The Significance of Securing AWS Lambda Secrets
In today’s cloud-native world, securing sensitive data in serverless applications is a critical concern for organizations of all sizes. AWS Lambda, a popular serverless computing service, enables developers to build and run applications without the need for managing servers. However, this also introduces new challenges in managing secrets, such as API keys, database credentials, and encryption keys, that are used in Lambda functions. Securing AWS Lambda secrets is essential to prevent data breaches, unauthorized access, and compliance issues. By implementing robust secret management strategies, organizations can ensure the confidentiality, integrity, and availability of their sensitive data in AWS Lambda.
One of the primary benefits of securing AWS Lambda secrets is reducing the risk of data breaches. Unsecured secrets can provide an easy entry point for attackers, leading to the exposure of sensitive data and potential financial losses. By implementing best practices for secret management, organizations can minimize the risk of data breaches and protect their customers’ data.
Another benefit of securing AWS Lambda secrets is ensuring compliance with industry regulations and standards. Many industries have strict regulations around the handling and storage of sensitive data, and failure to comply can result in hefty fines and reputational damage. By using a secure and compliant secret management solution, organizations can demonstrate their commitment to data security and regulatory compliance.
Implementing robust secret management strategies in AWS Lambda can also improve application performance and reliability. By using secure and up-to-date secrets, organizations can ensure that their applications are running with the latest configurations and settings, reducing the risk of errors and downtime.
In summary, securing AWS Lambda secrets is essential for protecting sensitive data, ensuring compliance, and improving application performance. By implementing best practices for secret management, organizations can minimize the risk of data breaches, reduce the risk of compliance issues, and improve the reliability and security of their serverless applications.
Understanding Secrets in AWS Lambda: Types and Use Cases
Secrets are sensitive data, such as API keys, database credentials, and encryption keys, that are used in AWS Lambda functions to access external resources and services. Secrets are essential for the secure and efficient operation of serverless applications, but they also pose a significant security risk if not managed properly. There are various types of secrets in AWS Lambda, each with its unique use cases and requirements. For example, API keys are used to authenticate and authorize access to external APIs and services, while database credentials are used to connect to databases and other data stores. Encryption keys are used to encrypt and decrypt sensitive data, ensuring its confidentiality and integrity.
Secrets are used in AWS Lambda functions to access external resources and services, such as databases, storage services, and messaging systems. For example, a Lambda function that processes user data might use a secret to authenticate and authorize access to a database or a messaging system. Similarly, a Lambda function that sends emails might use a secret to authenticate and authorize access to an email service.
Secrets are also used in AWS Lambda functions to implement security and compliance controls, such as access controls, auditing, and logging. For example, a Lambda function that handles sensitive data might use a secret to implement access controls, ensuring that only authorized users and processes can access the data. Similarly, a Lambda function that processes compliance-related data might use a secret to implement auditing and logging, ensuring that all access and changes to the data are logged and audited.
In summary, secrets are sensitive data that are used in AWS Lambda functions to access external resources and services, implement security and compliance controls, and ensure the secure and efficient operation of serverless applications. Understanding the different types of secrets and their use cases is essential for implementing robust secret management strategies in AWS Lambda.
AWS Secrets Manager: A Comprehensive Solution for Managing Secrets
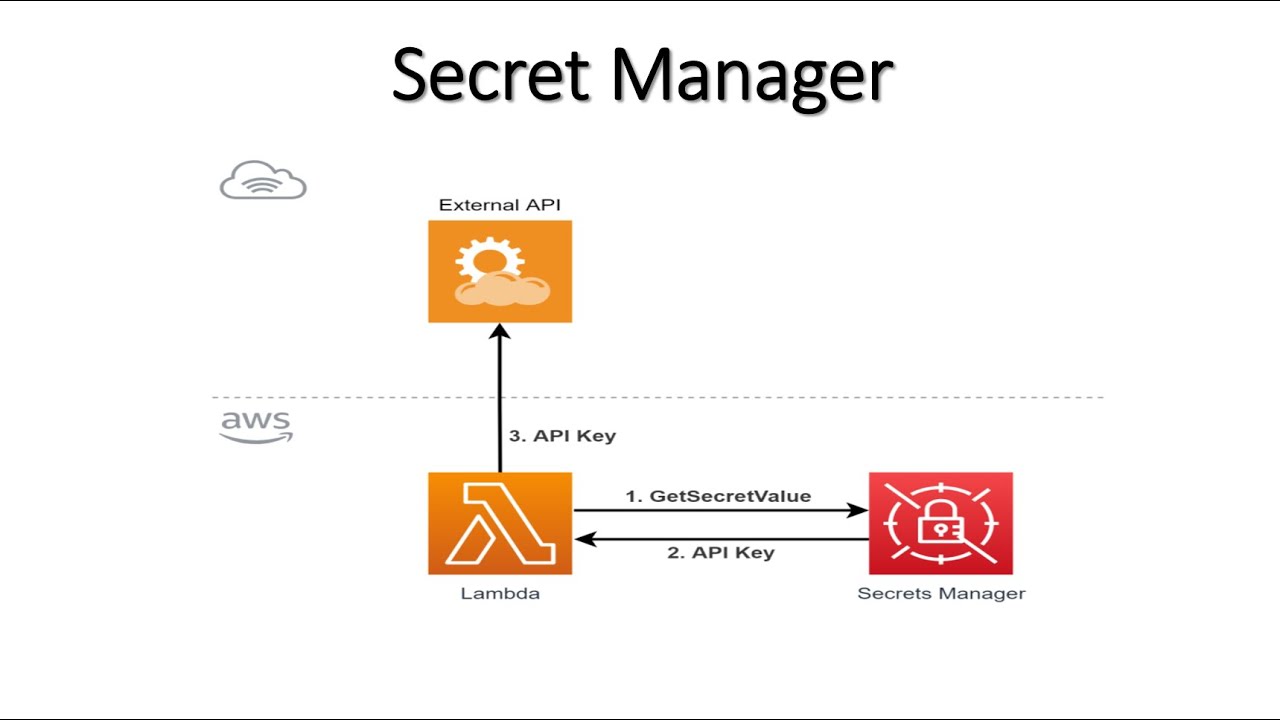
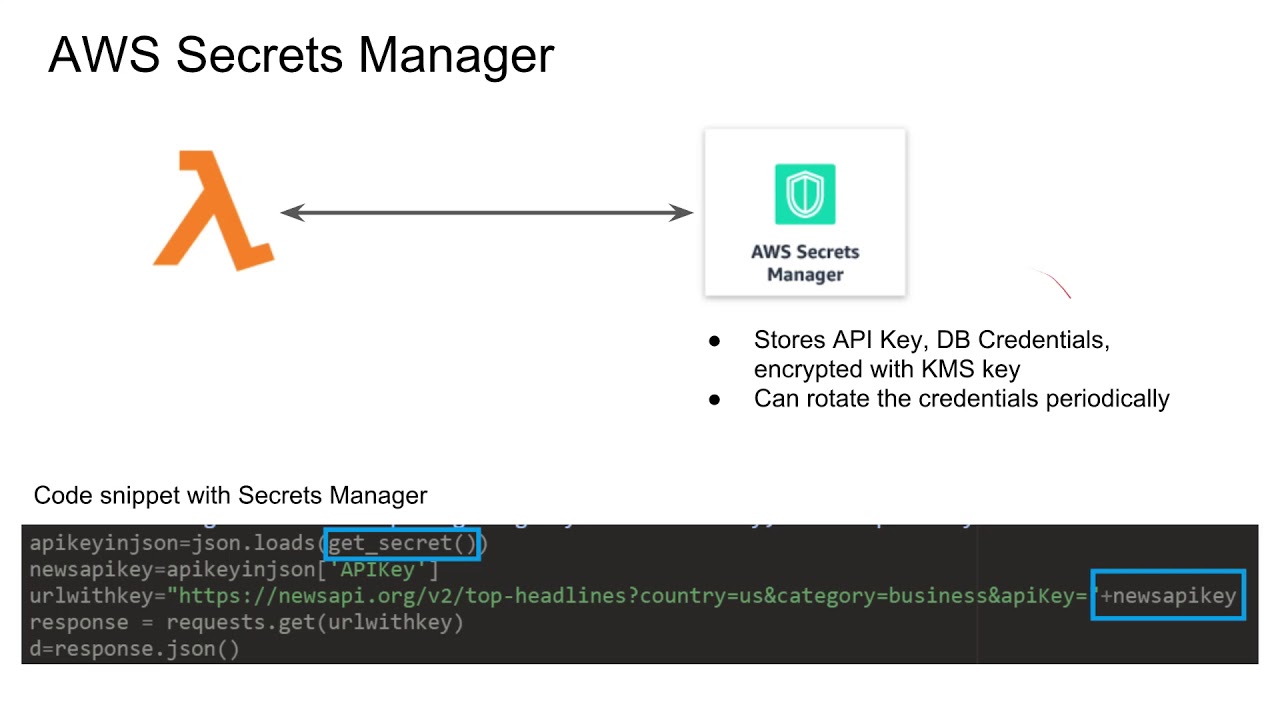
AWS Secrets Manager is a fully managed service that enables organizations to securely store, rotate, and manage secrets in AWS Lambda and other AWS services. Secrets Manager simplifies secret management by providing a centralized and secure repository for storing secrets, automating secret rotation, and integrating with AWS services and applications. Secrets Manager supports various types of secrets, including API keys, database credentials, and encryption keys. Secrets are encrypted at rest and in transit, ensuring their confidentiality and integrity. Secrets Manager also provides access controls and permissions, enabling organizations to restrict access to secrets based on user roles and permissions.
Secrets Manager offers several features that make it an ideal solution for managing secrets in AWS Lambda. For example, Secrets Manager enables organizations to rotate secrets automatically, reducing the risk of credential theft and unauthorized access. Secrets Manager also provides a secure and auditable way to manage secrets, enabling organizations to meet compliance requirements and regulatory standards.
Secrets Manager integrates seamlessly with AWS Lambda, enabling developers to access secrets in Lambda functions securely. Developers can retrieve secrets using the AWS SDK or the Secrets Manager API, ensuring that secrets are always up-to-date and secure. Secrets Manager also provides a dashboard for managing secrets, enabling developers to view, edit, and delete secrets easily.
Secrets Manager has some limitations compared to other secret management solutions. For example, Secrets Manager is only available in certain regions, limiting its availability for global organizations. Secrets Manager also has some limitations in terms of secret rotation, such as the lack of support for custom rotation schedules and the need for manual intervention in some cases.
In summary, AWS Secrets Manager is a comprehensive solution for managing secrets in AWS Lambda and other AWS services. Secrets Manager offers several features, such as automatic secret rotation, access controls, and integrations with AWS services, that make it an ideal solution for managing secrets in serverless applications. However, Secrets Manager also has some limitations, such as regional availability and limitations in secret rotation, that organizations should consider when evaluating secret management solutions.
How to Implement AWS Secrets Manager in AWS Lambda: A Step-by-Step Guide
Implementing AWS Secrets Manager in AWS Lambda is a straightforward process that involves several steps. Here is a step-by-step guide to integrating Secrets Manager with AWS Lambda:
Step 1: Create a Secret in Secrets Manager
The first step is to create a secret in Secrets Manager. This can be done by navigating to the Secrets Manager console, clicking on “Store a new secret,” and following the prompts to create a new secret. Make sure to store the secret in a region that is compatible with your AWS Lambda function.
Step 2: Grant Access to Secrets Manager
The next step is to grant access to Secrets Manager for your AWS Lambda function. This can be done by creating an IAM role that has the necessary permissions to access Secrets Manager. Make sure to grant the IAM role permission to access the specific secret that you created in Step 1.
Step 3: Access Secrets in Lambda Functions
Once you have created the secret and granted access to Secrets Manager, you can access the secret in your AWS Lambda function. This can be done by using the AWS SDK for your preferred programming language. Here is an example of how to access a secret in a Node.js Lambda function:
const AWS = require('aws-sdk'); const secretsManager = new AWS.SecretsManager({ region: 'REGION' }); exports.handler = async (event) => { const secretName = 'SECRET_NAME'; const { SecretString } = await secretsManager.getSecretValue({ SecretId: secretName }).promise(); const secret = JSON.parse(SecretString); // Use the secret in your Lambda function }; Step 4: Configure Access Controls and Permissions
The final step is to configure access controls and permissions for your secret. This can be done by using IAM policies and roles to restrict access to the secret based on user roles and permissions. Make sure to follow the principle of least privilege and only grant access to users who need it.
By following these steps, you can integrate AWS Secrets Manager with AWS Lambda and securely manage secrets in your serverless applications. Remember to follow best practices for managing secrets, such as using encryption, implementing access controls, and monitoring secret usage. This will help you maintain secret hygiene, handle secret rotation and revocation, and respond to secret-related incidents.
Best Practices for Managing Secrets in AWS Lambda
Managing secrets in AWS Lambda is critical to ensuring the security and integrity of your serverless applications. Here are some best practices for managing secrets in AWS Lambda:
Use Encryption
Encrypting secrets is one of the most effective ways to protect them from unauthorized access. AWS Lambda supports encryption at rest and in transit, so make sure to encrypt secrets before storing them in AWS Lambda. You can use AWS Key Management Service (KMS) to manage encryption keys and control access to secrets.
Implement Access Controls
Implementing access controls is essential to preventing unauthorized access to secrets. Use IAM policies and roles to restrict access to secrets based on user roles and permissions. Make sure to follow the principle of least privilege and only grant access to users who need it.
Monitor Secret Usage
Monitoring secret usage is critical to detecting and responding to secret-related incidents. Use AWS CloudTrail and AWS Config to monitor API calls and configuration changes related to secrets. Set up alerts and notifications to notify you of any suspicious activity.
Maintain Secret Hygiene
Maintaining secret hygiene is essential to preventing secret-related incidents. Make sure to regularly review and rotate secrets, and revoke access to secrets that are no longer needed. Use AWS Secrets Manager to automate secret rotation and manage secret lifecycles.
Handle Secret Rotation and Revocation
Handling secret rotation and revocation is critical to maintaining the security and integrity of your serverless applications. Use AWS Secrets Manager to automate secret rotation and manage secret lifecycles. Make sure to test and validate secret rotation and revocation processes to ensure they are working as expected.
Respond to Secret-Related Incidents
Responding to secret-related incidents is essential to minimizing the impact of security breaches. Have a incident response plan in place, and make sure to follow it in the event of a secret-related incident. Use AWS Security Hub to aggregate security alerts and respond to incidents quickly.
By following these best practices, you can effectively manage secrets in AWS Lambda and ensure the security and integrity of your serverless applications. Remember to use encryption, implement access controls, monitor secret usage, maintain secret hygiene, handle secret rotation and revocation, and respond to secret-related incidents. This will help you maintain secret hygiene, prevent secret-related incidents, and respond to incidents quickly and effectively.
Alternatives to AWS Secrets Manager: Comparing Other Secret Management Solutions
While AWS Secrets Manager is a powerful and popular secret management solution for AWS Lambda, it’s not the only option available. Here are some alternatives to AWS Secrets Manager and how they compare:
AWS Systems Manager Parameter Store
AWS Systems Manager Parameter Store is a free service that allows you to securely store and manage configuration data, such as passwords, license codes, and API keys, for your applications and services. It provides basic secret management capabilities, such as access controls and versioning, but lacks some of the more advanced features of AWS Secrets Manager, such as automatic secret rotation and integration with other AWS services.
HashiCorp Vault
HashiCorp Vault is an open-source secret management solution that provides secure storage and management of secrets, tokens, and encryption keys. It offers advanced features, such as dynamic secrets, data encryption, and fine-grained access controls, making it a popular choice for organizations with complex secret management needs. However, it requires more setup and maintenance than managed services like AWS Secrets Manager.
AWS Key Management Service (KMS)
AWS Key Management Service (KMS) is a managed service that enables you to create and manage cryptographic keys for data encryption and decryption. While it’s not a secret management solution per se, it can be used in conjunction with other secret management solutions, such as AWS Secrets Manager or HashiCorp Vault, to provide secure encryption and decryption of secrets.
When choosing a secret management solution for AWS Lambda, consider your specific needs and requirements. If you’re looking for a simple and easy-to-use solution, AWS Systems Manager Parameter Store may be a good fit. If you need more advanced features and capabilities, consider HashiCorp Vault or AWS Key Management Service (KMS) in combination with other secret management solutions.
Remember to follow best practices for managing secrets in AWS Lambda, such as using encryption, implementing access controls, and monitoring secret usage, regardless of the secret management solution you choose. This will help you maintain secret hygiene, prevent secret-related incidents, and ensure the security and integrity of your serverless applications.
Real-World Examples: Securing Sensitive Data in Serverless Applications
Securing sensitive data in serverless applications is a critical concern for organizations of all sizes. Here are some real-world examples of how to secure sensitive data in serverless applications using AWS Secrets Manager or other secret management solutions:
Example 1: Securing Database Credentials
One common use case for secrets in AWS Lambda is securing database credentials. In this example, we’ll show you how to use AWS Secrets Manager to securely store and manage your database credentials, and how to access them in your Lambda functions.
Example 2: Securing API Keys
Another common use case for secrets in AWS Lambda is securing API keys. In this example, we’ll show you how to use AWS Secrets Manager to securely store and manage your API keys, and how to access them in your Lambda functions.
Example 3: Securing Encryption Keys
Securing encryption keys is another critical concern for organizations. In this example, we’ll show you how to use AWS Key Management Service (KMS) in combination with AWS Secrets Manager to securely store and manage your encryption keys, and how to use them to encrypt and decrypt sensitive data in your Lambda functions.
These examples demonstrate the importance of securing sensitive data in serverless applications, and how to use AWS Secrets Manager or other secret management solutions to achieve this goal. By following best practices for managing secrets in AWS Lambda, such as using encryption, implementing access controls, and monitoring secret usage, you can maintain secret hygiene, prevent secret-related incidents, and ensure the security and integrity of your serverless applications.
Future Trends: Advances in Secret Management for Serverless Applications
As serverless applications continue to grow in popularity, so too will the need for robust secret management strategies. Here are some future trends and advances in secret management for serverless applications that you should be aware of:
Trend 1: Automation
Automation is becoming increasingly important in secret management, as it enables organizations to manage secrets at scale and reduce the risk of human error. In the future, we can expect to see more automation in secret management for serverless applications, such as automatic secret rotation, revocation, and access controls.
Trend 2: Machine Learning
Machine learning is another area that is poised to revolutionize secret management for serverless applications. By using machine learning algorithms to analyze secret usage patterns and detect anomalies, organizations can proactively identify and respond to secret-related incidents, reducing the risk of data breaches and unauthorized access.
Trend 3: Decentralization
Decentralization is becoming increasingly important in secret management, as it enables organizations to distribute secrets across multiple environments and reduce the risk of centralized points of failure. In the future, we can expect to see more decentralized secret management solutions for serverless applications, such as blockchain-based secret management platforms and decentralized identity management systems.
To stay up-to-date with these trends and advances in secret management for serverless applications, it’s important to regularly review and update your secret management strategies. Consider attending industry conferences and events, reading industry publications, and participating in online communities to stay informed about the latest developments in secret management.
By staying up-to-date with these trends and advances, you can leverage the latest technologies and best practices to improve your secret management strategies, reduce the risk of data breaches and unauthorized access, and ensure the security and integrity of your serverless applications.