What is a Directory Service and Why is it Important?
A directory service is a fundamental component of modern IT infrastructure. It serves as a centralized repository. This repository manages users, computers, and other network resources. Think of it as a digital phonebook for an organization. It efficiently organizes and provides access to crucial information.
The primary purpose of a directory service is to simplify administration. It improves security, and enables seamless collaboration. By centralizing user account management, administrators can easily create, modify, and delete user accounts. They can also manage access permissions from a single point. This eliminates the need to manage individual accounts on multiple systems. This saves time and reduces the risk of errors. A well-managed directory service is crucial for maintaining a secure IT environment. It allows for the implementation of consistent security policies across the organization. Access control lists (ACLs) define who can access specific resources. Centralized authentication mechanisms, such as passwords and multi-factor authentication, ensure that only authorized users gain access to sensitive data. These are important active directory concepts.
Directory services foster collaboration by providing a shared, searchable repository of information. Users can easily find colleagues, locate shared resources, and communicate effectively. This promotes teamwork and knowledge sharing. Microsoft’s Active Directory (AD) is a widely-used example of a directory service. It is a core component of many Windows-based networks. Understanding the fundamental concepts of directory services, including active directory concepts, is essential for anyone involved in IT administration, security, or networking. Efficient directory services enable organizations to streamline their IT operations. They enhance security, and improve collaboration, ultimately leading to increased productivity and efficiency. Exploring active directory concepts is a great path in the IT world. The active directory concepts apply to managing network resources effectively and securely.
Demystifying Active Directory: An Overview
Active Directory (AD) is Microsoft’s directory service implementation. It is a cornerstone of many Windows-based networks. Understanding active directory concepts is crucial for managing these environments effectively. This section provides a high-level overview of Active Directory. It sets the stage for exploring more specific active directory concepts. Active Directory simplifies the management of users, computers, and other network resources. It offers a centralized and organized approach. This improves security and simplifies administration.
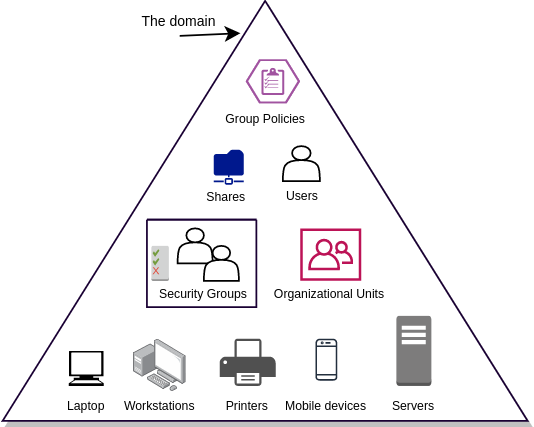
Active Directory relies on several core components working together. These components are integral to its functionality. The key active directory concepts include domains, organizational units (OUs), and domain controllers. The schema also plays a vital role. A domain represents a security boundary and administrative unit. OUs offer a way to structure resources within a domain. Domain controllers are the servers that host the Active Directory database. The schema defines the objects and attributes that can be stored in the directory. Group Policy provides centralized configuration management. Active Directory uses Lightweight Directory Access Protocol (LDAP). LDAP is used for accessing and managing directory information. These active directory concepts are foundational to understanding how AD operates.
Active Directory plays a pivotal role in managing Windows networks. It provides authentication and authorization services. It also provides centralized management capabilities. By understanding active directory concepts, administrators can efficiently manage user access, deploy software, and enforce security policies. Active Directory integrates with other Microsoft technologies. This improves the overall efficiency of the IT infrastructure. Proper planning and design are critical for a successful Active Directory deployment. This ensures that it meets the specific needs of the organization. The complexity of Active Directory requires ongoing learning. A solid grasp of active directory concepts is essential for IT professionals.
Understanding the Active Directory Domain
An Active Directory domain serves as the fundamental building block within a Microsoft Active Directory environment. Think of it as a secure container holding user accounts, computer accounts, and other network resources. Each domain has a unique namespace, defining its identity and allowing for easy identification within a network. This namespace typically reflects the organization’s structure, improving clarity and management. Understanding Active Directory domains is crucial for comprehending core active directory concepts.
The domain’s boundaries establish a security perimeter. Resources within a domain are subject to its specific security policies and access controls. This allows for granular control over who can access what, enhancing security and protecting sensitive information. Domain controllers, essential servers within the domain, manage the Active Directory database. These controllers authenticate users and computers, ensuring only authorized individuals access network resources. This authentication process is critical for maintaining data integrity and overall network security. Proper understanding of these active directory concepts is vital for efficient IT management.
Multiple domain controllers provide redundancy and fault tolerance. They replicate the Active Directory database across various servers, preventing data loss if one controller fails. This replication ensures high availability and minimizes disruption to network services. This architecture is a key aspect of robust network design, leveraging the power of distributed systems to enhance reliability and performance. Mastering these core active directory concepts will allow for a deeper understanding of the intricate workings of a Microsoft Active Directory deployment. The domain’s hierarchical structure is instrumental in simplifying administration and promoting efficient resource management. The domain itself is a critical component of numerous enterprise-level security and management strategies.
Organizational Units (OUs): Structuring Your Directory
Organizational Units (OUs) are fundamental active directory concepts within an Active Directory domain. They provide a hierarchical structure for organizing objects. These objects include users, computers, groups, and other OUs. Consider OUs as containers that allow administrators to logically group resources. This grouping simplifies management and enables the delegation of administrative control.
OUs are essential for implementing a well-organized Active Directory environment. They allow administrators to mirror the organizational structure of a company. For example, an organization might create OUs for departments such as “Sales,” “Marketing,” or “IT.” Within each department OU, further subdivisions can be created for specific teams or locations. This nested structure provides granular control over resources and permissions. One of the key benefits of OUs is the ability to delegate administrative control. Instead of granting domain-wide administrative privileges, administrators can delegate control over specific OUs to designated users or groups. This ensures that only authorized personnel can manage resources within a particular OU, enhancing security and accountability. Through effective use of active directory concepts, companies can realize significant benefit.
Furthermore, OUs play a crucial role in applying Group Policy settings. Group Policy Objects (GPOs) can be linked to OUs. This allows administrators to enforce specific configurations and security settings on all users and computers within that OU. For example, a GPO linked to the “Sales” OU might configure specific software settings or restrict access to certain applications. Group Policy inheritance allows settings to be applied hierarchically. Settings applied to a parent OU are inherited by its child OUs, unless specifically overridden. This simplifies the process of managing configurations across the organization. OUs are critical active directory concepts that ensure a flexible, manageable, and secure Active Directory infrastructure. Properly planned and implemented OUs are essential for efficient IT administration and security management. Mastering these active directory concepts is key for any IT professional working with Windows-based networks.
How to Manage Users and Groups in Active Directory
Managing users and groups is a fundamental aspect of administering Active Directory. This involves creating, modifying, and deleting user accounts and groups to maintain an organized and secure network environment. Understanding these active directory concepts is crucial for effective administration. The process begins with creating user accounts, which represent individual users within the domain. When creating a user account, administrators must provide essential information such as the user’s name, username, and password. Additional attributes, such as email address, phone number, and department, can also be specified to provide a more complete user profile. User accounts are central to many active directory concepts.
Modifying user accounts involves updating existing user information or resetting passwords. This can be necessary when a user changes their name, job title, or contact information. It’s also essential for maintaining security by periodically resetting passwords and enforcing strong password policies. Deleting user accounts is necessary when an employee leaves the organization or no longer requires access to the network. It is a critical step in maintaining security and preventing unauthorized access to resources. Groups, another core component of active directory concepts, simplify the process of assigning permissions and managing access to resources.
Active Directory offers different types of groups, including security groups and distribution groups. Security groups are used to grant permissions to resources, such as files, folders, and printers. By adding users to a security group, administrators can easily grant them the necessary access rights. Distribution groups, on the other hand, are primarily used for email distribution lists. When an email is sent to a distribution group, it is automatically forwarded to all members of the group. Managing groups involves creating new groups, adding or removing members, and modifying group properties. Understanding these active directory concepts empowers administrators to efficiently manage user access and maintain a secure and well-organized network environment. The effective management of users and groups exemplifies practical active directory concepts, contributing to streamlined administration and enhanced security.
Group Policy: Centralized Configuration Management
Group Policy is a cornerstone of managing Windows environments within the framework of active directory concepts. It offers a centralized way to configure and manage operating systems, applications, and user settings. By leveraging Group Policy, administrators can enforce security policies, deploy software, and customize desktop environments across an entire organization efficiently. This capability is critical for maintaining a consistent and secure computing environment.
At the heart of Group Policy are Group Policy Objects (GPOs). These objects contain specific configuration settings that are applied to users and computers within defined scopes. GPOs can be linked to sites, domains, or Organizational Units (OUs), determining which users and computers receive the settings. Understanding Group Policy inheritance is crucial; settings applied at a higher level (e.g., domain level) are inherited by lower levels (e.g., OUs), unless blocked or overridden. This hierarchical structure allows for granular control over configuration management. Several active directory concepts are in play to make Group Policy a success, including proper planning of OUs and security groups.
The range of settings that can be managed through Group Policy is extensive. Common settings include password policies, account lockout policies, software installation, drive mappings, and security settings. For example, an administrator can use Group Policy to enforce strong password requirements, ensuring that all users within the domain adhere to a specific password complexity and expiration policy. Similarly, Group Policy can be used to deploy software updates automatically, minimizing the risk of vulnerabilities. Effectively utilizing Group Policy requires a solid understanding of active directory concepts. This includes how objects are organized within the directory, and how Group Policy settings are applied and inherited. By mastering Group Policy, administrators can significantly streamline their management tasks and enhance the security posture of their organization, highlighting the importance of active directory concepts in modern IT infrastructure.
Active Directory Schema: Defining the Structure
The Active Directory schema is the foundational blueprint that governs the entire Active Directory environment. It acts as the central repository defining all object classes and attributes that can exist within the directory. Understanding the schema is crucial for administrators seeking to extend or customize Active Directory beyond its default capabilities. Without a solid grasp of the schema, making changes can lead to instability or data corruption. The schema defines what type of data can be stored, influencing all active directory concepts within the organization.
Essentially, the schema dictates the structure of every object, such as users, computers, groups, and organizational units. Each object class is defined by a set of attributes, which specify the characteristics or properties of that object. For example, a user object might have attributes for first name, last name, user principal name, and password. The schema defines the syntax and data type for each attribute, ensuring data consistency across the directory. Any attempt to create an object or modify an attribute that violates the schema will be rejected. Modifications to the Active Directory schema should be performed with extreme caution and only after thorough planning and testing. Incorrect modifications can potentially render the entire directory unusable, impacting all active directory concepts relying on the schema’s integrity.
While the default schema provides a comprehensive set of object classes and attributes, organizations often need to extend it to accommodate specific business requirements. This might involve adding new attributes to existing object classes or creating entirely new object classes. For example, a company might add a “department code” attribute to the user object class to facilitate reporting or application integration. Extending the schema requires modifying the schema objects themselves, which are stored within the Active Directory database. These changes propagate to all domain controllers in the forest, ensuring a consistent schema throughout the environment. Understanding the Active Directory schema is important when integrating third-party applications that rely on specific attributes or object classes. Careful schema management and documentation are essential components of maintaining a healthy and functional Active Directory environment. This understanding of the active directory concepts related to schema management ensures smooth operation and reduces the risk of unforeseen issues.
Domain Controllers: The Heart of Active Directory
Domain controllers are fundamental to understanding active directory concepts. They are the servers that hold a copy of the Active Directory database. They also authenticate users and computers within the domain. Each domain controller acts as a gatekeeper. It verifies credentials and enforces security policies. This ensures only authorized users and devices can access network resources. In essence, domain controllers are the cornerstone of any Active Directory environment, playing a vital role in managing access and maintaining security.
For robust and reliable active directory concepts, it’s crucial to have multiple domain controllers. This redundancy ensures fault tolerance. If one domain controller fails, others can seamlessly take over. This prevents service interruption. The Active Directory database is replicated between domain controllers. Changes made on one are automatically propagated to others. This replication process uses a multi-master replication model. Any domain controller can accept changes. These changes are then replicated to its partners. This ensures consistency across the entire Active Directory environment. Proper planning and configuration of domain controllers are crucial for a healthy and resilient Active Directory infrastructure. Understanding these active directory concepts is vital for any network administrator.
The replication topology impacts the efficiency of Active Directory. It determines how changes are propagated. There are different ways to configure replication. These include site links and bridgehead servers. These configurations are important for large, geographically dispersed networks. Domain controllers also handle other critical functions. These functions include DNS resolution and Group Policy application. They are multifaceted servers that require careful management. Domain controllers are essential to many active directory concepts. Properly managed domain controllers contribute significantly to a secure and well-performing network. Therefore, understanding the role and functionality of domain controllers is essential for anyone working with Active Directory.