Understanding Daemon Sets: Core Concepts
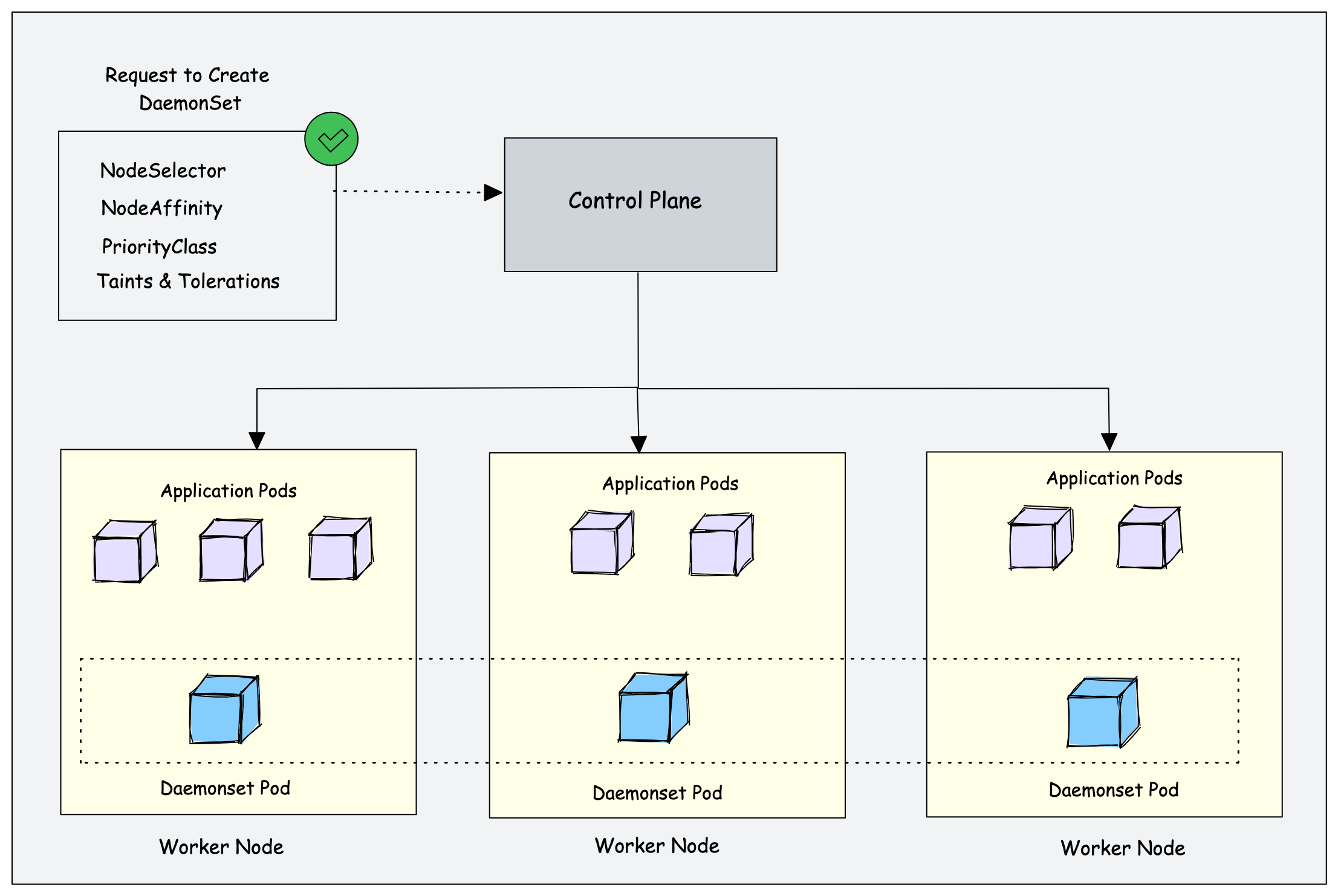
Daemon Sets in Kubernetes are a specialized type of controller that ensures consistent application deployment across every node in a cluster. A daemon set guarantees a single instance of a particular application runs on each node. Their purpose is crucial for managing stateful applications and guaranteeing reliable service availability. Key functionalities of daemon sets include maintaining a consistent application presence across all nodes, simplifying system-level utilities deployment, and enabling high availability deployments. A significant difference between DaemonSets and other Kubernetes object types, such as Deployments and StatefulSets, lies in their deployment strategy. While Deployments manage replicas across available nodes, DaemonSets are designed to deploy a single copy per node.
A daemon set excels in situations requiring persistent background services on each node. Excellent examples include network monitoring agents, log aggregators, or system utilities. Daemon Sets are especially well-suited for such tasks where consistent presence on each machine is paramount. The predictable deployment pattern and the assurance that each machine runs the daemon set allow for more streamlined and robust service management. Understanding these differences allows for the correct application of daemon set deployments in diverse scenarios. This is vital for selecting the right Kubernetes object type for any given application deployment, thereby optimizing resource management and enhancing efficiency.
Crucially, daemon sets play a pivotal role in ensuring a consistent application state across every node in the Kubernetes cluster. This consistency is a core concept of daemon sets, ensuring reliability and availability. The use of daemon sets for maintaining a constant application presence on each machine is a crucial characteristic that distinguishes them from other deployment types in Kubernetes. Their purpose in Kubernetes is to establish a consistent and dependable service across every machine in the cluster. Furthermore, understanding the difference between daemon sets and other Kubernetes object types like Deployments and StatefulSets is critical for making informed choices about deployment strategy. This facilitates the appropriate application of the correct tool and helps maintain a high level of consistency throughout the cluster.
Designing Daemon Set Strategies
Daemon sets are particularly well-suited for applications that need to run on every node in a Kubernetes cluster. These applications often monitor system resources, collect logs, or perform tasks that require presence on every node. Crucially, daemon sets ensure reliable and consistent execution of these tasks across all cluster nodes. Consider applications like network monitoring agents, which consistently gather data from all network interfaces.
Compared to other Kubernetes object types, daemon sets excel in situations where consistent presence is essential across all nodes. For example, a daemon set might manage system-level utilities or deploy agents that require constant monitoring of every node. They stand in contrast to deployments, which aim to maintain a specific number of application instances, or stateful sets, which manage applications with persistent storage. This allows for flexibility in managing distributed applications across a cluster, with daemon sets a practical choice for tasks needing consistent presence across all nodes. This broad applicability highlights the value of daemon sets in various use cases, making them a valuable asset in the Kubernetes ecosystem. Applications that benefit from a daemon set’s features often involve consistent monitoring, or the collection of data, in situations requiring system-wide presence, such as logging.
Another illustrative example concerns log aggregation. A daemon set could be the optimal choice for deploying log collection agents on each node. This approach ensures that logs from all nodes are reliably collected and aggregated, enabling comprehensive analysis of cluster-wide activities. This centralized approach to log management helps improve cluster observability and provides a way to gain valuable insights from all the nodes in a Kubernetes cluster. Daemon sets are also ideal for deploying agents that need to interact directly with system resources, making them a flexible choice for a wide range of system-level utilities and monitoring applications. Consider also that a daemon set offers a powerful method for managing agents on all cluster nodes.
Implementing Daemon Sets in Kubernetes
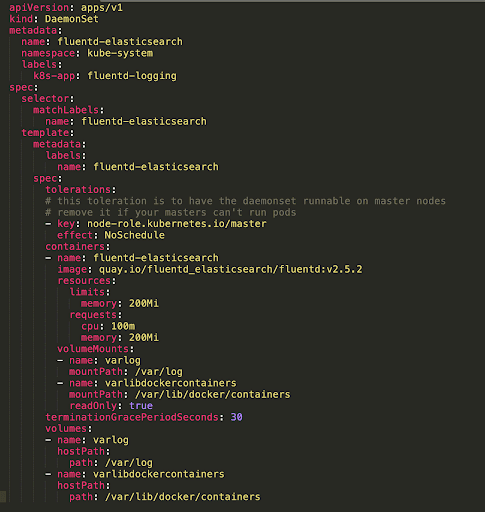
Implementing a daemon set in Kubernetes involves crafting YAML configuration files that precisely define the desired behavior. These files serve as blueprints, instructing the Kubernetes control plane on how to deploy and manage the daemon set. Understanding the structure and content of these files is crucial for successfully deploying and maintaining a daemon set.
A fundamental aspect of the YAML configuration revolves around specifying the desired image. The correct container image dictates the exact functionality of the daemon set’s pods. Furthermore, the configuration should clearly define resource limits and requests. These specifications ensure that each pod receives the necessary resources, thereby preventing resource contention and performance bottlenecks. Precise resource allocation also promotes cluster stability and optimal performance for the daemon set. Properly configuring labels and selectors aids in identifying and managing daemon set pods effectively. This allows for targeted updates and maintenance tasks. For instance, labels can be used to distinguish between pods running different versions of the daemon set or different components of the daemon set. Adhering to these best practices facilitates smoother and more reliable operations.
The configuration files should also define the desired number of pods, as well as the conditions under which they should start and stop. Crucially, the YAML files should specify the appropriate service accounts and security contexts for accessing required resources. Implementing these security configurations protects the cluster from unauthorized access and ensures compliance with security best practices. Thoroughly testing the configuration before deployment is vital. Comprehensive testing ensures that the daemon set functions as expected and that there are no unforeseen errors. Rigorous testing minimizes risks and enhances the reliability of the daemon set.
Managing Daemon Set Deployments
Effective management of daemon set deployments is crucial for maintaining service availability and ensuring the stability of Kubernetes clusters. Scaling, updating, and rolling out updates require meticulous planning and execution. Understanding these processes is key to preventing disruptions and downtime. Monitoring daemon set health during these operations is essential. Detailed monitoring will help prevent potential issues during updates.
Scaling a daemon set involves adjusting the number of pods running across nodes. Implementing proper scaling mechanisms ensures sufficient resources are available to meet demands. This proactive approach allows for graceful handling of increased or decreased workloads. Careful consideration must be given to the impact of scaling on the overall system’s performance and stability. For instance, rapid scaling might induce stress on the cluster. Updates for daemon sets, like those for other Kubernetes resources, often involve rolling updates. A rolling update strategy progressively replaces old pods with new ones. This technique limits disruption by maintaining at least one version of the daemon set running at any given time. Careful configuration and monitoring are vital during the process to avoid cascading failures. Strategies for dealing with potential issues, including graceful degradation or failovers, are essential for maintaining service continuity during updates. Continuous monitoring is essential during the update phase, allowing quick identification and remediation of any issues that might arise.
Troubleshooting and preventing problems are crucial for maintaining continuous operation. Maintaining a thorough logging system allows for efficient debugging and rapid identification of potential issues. Monitoring tools provide insights into the daemon set’s health and operational status. Addressing any reported problems, whether they stem from resource constraints or configuration issues, is vital to maintain operational efficiency. This proactive approach will limit disruptions and support continuous, reliable service availability. Accurate assessment of resource consumption and proper allocation helps ensure the daemon set functions optimally. Monitoring these aspects and understanding the implications of any updates are crucial for avoiding future problems.
Troubleshooting and Common Challenges
Troubleshooting daemon set deployments often involves understanding common issues and implementing effective solutions. One frequent challenge is ensuring proper communication between the daemon set pods and the target systems. Network connectivity problems can prevent daemon set pods from performing their designated tasks. Network configuration issues, firewall rules, or insufficient permissions are potential causes. Diagnose these issues by meticulously examining logs for errors related to network access or communication failures. Consider network monitoring tools to identify potential problems.
Another common issue is ensuring the daemon set’s components correctly install and start. This might manifest as failed pod initialization, or inconsistencies in running processes. Analyze pod logs for errors in container startup, execution issues, or resource constraints. Investigate if the daemon set’s container image is compatible with the Kubernetes cluster’s infrastructure. Use Kubernetes monitoring tools to track the daemon set’s health and identify any deviations from expected behavior. Thorough log analysis and comprehensive monitoring are vital for resolving these issues effectively.
Misconfigurations in daemon set deployments can lead to unexpected behavior or failures. Double-check the YAML configuration files for any syntax errors, incorrect resource requests, or inadequate labels. Use the Kubernetes command-line tool for checking the daemon set manifest for potential problems. Incorrectly specified selectors or labels can also lead to mismatched daemon set pods. Carefully review selector and label specifications in the YAML file. Reviewing and understanding the intended function of the daemon set and the target systems is vital in properly troubleshooting these scenarios. Verify that the daemon set is properly configured to interact with the intended components of the target system. These troubleshooting steps help ensure optimal performance and operational efficiency of a daemon set deployment.
Optimizing Daemon Set Performance
Optimizing daemon set performance is crucial for achieving efficient resource utilization and minimizing costs in a Kubernetes cluster. Proper configuration of resource requests and limits directly impacts the daemon set’s performance. Understanding how to effectively manage resource allocation is paramount for maintaining a healthy and responsive cluster. A well-tuned daemon set ensures consistent service availability and minimizes resource contention.
To optimize resource allocation, precisely define the resource requests and limits for the daemon set’s pods. This entails specifying the CPU and memory resources required by each daemon set pod. Setting appropriate requests prevents over-allocation, ensuring sufficient resources are available for other applications. Conversely, setting limits prevents excessive resource consumption by a single pod, safeguarding other deployments. Careful consideration must be given to both requests and limits to avoid resource starvation or excessive resource consumption by the daemon set.
Managing the pod lifecycle effectively is another critical aspect of daemon set optimization. Strategies for managing pod lifecycle events, such as startup, termination, and restart, influence the overall performance of the daemon set. Efficient handling of these events can significantly enhance application responsiveness and stability. Monitoring the pod lifecycle provides crucial insights into potential performance bottlenecks. Robust monitoring and logging tools are vital for pinpointing performance issues and optimizing the overall daemon set performance. Monitoring daemon set resource consumption, including CPU usage and memory usage, and analyzing metrics provide valuable insights for optimizing daemon set behavior. Furthermore, employing automated scaling strategies in response to resource demands contributes to ensuring the daemon set’s responsiveness to fluctuations in load. A well-orchestrated daemon set will be agile and adapt to varying workloads without compromising system stability. The performance of a daemon set directly affects the efficiency of the entire Kubernetes cluster, making optimization efforts crucial for overall cluster health and performance.
Advanced Daemon Set Techniques
This section delves into advanced features of daemon sets, empowering users with sophisticated customization options. Leveraging annotations and custom resource definitions (CRDs) enables extending the functionality of daemon sets. Integrating daemon sets with other Kubernetes components enhances their capabilities.
Annotations offer a flexible mechanism for adding metadata to daemon set resources. This metadata can be used to tailor the behavior of the daemon set in specific scenarios. For instance, annotations can be used to configure specific parameters for the daemon set’s containers. Utilizing annotations unlocks possibilities for fine-grained control over daemon set behavior. Custom resource definitions (CRDs) allow for the creation of custom resource types. With CRDs, users can extend the Kubernetes API to define new resources tailored to specific needs. Extending the capabilities of a daemon set becomes possible by incorporating CRDs. Integrating daemon sets with other Kubernetes components enhances functionality. For instance, this could involve integrating with ingress controllers for enhanced network management or with job controllers to manage daemon set-related tasks.
By exploring these advanced techniques, users can optimize their daemon set deployments for complex use cases. Advanced configurations, like defining custom resource limits or using labels for more nuanced pod selection strategies, will further enhance the efficacy of the daemon set. In essence, these techniques equip users with the power to create tailored daemon set solutions optimized for unique cluster needs, thus ensuring optimal functionality within their Kubernetes environment.
Best Practices and Considerations for Daemon Sets
Daemon sets offer a powerful mechanism for managing system-level applications within a Kubernetes cluster. Understanding when a daemon set is the ideal choice is crucial for optimal cluster management. This involves evaluating trade-offs against alternative approaches like deployments and stateful sets, considering the nature of the application.
Daemon sets excel when deploying agents or services that must run on every node. Examples include network monitoring tools, log aggregators, or system utilities. A key advantage of daemon sets is their guaranteed presence across all nodes. This ensures reliable service availability and consistent functionality. This proactive approach to resource management contrasts with other Kubernetes object types, particularly deployments, where ensuring application presence on every node requires explicit configuration. Thorough planning and analysis are essential to determine whether the deployment demands of a daemon set outweigh the potential advantages. A critical element in choosing a daemon set is the application’s dependency on widespread deployment across all nodes. Kubernetes’ daemon set mechanism ensures consistent functionality on all nodes. Assessing resource requirements and the need for consistent behavior across the cluster helps in determining if a daemon set is appropriate.
Security is paramount when implementing daemon sets. Adhering to the principle of least privilege is critical. Ensure the daemon set pods have only the necessary permissions to function. Carefully define the authorization policies to restrict access to sensitive resources. This precautionary measure prevents potential security vulnerabilities within the daemon set deployment. Robust security protocols are necessary for a dependable and secure Kubernetes environment. A security audit during the implementation phase helps to mitigate potential vulnerabilities. Properly configured authorization restrictions limit the potential for unintended consequences. The security of daemon sets can be enhanced through proactive measures. Regularly reviewing security practices ensures the sustained security of the daemon set deployment.