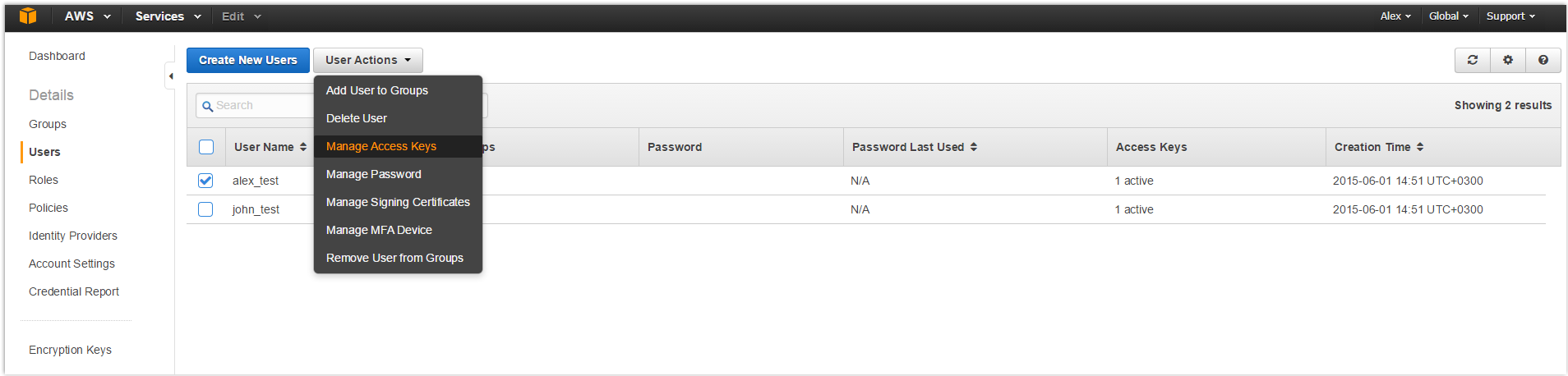
Understanding AWS Secrets Management
Securely managing AWS credentials, particularly access keys, is paramount for protecting your AWS environment. AWS Secrets Manager offers a robust solution for centralizing and controlling access to sensitive information, including database passwords, API keys, and other secrets. The compromise of AWS credentials can lead to unauthorized access, data breaches, and significant financial losses. Therefore, understanding and implementing proper secrets management practices is crucial. Hardcoding credentials directly into application code or storing them in plain text configuration files represents a significant security risk. If these credentials are exposed, malicious actors can gain complete control over your AWS resources.
The ramifications of mishandling AWS credentials extend beyond immediate data breaches. Compliance violations, reputational damage, and legal liabilities can arise from security incidents stemming from compromised access keys. Using AWS Secrets Manager allows for centralized control, enabling features like automatic rotation of secrets, which significantly reduces the window of opportunity for attackers. When properly implemented, it becomes significantly easier to manage access and audit use. Understanding how to securely obtain `aws get secret access key` is a fundamental aspect of maintaining a secure cloud environment. This process must adhere to best practices, leveraging tools like AWS Secrets Manager to mitigate risks associated with credential exposure. Improperly secured credentials can have severe consequences, emphasizing the need for robust security measures.
Instead of embedding secrets directly in code, applications can dynamically retrieve them from AWS Secrets Manager at runtime. This approach minimizes the risk of accidental exposure and simplifies credential management. Furthermore, AWS Secrets Manager integrates seamlessly with other AWS services, such as IAM (Identity and Access Management), allowing for fine-grained control over who can access specific secrets. Access to the `aws get secret access key` should be strictly controlled and monitored. Regular auditing of secret access and rotation policies is essential for maintaining a strong security posture. By prioritizing secure secrets management and understanding the implications of mishandling credentials, organizations can protect their AWS environments from potential threats and maintain the integrity of their data.
How to Retrieve Secrets Using the AWS CLI
This section details how to use the AWS Command Line Interface (CLI) to retrieve secrets stored within AWS Secrets Manager. The AWS CLI provides a direct interface to manage your AWS services. Retrieving secrets involves a simple command structure focused on obtaining the `SecretId`. This is crucial when you need to programmatically or manually retrieve an aws get secret access key.
To retrieve a secret, you will primarily use the `aws secretsmanager get-secret-value` command. The most essential parameter is `–secret-id`, which identifies the specific secret you want to retrieve. Replace `”YourSecretName”` with the actual name or ARN (Amazon Resource Name) of your secret. The basic command structure is:
aws secretsmanager get-secret-value --secret-id "YourSecretName" --region your-aws-region
Remember to replace `”YourSecretName”` and `”your-aws-region”` with your specific secret name and AWS region. The command returns a JSON output containing the secret value. If the secret is stored as a string, the value will be under the `SecretString` key. If stored as binary data, it will be base64 encoded under the `SecretBinary` key. For example, to get an aws get secret access key you might use:
aws secretsmanager get-secret-value --secret-id "prod/database/credentials" --region us-west-2
To extract only the secret value and not the entire JSON response, you can use the `–query` option along with the `jq` command-line JSON processor (if installed). For example, to retrieve the `SecretString` value, you can use:
aws secretsmanager get-secret-value --secret-id "YourSecretName" --region your-aws-region --query SecretString --output text
This command directly outputs the secret value to the console. The `aws get secret access key` command through the CLI is a direct way to interface with AWS Secrets Manager and retrieve the information you need for your applications and services. It is important to remember that the user or IAM role executing the command must have the necessary permissions to access the specified secret. Without the correct permissions, the command will fail, highlighting the importance of properly configured IAM policies.
Leveraging the AWS SDK for Secret Access
The AWS SDK (Software Development Kit) offers a powerful and flexible way to programmatically access secrets stored in AWS Secrets Manager. This approach is essential for applications that require automated retrieval of sensitive information, such as database passwords or API keys. Using the AWS SDK, developers can seamlessly integrate secret management into their code, enhancing security and streamlining deployment processes. The AWS SDKs are available in various programming languages, including Python (Boto3), Java, and Node.js, ensuring broad compatibility with different technology stacks. This approach also ensures a reliable way to securely use aws get secret access key.
To access secrets using the AWS SDK, the application must first authenticate with AWS. This can be achieved through various methods, including IAM roles, access keys, or temporary credentials obtained via STS (Security Token Service). Once authenticated, the application can use the Secrets Manager client to retrieve secrets. For example, in Python using Boto3, the code would look like this:
Best Practices for Storing and Rotating AWS Access Keys
After successfully retrieving an `aws get secret access key`, the immediate concern shifts to its secure storage and lifecycle management. Storing these keys directly in code or configuration files is a significant security risk and should be avoided at all costs. Committing secrets to source control repositories, even private ones, exposes them to potential compromise through accidental leaks or unauthorized access. A compromised `aws get secret access key` could grant attackers complete control over your AWS resources.
Instead of directly embedding credentials, leverage environment variables or dedicated configuration files that are excluded from source control. Environment variables provide a secure and dynamic way to inject secrets into your application at runtime. Configuration files, if used, should be encrypted and stored in a secure location with restricted access. These files should never be committed to version control systems. Remember that even temporary storage of the `aws get secret access key` requires careful consideration. Clear sensitive data from memory as soon as it is no longer needed. Implement mechanisms to prevent secrets from being inadvertently logged or exposed through debugging information.
Regular rotation of access keys is crucial to mitigate the risks associated with compromised credentials. AWS Secrets Manager offers automated secret rotation capabilities, simplifying this process. With automated rotation, new access keys are generated and the old ones are deactivated on a scheduled basis. This reduces the window of opportunity for attackers to exploit compromised credentials. Consider implementing a rotation policy that aligns with your organization’s security requirements. Utilizing IAM roles for EC2 instances and Lambda functions eliminates the need to manage long-term access keys altogether. When a service assumes an IAM role, it receives temporary credentials from the AWS Security Token Service (STS). These temporary credentials automatically expire, reducing the risk of persistent credential compromise and making using `aws get secret access key` directly less necessary.
Alternatives to Long-Term Access Keys: IAM Roles and Temporary Credentials
Long-term AWS access keys, while seemingly convenient, pose a significant security risk if compromised. A more secure approach involves utilizing IAM roles and temporary credentials. This eliminates the need to directly manage and store access keys for services running within the AWS environment. Understanding the weaknesses of long-term keys is the first step in improving your AWS security posture. IAM roles offer a robust alternative by granting permissions to AWS resources, such as EC2 instances and Lambda functions, without requiring explicit access keys. This is a crucial step towards securing aws get secret access key processes.
IAM roles function by assuming a specific set of permissions when an AWS service needs to interact with other AWS resources. For instance, an EC2 instance requiring access to an S3 bucket can assume an IAM role that grants it the necessary permissions. The instance does not need any explicitly configured AWS access key. The AWS infrastructure handles the temporary credential generation and management behind the scenes. This significantly reduces the attack surface, as there are no long-term credentials to potentially expose. Moreover, temporary credentials can be obtained through the Security Token Service (STS). STS enables the creation of temporary, limited-privilege credentials for users or applications. This is particularly useful for scenarios where fine-grained access control is needed or when granting access to external parties. For example, you might use STS to grant a third-party application temporary access to upload files to a specific S3 bucket, without giving them full access to your AWS account. Using roles and temporary credentials avoids storing the aws get secret access key, which minimizes the risks.
Compared to using statically defined AWS access key credentials, leveraging IAM roles and STS for obtaining temporary credentials significantly enhances the security of your AWS environment. These approaches minimize the risk of credential exposure and simplify access management. Adopt these methods as a best practice to secure your AWS resources and to improve overall security. These practices are highly recommended when you want to aws get secret access key. Embrace these alternative methods for enhanced security and simplified management, reinforcing a more robust security strategy.
Troubleshooting Common Issues When Accessing Secrets
Encountering issues while attempting to retrieve secrets is a common experience. One frequent problem involves permission errors. This usually manifests when the IAM role or user lacks the necessary permissions to access the specific secret within AWS Secrets Manager. The error message often states an “Access Denied” or “Unauthorized” condition. To resolve this, verify that the IAM policy attached to the role or user grants the `secretsmanager:GetSecretValue` permission, specifically targeting the `SecretId` of the secret you are trying to access. Remember to implement the principle of least privilege; grant access only to the secrets that are absolutely required.
Another potential pitfall is the use of invalid or expired credentials. This can occur if the AWS CLI or SDK is configured with incorrect access keys or if the session token has expired. Double-check the configured AWS credentials using `aws configure list`. Ensure that the access key ID, secret access key, and region are accurate. If you are using temporary credentials obtained via STS (Security Token Service), verify that the session token is still valid. Regularly rotating your `aws get secret access key` is also crucial to prevent security breaches. A common symptom is receiving “InvalidClientTokenId” or “SignatureDoesNotMatch” errors. If these errors arise, refreshing your credentials or reconfiguring the AWS CLI with valid credentials should address the issue.
Network connectivity problems can also impede the retrieval of secrets. If the EC2 instance, Lambda function, or local machine attempting to access the secret is unable to reach the AWS Secrets Manager service endpoint, a connection timeout or DNS resolution error may occur. Verify that the security group associated with the instance or function allows outbound traffic to the Secrets Manager service endpoint (port 443). Also, confirm that the VPC configuration, including route tables and network ACLs, permits communication with the Secrets Manager endpoint. Furthermore, ensure that DNS resolution is working correctly. If using a VPC endpoint for Secrets Manager, ensure it is correctly configured and associated with the relevant subnet. Resolving network connectivity problems often involves checking firewall rules, security group configurations, and VPC settings to ensure proper communication with AWS services. Remember to regularly review your `aws get secret access key` configurations.
Implementing Least Privilege Access with AWS IAM Policies
The principle of least privilege is a fundamental security concept that dictates granting users or applications only the minimum level of access required to perform their tasks. In the context of AWS Secrets Manager, this means carefully crafting AWS IAM (Identity and Access Management) policies to restrict access to only the necessary secrets. Implementing this principle significantly reduces the risk of unauthorized access and potential data breaches. When configuring access to `aws get secret access key`, meticulous IAM policies are paramount. These policies define who can access which secrets and what actions they can perform. The goal is to ensure that no user or application has broader access than absolutely necessary, thereby limiting the potential impact of a compromised account.
To effectively implement least privilege, begin by identifying the specific secrets each user or application needs to access. Then, create IAM policies that explicitly grant permission to retrieve only those secrets. Avoid using wildcard characters (*) in the `Resource` section of your IAM policies unless absolutely necessary, as this can inadvertently grant broader access than intended. For example, instead of granting access to all secrets, specify the Amazon Resource Names (ARNs) of the individual secrets a user requires. Here’s an example of an IAM policy that grants access to a specific secret:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "secretsmanager:GetSecretValue",
"Resource": "arn:aws:secretsmanager:region:account-id:secret:my-secret"
}
]
}
This policy allows the user to retrieve the value of the secret named “my-secret” in the specified region and account. `aws get secret access key` is governed by such policies, thus securing `aws get secret access key` usage.
Furthermore, consider using IAM roles for EC2 instances, Lambda functions, and other AWS services that need to access secrets. IAM roles provide a secure way to grant permissions to these services without embedding long-term access keys directly in the code or configuration. When a service assumes an IAM role, it receives temporary credentials that are automatically rotated, further reducing the risk of compromised credentials. Regularly review and update your IAM policies to ensure they remain aligned with the principle of least privilege. As your application evolves and access requirements change, adjust the policies accordingly. Tools like AWS IAM Access Analyzer can help identify overly permissive policies and suggest improvements. By diligently implementing least privilege, you can significantly enhance the security of your secrets and minimize the potential impact of security incidents. Remember, properly restricting access to `aws get secret access key` operations is vital for overall security posture. It also helps prevent unintended leakage of `aws get secret access key` and prevents any malicious attacks.
Monitoring and Auditing Secret Access with CloudTrail and CloudWatch
AWS CloudTrail and CloudWatch provide powerful tools for monitoring and auditing access to secrets managed within AWS Secrets Manager. By leveraging these services, organizations can gain valuable insights into who is accessing secrets, when they are being accessed, and from where. This enhanced visibility is crucial for maintaining a strong security posture and detecting potential security breaches. CloudTrail records API calls made to AWS services, including Secrets Manager. This allows you to track every request to retrieve, create, update, or delete secrets. Examining CloudTrail logs enables identification of the user or application that made the request, the source IP address, and the timestamp of the event. Analyzing these logs is essential for identifying any unauthorized or suspicious activity related to your secrets. To effectively monitor secret access, configure CloudTrail to log all Secrets Manager events to an S3 bucket. This ensures that you have a comprehensive record of all activity for auditing and analysis. Regular review of these logs is a key component of a robust security strategy, helping to identify potential vulnerabilities and respond quickly to security incidents where someone tried to aws get secret access key.
CloudWatch complements CloudTrail by providing real-time monitoring and alerting capabilities. You can create CloudWatch alarms based on metrics derived from CloudTrail logs to detect specific events, such as failed access attempts or unusual access patterns. For example, an alarm can be configured to trigger when there are multiple failed attempts to retrieve a specific secret within a short period. This could indicate a potential brute-force attack or an application misconfiguration. When an alarm is triggered, CloudWatch can send notifications via email or other channels, allowing security teams to investigate the issue promptly. Consider setting up alarms for actions such as secret deletion, modification of secret policies, and access from unusual geographic locations. These alarms help in detecting and responding to potentially malicious activity involving your secrets. Monitoring `aws get secret access key` is key.
Analyzing CloudTrail logs provides valuable insights into patterns of `aws get secret access key`. To streamline the analysis process, consider using AWS Athena to query CloudTrail logs stored in S3. Athena allows you to use SQL to efficiently search and filter log data, making it easier to identify specific events or trends. For example, you can use Athena to determine which users have accessed a particular secret over a specific period. This information can be used to identify potential insider threats or to verify that access permissions are being enforced correctly. Additionally, CloudWatch Logs Insights can be used to interactively search and analyze CloudTrail logs. Logs Insights provides a powerful query language that allows you to quickly identify specific events and patterns. Regularly reviewing CloudTrail logs and CloudWatch alarms is essential for maintaining the security and integrity of your secrets and ensuring compliance with regulatory requirements. Properly configured monitoring tools allow for the quick detection and mitigation of any unauthorized attempts to `aws get secret access key`.