Understanding Azure Blob Storage and Its Access Mechanisms
Azure Blob Storage is a scalable object storage solution designed to store large amounts of unstructured data, such as text and binary data. It is a critical component of Azure’s storage offerings, providing developers with a flexible and secure method to store and manage data for various applications, including big data analytics, IoT, and web and mobile applications. Managing access to stored data is crucial to ensure data security and prevent unauthorized access.
Azure Blob Storage offers two primary access mechanisms: access keys and shared access signatures (SAS). Access keys are long-lived, secret credentials that provide full control over Blob Storage accounts. SAS, on the other hand, are time-limited, revocable tokens that grant restricted access to specific Blob Storage resources. By understanding the differences between these two access mechanisms and implementing best practices, you can ensure secure access to your Azure Blob Storage data.
Access Key Management: Best Practices and Strategies
Access keys are essential credentials that grant full control over Azure Blob Storage accounts. Proper management and rotation of access keys are crucial to maintaining the security and integrity of your stored data. This section discusses best practices and strategies for managing access keys when accessing Azure Blob Storage.
Access keys are automatically generated when creating a new Blob Storage account. These keys consist of a primary and secondary key, both providing complete access to the account. It is essential to manage and rotate these keys regularly to minimize the risk of unauthorized access. Implementing best practices, such as restricting access to keys, monitoring key usage, and setting up alerts, can significantly enhance the security of your Blob Storage data.
To mitigate the risks associated with key mismanagement, follow these recommendations:
- Limit access to keys: Restrict the number of users and applications with access to your keys. Implementing role-based access control (RBAC) can help you manage permissions more effectively.
- Monitor key usage: Regularly monitor key usage to detect any unusual or unauthorized access patterns. Azure Monitor and Azure Security Center can help you track key usage and set up alerts for suspicious activities.
- Set up key rotation: Establish a key rotation schedule to ensure that keys are updated regularly. Rotating keys at least once every 90 days is a good practice to minimize the risk of unauthorized access.
- Implement multi-factor authentication (MFA): Require MFA for users accessing your keys to add an extra layer of security.
- Use a key vault: Store your keys in Azure Key Vault to benefit from advanced security features, such as hardware security modules (HSMs) and access control policies.
Introducing Shared Access Signatures (SAS): A Flexible Access Option
Shared Access Signatures (SAS) are a flexible and secure method for granting limited access to specific Azure Blob Storage resources for a defined period. SAS tokens provide an alternative to sharing access keys, improving security and reducing the risk of unauthorized access. This section discusses the functionality and benefits of SAS tokens and how they compare to access keys.
SAS tokens are time-limited, revocable, and can be customized to grant specific permissions to Blob Storage resources. By using SAS tokens, you can restrict access to a container or blob, allowing users to perform specific actions, such as read, write, or delete, without providing full access to the entire Blob Storage account. This granular level of control enhances security and reduces the risk of unauthorized access or data breaches.
Compared to access keys, SAS tokens offer several advantages:
- Improved security: SAS tokens can be customized to grant specific permissions, reducing the risk of unauthorized access or data breaches.
- Flexibility: SAS tokens can be generated for a specific resource, allowing you to grant access to individual containers or blobs without sharing access keys.
- Time-limited: SAS tokens have an expiration date, ensuring that access is automatically revoked after a defined period.
- Revocable: SAS tokens can be revoked at any time, allowing you to maintain control over access to your Blob Storage resources.
- Reduced risk: By using SAS tokens, you can minimize the risk of exposing access keys, which provide full control over the Blob Storage account.
How to Generate and Manage SAS Tokens: A Step-by-Step Guide
This section provides a detailed, beginner-friendly guide on generating and managing Shared Access Signatures (SAS) tokens for Azure Blob Storage using Azure Storage Explorer and the Azure Portal. Examples and screenshots are included to enhance understanding.
Using Azure Storage Explorer
Azure Storage Explorer is a free, standalone app from Microsoft that allows you to easily create, manage, and delete SAS tokens for your Blob Storage resources.
- Download and install Azure Storage Explorer from the official website.
- Connect to your Azure Storage account.
- Right-click the container or blob you want to grant access to and select “Get Shared Access Signature.”
- Configure the SAS token settings, such as the expiry time and allowed permissions, then click “Create.”
- Copy the generated SAS token and share it with the intended users or applications.
Using the Azure Portal
The Azure Portal also allows you to generate SAS tokens for your Blob Storage resources. Follow these steps to create a SAS token:
- Log in to the Azure Portal and navigate to your Storage account.
- Click “Blobs” in the left-hand menu, then select the container you want to grant access to.
- Click the “Shared Access Signature” button in the top menu.
- Configure the SAS token settings, such as the expiry time and allowed permissions, then click “Generate SAS and connection string.”
- Copy the generated SAS token and share it with the intended users or applications.
Managing SAS tokens is essential to maintaining the security and integrity of your Blob Storage data. Regularly review and revoke SAS tokens to minimize the risk of unauthorized access. Azure Storage Explorer and the Azure Portal provide user-friendly interfaces for generating and managing SAS tokens, ensuring secure access to your Blob Storage resources.
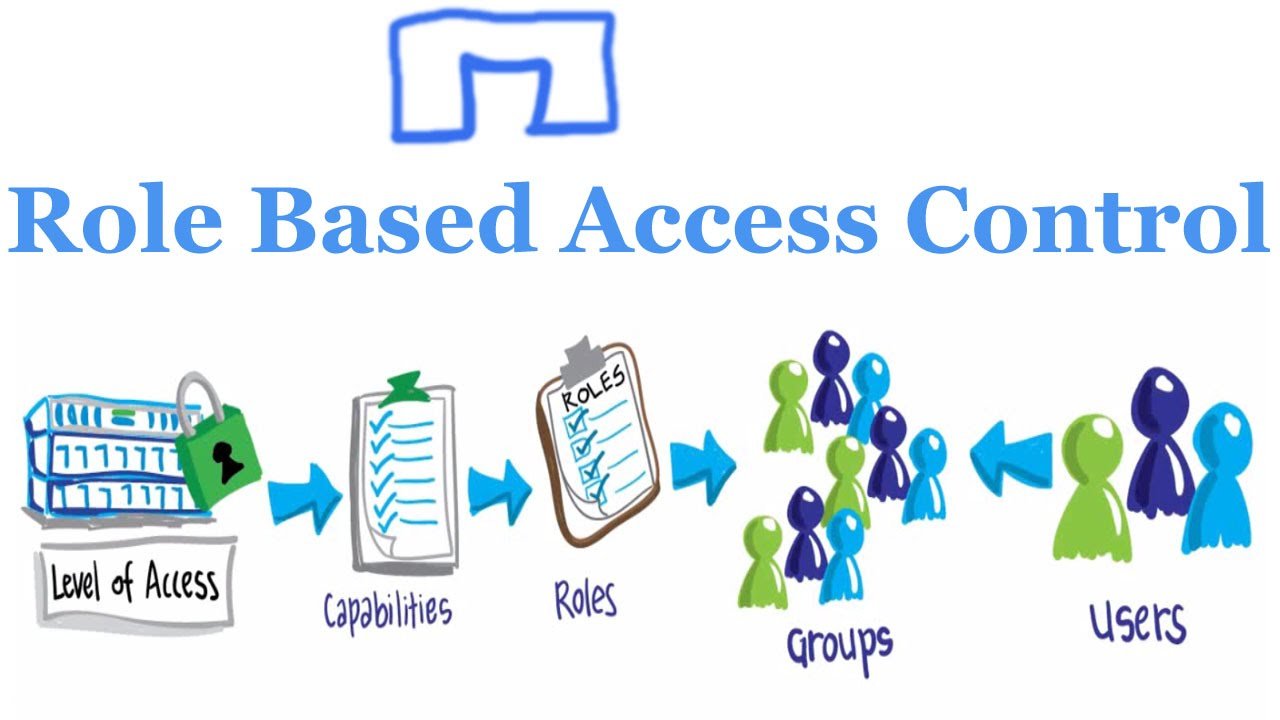
Implementing Role-Based Access Control (RBAC) for Fine-Grained Permissions
Role-Based Access Control (RBAC) is a powerful method for managing access to Azure resources at scale. RBAC enables you to grant fine-grained permissions to Blob Storage resources, improving security and reducing the risk of over-provisioning. This section discusses how to implement RBAC for Azure Blob Storage and the benefits it provides.
RBAC uses role assignments to grant specific permissions to users, groups, or applications. Azure provides built-in roles, such as “Storage Blob Data Contributor” and “Storage Blob Data Reader,” that can be assigned to users or groups at various scopes (subscription, resource group, or storage account). By using RBAC, you can ensure that users and applications have the minimum necessary permissions to perform their tasks, reducing the risk of unauthorized access or accidental modifications.
To implement RBAC for Azure Blob Storage, follow these steps:
- Navigate to the Azure Portal and open your storage account.
- Click “Access control (IAM)” in the left-hand menu, then click “Add role assignment” to create a new role assignment.
- Select the role you want to assign (e.g., “Storage Blob Data Contributor”) and enter the user, group, or application details.
- Choose the appropriate scope for the role assignment (subscription, resource group, or storage account).
- Review the settings and click “Save” to create the role assignment.
By implementing RBAC for Azure Blob Storage, you can:
- Grant fine-grained permissions to users, groups, or applications.
- Reduce the risk of over-provisioning and unauthorized access.
- Simplify access management by using built-in roles and scopes.
- Monitor and audit access using Azure Monitor, Azure Security Center, and Azure Policy.
RBAC is a valuable tool for managing access to Azure Blob Storage resources. By combining RBAC with other access mechanisms, such as access keys, SAS tokens, and Azure Active Directory (AAD), you can create a comprehensive, secure access management strategy for your Azure Storage accounts.
Integrating Azure Active Directory (AAD) for Identity-Based Access
Azure Active Directory (AAD) provides identity-based access to Azure services, including Azure Blob Storage. By using AAD, you can enhance security and simplify access management for your storage accounts. This section discusses the advantages of using AAD for Blob Storage and how to configure AAD authentication and authorization.
AAD offers several benefits for accessing Azure Blob Storage:
- Identity-based access: AAD uses identities, rather than shared keys, to grant access to Blob Storage resources.
- Fine-grained access control: AAD enables you to define role-based access control (RBAC) roles and assign them to users, groups, or applications at various scopes.
- Integration with existing authentication systems: AAD can be integrated with your on-premises Active Directory or other identity providers, allowing you to leverage existing authentication mechanisms.
- Conditional Access: AAD provides conditional access policies that enable you to control access to Blob Storage based on user location, device, and other factors.
To configure AAD authentication and authorization for Azure Storage accounts, follow these steps:
- Register your application in the Azure Portal: Register your application in the Azure Portal to obtain an Application (client) ID and Directory (tenant) ID.
- Assign roles to your application: Assign RBAC roles to your application at the appropriate scope (subscription, resource group, or storage account).
- Configure Azure Storage account for AAD authentication: Enable AAD authentication for your storage account using the Azure Portal or Azure PowerShell.
- Authenticate using Azure AD: Authenticate your application using Azure AD when accessing Blob Storage resources.
By integrating AAD with Azure Blob Storage, you can enhance security, simplify access management, and meet compliance requirements. AAD provides a robust, flexible, and secure method for managing access to your Blob Storage resources.
Monitoring and Auditing Azure Blob Storage Access
Monitoring and auditing Blob Storage access is crucial for detecting potential security threats and ensuring compliance with organizational policies. Azure provides several tools to help you monitor and audit Blob Storage access, including Azure Monitor, Azure Security Center, and Azure Policy. This section discusses how to use these tools to monitor and audit Blob Storage access.
Azure Monitor
Azure Monitor collects data from various sources, including Blob Storage, and provides detailed insights into usage patterns, performance, and security. By using Azure Monitor, you can:
- Create custom dashboards to visualize Blob Storage metrics and logs.
- Set up alerts for specific events or conditions, such as failed access attempts or data exfiltration attempts.
- Integrate Azure Monitor with Azure Log Analytics to perform advanced analytics and correlation across multiple services.
Azure Security Center
Azure Security Center provides a centralized security management and threat protection solution for Azure resources, including Blob Storage. By using Azure Security Center, you can:
- Assess the security posture of your Blob Storage resources and identify potential vulnerabilities.
- Receive security recommendations tailored to your Blob Storage resources.
- Monitor security alerts and respond to threats using Azure Security Center’s built-in incident response capabilities.
Azure Policy
Azure Policy enables you to define and enforce consistent policies across your Azure resources, including Blob Storage. By using Azure Policy, you can:
- Create custom policies that enforce specific rules, such as requiring encryption for Blob Storage data.
- Monitor compliance with organizational policies and identify resources that are out of compliance.
- Remediate non-compliant resources by applying policies that automatically correct the issue or notify the appropriate personnel for manual remediation.
By using Azure Monitor, Azure Security Center, and Azure Policy, you can effectively monitor and audit Blob Storage access, ensuring compliance with organizational policies and detecting potential security threats. Regularly reviewing and analyzing Blob Storage access data is essential for maintaining a secure and compliant storage environment.
Securely Accessing Azure Blob Storage: Summary and Recommendations
Azure Blob Storage is a powerful and scalable object storage solution that requires careful attention to access management to ensure data security and compliance. This article discussed various access mechanisms, including access keys, shared access signatures (SAS), Role-Based Access Control (RBAC), and Azure Active Directory (AAD). By understanding the benefits and limitations of each mechanism, you can make informed decisions about implementing secure access to Azure Blob Storage.
Recommendations
- Manage access keys securely: Follow best practices for managing and rotating access keys, and be aware of the potential risks associated with key mismanagement. Consider implementing Azure Key Vault to securely store and manage access keys.
- Use SAS for limited access: SAS is a flexible and secure option for granting limited access to specific Blob Storage resources for a defined period. Use SAS to delegate access to external users or applications without exposing your access keys.
- Implement RBAC for fine-grained permissions: RBAC enables you to grant fine-grained permissions to Blob Storage resources, improving security and reducing the risk of over-provisioning. Use RBAC to define custom roles and assign them to users, groups, or applications at various scopes.
- Integrate AAD for identity-based access: AAD provides identity-based access to Azure services, including Blob Storage. By using AAD, you can enhance security and simplify access management for your storage accounts. Configure AAD authentication and authorization for Azure Storage accounts to leverage existing authentication mechanisms and conditional access policies.
- Monitor and audit Blob Storage access: Regularly monitor and audit Blob Storage access to detect potential security threats and ensure compliance. Use Azure Monitor, Azure Security Center, and Azure Policy to monitor and audit Blob Storage access, and take appropriate action based on the data insights and security recommendations provided.
By following these recommendations, you can implement secure access to Azure Blob Storage, ensuring data security and compliance. Remember that ongoing monitoring and auditing are essential for maintaining a secure and compliant storage environment.