Understanding Endpoint Security in Cloud Computing
Cloud computing, and specifically AWS (Amazon Web Services), relies heavily on endpoints for communication and data transfer. An endpoint is essentially any point of access to AWS resources. These points, whether APIs or network interfaces, are critical targets for malicious actors. Effective aws endpoint security is crucial for maintaining data integrity, ensuring service availability, and preventing unauthorized access. Protecting these entry points is fundamental to a robust cloud security strategy.
Protecting endpoints in the AWS ecosystem requires a deep understanding of the potential attack vectors. Endpoints serve as crucial gateways, connecting users and applications to AWS services. Vulnerabilities in these endpoints can lead to a cascade of security breaches, potentially impacting applications and compromising data. A detailed knowledge of these attack vectors is essential for formulating a robust security posture. Comprehensive security analysis of AWS endpoints is critical for maintaining the confidentiality and integrity of data transactions.
The role of endpoints in the broader cloud architecture is paramount. Endpoint security strategies must consider potential threats like malicious software, network intrusions, and configuration errors. Strong security protocols are essential to maintain the confidentiality and integrity of data traversing these entry points. Secure communications are essential for protecting sensitive information during transfer between AWS services and clients. Proper protection of aws endpoints is a fundamental component of any successful cloud security strategy, ensuring the stability and reliability of cloud services.
Key AWS Endpoint Security Threats
Numerous threats jeopardize AWS endpoint security. Malicious actors often exploit vulnerabilities to gain unauthorized access. Common attacks include denial-of-service (DoS) assaults and distributed denial-of-service (DDoS) attacks, aiming to overwhelm systems. Improper configuration of AWS services also presents a significant risk. Misconfigured security groups or insufficient access controls enable unauthorized access to sensitive data. Vulnerabilities within AWS services themselves can lead to breaches. These weaknesses demand proactive measures to maintain robust AWS endpoint security.
Data breaches can result from insecure API calls, which expose sensitive information. Insufficient authentication and authorization mechanisms also contribute to security risks. Software vulnerabilities, both within AWS services and deployed applications, can be exploited. Third-party integrations can expose vulnerabilities if not carefully vetted and managed. Researchers frequently discover vulnerabilities, necessitating regular updates and security patches. Implementing robust security protocols is essential for mitigating these risks and maintaining a strong defense. Robust and multifaceted security measures are critical to bolstering AWS endpoint security.
Phishing attacks, social engineering schemes, and insider threats pose significant risks to AWS endpoint security. Protecting against these requires education and awareness programs. Implementing strong security policies, regular audits, and proactive monitoring are essential to detect and respond to threats effectively. To maintain the integrity of AWS endpoints, organizations must prioritize consistent security vigilance. A layered defense strategy and careful consideration of all possible attack vectors are crucial aspects of strong AWS endpoint security practices.
AWS Services for Endpoint Protection
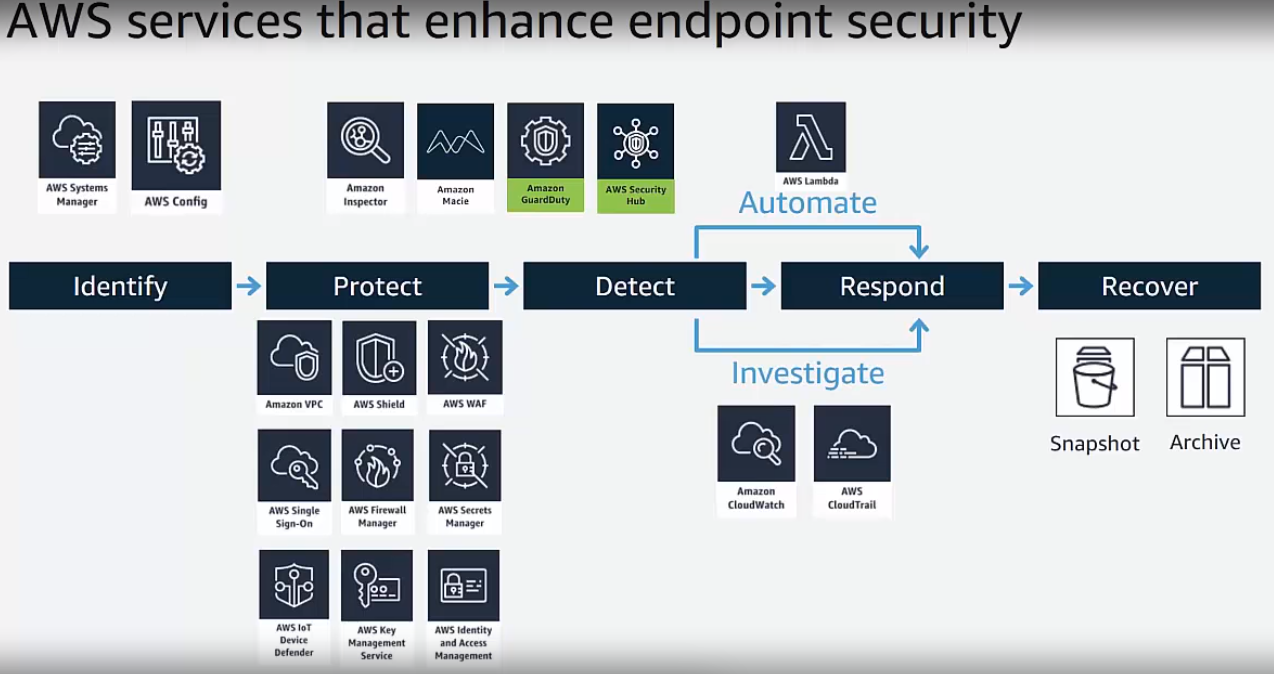
AWS offers a robust suite of services dedicated to bolstering aws endpoint security. These services proactively mitigate risks and enhance the overall security posture of AWS endpoints. AWS WAF (Web Application Firewall), for example, safeguards applications by filtering malicious traffic. CloudFront, a content delivery network, acts as a crucial layer of defense, distributing traffic and protecting origin servers from attack. Furthermore, various security features within other AWS services help fortify specific endpoints against threats.
These AWS-provided services represent a critical component of the layered security approach that is essential for protecting aws endpoint security. By implementing these services, organizations can effectively reduce vulnerabilities and enhance their resilience against a range of potential threats. Beyond leveraging AWS’s built-in security, integrating appropriate security policies and configurations within the user’s deployments plays an essential role in further enhancing the overall security posture of aws endpoint security.
AWS services like Amazon Inspector, Shield, and Macie actively detect and respond to potential threats. These services represent different aspects of a multi-faceted approach to aws endpoint security. Implementing these services effectively enhances the comprehensive security framework. Users should meticulously review and configure these services to align with their specific security requirements. The judicious use of these tools can significantly contribute to the protection of valuable resources within AWS environments and will improve the protection of aws endpoint security.
Best Practices for AWS Endpoint Security Configuration
Securing AWS endpoints requires a multi-layered approach. Implementing robust security measures is crucial to mitigating threats and maintaining the integrity of data flowing through these critical points of access. Effective AWS endpoint security configuration involves careful planning and execution of various strategies. Prioritizing and implementing these practices can significantly bolster the security posture of AWS deployments. Understanding the practical considerations in AWS endpoint security is vital to maintaining data safety and compliance.
A cornerstone of AWS endpoint security is the proper configuration of Identity and Access Management (IAM) roles and policies. Restricting access to only necessary resources is paramount. Implementing least privilege access is crucial to limit the damage potential in the event of a compromise. By utilizing specific IAM roles and policies, organizations can ensure that only authorized individuals and applications can access and interact with AWS resources. Furthermore, employing network security groups (NSGs) acts as a critical defensive line. Carefully defining and implementing NSGs for different AWS services offers precise control over incoming and outgoing traffic. NSGs play a crucial role in AWS endpoint security, blocking unauthorized access and enhancing data integrity. Implementing encryption for data in transit and at rest is essential for protecting sensitive information traversing AWS endpoints. Data encryption ensures confidentiality, even if an unauthorized party gains access to the data. By adopting comprehensive data encryption, organizations significantly enhance the security posture of their AWS endpoints. Leveraging robust and consistent security measures such as these is vital to fortifying AWS endpoint security across the entire infrastructure.
Comprehensive security measures and diligent configuration of AWS endpoints are indispensable components of a robust AWS endpoint security strategy. Organizations benefit from adopting these best practices to protect against malicious actors and maintain data integrity. By prioritizing security configurations, organizations enhance overall AWS endpoint security and minimize potential vulnerabilities. This approach not only protects data but also safeguards the reputation and business continuity of the organizations relying on the cloud platform. Implementing these strategies demonstrates a commitment to safeguarding AWS endpoints and ensuring data security within the cloud environment. These vital elements of AWS endpoint security configuration contribute significantly to a secure and reliable cloud environment.
Implementing a Robust AWS Endpoint Security Strategy
A robust AWS endpoint security strategy necessitates a layered approach. This involves proactive measures to anticipate and mitigate potential threats, alongside reactive responses to incidents. Regular security audits are crucial. These audits should encompass all aspects of endpoint security configurations. Employing automated tools can significantly streamline this process. Thorough assessments of current configurations against best practices are essential. This helps pinpoint vulnerabilities and ensure optimal protection for AWS endpoints. Proactive monitoring is paramount. It’s vital to actively monitor endpoint activity for unusual patterns, which could signal malicious activity. Security information and event management (SIEM) systems can automate this process, helping identify potential threats early. Developing incident response plans is another critical element. These plans should detail procedures for handling security incidents promptly and effectively. This ensures a rapid and coordinated response in the event of a security breach. Maintaining compliance with industry standards, like PCI DSS, is also necessary. This demonstrates a commitment to high security standards and protects sensitive data.
Establishing a secure framework requires ongoing vigilance. This includes implementing measures for data loss prevention (DLP) and regular patching of vulnerabilities. Regular training sessions for personnel on security best practices are essential. This fosters a security-conscious culture and empowers employees to identify and report suspicious activities. Monitoring for anomalous activities is critical. Automated tools for threat detection and response enhance this process. A strong security culture is vital. Encouraging proactive reporting of security concerns is important. Integrating security into the overall development lifecycle is also essential. Building secure applications from the outset reduces the risk of vulnerabilities later in the AWS endpoint security lifecycle. This layered approach fosters continuous improvement and resilience against evolving threats in the AWS environment.
Continuous monitoring and auditing are key components of a strong AWS endpoint security strategy. Regularly review and update security policies and configurations. Establish reporting mechanisms that facilitate quick communication during security events. Maintaining clear communication channels among security teams and relevant stakeholders is crucial. Regularly reviewing and improving the incident response plan is equally important. This ensures effectiveness in handling security incidents. This proactive approach is critical to sustaining a strong AWS endpoint security posture. By combining proactive security measures and responsive incident handling strategies, organizations can significantly reduce the risk of successful attacks and mitigate potential damage to the AWS ecosystem. This holistic approach guarantees a secure environment.
How to Choose the Right Security Tools for AWS Endpoints
Selecting the appropriate security tools for AWS endpoint security is crucial. A well-informed decision hinges on understanding specific requirements and budget constraints. Assess the unique characteristics of each tool before making a choice. Evaluate the tool’s ability to meet the specific needs of an AWS environment. Consider factors like scalability, integration capabilities, and ease of implementation.
AWS offers a suite of services designed for robust endpoint security. Users should evaluate these services alongside third-party options. Evaluate cost-effectiveness and compatibility with existing infrastructure. Analyzing the pros and cons of different security solutions helps determine the best fit for the organization. Prioritize tools with demonstrably strong performance, reliability, and scalability to safeguard AWS endpoints. A careful evaluation can lead to the selection of optimal tools for enhanced security posture in a robust AWS environment. The choice of security tools directly influences the overall success of an AWS endpoint security strategy.
A balanced approach considers both AWS-provided services and third-party solutions. Carefully weigh the benefits of each option in relation to the specific requirements of the organization. Understand the capabilities and limitations of various security tools. Evaluate their effectiveness in safeguarding against potential threats in AWS endpoint security. Making informed choices will effectively safeguard valuable data and resources. By strategically selecting the right tools, organizations can confidently maintain a high level of security throughout their AWS endpoints.
Monitoring and Auditing AWS Endpoint Security
Continuous monitoring of endpoint activity and meticulous auditing of configurations are critical components of a robust AWS endpoint security strategy. Effective monitoring tools are essential for detecting anomalies and potential breaches promptly. These tools should proactively flag deviations from established baselines, allowing for swift intervention. Identifying suspicious activities early is paramount to minimizing potential damage. Automated alerts for potential security issues, such as unusual login attempts or suspicious traffic patterns, should be configured. Regular auditing of AWS security configurations is crucial, ensuring policies are correctly applied and resources remain secure. This includes reviewing access permissions to sensitive data, scrutinizing network security groups, and validating the security posture of all AWS endpoints. Auditing should encompass all key aspects of endpoint protection. Tools for automated security audits can significantly improve the process’s effectiveness and efficiency. Proactive measures like this form a strong defensive line against malicious attacks and misconfigurations within AWS endpoint security.
Crucial to a successful monitoring strategy is choosing the right monitoring tools for specific needs. AWS offers several built-in services for this purpose, such as CloudTrail and CloudWatch Logs. These services provide a comprehensive audit trail of user activity and allow for detailed analysis of events. External tools and platforms can complement AWS’s native solutions, offering deeper visibility into endpoint security activities. Integrating these tools effectively ensures a comprehensive security picture of your AWS deployments, allowing for comprehensive analysis of security incidents and identifying trends for proactive risk mitigation. The data gathered through monitoring and auditing serves as the foundation for adjusting security controls and improving the overall AWS endpoint security posture. Compliance requirements are essential and often dictate specific monitoring and auditing procedures. Regular reporting of security findings and compliance status is critical for maintaining a trustworthy and compliant AWS environment.
An important aspect of ongoing AWS endpoint security is maintaining compliance with industry regulations and best practices. Adherence to established standards, such as PCI DSS or HIPAA, often necessitates specific monitoring and auditing procedures. Regular security reviews and penetration testing exercises, even internal ones, enhance understanding of potential vulnerabilities and help in strengthening the overall AWS endpoint security infrastructure. By understanding the security posture and proactively addressing potential vulnerabilities, organizations can significantly reduce the risk of security breaches and maintain a robust AWS endpoint security framework. Documentation of auditing procedures and results is vital for future reference and improvement. It also provides evidence of ongoing efforts to maintain the security of AWS endpoints and compliance.
Real-World Examples of AWS Endpoint Security Failures and Successes
Examining successful and failed implementations of AWS endpoint security strategies provides valuable insights. Understanding these real-world scenarios allows readers to apply lessons learned in their own AWS deployments. A well-structured approach to AWS endpoint security is critical. A significant portion of the strategies in AWS endpoint security are proactive, rather than reactive.
One example of a security failure involves a misconfigured AWS S3 bucket. Lack of proper access controls allowed unauthorized access to sensitive data. This demonstrates the importance of meticulous IAM (Identity and Access Management) role and policy configurations. A significant part of AWS endpoint security involves proper configuration. Many failures and successes revolve around these configurations. A successful implementation, on the other hand, showcases a company’s proactive security controls. For instance, a company leveraging AWS WAF (Web Application Firewall) prevented a DDoS (Distributed Denial-of-Service) attack targeting its API endpoints. This demonstrates proactive measures in AWS endpoint security that can prevent breaches.
Another hypothetical scenario illustrates the benefits of encryption. A company experienced a data breach due to unencrypted data stored in an unsecured database. In contrast, a company that implemented robust encryption throughout its AWS infrastructure, from data in transit to data at rest, experienced no security compromise. This highlights the necessity of encrypting data at every stage for optimal AWS endpoint security. AWS endpoint security best practices and techniques are widely available, allowing companies to take proactive measures and prevent failures. Thorough audits and meticulous security procedures can lead to considerable success in AWS endpoint security.