Reinforcing AWS Security and Compliance: A Comprehensive Guide
Demystifying AWS Security and Compliance: An Overview
AWS security and compliance is a critical aspect of maintaining a secure cloud environment. The shared responsibility model, which divides security responsibilities between AWS and the customer, significantly impacts the security posture of an organization’s AWS infrastructure. Understanding this model is essential for implementing proper security measures and ensuring compliance with relevant regulations.
Reinforcing AWS Security and Compliance: A Comprehensive Guide
Demystifying AWS Security and Compliance: An Overview
AWS security and compliance is a critical aspect of maintaining a secure cloud environment. The shared responsibility model, which divides security responsibilities between AWS and the customer, significantly impacts the security posture of an organization’s AWS infrastructure. Understanding this model is essential for implementing proper security measures and ensuring compliance with relevant regulations.
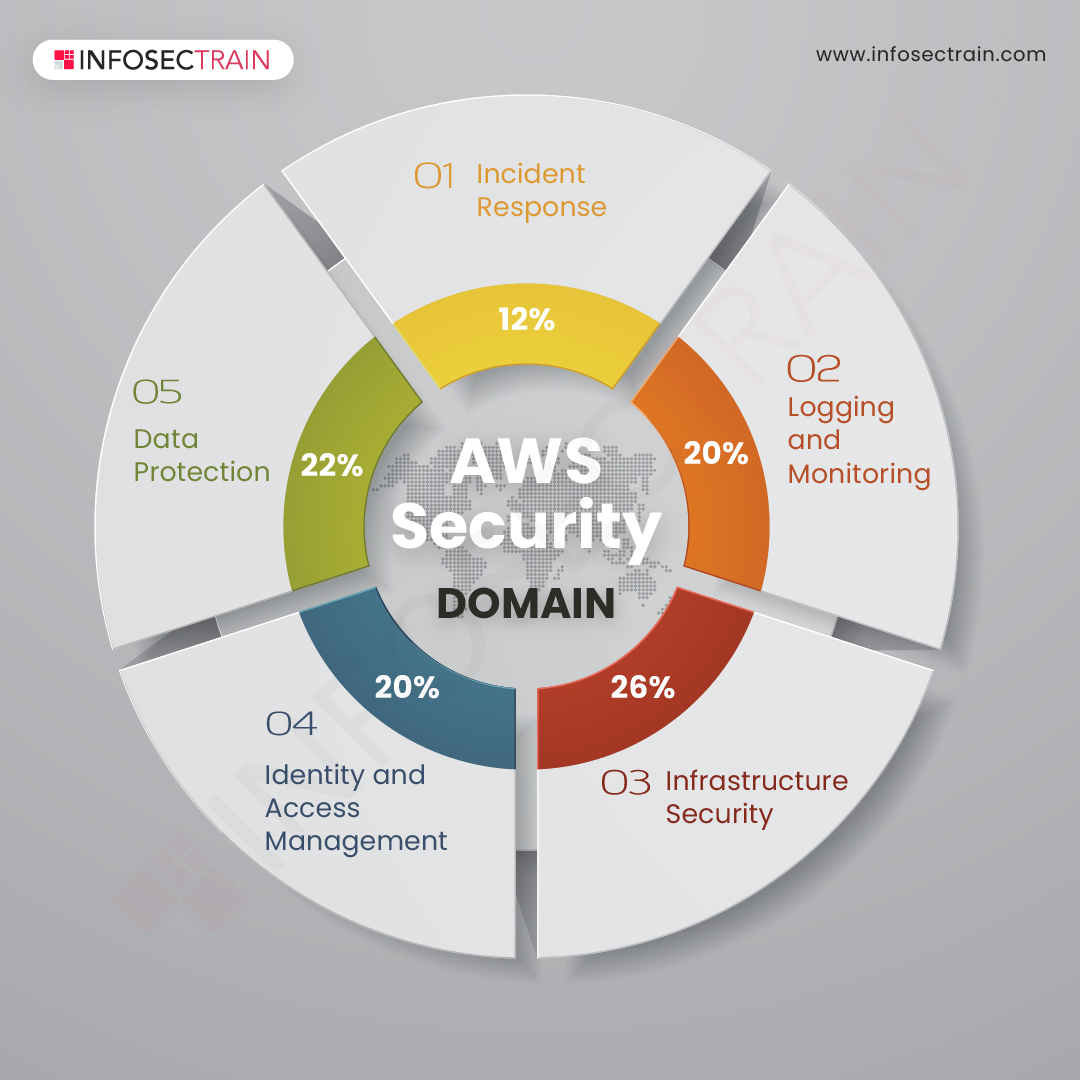
Implementing Identity and Access Management (IAM) Best Practices
IAM is crucial for securing AWS resources. It enables organizations to manage access to AWS services and resources securely. Best practices include adhering to the least privilege principle, using IAM roles, and regularly reviewing access policies. The least privilege principle ensures that users and services are granted the minimum permissions necessary to perform their tasks. IAM roles enable the assignment of permissions to entities that can be assumed by users, applications, or services. Regularly reviewing access policies helps identify and rectify any misconfigurations or unnecessary permissions. Common IAM misconfigurations, such as overly permissive policies or unmanaged access keys, can lead to security vulnerabilities. For instance, allowing a user or service to have more permissions than required increases the risk of unauthorized access or data breaches. Similarly, unmanaged access keys can be easily compromised if they are not rotated or revoked regularly. By following best practices, organizations can minimize the risk of unauthorized access and data breaches, thereby ensuring AWS Security and Compliance.
Configuring Virtual Private Cloud (VPC) for Enhanced Network Security
Virtual Private Cloud (VPC) is a fundamental component of AWS security and compliance. It enables organizations to launch AWS resources in a virtual network that closely resembles a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS. VPC provides advanced security features such as security groups, network access control lists (NACLs), and VPC peering, which are essential in maintaining a secure network within the AWS environment.
Security groups act as virtual firewalls that control inbound and outbound traffic at the instance level. They are stateful, meaning that if you allow traffic in, the response traffic is automatically allowed, even if you don’t create an explicit rule for it. Security groups can be applied to instances in a VPC, enabling you to control traffic to and from those instances.
Network access control lists (NACLs) are virtual firewalls that control inbound and outbound traffic at the subnet level. NACLs can be used to add an additional layer of security to your VPC by controlling traffic before it reaches the instance level. NACLs are stateless, meaning that you need to specify rules for both inbound and outbound traffic separately.
VPC peering enables the connection of two VPCs to enable resources in either VPC to communicate with each other as if they were in the same network. VPC peering can be used to extend the network infrastructure across different regions or accounts, enabling organizations to create a secure and scalable network infrastructure.
By implementing VPC, organizations can ensure that their network traffic and data are secured within the AWS environment, thereby achieving AWS Security and Compliance. It is essential to configure security groups, NACLs, and VPC peering rules correctly to maintain a secure network infrastructure.
Monitoring and Logging AWS Activities with CloudTrail and Config
Continuous monitoring and logging are essential components of AWS security and compliance. AWS CloudTrail and Config are two services that provide advanced features and functionalities for monitoring and logging AWS activities. AWS CloudTrail is a service that enables organizations to monitor and record account activity related to actions taken on their AWS resources. CloudTrail provides visibility into user activity, API calls, and resource changes across AWS accounts and services. It can be used to detect anomalies, investigate security incidents, and ensure compliance with regulatory requirements.
CloudTrail provides detailed logs that can be used to track API calls, identify who made the calls, when they were made, and the source IP address. CloudTrail logs can be integrated with other AWS services, such as AWS Lambda, Amazon SNS, and Amazon S3, to enable automated responses to security incidents or to trigger alerts when specific events occur.
AWS Config is a service that enables organizations to assess, audit, and evaluate the configurations of their AWS resources. Config provides a detailed inventory of AWS resources, including relationships between resources, and allows organizations to track changes to resource configurations over time.
Config provides a configuration history for each resource, enabling organizations to view changes made to resource configurations, when the changes were made, and who made the changes. Config rules can be used to evaluate the configuration of resources against best practices, regulatory requirements, or custom requirements.
By implementing CloudTrail and Config, organizations can ensure that they have a complete audit trail of all AWS activities and resource configurations, enabling them to detect anomalies, investigate security incidents, and maintain a secure infrastructure. Regular reviews of CloudTrail and Config data can help organizations identify and remediate misconfigurations, thereby achieving AWS Security and Compliance.
How to Secure AWS Storage Services: S3, EBS, and EFS
Securing AWS storage services is crucial in maintaining AWS Security and Compliance. AWS provides several storage services, including Amazon S3, Amazon EBS, and Amazon EFS. In this section, we will focus on best practices for securing these storage services. Amazon S3 (Simple Storage Service) is an object storage service that offers industry-leading scalability, data availability, security, and performance. To secure S3 buckets, organizations should implement S3 bucket policies, access point policies, and access control lists (ACLs). S3 bucket policies enable organizations to allow or deny access to specific users, groups, or IP addresses. Access point policies enable organizations to manage permissions at the bucket level, while ACLs enable organizations to manage permissions at the object level.
Real-world example: A healthcare organization stores sensitive patient data in S3 buckets. To secure the data, the organization implements S3 bucket policies that allow access only to authorized users and IP addresses. The organization also implements access point policies that enable healthcare professionals to access the data they need to provide patient care.
Amazon EBS (Elastic Block Store) is a block storage service that provides persistent storage for Amazon EC2 instances. To secure EBS volumes, organizations should implement EBS encryption, which encrypts data at rest and in transit. Organizations should also implement access control policies that restrict access to authorized users and services.
Real-world example: A financial organization stores sensitive financial data in EBS volumes. To secure the data, the organization implements EBS encryption and access control policies that restrict access to authorized users and services.
Amazon EFS (Elastic File System) is a fully managed file service that makes it easy to set up and scale shared file storage in the cloud. To secure EFS file systems, organizations should implement EFS access control, which enables organizations to manage permissions at the file system level, directory level, and file level. Organizations should also implement VPC security groups and NACLs to restrict access to authorized users and services.
Real-world example: A media organization stores multimedia files in EFS file systems. To secure the files, the organization implements EFS access control and VPC security groups that restrict access to authorized users and services.
By implementing best practices for securing AWS storage services, organizations can ensure that their data is protected and compliant with regulatory requirements. Regular reviews of S3 bucket policies, EBS encryption, and EFS access control can help organizations identify and remediate misconfigurations, thereby achieving AWS Security and Compliance.
Achieving Compliance in AWS: Common Frameworks and Standards
AWS provides a wide range of services and tools that can help organizations achieve and maintain compliance with various regulatory frameworks and industry standards. In this section, we will discuss some of the most common compliance frameworks and standards applicable to AWS, such as PCI DSS, HIPAA, and GDPR. The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. AWS provides a wide range of services that can help organizations achieve and maintain PCI DSS compliance, including Amazon EC2, Amazon VPC, and Amazon S3. To achieve PCI DSS compliance in AWS, organizations should follow best practices such as implementing strong access controls, encrypting sensitive data, and regularly monitoring and logging AWS activities.
The Health Insurance Portability and Accountability Act (HIPAA) is a US law that provides data privacy and security provisions for safeguarding medical information. AWS provides a wide range of services that can help organizations achieve and maintain HIPAA compliance, including Amazon S3, Amazon EC2, and Amazon RDS. To achieve HIPAA compliance in AWS, organizations should follow best practices such as implementing strong access controls, encrypting sensitive data, and regularly monitoring and logging AWS activities.
The General Data Protection Regulation (GDPR) is a regulation in EU law on data protection and privacy in the European Union and the European Economic Area. AWS provides a wide range of services that can help organizations achieve and maintain GDPR compliance, including Amazon S3, Amazon EC2, and Amazon RDS. To achieve GDPR compliance in AWS, organizations should follow best practices such as implementing strong access controls, encrypting sensitive data, and regularly monitoring and logging AWS activities.
To achieve and maintain compliance in AWS, organizations should regularly assess and audit their AWS infrastructure and resources. AWS provides several tools and services that can help organizations with compliance assessments and audits, such as AWS Config, AWS Security Hub, and AWS Audit Manager. These tools can help organizations monitor and report on their compliance posture, identify compliance gaps and misconfigurations, and provide evidence of compliance to auditors.
By following best practices for achieving compliance in AWS, organizations can ensure that their AWS infrastructure and resources are secure, compliant, and meet regulatory requirements. Regular assessments and audits can help organizations identify and remediate compliance gaps and misconfigurations, thereby achieving AWS Security and Compliance.
Utilizing AWS Security Hub for Centralized Security Management
AWS Security Hub is a service that provides centralized security management across AWS accounts and services. It enables organizations to consolidate security alerts, automate compliance checks, and improve their security posture in the cloud. In this section, we will discuss how AWS Security Hub can help organizations achieve AWS Security and Compliance. AWS Security Hub integrates with other AWS security services, such as Amazon GuardDuty, Amazon Inspector, and Amazon Macie, to provide a comprehensive view of an organization’s security posture. It enables organizations to consolidate security alerts and findings from multiple sources, providing a single view of potential security risks. This can help organizations prioritize security responses, reduce response times, and improve their overall security posture.
AWS Security Hub also provides automated compliance checks, enabling organizations to assess their compliance with various regulatory frameworks and industry standards. It supports compliance standards such as PCI DSS, HIPAA, and GDPR, and provides detailed compliance reports that can be used to demonstrate compliance to auditors. Regular assessments and audits can help organizations maintain compliance and reduce the risk of security breaches.
AWS Security Hub provides customizable security automation rules, enabling organizations to automate security responses and reduce the workload of security teams. It also provides integration with AWS Lambda, enabling organizations to create custom security automation workflows. This can help organizations respond quickly to security threats, reduce the attack surface, and improve their overall security posture.
To get started with AWS Security Hub, organizations can enable the service in the AWS Management Console, AWS CLI, or AWS SDKs. They can then configure the service to aggregate security alerts and findings from other AWS security services, and enable automated compliance checks. Organizations can also customize security automation rules and workflows to meet their specific security requirements.
By utilizing AWS Security Hub, organizations can improve their security posture, achieve compliance with regulatory frameworks and industry standards, and reduce the workload of security teams. AWS Security Hub provides a centralized view of security alerts and findings, automated compliance checks, and customizable security automation rules, making it an essential tool for organizations looking to achieve AWS Security and Compliance.
Automating AWS Security with AWS Lambda and CloudFormation
In today’s complex and ever-evolving digital landscape, organizations must prioritize security and compliance within their AWS environments. One of the most effective ways to enhance security and reduce the attack surface is by automating AWS security using services like AWS Lambda and CloudFormation. This approach not only streamlines security management but also ensures consistent enforcement of security policies across the entire AWS infrastructure.
AWS Lambda: Serverless Security Automation
AWS Lambda is a serverless computing service that lets you run your code without provisioning or managing servers. This service can be harnessed to automate security tasks, such as monitoring for anomalous activities, enforcing access controls, and responding to security incidents. By integrating AWS Lambda with other AWS security services, you can create a powerful, automated security solution tailored to your organization’s needs.
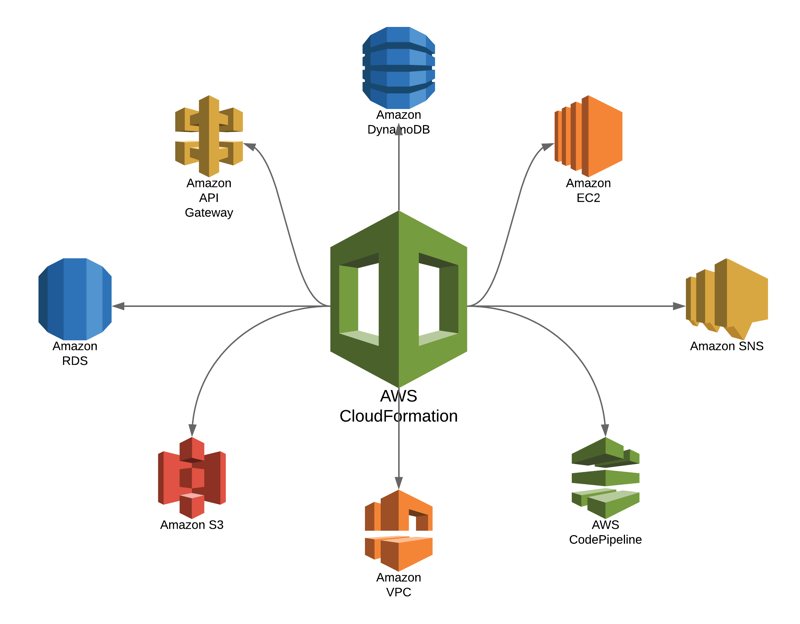
Infrastructure as Code: AWS CloudFormation
AWS CloudFormation is a service that allows you to model and set up your AWS resources in a safe, predictable manner. By treating infrastructure as code, you can version control your AWS resources, manage them across multiple environments, and automate their deployment, configuration, and management. This approach ensures consistent security policies and settings, reducing the risk of misconfigurations and vulnerabilities.
Benefits of Automating AWS Security
Automating AWS security offers numerous benefits, including:
- Reduced human error: By automating repetitive security tasks, you minimize the potential for mistakes and misconfigurations.
- Consistent security policies: Infrastructure as code enables you to enforce security policies consistently across all environments and resources.
- Scalability: Automated security solutions can easily scale to accommodate growing AWS infrastructures without compromising security.
- Cost-effectiveness: Serverless computing and infrastructure as code help you optimize resource usage and minimize costs associated with security management.
- Improved compliance: Automated security solutions can help you maintain compliance with various frameworks and standards, such as PCI DSS, HIPAA, and GDPR, by ensuring consistent enforcement of security policies and regular audits.
Conclusion
Automating AWS security using services like AWS Lambda and CloudFormation is a powerful strategy for enhancing security, reducing the attack surface, and maintaining compliance within your AWS environment. By treating infrastructure as code and automating security tasks, you can ensure consistent enforcement of security policies, minimize human error, and scale security management efficiently. Embrace the potential of serverless computing and infrastructure as code to fortify your AWS security and compliance posture.