Understanding AWS Account Management and Trusted Access
AWS account management is the process of organizing, controlling, and securing resources within the Amazon Web Services (AWS) ecosystem. A well-managed AWS account structure enables businesses to maintain a secure, cost-effective, and efficient cloud environment. Trusted Access is a crucial aspect of AWS account management, focusing on enhancing security measures and controlling user permissions.
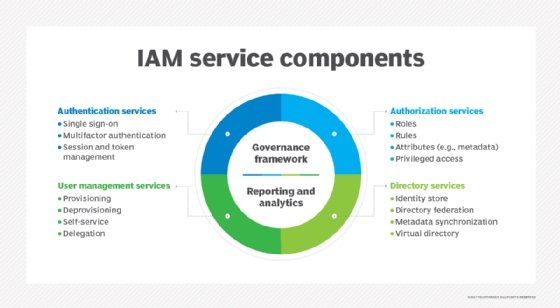
AWS Trusted Access solutions provide a centralized and consistent approach to managing user identities, permissions, and authentication across various AWS services. By implementing Trusted Access, organizations can ensure that only authorized users and applications can access their AWS resources, thereby reducing the risk of unauthorized access and data breaches.
The main keyword “aws account management trusted access” is essential for understanding and optimizing your AWS environment. By familiarizing yourself with this concept and implementing the best practices discussed in this article, you can significantly improve your cloud security and operational efficiency.
Implementing AWS Account Management Best Practices
Effective AWS account management involves following best practices to ensure a secure, organized, and cost-efficient cloud environment. Implementing these best practices is crucial for enhancing security measures and controlling user permissions. Here are some key best practices for AWS account management:
1. Use IAM Roles and Users
AWS Identity and Access Management (IAM) allows you to create and manage users, groups, and roles within your AWS account. By creating individual IAM users and roles, you can grant specific permissions to access AWS resources, ensuring that users only have access to the resources they need to perform their tasks.
2. Implement Least Privilege Access
Least privilege access means granting users the minimum permissions required to perform their tasks. By following this principle, you can reduce the risk of unauthorized access and potential security breaches. Regularly review and update access policies to ensure they align with the principle of least privilege.
3. Regularly Review Access Policies
Regularly reviewing and updating access policies helps maintain a secure AWS environment. Ensure that users’ permissions are up-to-date and reflect their current responsibilities. Remove or modify unnecessary permissions to minimize the risk of unauthorized access.
4. Use Access Keys Wisely
Access keys are used to authenticate API requests and access the AWS Management Console. Store access keys securely and rotate them regularly to minimize the risk of unauthorized access. Avoid sharing access keys between users and services.
5. Enable Multi-Factor Authentication (MFA)
MFA adds an extra layer of security to AWS account access. By requiring a unique, one-time code in addition to a password, MFA significantly reduces the risk of unauthorized access. Enable MFA for IAM users and the AWS Management Console to enhance security measures.
6. Use AWS Trusted Advisor
AWS Trusted Advisor is a service that helps you identify potential issues and risks in your AWS environment. By following Trusted Advisor’s recommendations, you can improve security, performance, and fault tolerance in your AWS account.
7. Monitor and Audit AWS Account Activity
Monitoring and auditing AWS account activity is essential for maintaining security and compliance. Use AWS services such as AWS CloudTrail, AWS Config, and AWS Security Hub to track user activity, review configurations, and detect potential security threats.
Exploring AWS Trusted Access Solutions
AWS offers various Trusted Access solutions to help organizations manage user identities, permissions, and authentication across AWS services. These solutions provide centralized and consistent control, ensuring secure access to AWS resources. Here are some of the key AWS Trusted Access solutions:
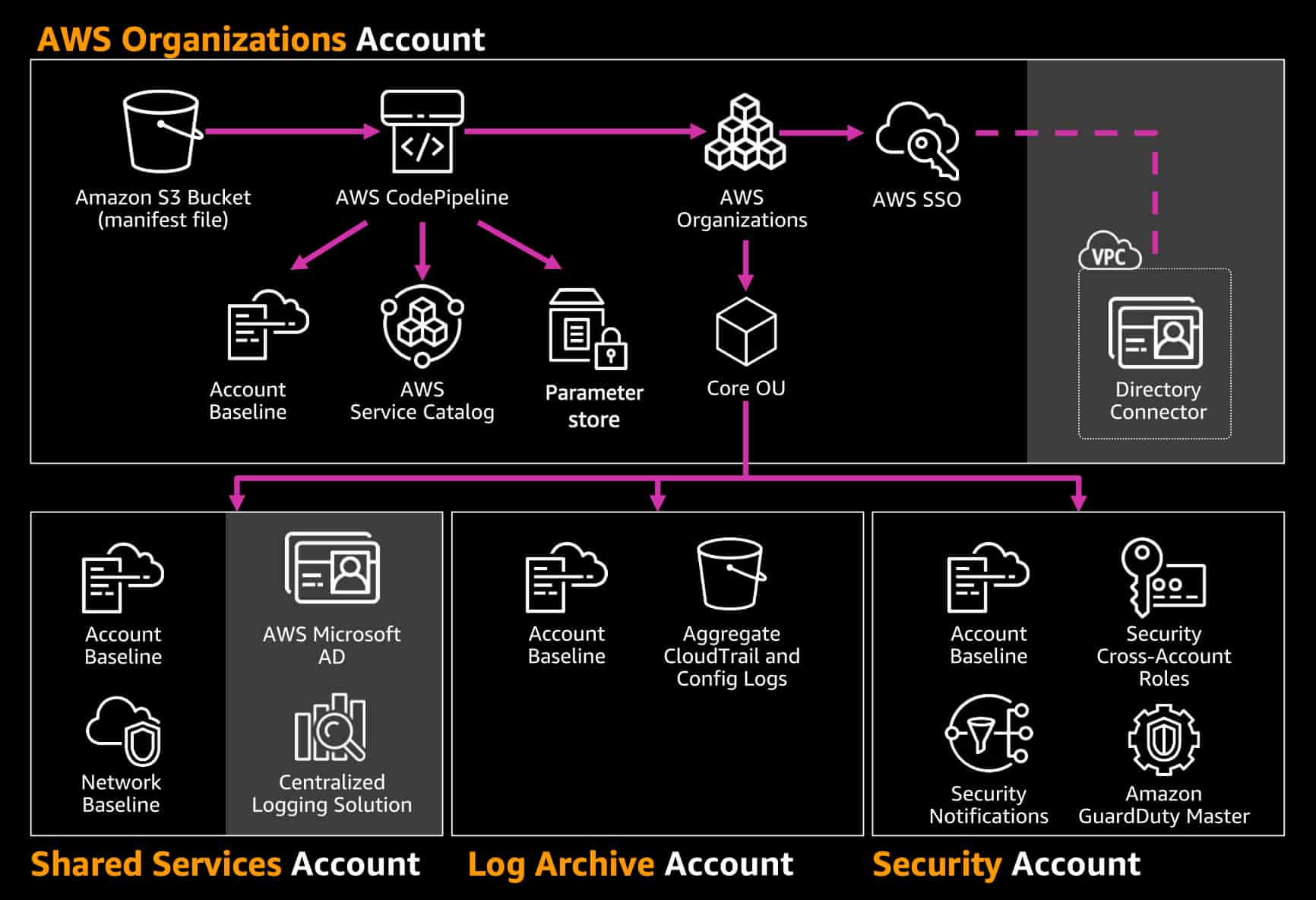
1. AWS Organizations
AWS Organizations allows you to centrally manage and govern multiple AWS accounts within your organization. By using AWS Organizations, you can create service control policies (SCPs) to enforce permissions across accounts, ensuring consistent access management and compliance.
2. AWS Single Sign-On (SSO)
AWS Single Sign-On (SSO) enables users to access multiple AWS accounts and applications using a single set of credentials. AWS SSO integrates with on-premises identity providers, such as Microsoft Active Directory, allowing you to manage access to AWS services and SaaS applications from a central location.
3. AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is a core service for managing access to AWS resources. IAM allows you to create and manage users, groups, and roles, as well as define permissions and policies to control access to AWS services and resources. IAM is a fundamental building block for AWS Trusted Access.
4. AWS Directory Service
AWS Directory Service enables you to integrate AWS resources with on-premises Microsoft Active Directory or set up a standalone directory in the AWS Cloud. By using AWS Directory Service, you can manage user access to AWS resources and applications using familiar directory-based authentication methods.
5. AWS Resource Access Manager (RAM)
AWS Resource Access Manager (RAM) enables you to share AWS resources across accounts and within your organization. By using RAM, you can centrally manage access to shared resources, such as Amazon RDS databases, Amazon S3 buckets, and Amazon EC2 instances, ensuring secure and controlled access.
6. AWS Security Token Service (STS)
AWS Security Token Service (STS) allows you to request temporary security credentials to access AWS services and resources. By using STS, you can grant limited, time-bound access to users, enhancing security and reducing the risk of unauthorized access.
7. AWS IAM Identity Center
AWS IAM Identity Center (formerly AWS Single Sign-On) is a cloud-based service that enables users to sign in to AWS services and applications using a single set of credentials. IAM Identity Center simplifies user management and access control, making it easier to manage Trusted Access in your AWS environment.
Securing AWS Account Access with Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security to AWS account access, ensuring that only authorized users can log in and access AWS resources. MFA requires users to provide two forms of authentication: something they know (such as a password) and something they have (such as a physical token or a one-time code sent to their mobile device). Implementing MFA for IAM users and the AWS Management Console is a crucial best practice for enhancing AWS account security.
Enabling MFA for IAM Users
To enable MFA for an IAM user, follow these steps:
- Sign in to the AWS Management Console and navigate to the IAM service.
- Select the desired user and click on the “Security Credentials” tab.
- In the “Assigned MFA device” section, click “Manage MFA Device” and then “Activate MFA.”
- Follow the on-screen instructions to configure the MFA device (e.g., virtual MFA app or hardware token).
- Once the MFA device is configured, users will be required to provide a one-time code from their MFA device when signing in to the AWS Management Console.
Enabling MFA for the AWS Management Console
To enable MFA for the AWS Management Console, follow these steps:
- Sign in to the AWS Management Console and navigate to the “My Security Credentials” page.
- In the “Multi-Factor Authentication (MFA)” section, click “Activate MFA.”
- Follow the on-screen instructions to configure the MFA device (e.g., virtual MFA app or hardware token).
- Once the MFA device is configured, users will be required to provide a one-time code from their MFA device when signing in to the AWS Management Console.
By implementing MFA for IAM users and the AWS Management Console, you can significantly reduce the risk of unauthorized access to your AWS account and resources. MFA is a simple yet powerful security measure that should be part of any AWS account management trusted access strategy.
Monitoring and Auditing AWS Account Activity for Security and Compliance
Monitoring and auditing AWS account activity is crucial for maintaining security, ensuring compliance, and detecting potential threats. AWS provides several services that help you track user activity, review configurations, and monitor resource usage. In this article, we will introduce AWS CloudTrail, AWS Config, and AWS Security Hub, and discuss how they contribute to effective AWS account management trusted access.
AWS CloudTrail
AWS CloudTrail is a service that records API calls made to AWS resources and delivers log files to an Amazon S3 bucket. CloudTrail enables you to monitor user activity, track changes to resources, and detect potential security threats. By analyzing CloudTrail logs, you can gain insights into who made specific API calls, when the calls were made, and the source IP addresses. CloudTrail also integrates with AWS Lambda, allowing you to automate responses to specific events or anomalies in your AWS environment.
AWS Config
AWS Config is a service that continuously monitors and records configurations for AWS resources in your account. Config provides a detailed view of the resource configurations, allowing you to assess, audit, and evaluate changes over time. By using Config, you can ensure that your AWS resources comply with your organization’s security and compliance policies. Config also integrates with AWS CloudTrail, enabling you to correlate configuration changes with corresponding API calls.
AWS Security Hub
AWS Security Hub is a service that aggregates security findings from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, and Amazon Macie, into a unified view. Security Hub simplifies security management by providing a comprehensive overview of your security and compliance posture in a single location. By using Security Hub, you can prioritize security alerts, automate remediation, and maintain a secure AWS environment. Security Hub also integrates with AWS CloudTrail, enabling you to track changes to security configurations and monitor user activity related to security-related events.
By leveraging AWS CloudTrail, AWS Config, and AWS Security Hub, you can effectively monitor and audit your AWS account activity, ensuring a secure and compliant cloud environment. These services contribute significantly to AWS account management trusted access, enabling you to maintain control over your AWS resources and protect your organization from potential threats.
How to Create an AWS IAM Role for Trusted Access
In this article, we will guide you through the process of creating an AWS Identity and Access Management (IAM) role for Trusted Access. An IAM role is an IAM entity that defines a set of permissions for making AWS service requests. IAM roles are not associated with a specific user or group, making them an ideal choice for granting access to specific AWS services or resources.
Step 1: Create a Role
To create an IAM role, sign in to the AWS Management Console and navigate to the IAM service. In the navigation pane, choose “Roles” and then click the “Create role” button.
Step 2: Define the Role’s Trusted Entities
After creating the role, you need to define the trusted entities that can assume the role. Trusted entities can be AWS services, IAM users, or external AWS accounts. To define trusted entities, choose the appropriate service, user, or account, and then click “Next: Permissions.”
Step 3: Set Permissions
Next, you need to set the permissions for the role. You can attach existing policies directly or create custom policies that grant access to specific AWS services or resources. To attach a policy, choose the policy from the list, and then click “Next: Tags.”
Step 4: Add Tags (Optional)
You can add tags to the role to help organize and categorize it. Tags are key-value pairs that you can assign to AWS resources. To add tags, enter the tag key and value, and then click “Next: Review.”
Step 5: Review and Create the Role
Finally, review the role’s configuration, including the trusted entities, permissions, and tags. If everything looks correct, click “Create role” to create the role. The new IAM role is now available for use and can be attached to EC2 instances or AWS resources as needed.
By following these steps, you can create an IAM role for Trusted Access, ensuring secure and controlled access to your AWS resources. IAM roles are an essential component of AWS account management trusted access, enabling you to manage permissions and access control effectively.
Integrating AWS Trusted Access with On-Premises Identity Systems
In many organizations, on-premises identity systems, such as Microsoft Active Directory (AD), are integral to managing user access and authentication. AWS provides several solutions to integrate AWS Trusted Access with on-premises identity systems, ensuring a seamless and secure user experience.
AWS Directory Service
AWS Directory Service enables you to set up and manage directory services in the AWS Cloud. You can create a directory in AWS and connect it to your on-premises directory, allowing you to manage user access and authentication for AWS resources and on-premises applications. AWS Directory Service supports various directory types, including Microsoft AD, Simple AD, and AD Connector.
AWS Single Sign-On
AWS Single Sign-On (SSO) is a cloud-based service that enables users to sign in to multiple AWS accounts and applications using their corporate credentials. AWS SSO integrates with on-premises identity providers, such as Microsoft AD, allowing you to manage access to AWS services and SaaS applications from a central location. With AWS SSO, you can create and manage user access policies, ensuring a consistent and secure user experience across your AWS and on-premises resources.
Integrating AWS Trusted Access with Microsoft AD
To integrate AWS Trusted Access with Microsoft AD, you can use AWS Directory Service or AWS SSO. By connecting your on-premises AD to AWS, you can manage user access and authentication for AWS resources and applications using familiar tools and processes. This integration enables you to leverage your existing on-premises identity and access management infrastructure, ensuring a secure and seamless user experience.
Benefits of Integrating AWS Trusted Access with On-Premises Identity Systems
Integrating AWS Trusted Access with on-premises identity systems offers several benefits, including:
- Centralized user management: Manage user access and authentication for both on-premises and AWS resources from a central location.
- Seamless user experience: Enable users to sign in to AWS services and applications using their corporate credentials, reducing the need for multiple usernames and passwords.
- Enhanced security: Leverage your existing on-premises identity and access management infrastructure to ensure a secure user experience in the AWS Cloud.
- Consistent access policies: Apply consistent access policies across your AWS and on-premises resources, ensuring a unified security posture.
By integrating AWS Trusted Access with on-premises identity systems, you can ensure a secure and seamless user experience while maintaining a consistent security posture across your AWS and on-premises resources.
Best Practices for Managing Trusted Access in a Multi-Account Environment
Managing Trusted Access in a multi-account AWS environment can be challenging. To ensure a secure and organized cloud environment, it is essential to follow best practices for AWS account management. This article will discuss strategies for managing Trusted Access in a multi-account environment, including using AWS Organizations, implementing service control policies, and utilizing AWS Resource Access Manager (RAM).
Using AWS Organizations
AWS Organizations is a service that enables you to manage multiple AWS accounts from a single location. By using AWS Organizations, you can create a hierarchy of accounts, apply service control policies, and centrally manage billing and access control. Organizations also provide consolidated billing and volume discounts for AWS services.
Implementing Service Control Policies
Service control policies (SCPs) are a type of policy that you can use to manage permissions across multiple AWS accounts in your organization. SCPs enable you to specify which AWS services and actions are allowed or denied in each account. By using SCPs, you can ensure that all accounts in your organization comply with your security and compliance policies.
Utilizing AWS Resource Access Manager (RAM)
AWS Resource Access Manager (RAM) is a service that enables you to share AWS resources across multiple accounts in your organization. With RAM, you can centrally manage access to shared resources, such as Amazon RDS databases, Amazon S3 buckets, and Amazon EC2 instances. By using RAM, you can simplify access management and ensure that users have access to the resources they need to perform their job functions.
Benefits of Managing Trusted Access in a Multi-Account Environment
Managing Trusted Access in a multi-account environment offers several benefits, including:
- Centralized management: Manage access control, billing, and compliance policies for multiple accounts from a single location.
- Consistent security posture: Ensure that all accounts in your organization comply with your security and compliance policies.
- Efficient resource sharing: Simplify access management and ensure that users have access to the resources they need to perform their job functions.
- Cost optimization: Consolidate billing and take advantage of volume discounts for AWS services.
By following best practices for managing Trusted Access in a multi-account environment, you can ensure a secure and organized cloud environment. Utilizing AWS Organizations, implementing service control policies, and using AWS Resource Access Manager (RAM) can help you manage access control, billing, and compliance policies across multiple accounts, ensuring a consistent security posture and efficient resource sharing.