What is a Virtual Private Cloud and How Does it Work?
A Virtual Private Cloud (VPC) represents a fundamental building block within the realm of cloud computing. Imagine it as a secure, logically isolated environment inside a public cloud provider’s infrastructure. Think of a modern office space with many companies working side by side; the VPC is that one private office, where only you have control. This isolation is the key feature, providing unparalleled security and control over your cloud resources. The primary function of a vpc cloud is to allow businesses to run applications and store data in their own private space. It’s as if they have their own dedicated data center within the broader cloud environment. A vpc cloud empowers users to define a virtual network, determining IP address ranges, creating subnets, and configuring route tables. The resources that you have inside your vpc cloud are totally under your control.
The isolation offered by a VPC translates directly into enhanced security. Resources deployed within a VPC are shielded from unauthorized access. Users define strict access rules, controlling network traffic both inbound and outbound. This granular control over network access is crucial for protecting sensitive data and applications. Furthermore, the logical isolation contributes significantly to meeting compliance requirements, especially those related to data privacy and security. A vpc cloud allows companies to meet the stringent requirements of the best compliance frameworks.
Beyond security, a vpc cloud provides a high degree of control and customization. Businesses can tailor their virtual network to precisely match their application requirements. For example, they can create multiple subnets to isolate different tiers of an application or configure specific routing rules to optimize network performance. The customizability extends to integrating the vpc cloud with other cloud services, creating a seamless and efficient IT environment. This level of flexibility is crucial for organizations that need to adapt quickly to changing business needs. In short, a vpc cloud offers a powerful and versatile platform for deploying and managing applications in the cloud, combining the benefits of security, control, and customization.
Benefits of Using VPCs: Security, Control, and Customization
Virtual Private Clouds (VPCs) offer significant advantages in security, control, and customization for cloud deployments. A primary benefit is enhanced security. VPCs allow the implementation of network access control lists (ACLs). ACLs act as firewalls, controlling traffic at the subnet level. Security groups provide another layer of security. They manage inbound and outbound traffic for individual instances. These features ensure that only authorized traffic reaches your resources, contributing to a robust security posture in the vpc cloud. These security measures are paramount for businesses handling sensitive data and requiring strict access controls within their vpc cloud.
Users gain extensive control over their virtual network environment with a vpc cloud. This includes defining IP address ranges. Subnets can be created to segment the network. Route tables dictate traffic flow within the VPC and to external networks. This level of control enables organizations to design networks that perfectly match their application requirements. Customization options extend to selecting specific instance types, operating systems, and software. This flexibility is crucial for optimizing performance and cost efficiency within the vpc cloud. The ability to tailor the network environment ensures resources are allocated effectively. This results in a highly optimized and scalable vpc cloud infrastructure.
Furthermore, VPCs offer customization options, allowing tailoring to specific application demands, and compliance benefits are achieved through data isolation. Organizations can meet regulatory requirements by isolating sensitive workloads within a dedicated vpc cloud environment. The isolation provided by a vpc cloud helps meet stringent data privacy standards. This is especially important for industries like healthcare and finance, where compliance is critical. By leveraging the security features and control offered by vpc cloud, businesses can confidently deploy applications and store data in the cloud, knowing their environment is secure, compliant, and highly customizable. The vpc cloud empowers organizations to build secure, scalable, and compliant cloud solutions.
Creating Your First VPC: A Step-by-Step Walkthrough on AWS
Embark on creating your first vpc cloud on Amazon Web Services (AWS) with this practical guide. The process begins by logging into the AWS Management Console. Navigate to the VPC service through the search bar or the services menu. Once in the VPC dashboard, locate and click the “Create VPC” button. AWS offers two options: “VPC only” or “VPC and more.” For simplicity, select “VPC only” to start. Assign a meaningful name to your VPC in the “Name tag” field. This helps in identifying your VPC later.
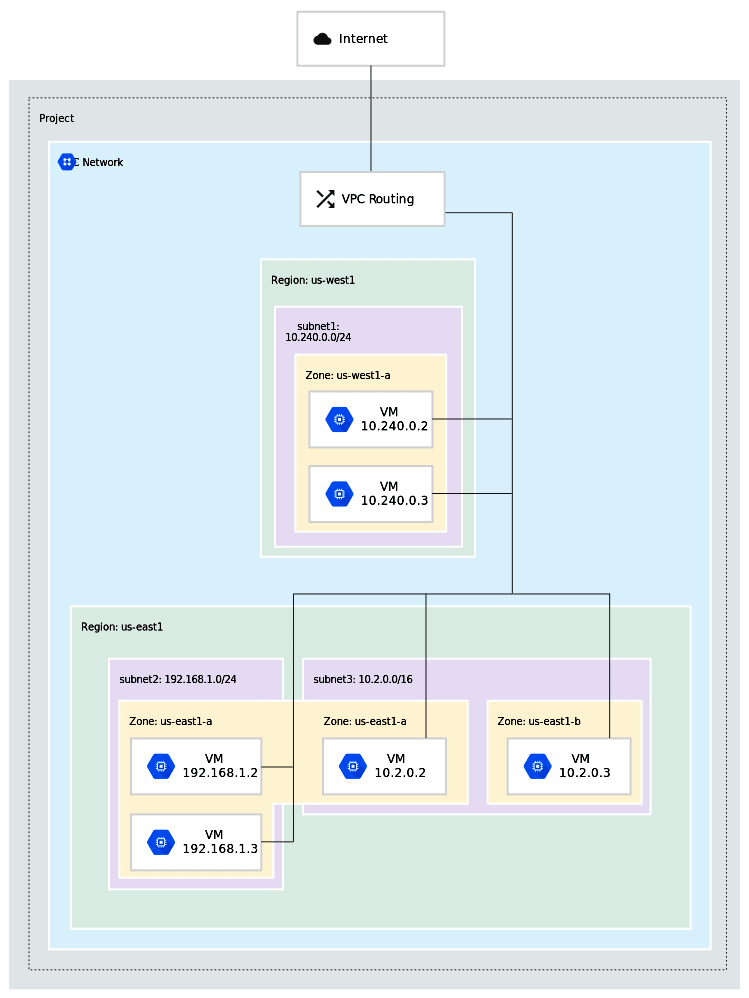
Next, specify the IPv4 CIDR block for your VPC. This determines the range of private IP addresses available within your vpc cloud. A common choice for a small to medium-sized VPC is “10.0.0.0/16,” which provides 65,536 private IP addresses. Choose a CIDR block that does not overlap with any existing networks. After configuring the CIDR block, click “Create VPC.” The AWS Management Console will then provision your virtual network. With the VPC created, the next essential step is creating subnets. Subnets divide the VPC into smaller, isolated networks. To create a subnet, go to the “Subnets” section in the VPC dashboard and click “Create Subnet.” Select the VPC you just created from the “VPC ID” dropdown menu. Provide a name for the subnet, such as “Public Subnet 1.”
Choose an Availability Zone for the subnet to ensure high availability. Specify the IPv4 CIDR block for the subnet, ensuring it falls within the VPC’s CIDR block. For example, use “10.0.1.0/24” for the first subnet. Click “Create Subnet” to provision the subnet. Repeat this process to create additional subnets as needed. Now, configure a route table to control network traffic within your vpc cloud. A route table contains a set of rules, called routes, that determine where network traffic is directed. To create a route table, go to the “Route Tables” section in the VPC dashboard and click “Create Route Table.” Assign a name to the route table and select the VPC you created. Click “Create Route Table” to create the route table. To enable internet access for resources within the public subnet, attach an Internet Gateway to your VPC. Go to the “Internet Gateways” section in the VPC dashboard and click “Create Internet Gateway.” Provide a name for the Internet Gateway and click “Create Internet Gateway.” After creating the Internet Gateway, attach it to your VPC by selecting it and choosing “Attach to VPC” from the “Actions” menu. Select your VPC from the dropdown menu and click “Attach Internet Gateway.” Finally, associate the route table with the public subnet and add a route to the Internet Gateway. This step is crucial for allowing instances in the public subnet to communicate with the internet. Select the route table and go to the “Subnet Associations” tab. Click “Edit subnet associations” and select the public subnet. Then, go to the “Routes” tab and click “Edit routes.” Add a route with the destination “0.0.0.0/0” (all traffic) and the target as the Internet Gateway you created. This directs all internet-bound traffic from the subnet to the Internet Gateway. With these steps, your first vpc cloud on AWS is set up, complete with subnets and internet access.
Configuring Network Security Within Your VPC
Securing a vpc cloud environment is paramount, and this is primarily achieved through security groups and network Access Control Lists (ACLs). Security groups act as virtual firewalls, controlling inbound and outbound traffic at the instance level. They operate on a ‘stateful’ basis, meaning that if you allow inbound traffic on a specific port, the corresponding outbound traffic is automatically allowed. Network ACLs, on the other hand, operate at the subnet level and provide a stateless filtering mechanism. This means that inbound and outbound rules must be explicitly configured. Understanding the difference is critical for a secure vpc cloud configuration.
Consider some common security configurations within a vpc cloud. For example, to protect a web server, you might configure a security group to allow inbound traffic on port 80 (HTTP) and port 443 (HTTPS) from anywhere (0.0.0.0/0). However, it’s crucial to restrict inbound SSH access (port 22) to only specific IP addresses or ranges, limiting potential intrusion points. Similarly, for a database server, you would restrict access to the database port (e.g., 3306 for MySQL) to only the IP addresses of the application servers that need to communicate with it. Network ACLs can be used to block traffic from known malicious IP addresses or to enforce broader network-level security policies within the vpc cloud.
Best practices for hardening your vpc cloud against potential threats include implementing the principle of least privilege, granting only the necessary permissions to users and resources. Regularly review and update your security group and network ACL rules to ensure they remain aligned with your security requirements. Utilize intrusion detection and prevention systems to monitor network traffic for suspicious activity. Enable logging to track network traffic and security events, aiding in incident response and forensic analysis. Multi-Factor Authentication (MFA) should be enforced for all administrative access to the vpc cloud environment. By following these guidelines, you can significantly enhance the security posture of your vpc cloud and protect your valuable data and applications. The continuous assessment and improvement of security measures are vital for a robust vpc cloud environment.
Connecting Your VPC to On-Premises Networks: Hybrid Cloud Scenarios
Establishing a connection between a vpc cloud environment and an on-premises data center allows organizations to create a hybrid cloud. This integration offers flexibility, scalability, and enhanced control over IT infrastructure. A hybrid cloud strategy allows businesses to leverage the benefits of both the public cloud and their existing private infrastructure. Several connectivity options facilitate this integration, each with its own advantages and considerations.
One common method for connecting a vpc cloud to an on-premises network is through a Virtual Private Network (VPN). A VPN creates a secure, encrypted tunnel over the public internet. This tunnel extends the on-premises network to the vpc cloud, enabling secure communication between resources in both environments. VPN connections are relatively easy to set up and are suitable for workloads that do not require extremely high bandwidth or low latency. Another option is Direct Connect (AWS) or equivalent services like Azure ExpressRoute and Google Cloud Interconnect. These services establish a dedicated network connection between the on-premises data center and the cloud provider’s infrastructure. Direct Connect provides higher bandwidth, lower latency, and more consistent network performance compared to VPN connections. Direct connect is ideal for mission-critical applications and large-scale data transfers between the vpc cloud and on-premises environments. Choosing the appropriate connectivity option depends on the specific requirements of the hybrid cloud deployment.
Hybrid cloud deployments offer various use cases. Data migration is a primary application. Organizations can seamlessly migrate data between their on-premises systems and the vpc cloud. This allows for a phased approach to cloud adoption, minimizing disruption to existing operations. Another significant use case is disaster recovery. By replicating critical data and applications to the vpc cloud, organizations can ensure business continuity in the event of a disaster affecting their on-premises infrastructure. The vpc cloud acts as a failover site, providing a resilient and cost-effective disaster recovery solution. Moreover, hybrid clouds enable organizations to extend their computing capacity by offloading workloads to the vpc cloud during peak demand. This allows for greater agility and scalability, ensuring that applications can handle fluctuating workloads without requiring significant investments in on-premises hardware. Hybrid vpc cloud solutions therefore present a balanced approach that fits many organizational needs.
Common VPC Networking Challenges and Solutions
Working with VPCs can present various networking challenges. These challenges often stem from misconfigurations, security oversights, or a lack of understanding of VPC cloud networking principles. Addressing these issues promptly is crucial for maintaining a stable and secure cloud environment. One common problem is routing issues, where instances within the VPC cloud are unable to communicate with each other or with resources outside the VPC. This can be caused by incorrect route table configurations, missing routes, or overlapping CIDR blocks. Always double-check your route tables to ensure they contain the necessary routes for traffic to flow correctly.
Another frequent challenge is connectivity problems when peering VPCs. This typically occurs when there are overlapping CIDR blocks between the peered VPCs. VPC peering requires unique, non-overlapping IP address ranges. To resolve this, you’ll need to reconfigure the IP address range of one of the VPCs. Security misconfigurations can also lead to issues. For instance, overly permissive security group rules can expose your VPC cloud resources to unnecessary risks. Conversely, overly restrictive rules can block legitimate traffic. Regularly review your security group and network ACL configurations to ensure they align with the principle of least privilege. Ensure that you have properly configured your inbound and outbound rules for each security group associated with your resources, allowing only necessary traffic.
Troubleshooting VPC cloud networking problems often involves a systematic approach. Start by examining the route tables to verify the correct routes are in place. Next, check the security group and network ACL rules to ensure traffic is not being blocked. Utilize network monitoring tools to track traffic flow and identify potential bottlenecks or issues. Furthermore, consult the official documentation and community resources provided by your cloud provider for specific guidance and troubleshooting steps. Remember to document your VPC cloud configurations and changes to facilitate future troubleshooting efforts. Many issues related to vpc cloud implementations can be avoided with careful planning and adherence to best practices. Properly designed networks are easier to manage, scale, and secure.
Comparing VPC Solutions: AWS vs Azure vs Google Cloud
When choosing a cloud provider, understanding their Virtual Private Cloud (VPC) offerings is crucial. AWS (Amazon Virtual Private Cloud), Azure (Azure Virtual Network), and Google Cloud (Virtual Private Cloud) each provide robust solutions for creating isolated networks within their public cloud infrastructure. While all three share the core functionality of enabling users to define and control their network environment, key differences exist in their features, pricing models, and ease of use. A thorough comparison of these platforms is essential for selecting the one that best aligns with your organization’s specific needs and technical expertise to manage your vpc cloud.
AWS VPC is known for its maturity and extensive feature set. It offers granular control over network configurations, including security groups, network ACLs, and route tables. Azure Virtual Network integrates seamlessly with other Azure services and boasts a user-friendly interface, particularly for those already familiar with the Microsoft ecosystem. Google Cloud VPC emphasizes its global network and software-defined networking capabilities, allowing for flexible and scalable deployments. The pricing structures also vary, with AWS offering a pay-as-you-go model, Azure providing reserved instance options, and Google Cloud focusing on sustained use discounts. Each vendor provides options and possibilities for its vpc cloud.
Ultimately, the optimal choice depends on your specific requirements and priorities. Consider factors such as the complexity of your network architecture, the level of integration needed with other cloud services, and your team’s expertise. A detailed comparison, as outlined in the table below, can help you make an informed decision and effectively manage your vpc cloud. Evaluating differentiators like advanced networking features, integration with container orchestration platforms (e.g., Kubernetes), and serverless computing environments is important. Also, carefully review documentation and community resources to understand the nuances of each platform and ensure seamless deployment and management of your virtual networks. Take into account the overall scalability of the vpc cloud based on the provider selected.
Advanced VPC Concepts: Peering, Transit Gateways, and More
Virtual Private Cloud (VPC) environments offer advanced networking capabilities that extend beyond basic setup. VPC peering enables connections between VPCs, facilitating resource sharing and communication as if they were a single network. This is particularly useful for organizations with multiple VPCs across different AWS accounts or regions. Establishing a VPC peering connection involves configuring routing tables to direct traffic between the peered VPCs and updating security groups to allow traffic flow. This allows applications in different vpc cloud networks to communicate securely and efficiently.
For more complex network topologies involving numerous VPCs and on-premises connections, Transit Gateways provide a simplified and scalable solution. A Transit Gateway acts as a central hub, allowing you to connect multiple VPCs and VPN connections in a hub-and-spoke configuration. This eliminates the need for complex peering arrangements between individual VPCs, reducing management overhead and improving network visibility. Transit Gateways support various routing options, including static and dynamic routing, to accommodate different network requirements. The vpc cloud transit gateway centralizes network management.
Beyond peering and transit gateways, VPCs offer other advanced features such as VPC endpoints and PrivateLink, enhancing security and privacy. VPC endpoints enable you to connect to AWS services without traversing the public internet, keeping your data within the AWS network. PrivateLink allows you to offer your own services to other AWS customers in a secure and private manner, without exposing your VPC to the internet. Furthermore, consider the integration of VPCs with serverless technologies like AWS Lambda and container orchestration platforms like Kubernetes. Lambda functions can be deployed within a VPC to access resources securely, while Kubernetes clusters can be configured to use VPC networking for enhanced isolation and control. These advanced features make the vpc cloud a robust and versatile platform for building complex and secure cloud-based applications. The modern vpc cloud is able to host and isolate many cloud native services.