What is AWS-MFA and Why is it Important?
AWS-MFA, or Multi-Factor Authentication, is a security mechanism provided by Amazon Web Services (AWS) to protect user accounts and resources from unauthorized access. By requiring a second form of authentication in addition to a password, AWS-MFA adds an essential layer of protection against cyber threats such as phishing, credential stuffing, and brute force attacks. This second factor is typically a unique, time-based code generated by an MFA device, which can be either a virtual app on a smartphone or a hardware token.
Implementing AWS-MFA is crucial for maintaining the security and integrity of your AWS resources and data. According to a 2021 Data Breach Investigations Report by Verizon, 61% of data breaches involved stolen or weak credentials. By using MFA, you significantly reduce the risk of falling victim to these types of attacks. Furthermore, AWS recommends using MFA for all IAM users that have access to sensitive resources and data.
In summary, AWS-MFA is a powerful security feature that helps protect your AWS resources and data from unauthorized access. By understanding its importance and implementing it effectively, you can significantly enhance your overall AWS security posture.
How to Implement AWS-MFA for Your AWS Account
To enable AWS-MFA for your AWS account, follow these steps:
- Sign in to the AWS Management Console and navigate to the “My Security Credentials” page.
- Under the “Multi-Factor Authentication (MFA)” section, click “Activate MFA.”
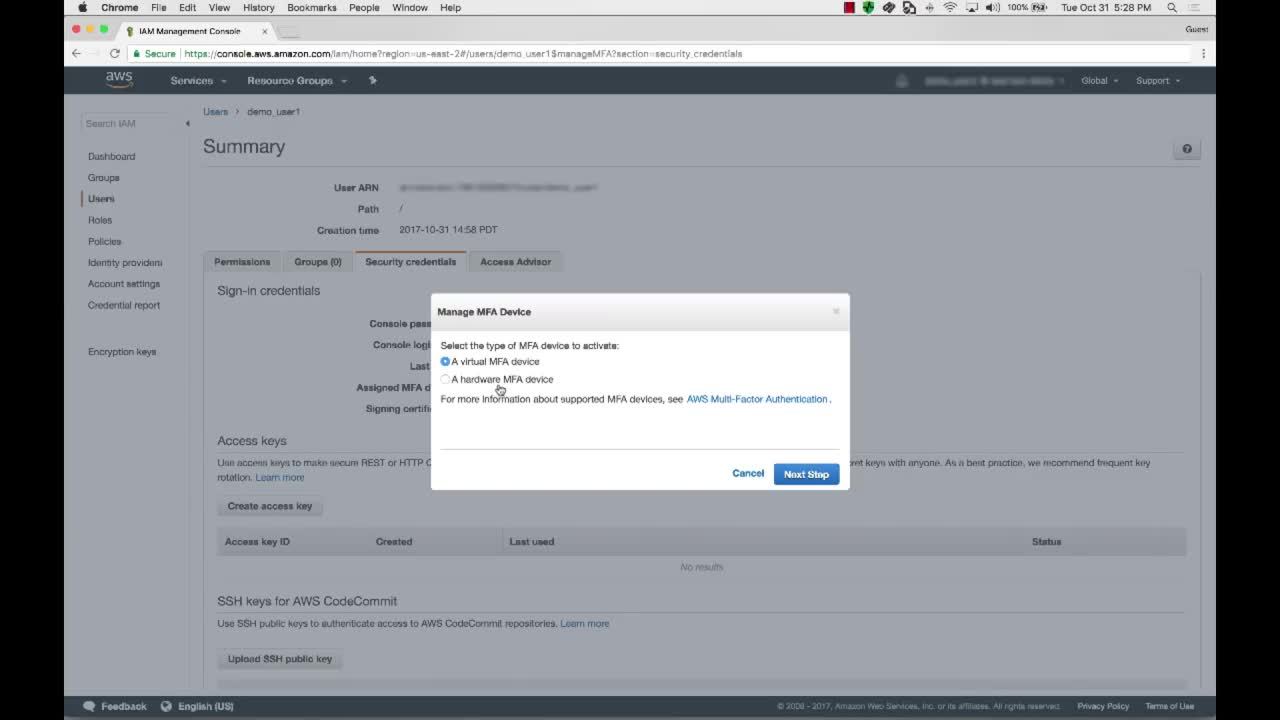
- Select the type of MFA device you want to use (virtual or hardware) and click “Continue.”
- Follow the on-screen instructions to configure your MFA device. For virtual MFA apps, you will typically need to scan a QR code using the app on your smartphone. For hardware tokens, you will need to follow the manufacturer’s instructions.
- Once your MFA device is configured, enter the generated code into the “MFA code” field and click “Assign MFA.”
To further illustrate the process, let’s consider an example using a virtual MFA app like Google Authenticator. After selecting “Virtual MFA device” in step 3, you will be presented with a QR code. Open the Google Authenticator app on your smartphone and click the “+” button to add a new account. Select “Scan a barcode” and scan the QR code displayed on the AWS Management Console. The app will then generate a six-digit code, which you can enter into the “MFA code” field on the AWS Management Console to complete the setup.
By following these steps, you have successfully implemented AWS-MFA for your AWS account. Remember to store your MFA device securely and never share your MFA codes with anyone. Additionally, regularly review your MFA settings and monitor MFA usage to ensure ongoing security and compliance.
MFA Options: Virtual and Hardware Devices
AWS-MFA supports two primary types of devices: virtual and hardware. Understanding the differences between these options can help you choose the best solution for your needs. Both virtual and hardware MFA devices offer robust security, but they have distinct advantages and disadvantages.
Virtual MFA Devices
Virtual MFA devices are software applications installed on smartphones or tablets. Examples include Google Authenticator, Authy, and Microsoft Authenticator. These apps generate time-based one-time passwords (TOTPs) that users must enter, along with their username and password, to access their AWS resources.
- Pros: Virtual MFA devices are convenient, as they do not require any additional hardware. They are also easy to set up and manage, and users can have multiple virtual MFA devices associated with their AWS account.
- Cons: Virtual MFA devices rely on the device’s battery life and internet connectivity. Additionally, if a user loses access to their smartphone or tablet, they may lose access to their AWS resources until they can set up a new virtual MFA device.
Hardware MFA Devices
Hardware MFA devices are physical devices that generate TOTPs or use challenge-response authentication. Examples include YubiKey, SafeNet, and RSA SecurID. These devices typically connect to a user’s computer via USB or NFC and require users to press a button or enter a code to generate the TOTP.
- Pros: Hardware MFA devices are highly secure, as they are not dependent on a user’s smartphone or tablet. They also do not require internet connectivity or battery life, making them ideal for users who travel or work in remote locations.
- Cons: Hardware MFA devices can be more expensive than virtual MFA devices, and users must carry them physically. Additionally, setting up and managing hardware MFA devices can be more complex than virtual MFA devices.
In summary, virtual and hardware MFA devices both offer robust security for AWS resources. Choosing the right option depends on your specific needs and constraints. Virtual MFA devices are more convenient and easier to set up, while hardware MFA devices offer higher security and are less dependent on external factors such as battery life and internet connectivity.
Adding MFA to AWS IAM Users
AWS Identity and Access Management (IAM) enables you to manage access to AWS services and resources securely. Implementing MFA for IAM users and groups is crucial to protect sensitive resources and data. Here’s how to enable MFA for IAM users:
- Sign in to the AWS Management Console and navigate to the IAM dashboard.
- In the navigation pane, choose “Users” and select the user you want to enable MFA for.
- Under “Security Credentials,” choose “Manage MFA Device.”
- Click “Assign MFA Device” and select the type of MFA device you want to use (virtual or hardware).
- Follow the on-screen instructions to configure your MFA device. For virtual MFA apps, you will typically need to scan a QR code using the app on your smartphone. For hardware tokens, you will need to follow the manufacturer’s instructions.
- Once your MFA device is configured, enter the generated code into the “MFA code” field and click “Assign MFA.”
It’s essential to implement MFA for users with access to sensitive resources and data. For example, if a user has permissions to create or modify AWS resources, enabling MFA can prevent unauthorized access and data breaches. Additionally, consider implementing MFA for IAM groups that have similar access requirements, making it easier to manage MFA settings for multiple users.
By following these steps, you have successfully enabled MFA for an IAM user. Remember to store your MFA device securely and never share your MFA codes with anyone. Additionally, regularly review your MFA settings and monitor MFA usage to ensure ongoing security and compliance.
MFA-Protected AWS API Calls
AWS Security Token Service (STS) allows you to make MFA-protected API calls to enhance security in AWS applications and services. MFA-protected API calls require users to provide an MFA code, along with their access key and secret access key, to authenticate the API request. This additional layer of security is particularly useful for sensitive API operations, such as creating or modifying IAM users or accessing billing information.
To make an MFA-protected API call, follow these steps:
- Generate a temporary security credential using the AWS STS
AssumeRoleWithSAMLorAssumeRoleWithWebIdentityAPI operation. Include the MFA token in the request. - Use the temporary security credential to sign the API request.
- Submit the signed API request.
Here’s an example of how to make an MFA-protected API call using the AWS CLI:
$ aws sts assume-role --role-arn arn:aws:iam::123456789012:role/MyRole --role-session-name MySession --serial-number arn:aws:iam::123456789012:mfa/MyUser --token-code 123456 In this example, replace arn:aws:iam::123456789012:role/MyRole with the ARN of the IAM role you want to assume, MySession with a name for the role session, arn:aws:iam::123456789012:mfa/MyUser with the ARN of the MFA device, and 123456 with the MFA token. The assume-role command returns temporary security credentials that you can use to make MFA-protected API calls.
By implementing MFA-protected API calls, you can significantly enhance the security of your AWS applications and services. Regularly review your MFA settings, monitor MFA usage, and educate users about MFA security to ensure ongoing protection against unauthorized access and data breaches.
Troubleshooting Common AWS-MFA Issues
Implementing AWS-MFA can sometimes lead to issues that may hinder the user experience. Here are some common problems and their solutions:
Syncing Issues with Virtual MFA Apps
Virtual MFA apps like Google Authenticator or Authy may experience syncing issues, causing the generated MFA codes to be invalid. To resolve this issue, try the following steps:
- Ensure that the time on your smartphone is accurate. Virtual MFA apps use the time to generate MFA codes. An incorrect time can cause syncing issues.
- Manually synchronize the time on your virtual MFA app. In Google Authenticator, for example, you can tap the three-dot menu next to the affected MFA device and select “Sync now.”
- If synchronization fails, remove the affected MFA device from your virtual MFA app and re-add it. This will generate a new QR code, which you can scan to re-establish the MFA device.
Hardware Token Compatibility
Some hardware tokens may not be compatible with certain AWS services or devices. To ensure compatibility, check the following:
- Verify that your hardware token is on the AWS-supported hardware token list.
- Check the documentation for the specific AWS service you are using to ensure that it supports hardware tokens.
- If your hardware token is not compatible, consider using a virtual MFA app or a different hardware token.
By understanding these common issues and their solutions, you can ensure a smooth implementation of AWS-MFA in your AWS environment. Regularly review your MFA settings, monitor MFA usage, and educate users about MFA security to maintain a secure and compliant AWS infrastructure.
Best Practices for AWS-MFA Implementation
Implementing AWS-MFA is a crucial step in securing your AWS resources and data. To ensure a successful implementation, follow these best practices:
Regularly Review MFA Settings
Regularly review your MFA settings to ensure that they are up-to-date and correctly configured. This includes checking the status of MFA for your AWS account, IAM users, and groups, as well as verifying that MFA is enabled for users with access to sensitive resources and data.
Monitor MFA Usage
Monitor MFA usage to detect any unusual or unauthorized access attempts. This includes tracking MFA activation and deactivation events, as well as monitoring MFA device assignments and removals.
Educate Users about MFA Security
Educate your users about the importance of MFA security and how to use MFA devices effectively. This includes providing guidance on how to set up and use virtual and hardware MFA devices, as well as how to recognize and report suspicious activity.
Implement a Strong Password Policy
Implement a strong password policy to complement your MFA implementation. This includes enforcing password complexity requirements, setting password expiration policies, and limiting password reuse.
Use MFA-Protected API Calls
Use MFA-protected API calls to enhance security in your AWS applications and services. This includes using MFA to authenticate sensitive API operations, as well as implementing MFA-protected access controls for your AWS resources and data.
Regularly Update MFA Devices
Regularly update your MFA devices to ensure that they are running the latest software and firmware. This includes updating virtual MFA apps on your smartphone, as well as updating the firmware on your hardware tokens.
Plan for MFA Device Failure
Plan for MFA device failure by implementing backup and recovery procedures. This includes setting up backup MFA devices for critical users and resources, as well as implementing procedures for recovering lost or stolen MFA devices.
By following these best practices, you can ensure a successful implementation of AWS-MFA in your AWS environment. Regularly review your MFA settings, monitor MFA usage, and educate users about MFA security to maintain a secure and compliant AWS infrastructure.
Staying Updated with AWS-MFA: Latest Features and Improvements
AWS continuously updates its security features and best practices to help users protect their resources and data. Staying informed about the latest AWS-MFA features and improvements can help you maintain a secure and compliant AWS infrastructure.
Virtual MFA App Improvements
AWS has made several improvements to virtual MFA apps, including support for third-party authenticators and the ability to use virtual MFA devices with AWS Single Sign-On (SSO). These improvements make it easier for users to set up and use virtual MFA devices, as well as integrate them with other AWS services.
Hardware Token Improvements
AWS has also improved hardware token support, including support for new hardware token models and the ability to use hardware tokens with AWS SSO. These improvements provide users with more options for securing their AWS resources and data, as well as simplifying the setup and management of hardware tokens.
MFA-Protected API Calls
AWS has expanded support for MFA-protected API calls, including support for additional API operations and services. This allows users to enhance security in their AWS applications and services, as well as meet compliance requirements for sensitive data and resources.
AWS Security Best Practices
AWS regularly updates its security best practices to help users protect their resources and data. Staying informed about these best practices, as well as implementing them in your AWS environment, can help you maintain a secure and compliant infrastructure.
To stay updated with the latest AWS-MFA features and improvements, regularly check the AWS New Releases page and the AWS Security Center. Additionally, consider subscribing to AWS security blogs and newsletters to receive the latest news and updates directly in your inbox.