and AWS Key Management Service.
Here are some real-world examples and case studies to illustrate the importance of complying with regulations and standards related to AWS security certificates:
-
Case study: A healthcare provider needed to comply with HIPAA regulations for handling protected health information (PHI). By using AWS Key Management Service (KMS) and AWS Identity and Access Management (IAM) to manage access to PHI, they were able to ensure the security and privacy of patient data.
-
Real-world example: A financial services company needed to comply with PCI DSS regulations for handling credit card information. By using AWS Key Management Service (KMS) and AWS Identity and Access Management (IAM) to manage access to credit card data, they were able to ensure the security and privacy of customer data.
By complying with regulations and standards related to AWS security certificates, you can help ensure that your AWS environment is secure, compliant, and provides a high level of security and privacy for sensitive data. This can help you avoid regulatory violations, data breaches, and reputational damage.