Understanding Security and Compliance in the Cloud
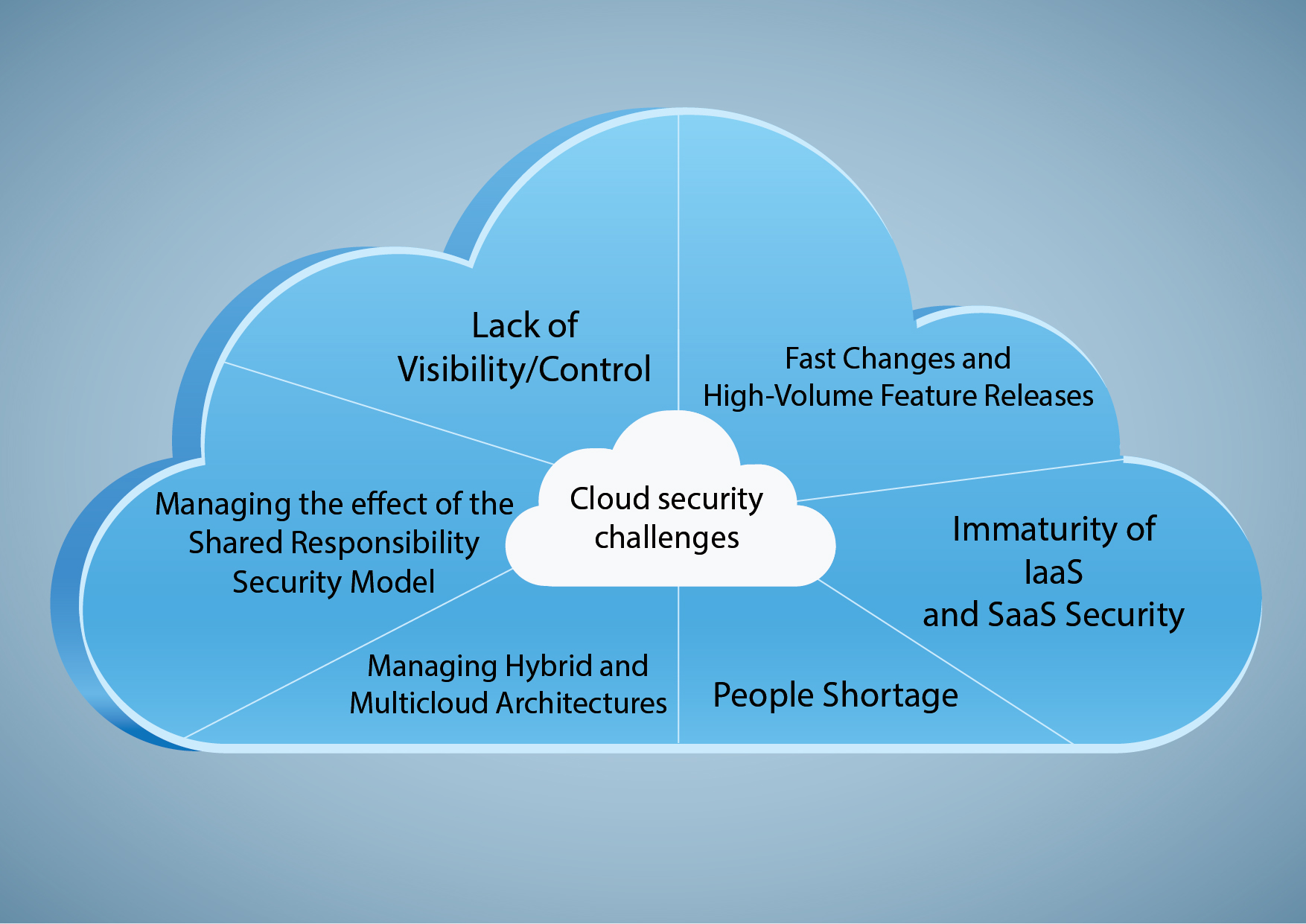
In today’s digital age, cloud computing has become an integral part of many organizations’ IT infrastructure. Google Cloud, one of the leading cloud service providers, offers a wide range of benefits, including scalability, flexibility, and cost savings. However, with these benefits come unique challenges related to security and compliance. It is essential to understand the shared responsibility model, which outlines the responsibilities of both the cloud service provider and the customer in ensuring the security and compliance of data and applications in the cloud.
The shared responsibility model in Google Cloud specifies that Google is responsible for the security of the underlying infrastructure, while customers are responsible for securing their applications, data, and identities in the cloud. This means that customers must implement appropriate security measures, such as access management, data encryption, and network security, to protect their assets in the cloud. Google Cloud provides various security features and capabilities to help customers meet their security and compliance requirements.
Google Cloud’s Security Features and Capabilities
Google Cloud offers a wide range of security features and capabilities to help customers protect their applications and data in the cloud. These features are designed to provide customers with the tools and controls they need to implement a robust security posture and meet their compliance requirements.
One of the key security features of Google Cloud is identity and access management. Google Cloud provides a centralized identity and access management system that enables customers to manage user access to their resources in a secure and scalable manner. Customers can use Identity-Aware Proxy (IAP) to control access to cloud applications based on user identity and context. Additionally, Google Cloud supports a wide range of industry-standard authentication protocols, such as OAuth, OpenID Connect, and SAML, to provide customers with flexibility and choice in implementing their access control policies.
Data encryption is another critical security feature of Google Cloud. Google Cloud provides encryption at rest and in transit for all customer data by default, with no additional cost or configuration required. Customers can also manage their own encryption keys using Cloud Key Management Service (KMS) to maintain full control over their data encryption. Furthermore, Google Cloud supports customer-supplied encryption keys (CSEK) for customers who want to use their own encryption keys for data at rest.
Network security is also a top priority for Google Cloud. Google Cloud provides a range of network security features, such as firewall rules, Virtual Private Cloud (VPC), and Security Groups, to help customers secure their network traffic and protect their applications and data from unauthorized access. Google Cloud also provides Distributed Denial of Service (DDoS) protection and Cloud Load Balancing to ensure high availability and performance for customer applications.
Security logging and monitoring is another essential security feature of Google Cloud. Google Cloud provides customers with detailed logs and monitoring capabilities to help them detect and respond to security threats in real-time. Customers can use Cloud Logging and Cloud Monitoring to collect, analyze, and alert on log data from their Google Cloud resources. Additionally, Google Cloud provides Cloud Security Command Center (SCC) to provide customers with a centralized view of their security posture and compliance status.
Google Cloud’s Compliance Certifications and Standards
Google Cloud has achieved numerous compliance certifications and standards that demonstrate its commitment to security and compliance. These certifications and standards provide customers with the confidence that Google Cloud has implemented the necessary controls and processes to meet their regulatory and compliance requirements.
Some of the key compliance certifications and standards that Google Cloud has achieved include SOC 1, SOC 2, ISO 27001, HIPAA, and PCI-DSS. These certifications and standards cover a wide range of compliance requirements, such as financial reporting, data privacy, and payment card security. By achieving these certifications and standards, Google Cloud has demonstrated its ability to meet the stringent requirements of these compliance frameworks.
SOC 1 and SOC 2 are reports that are issued by independent third-party auditors that attest to the design and operating effectiveness of Google Cloud’s controls related to security, availability, and confidentiality. These reports are based on the Trust Services Criteria, which are widely recognized and accepted standards for control objectives and controls.
ISO 27001 is an international standard for information security management systems (ISMS) that provides a framework for establishing, implementing, maintaining, and continually improving an organization’s information security management system. Google Cloud has achieved ISO 27001 certification for its data centers, infrastructure, and services.
HIPAA is a US federal law that establishes national standards for the protection of certain health information. Google Cloud has implemented the necessary controls and processes to enable customers to use its services in a manner that is consistent with the HIPAA Privacy and Security Rules.
PCI-DSS is a set of security standards that are designed to ensure the secure handling of payment card data. Google Cloud has achieved PCI-DSS certification for its Compute Engine, App Engine, and Kubernetes Engine services.
These compliance certifications and standards benefit Google Cloud customers in several ways. First, they provide customers with the confidence that Google Cloud has implemented the necessary controls and processes to meet their compliance requirements. Second, they reduce the burden on customers to perform their own security and compliance assessments. Third, they enable customers to leverage Google Cloud’s compliance investments to achieve their own compliance objectives.
How to Implement Security and Compliance in Google Cloud
Google Cloud provides a wide range of security and compliance features and capabilities that enable customers to secure their applications and data in the cloud. To fully leverage these features and capabilities, customers should follow best practices for access management, data protection, and network security. In this section, we provide practical guidance on how to implement security and compliance in Google Cloud.
Best Practices for Access Management
Access management is a critical aspect of cloud security and compliance. Google Cloud provides a range of tools and services for managing user access, including Identity-Aware Proxy (IAP), Cloud Identity, and Cloud IAM. To implement effective access management in Google Cloud, customers should:
- Define clear access policies that align with their business objectives and compliance requirements.
- Implement role-based access control (RBAC) to ensure that users have the minimum necessary privileges to perform their job functions.
- Use multi-factor authentication (MFA) to reduce the risk of unauthorized access.
- Regularly review and audit access logs to detect and respond to security threats.
Best Practices for Data Protection
Data protection is another critical aspect of cloud security and compliance. Google Cloud provides a range of tools and services for protecting customer data, including data encryption, access control, and data loss prevention (DLP). To implement effective data protection in Google Cloud, customers should:
- Encrypt data at rest and in transit using industry-standard encryption algorithms.
- Implement access controls to ensure that only authorized users can access sensitive data.
- Use DLP to detect and prevent the exfiltration of sensitive data.
- Regularly test and validate data backups to ensure that they can be restored in the event of a data loss or breach.
Best Practices for Network Security
Network security is essential for protecting applications and data in the cloud. Google Cloud provides a range of tools and services for securing network traffic, including Virtual Private Cloud (VPC), Cloud Load Balancing, and Cloud Armor. To implement effective network security in Google Cloud, customers should:
- Use VPC to segment their network into security zones and subnets.
- Implement firewall rules to control ingress and egress traffic to and from their network.
- Use Cloud Load Balancing to distribute traffic across multiple instances and regions for high availability and scalability.
- Use Cloud Armor to protect their applications from DDoS attacks and other security threats.
Real-World Examples and Case Studies
To illustrate the best practices for implementing security and compliance in Google Cloud, we can look at real-world examples and case studies. For instance, a financial services company may use Google Cloud’s encryption and access control features to secure sensitive financial data, while a healthcare provider may use Google Cloud’s HIPAA compliance features to protect patient data. By following best practices and leveraging Google Cloud’s security and compliance capabilities, customers can achieve their business objectives while maintaining the highest level of security and compliance.
Emerging Trends and Challenges in Cloud Security and Compliance
As cloud computing continues to grow in popularity, new security and compliance challenges are emerging. Cybercriminals are becoming more sophisticated, and regulatory requirements are constantly evolving. To stay ahead of these challenges, Google Cloud is investing in cutting-edge security technologies and compliance initiatives. In this section, we will discuss some of the emerging trends and challenges in cloud security and compliance and explain how Google Cloud is addressing them.
Ransomware Attacks
Ransomware attacks are becoming increasingly common, and they can have devastating consequences for businesses of all sizes. In a ransomware attack, cybercriminals encrypt a victim’s data and demand a ransom payment in exchange for the decryption key. To protect against ransomware attacks, Google Cloud offers a range of security features, including data encryption, access control, and security logging and monitoring. Customers can also use Google Cloud’s backup and disaster recovery services to ensure that their data is safe and recoverable in the event of an attack.
Data Breaches
Data breaches are another major concern for businesses in the cloud. In a data breach, sensitive information is exposed to unauthorized parties, which can result in financial losses, reputational damage, and legal liabilities. To prevent data breaches, Google Cloud offers a range of security features, including data encryption, access control, and security logging and monitoring. Customers can also use Google Cloud’s vulnerability assessment and penetration testing services to identify and remediate security vulnerabilities before they can be exploited.
Regulatory Changes
Regulatory requirements for cloud security and compliance are constantly evolving. For example, the European Union’s General Data Protection Regulation (GDPR) imposes strict requirements on how businesses handle personal data. To help customers stay compliant with regulatory requirements, Google Cloud offers a range of compliance certifications and standards, such as SOC 1, SOC 2, ISO 27001, HIPAA, and PCI-DSS. Google Cloud also provides documentation, training, and customer support to help customers understand and implement these requirements.
Emerging Trends
In addition to these challenges, there are several emerging trends in cloud security and compliance that businesses should be aware of. For example, the increasing use of artificial intelligence and machine learning is creating new security and compliance risks. To address these risks, Google Cloud is investing in cutting-edge security technologies, such as zero-trust security models and privacy-preserving data analytics. By staying ahead of these trends, Google Cloud is helping businesses to stay secure and compliant in an ever-changing landscape.
Google Cloud’s Security Resources and Support
Google Cloud offers a wide range of resources and support to help customers implement security and compliance in their cloud environments. In this section, we will highlight some of the key resources and support options available to Google Cloud customers.
Documentation
Google Cloud provides extensive documentation on its security features and capabilities. The documentation covers a wide range of topics, including identity and access management, data encryption, network security, and security logging and monitoring. Customers can use the documentation to learn how to configure and use Google Cloud’s security features and capabilities, as well as how to implement best practices for access management, data protection, and network security.
Training
Google Cloud offers a range of training programs to help customers improve their cloud security skills. The training programs cover a wide range of topics, including security fundamentals, incident response, and compliance. Customers can use the training programs to learn how to implement and manage Google Cloud’s security features and capabilities, as well as how to comply with regulatory requirements and industry standards.
Customer Support
Google Cloud provides 24/7 customer support to help customers with their security and compliance needs. Customers can contact Google Cloud’s support team through a variety of channels, including email, phone, and chat. Google Cloud’s support team can help customers troubleshoot security issues, answer questions about Google Cloud’s security features and capabilities, and provide guidance on how to implement best practices for access management, data protection, and network security.
Community
Google Cloud has a vibrant community of users and developers who share their knowledge and expertise on cloud security and compliance. Customers can join Google Cloud’s community forums to ask questions, share their experiences, and learn from other customers. Google Cloud’s community also hosts events, such as meetups and webinars, where customers can learn about the latest trends and best practices in cloud security and compliance.
Partners
Google Cloud has a network of partners who offer security and compliance solutions for Google Cloud customers. Customers can work with Google Cloud’s partners to implement security and compliance solutions that meet their specific needs. Google Cloud’s partners include leading security vendors, such as Palo Alto Networks, Symantec, and Check Point, as well as consulting and managed services providers, such as Accenture, Deloitte, and KPMG.
Conclusion: The Future of Cloud Security and Compliance with Google Cloud
In today’s digital age, security and compliance are critical considerations for businesses of all sizes. With the increasing adoption of cloud computing, it is essential to understand the unique challenges and benefits of using cloud services like Google Cloud. In this article, we have provided a comprehensive overview of Google Cloud’s security features and capabilities, compliance certifications and standards, and resources and support for implementing security and compliance in Google Cloud.
Google Cloud takes a shared responsibility model for security and compliance, meaning that both Google and its customers have a role to play in securing their data and applications. Google Cloud provides robust security features and capabilities, including identity and access management, data encryption, network security, and security logging and monitoring. These features are designed to help customers meet their compliance requirements and protect their data and applications from cyber threats.
Google Cloud has also achieved numerous compliance certifications and standards, such as SOC 1, SOC 2, ISO 27001, HIPAA, and PCI-DSS. These certifications demonstrate Google Cloud’s commitment to security and compliance and provide customers with the confidence that their data and applications are secure and compliant with industry standards and regulations.
To implement security and compliance in Google Cloud, customers should follow best practices for access management, data protection, and network security. Google Cloud provides extensive documentation, training, and customer support to help customers implement these best practices and achieve their security and compliance objectives. By leveraging Google Cloud’s security features and capabilities, customers can focus on their core business objectives while leaving the security and compliance to Google Cloud.
As cloud computing continues to evolve, emerging trends and challenges in cloud security and compliance will require new approaches and solutions. Google Cloud is committed to addressing these challenges and helping its customers stay informed and prepared. By staying up-to-date with the latest security and compliance developments and leveraging Google Cloud’s security features and capabilities, customers can achieve their business objectives while maintaining the highest level of security and compliance.