What is AWS Network and Security?
AWS network and security refers to the suite of services provided by Amazon Web Services (AWS) to ensure secure data transmission and storage in the cloud. With the increasing adoption of cloud computing, network and security have become critical components of any cloud infrastructure. AWS network and security encompass a wide range of services that provide security at various levels, from the network to the application layer.
At its core, AWS network and security is designed to provide a secure and reliable computing environment for businesses of all sizes. It offers a broad set of policies, technologies, and controls that allow customers to manage their security and compliance needs in the AWS cloud. From protecting data in transit and at rest to managing access to AWS resources, network and security play a vital role in ensuring the confidentiality, integrity, and availability of data in the cloud.
In today’s interconnected world, where data breaches and cyber attacks are becoming increasingly common, AWS network and security provides a robust and secure infrastructure for businesses to operate. By implementing best practices and staying up-to-date with emerging trends, businesses can ensure the security and integrity of their AWS environment, and protect their data from unauthorized access and theft.
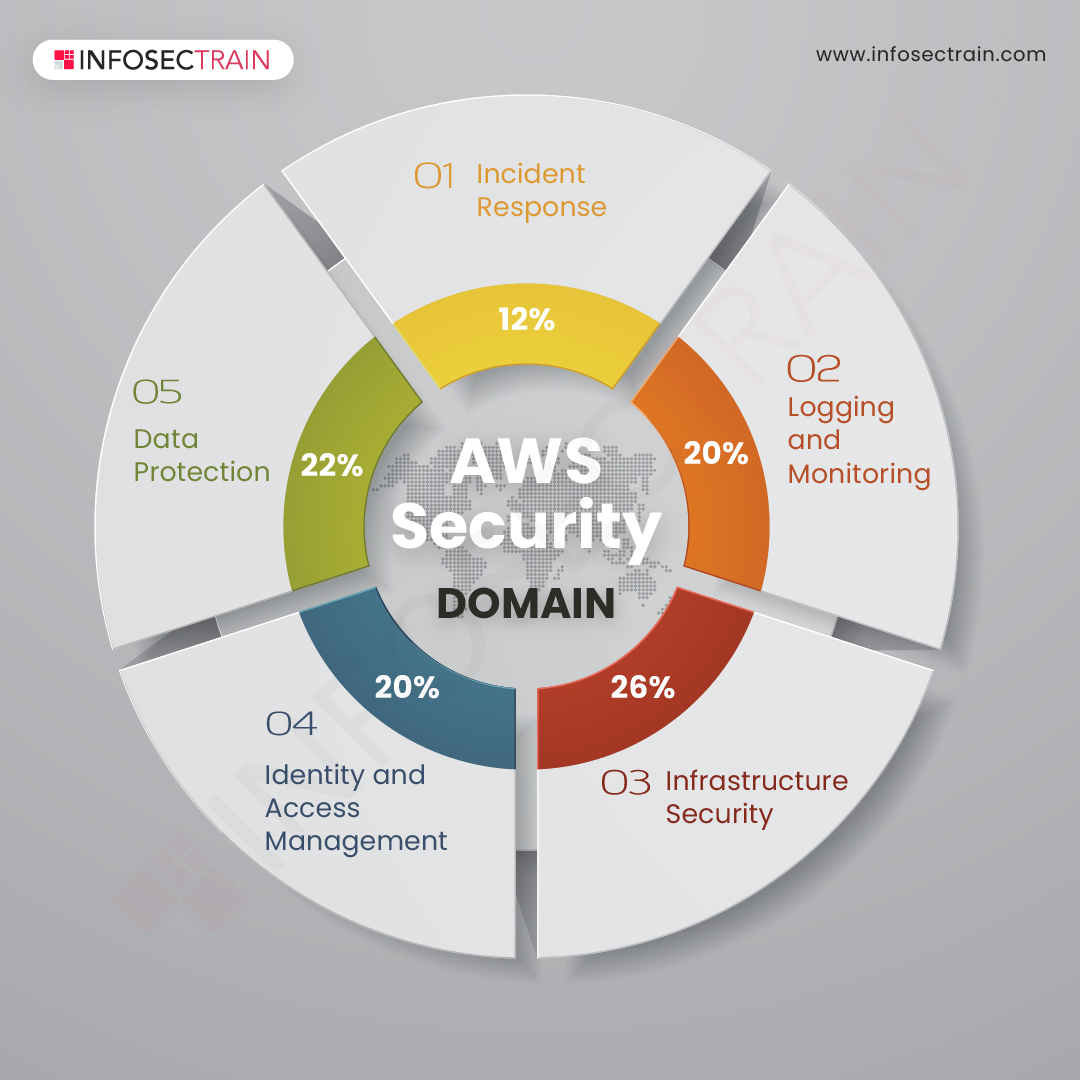
Key Components of AWS Network and Security
AWS network and security is composed of several key components that work together to provide a secure and reliable computing environment. These components include Amazon Virtual Private Cloud (VPC), Amazon Security Groups, and AWS Identity and Access Management (IAM).
Amazon Virtual Private Cloud (VPC)
Amazon VPC is a service that allows customers to launch AWS resources into a virtual network that they define. This virtual network closely resembles a traditional network that you would operate in your own data center, with the benefits of using the scalable infrastructure of AWS. With Amazon VPC, customers can define their own IP address range, create subnets, configure route tables, network gateways, and set up security settings.
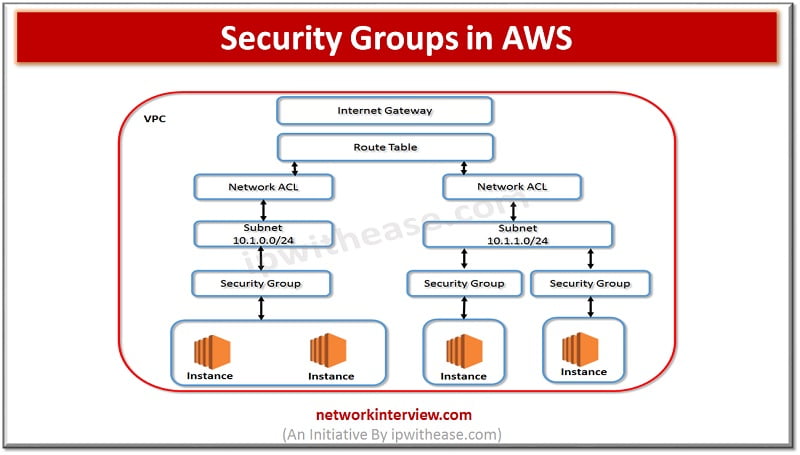
Amazon Security Groups
Amazon Security Groups are a virtual firewall for your Amazon Elastic Compute Cloud (EC2) instances and Amazon RDS instances. They allow customers to control inbound and outbound traffic based on rules that they define. Security groups act at the instance level, not the subnet level. This means that each instance in a subnet in your VPC can have its own set of security rules.
AWS Identity and Access Management (IAM)
AWS IAM is a service that helps customers securely control access to AWS resources. It enables customers to create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources. IAM is a critical component of AWS network and security because it allows customers to manage access to their AWS resources and ensure that only authorized users and services can access them.
By using these key components of AWS network and security, customers can build a secure and reliable computing environment that meets their specific needs. They can define their own virtual network, control traffic to and from their instances, and manage access to their AWS resources, all while taking advantage of the scalability and flexibility of the AWS cloud.
How to Implement AWS Network and Security: A Step-by-Step Guide
Implementing AWS network and security requires careful planning and configuration. Here is a step-by-step guide to help you get started:
Step 1: Create a VPC
The first step in implementing AWS network and security is to create a VPC. This will allow you to define your own virtual network within the AWS environment. When creating a VPC, you will need to specify the IP address range, create subnets, and configure route tables and network gateways.
Step 2: Set Up Security Groups
Once you have created your VPC, the next step is to set up security groups. Security groups act as a virtual firewall for your EC2 instances and RDS instances. You can use security groups to control inbound and outbound traffic based on rules that you define. It is important to ensure that your security groups are configured correctly to prevent unauthorized access to your instances.
Step 3: Configure IAM Policies and Roles
IAM policies and roles are used to control access to your AWS resources. You can use IAM to create and manage users and groups, and use permissions to allow and deny access to your resources. It is important to ensure that your IAM policies and roles are configured correctly to prevent unauthorized access to your AWS resources.
Step 4: Implement Network Segmentation
Network segmentation is the practice of dividing a network into smaller subnetworks. This can help improve security by limiting the scope of any potential security breaches. When implementing network segmentation in AWS, you can use security groups, network ACLs, and subnets to create separate network segments.
Step 5: Enable Data Encryption
Data encryption is the process of converting data into a format that is unreadable by unauthorized users. AWS provides several services that can be used to encrypt data, including Amazon S3 server-side encryption and Amazon EBS encryption. It is important to enable data encryption to protect sensitive data in transit and at rest.
Step 6: Conduct Regular Security Assessments
Regular security assessments are essential to ensure the security and integrity of your AWS environment. You can use AWS security services, such as Amazon Inspector and AWS Security Hub, to conduct security assessments and identify vulnerabilities in your environment.
By following these steps, you can implement AWS network and security in your environment. It is important to ensure that your network and security configuration is reviewed and updated regularly to ensure the security and integrity of your AWS environment.
Best Practices for AWS Network and Security
When it comes to AWS network and security, there are several best practices that businesses should follow to ensure a secure and reliable infrastructure. Here are some of the most important best practices to keep in mind:
Network Segmentation
Network segmentation is the practice of dividing a network into smaller subnetworks. This can help improve security by limiting the scope of any potential security breaches. When implementing network segmentation in AWS, you can use security groups, network ACLs, and subnets to create separate network segments.
Data Encryption
Data encryption is the process of converting data into a format that is unreadable by unauthorized users. AWS provides several services that can be used to encrypt data, including Amazon S3 server-side encryption and Amazon EBS encryption. It is important to enable data encryption to protect sensitive data in transit and at rest.
Regular Security Assessments
Regular security assessments are essential to ensure the security and integrity of your AWS environment. You can use AWS security services, such as Amazon Inspector and AWS Security Hub, to conduct security assessments and identify vulnerabilities in your environment.
IAM Best Practices
IAM policies and roles are used to control access to your AWS resources. It is important to follow IAM best practices, such as using least privilege access, regularly reviewing IAM policies, and using multi-factor authentication (MFA) for all IAM users.
Security Group Best Practices
Security groups act as a virtual firewall for your EC2 instances and RDS instances. It is important to follow security group best practices, such as minimizing the number of rules, using specific IP addresses and ranges, and regularly reviewing security group rules.
VPC Best Practices
When creating a VPC, it is important to follow best practices, such as using non-overlapping IP address ranges, enabling flow logs, and using network access control lists (ACLs) to control traffic between subnets.
Zero Trust Security Models
Zero trust security models assume that any user or system could potentially be compromised, and therefore, verify every request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, the zero trust model requires strict identity verification and access control.
Machine Learning for Threat Detection
Machine learning can be used to detect threats and anomalies in your AWS environment. AWS provides several machine learning services, such as Amazon GuardDuty and Amazon Macie, that can be used to detect threats and improve your security posture.
By following these best practices, businesses can ensure a secure and reliable AWS environment. It is important to regularly review and update your network and security configuration to ensure the security and integrity of your AWS environment.
Real-World Examples of AWS Network and Security
AWS network and security services are used by businesses of all sizes to secure their cloud infrastructure. Here are some real-world examples of how businesses have used AWS network and security to improve their security posture:
Example 1: Netflix
Netflix is a streaming service that uses AWS to run its infrastructure. To ensure the security and integrity of its data, Netflix uses a variety of AWS network and security services, including Amazon VPC, Amazon Security Groups, and AWS IAM. By using these services, Netflix is able to control access to its resources, segment its network, and encrypt its data.
Example 2: Airbnb
Airbnb is a hospitality company that uses AWS to run its infrastructure. To ensure the security and integrity of its data, Airbnb uses a variety of AWS network and security services, including Amazon Inspector, AWS Shield, and AWS WAF. By using these services, Airbnb is able to conduct regular security assessments, protect against DDoS attacks, and filter web traffic.
Example 3: Capital One
Capital One is a financial services company that uses AWS to run its infrastructure. To ensure the security and integrity of its data, Capital One uses a variety of AWS network and security services, including AWS KMS, AWS CloudHSM, and AWS Certificate Manager. By using these services, Capital One is able to encrypt its data, manage cryptographic keys, and manage SSL/TLS certificates.
Example 4: Expedia
Expedia is a travel company that uses AWS to run its infrastructure. To ensure the security and integrity of its data, Expedia uses a variety of AWS network and security services, including Amazon GuardDuty, Amazon Macie, and AWS Security Hub. By using these services, Expedia is able to detect threats, protect against data loss, and conduct regular security assessments.
These are just a few examples of how businesses have used AWS network and security to improve their security posture. By following best practices and staying up-to-date with emerging trends, businesses can ensure a secure and reliable AWS environment.
Comparing AWS Network and Security to Other Cloud Providers
When it comes to cloud computing, security is a top concern for businesses of all sizes. AWS network and security offers a variety of services and features that help ensure the security and integrity of your cloud infrastructure. But how does AWS network and security compare to other cloud providers, such as Microsoft Azure and Google Cloud Platform?
Amazon Virtual Private Cloud (VPC)
Amazon VPC is a service that allows you to launch AWS resources into a virtual network that you define. This virtual network closely resembles a traditional network that you would operate in your own data center, with the benefits of using the scalable infrastructure of AWS. While other cloud providers offer similar services, such as Microsoft Azure Virtual Network and Google Cloud Virtual Private Cloud, AWS VPC is known for its flexibility and ease of use.
Amazon Security Groups
Amazon Security Groups are a virtual firewall for your EC2 instances and RDS instances. They allow you to control inbound and outbound traffic based on rules that you define. While other cloud providers offer similar services, such as Microsoft Azure Network Security Groups and Google Cloud Firewall Rules, AWS Security Groups are known for their simplicity and integration with other AWS services.
AWS Identity and Access Management (IAM)
AWS IAM is a service that helps you securely control access to AWS resources. It enables you to create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources. While other cloud providers offer similar services, such as Microsoft Azure Active Directory and Google Cloud Identity and Access Management, AWS IAM is known for its fine-grained access control and integration with other AWS services.
AWS Network Firewall
AWS Network Firewall is a managed service that makes it easy to deploy essential network protections for your Amazon Virtual Private Cloud (VPC). It provides centralized management, visualization, and logging of your firewall rules and allows you to continuously monitor and manage the security of your network.
While other cloud providers offer similar services, such as Microsoft Azure Firewall and Google Cloud Firewall, AWS Network Firewall is known for its ease of use, integration with other AWS services, and centralized management.
AWS WAF
AWS WAF is a web application firewall that helps protect your web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. It gives you control over which traffic to allow or block to your web applications by defining customizable web security rules.
While other cloud providers offer similar services, such as Microsoft Azure WAF and Google Cloud WAF, AWS WAF is known for its flexibility, ease of use, and integration with other AWS services.
In conclusion, AWS network and security offers a variety of services and features that help ensure the security and integrity of your cloud infrastructure. While other cloud providers offer similar services, AWS network and security is known for its flexibility, ease of use, and integration with other AWS services. By choosing AWS network and security, businesses can have confidence that their cloud infrastructure is secure and reliable.
Emerging Trends in AWS Network and Security
As cloud computing continues to evolve, so do the network and security measures that protect it. AWS network and security is at the forefront of these advancements, constantly innovating to provide the best possible protection for its users. Here are some of the emerging trends in AWS network and security that are shaping the future of cloud security.
Zero Trust Security Models
Traditional security models operate on the assumption that everything inside the network is trustworthy. However, with the increasing number of cyber threats, this model is no longer sufficient. AWS network and security has adopted a zero trust security model, which assumes that all traffic is untrusted and must be verified before granting access. This model helps prevent data breaches and ensures that only authorized users and devices can access sensitive data.
Machine Learning for Threat Detection
Machine learning is becoming increasingly important in threat detection and response. AWS network and security uses machine learning algorithms to analyze network traffic and identify potential threats. This allows for real-time threat detection and response, reducing the risk of data breaches and cyber attacks.
Automated Security Response
AWS network and security offers automated security response capabilities that enable users to quickly and efficiently respond to security threats. This includes automated patching, configuration management, and security group management. Automated security response helps ensure that security measures are always up-to-date and reduces the risk of human error.
Network Segmentation
Network segmentation is a security best practice that involves dividing a network into smaller, isolated segments. AWS network and security offers network segmentation capabilities that allow users to create isolated networks for specific applications or users. This helps prevent lateral movement by attackers and reduces the risk of data breaches.
Data Encryption
Data encryption is a critical component of cloud security. AWS network and security offers encryption capabilities for data at rest and in transit. This includes encryption for Amazon S3, Amazon EBS, and Amazon RDS. Data encryption helps ensure that sensitive data is protected, even in the event of a data breach.
Regular Security Assessments
Regular security assessments are essential for maintaining a secure AWS environment. AWS network and security offers a variety of tools and services for conducting security assessments, including Amazon Inspector, AWS Security Hub, and AWS Config. Regular security assessments help identify vulnerabilities and ensure that security measures are effective.
In conclusion, AWS network and security is constantly evolving to meet the changing needs of cloud computing. By adopting emerging trends such as zero trust security models, machine learning for threat detection, automated security response, network segmentation, data encryption, and regular security assessments, AWS network and security is helping to shape the future of cloud security. It is essential for businesses to stay up-to-date with these trends and implement best practices to ensure the security and integrity of their AWS environment.
Conclusion: The Importance of AWS Network and Security in Cloud Computing
In today’s digital age, cloud computing has become an essential part of many businesses’ IT infrastructure. With the increasing adoption of cloud services, the importance of network and security cannot be overstated. AWS network and security provides a robust and secure environment for businesses to transmit and store their data in the cloud.
In this comprehensive guide, we have discussed the key components of AWS network and security, including Amazon Virtual Private Cloud (VPC), Amazon Security Groups, and AWS Identity and Access Management (IAM). We have also provided a step-by-step guide on how to implement AWS network and security, starting with creating a VPC and setting up security groups, and the importance of configuring IAM policies and roles for secure access to AWS resources.
Moreover, we have outlined best practices for AWS network and security, such as network segmentation, data encryption, and regular security assessments. By following these best practices, businesses can ensure a strong security posture in the AWS environment. We have also provided real-world examples of how businesses have used AWS network and security to secure their cloud infrastructure, highlighting the benefits of these services.
In addition, we have compared AWS network and security to other cloud providers, such as Microsoft Azure and Google Cloud Platform, discussing the unique features and benefits of AWS network and security and how they differentiate from competitors. We have also discussed emerging trends in AWS network and security, such as the adoption of zero trust security models and the use of machine learning for threat detection, and how these trends are shaping the future of cloud security.
In conclusion, AWS network and security is critical for businesses looking to ensure the security and integrity of their cloud infrastructure. By implementing best practices and staying up-to-date with emerging trends, businesses can build a secure and reliable AWS environment. It is essential to prioritize network and security in cloud computing to protect sensitive data and maintain customer trust.