Understanding AWS Access Key ID
An AWS Access Key ID is a unique identifier that grants secure access to AWS services. It is a crucial component of AWS Identity and Access Management (IAM) and is used in conjunction with a secret access key to authenticate API requests. Proper management and security measures for AWS Access Key ID are essential to ensure the safety and integrity of your AWS resources.
Creating an AWS Access Key ID
To create an AWS Access Key ID, follow these steps:
- Sign in to the AWS Management Console.
- Open the IAM console at https://console.aws.amazon.com/iam/.
- In the navigation pane, choose Users.
- Choose the name of the user for whom you want to create an access key.
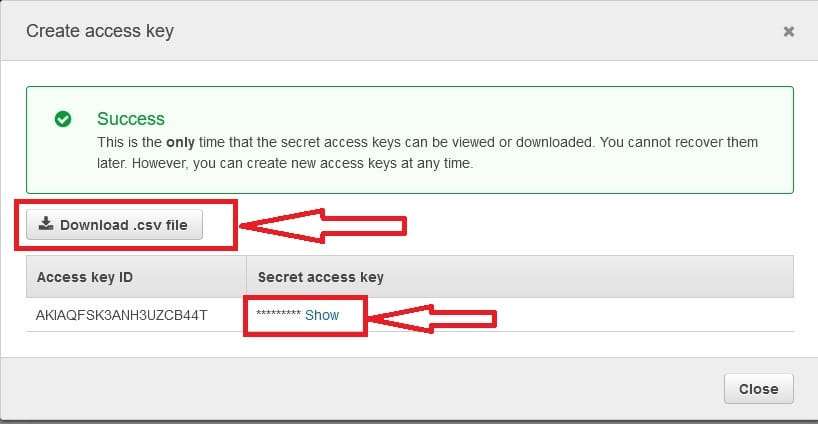
- Choose the Security Credentials tab, and then choose Create access key.
- A pop-up window will appear with the access key and secret access key. Save this information securely, as you will not be able to retrieve the secret access key again.
When creating an AWS Access Key ID, it is essential to follow these precautions:
- Do not share your AWS Access Key ID and secret access key with anyone.
- Store your access keys securely, using tools like AWS Systems Manager Parameter Store or AWS Secrets Manager.
- Limit the number of users with access keys and ensure they are only granted to those who require them for specific tasks.
- Regularly review and monitor access key usage to detect any unauthorized or suspicious activity.
Securing Your AWS Access Key ID
To enhance the security of your AWS Access Key ID, consider the following methods:
- Using IAM roles: IAM roles allow you to delegate access to users or services that need to perform specific tasks. By using IAM roles, you can avoid the need to share or manage Access Key IDs and secret access keys.
- Using temporary security credentials: Temporary security credentials provide access to AWS services for a limited time, reducing the risk of unauthorized access if a user’s credentials are compromised. You can generate temporary security credentials using AWS Security Token Service (STS).
- Following best practices for access key management: Implementing best practices for access key management can help ensure the security of your AWS resources. These practices include:
- Regularly reviewing and rotating access keys.
- Monitoring and auditing access key usage.
- Restricting access keys to specific IP addresses or ranges.
- Disabling access keys that are no longer needed.
- Implementing multi-factor authentication (MFA) for IAM users.
How to Rotate Your AWS Access Key ID
Rotating your AWS Access Key ID is a critical security practice that helps prevent unauthorized access to your AWS resources. The recommended frequency for rotation is every 90 days, but you can rotate your Access Key ID more frequently if needed.
To rotate your AWS Access Key ID, follow these steps:
- Create a new Access Key ID: Log in to the AWS Management Console, navigate to the IAM dashboard, and create a new Access Key ID.
- Update your applications and scripts: Update your applications and scripts to use the new Access Key ID. Test the applications and scripts to ensure they are functioning correctly.
- Test access to AWS services: Verify that you can still access AWS services using the new Access Key ID.
- Disable the old Access Key ID: Once you have confirmed that the new Access Key ID is working correctly, disable the old Access Key ID. This prevents any unauthorized access using the old key.
By rotating your AWS Access Key ID regularly, you can ensure the security of your AWS resources and maintain the integrity of your AWS environment. It is essential to update all applications and scripts that use the Access Key ID and test access to AWS services to ensure a smooth transition.
Monitoring Access to Your AWS Access Key ID
Monitoring access to your AWS Access Key ID is crucial to maintaining the security of your AWS environment. Regular monitoring can help you detect any unauthorized access or suspicious activity, allowing you to take prompt action to prevent data breaches or other security incidents.
There are several tools and techniques available for monitoring Access Key ID usage. Here are some of the most effective methods:
- AWS CloudTrail: AWS CloudTrail is a service that enables you to monitor and record API calls made to your AWS resources. By enabling CloudTrail, you can track all API calls made using your Access Key ID, including the date, time, and source IP address. This can help you identify any unauthorized or suspicious activity and take appropriate action.
- AWS Config: AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. By using AWS Config, you can track changes to your Access Key ID settings and configurations, helping you maintain compliance with your organization’s security policies.
- AWS Identity and Access Management (IAM) access advisor: The IAM access advisor is a tool that helps you visualize and understand the permissions associated with your Access Key ID. By using the access advisor, you can identify any unused or underutilized permissions, helping you reduce the risk of unauthorized access.
By regularly monitoring your Access Key ID usage and implementing these tools and techniques, you can maintain the security of your AWS environment and prevent unauthorized access or data breaches.
Revoking and Deleting AWS Access Key ID
Revoking and deleting an AWS Access Key ID is an essential part of managing your AWS security. Revoking an Access Key ID immediately stops it from granting access to AWS services, while deleting it permanently removes it from your AWS account. Here are the steps to revoke and delete an Access Key ID:
- Sign in to the AWS Management Console.
- Open the IAM dashboard.
- In the navigation pane, choose Access keys.
- Select the Access Key ID you want to revoke or delete, and then choose Revoke or Delete.
- Confirm the action by choosing Yes, Delete or Yes, Revoke.
It is recommended to revoke an Access Key ID before deleting it, as this will immediately stop it from granting access to AWS services. Once revoked, you can then delete the Access Key ID permanently.
Here are some scenarios when you should consider revoking or deleting an Access Key ID:
- If an employee or contractor with access to your AWS account leaves your organization.
- If you suspect an Access Key ID has been compromised or is being used without your authorization.
- If you have not used an Access Key ID for an extended period.
By regularly reviewing and managing your Access Key IDs, you can maintain a secure AWS environment and prevent unauthorized access to your AWS services.
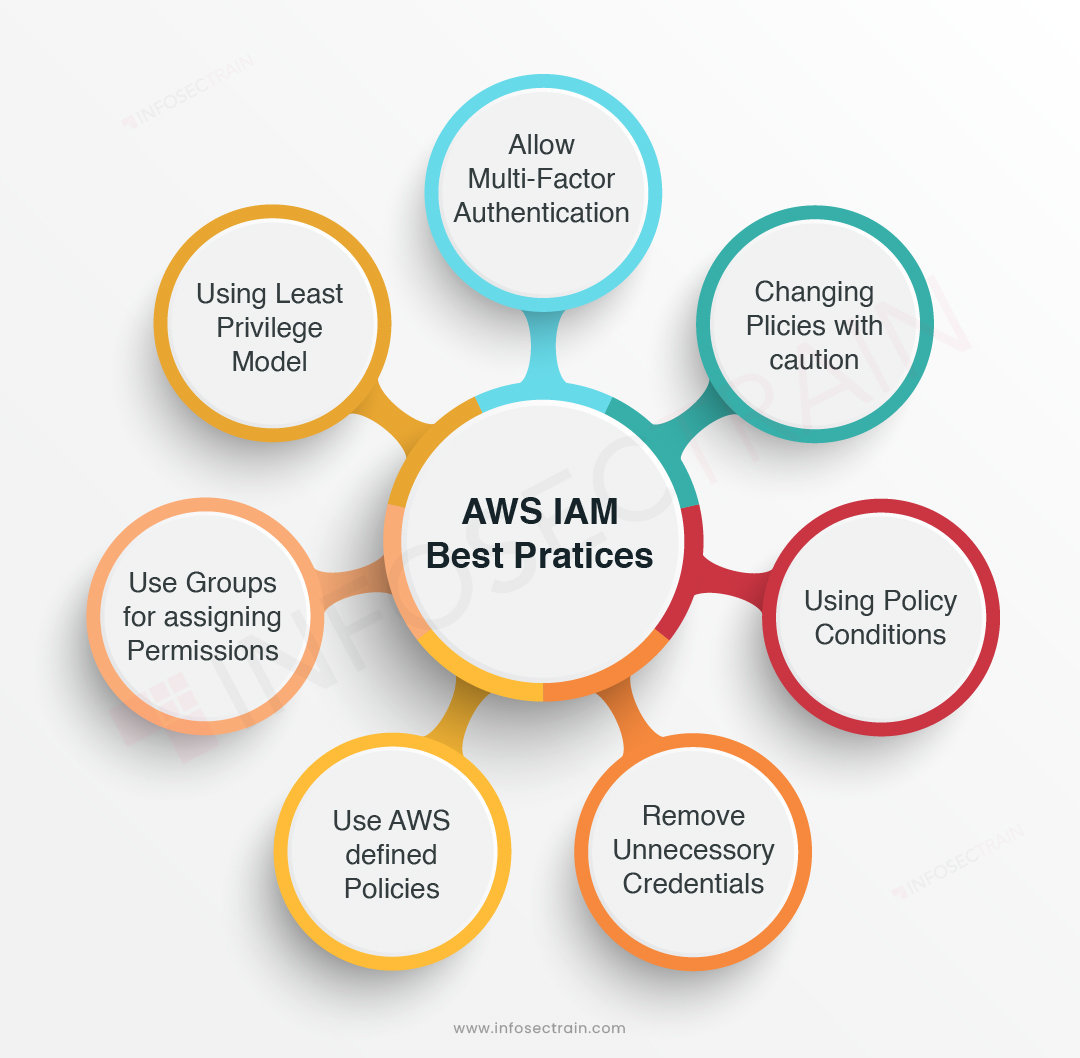
AWS Access Key ID Best Practices
Managing AWS Access Key IDs requires careful planning, execution, and monitoring to ensure the security and integrity of your AWS environment. Here are some best practices to follow for AWS Access Key ID management:
- Create Access Key IDs judiciously: Only create Access Key IDs when necessary, and assign the minimum necessary permissions to each ID. This reduces the risk of unauthorized access and data breaches.
- Secure Access Key IDs: Use IAM roles and temporary security credentials to limit the exposure of Access Key IDs. Store Access Key IDs securely, using tools like AWS Key Management Service (KMS) or hardware security modules (HSMs).
- Rotate Access Key IDs regularly: Rotate Access Key IDs every 90 days to reduce the risk of unauthorized access. Use AWS Systems Manager Parameter Store or AWS Secrets Manager to automate the rotation process.
- Monitor Access Key ID usage: Use tools like AWS CloudTrail and AWS Config to monitor Access Key ID usage and detect potential security threats. Regularly review Access Key ID activity logs and take prompt action if you detect any suspicious activity.
- Revoke and delete Access Key IDs promptly: Revoke and delete Access Key IDs promptly when they are no longer needed. This reduces the risk of unauthorized access and data breaches.
By following these best practices, you can maintain a secure AWS environment and prevent unauthorized access to your AWS services. Remember to regularly review and update your Access Key ID management policies to ensure they are up-to-date and effective.
Real-World Scenarios: Implementing AWS Access Key ID Management
Effective management of AWS Access Key IDs is crucial for maintaining a secure and compliant AWS environment. Here are some real-world examples and case studies of successful AWS Access Key ID management:
Case Study 1: Financial Services Company
A financial services company with a large AWS footprint implemented a strict Access Key ID management policy, requiring all Access Key IDs to be rotated every 90 days. The company used AWS Systems Manager Parameter Store to automate the rotation process, reducing the risk of unauthorized access and data breaches. By monitoring Access Key ID usage with AWS CloudTrail and AWS Config, the company was able to detect and respond to potential security threats promptly.
Case Study 2: Healthcare Provider
A healthcare provider with sensitive patient data in AWS implemented a policy of using IAM roles and temporary security credentials to limit the exposure of Access Key IDs. By following best practices for access key management, the healthcare provider was able to reduce the risk of unauthorized access and data breaches. The provider also used AWS Key Management Service (KMS) to encrypt Access Key IDs, adding an extra layer of security.
Case Study 3: E-commerce Company
An e-commerce company with a high volume of AWS API requests implemented a policy of monitoring Access Key ID usage with AWS CloudTrail and AWS Config. By detecting and responding to potential security threats promptly, the company was able to maintain a secure and compliant AWS environment. The company also used AWS Systems Manager Parameter Store to automate the rotation of Access Key IDs, reducing the risk of unauthorized access and data breaches.
These real-world examples and case studies demonstrate the importance of effective AWS Access Key ID management. By following best practices for creation, security, monitoring, and deletion, you can maintain a secure and compliant AWS environment and prevent unauthorized access to your AWS services.