Understanding the Basics of Multi-AZ Traffic Management
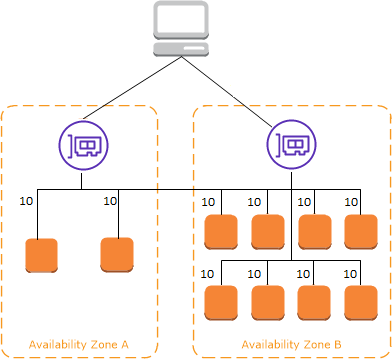
Availability Zones (AZs) are distinct locations within a cloud region. Each AZ is designed to be isolated from failures in other AZs. This isolation is crucial for achieving high availability and fault tolerance for applications. Distributing traffic across multiple AZs ensures that if one AZ experiences an outage, the application remains available in other AZs. This distribution is a fundamental strategy for building resilient systems. A key component in this multi-AZ architecture is a cross zone load balancer. This load balancer intelligently distributes incoming traffic across healthy instances in different AZs.
The benefits of distributing traffic across AZs are significant. Reduced downtime is a primary advantage. By having redundant instances in multiple AZs, the application can withstand the failure of a single AZ without significant disruption. Improved performance can also be achieved. A cross zone load balancer can route traffic to the AZ with the lowest latency or the most available resources. This optimization enhances the user experience. Using a cross zone load balancer offers significant protection from localized failures.
Implementing a cross zone load balancer is essential for modern cloud architectures. It provides a layer of abstraction that simplifies the management of traffic across multiple AZs. The cross zone load balancer continuously monitors the health of instances in each AZ. It automatically adjusts traffic distribution to avoid unhealthy instances. This dynamic adjustment ensures that traffic is always routed to available resources. This capability is crucial for maintaining application availability and performance in the face of unexpected events. A well-configured cross zone load balancer contributes significantly to the overall reliability and robustness of an application.
How to Configure Traffic Distribution Across Zones for Enhanced Resilience
Configuring traffic distribution across multiple Availability Zones (AZs) is a critical step in building resilient and highly available applications. This process involves setting up a cross zone load balancer and configuring it to distribute incoming traffic across healthy instances located in different AZs. While the specific steps may vary slightly depending on the cloud provider (AWS, Azure, GCP), the core concepts remain the same. A well-configured cross zone load balancer can significantly reduce downtime and improve overall application performance.
The initial step involves provisioning a load balancer that supports cross-AZ traffic distribution. This is often achieved using a managed load balancing service provided by your cloud provider. During the load balancer setup, it is essential to enable cross-zone load balancing. Subsequently, you will need to create target groups, which define the set of instances or resources that the load balancer will distribute traffic to. Each target group should contain instances located in different AZs. This ensures that traffic is spread across multiple zones, enhancing fault tolerance. Health checks are a vital component of this setup. The load balancer periodically checks the health of each instance in the target groups. If an instance becomes unhealthy, the load balancer automatically stops sending traffic to it, routing traffic only to healthy instances in other AZs. Proper configuration of health checks is essential for a cross zone load balancer to function correctly. You should configure health checks to accurately reflect the health of your application. These checks typically involve sending HTTP or TCP requests to specific endpoints on your instances.
After setting up the load balancer, target groups, and health checks, the final step is to configure the load balancer’s listeners and rules. Listeners define the ports and protocols that the load balancer will listen on for incoming traffic. Rules determine how traffic is routed to the different target groups based on various criteria, such as the request path or hostname. Ensure that your load balancer is configured to handle traffic efficiently across all Availability Zones. Regular monitoring of the load balancer’s performance and health is also recommended to identify and address any potential issues promptly. This includes monitoring metrics such as request latency, error rates, and the health of individual instances. A properly implemented cross zone load balancer significantly enhances the resilience and availability of your applications.
Comparing Different Approaches to Multi-AZ Load Balancing
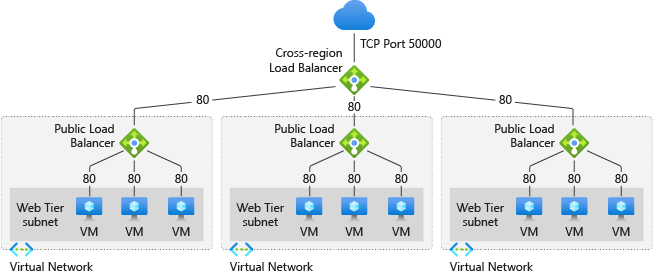
Several architectures exist for distributing traffic across Availability Zones (AZs). These range from simple DNS-based solutions to sophisticated dedicated load balancing services. Each approach presents its own set of advantages and disadvantages concerning performance, cost, and complexity. The selection of an appropriate architecture hinges on specific application requirements and organizational constraints. A key consideration when selecting the approach should be a solid understanding of the underlying characteristics of a cross zone load balancer.
DNS-based load balancing is a relatively straightforward approach. It involves configuring DNS records to resolve to multiple IP addresses, each corresponding to an instance in a different AZ. When a client requests the application, the DNS server returns a list of IP addresses. The client then attempts to connect to one of these addresses. This method is simple to implement and can be cost-effective. However, it lacks real-time health checking. If an instance in one AZ becomes unhealthy, the DNS server might continue to direct traffic to it until the DNS records are updated. This can result in downtime or degraded performance for some users. Furthermore, DNS-based solutions typically do not offer granular control over traffic distribution. They might not be suitable for applications requiring sophisticated load balancing algorithms or session persistence. The biggest risk might be not using a cross zone load balancer, which might lead to more manual work in the case of AZ issues.
Dedicated load balancing services, such as Application Load Balancers (ALBs) offered by cloud providers, provide a more robust and feature-rich solution. These services actively monitor the health of instances in different AZs and automatically route traffic only to healthy instances. They also support various load balancing algorithms, such as round robin, least connections, and weighted distribution, enabling fine-grained control over traffic flow. Furthermore, ALBs typically offer features such as SSL termination, session persistence, and content-based routing. While dedicated load balancing services offer significant advantages in terms of reliability and performance, they also come with a higher cost and complexity compared to DNS-based solutions. For applications requiring high availability and fault tolerance, the benefits of a cross zone load balancer generally outweigh the increased cost and complexity. Organizations should carefully evaluate their specific requirements and constraints before selecting an approach to multi-AZ load balancing, keeping in mind that an efficient cross zone load balancer strategy should be in place.
Deep Dive into Application Load Balancer Zone Redundancy
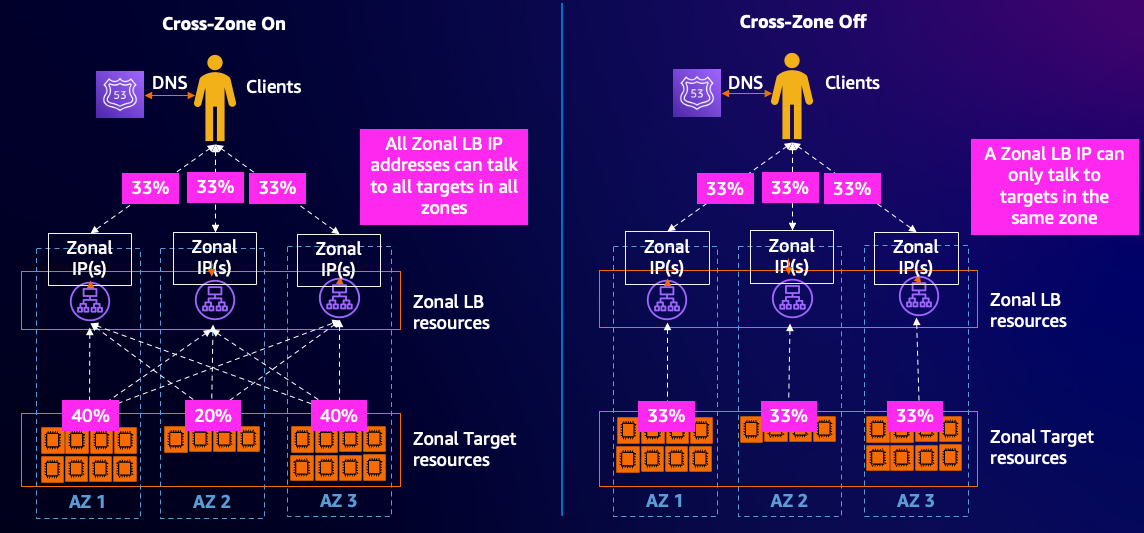
Application Load Balancers (ALBs) are designed with inherent zone redundancy to ensure high availability and fault tolerance. This means that an ALB can automatically distribute incoming traffic across multiple Availability Zones (AZs). The underlying mechanisms of an ALB are crucial to understanding how it handles AZ failures and maintains application uptime. The core concept is that the ALB itself is distributed. Its components are deployed across multiple AZs. This design ensures that the ALB remains operational even if one or more AZs experience issues. A key component is the data plane, responsible for forwarding traffic to healthy instances.
The ALB continuously monitors the health of registered instances in each AZ through health checks. These health checks are configurable and allow you to define the criteria for determining whether an instance is healthy and capable of serving traffic. For example, you can specify an HTTP endpoint that the ALB will periodically query. If an instance fails a health check, the ALB automatically stops routing traffic to it within that specific AZ. This process is dynamic and ensures that only healthy instances receive traffic. This automated rerouting is a fundamental aspect of how a cross zone load balancer provides resilience. The health check mechanism is vital for a cross zone load balancer, maintaining the integrity of the service during disruptions. Furthermore, the ALB’s routing algorithms consider the health status of instances. The cross zone load balancer will avoid unhealthy instances and prefer healthy ones, ensuring optimal performance and availability.
In the event of an AZ failure, the ALB seamlessly shifts traffic to healthy instances in the remaining operational AZs. This failover process is automatic and requires no manual intervention. The ALB is aware of the instances registered in each AZ and their health status. It is a critical function of a reliable cross zone load balancer. The cross zone load balancer ensures that traffic continues to flow without interruption. The ability to automatically adapt to AZ failures is a significant advantage of using an ALB for cross zone load balancing. The cross zone load balancer provides not only high availability but also simplifies the management of complex multi-AZ deployments. Application Load Balancers are key to any architecture that requires a robust and fault-tolerant cross zone load balancer solution.
Optimizing Traffic Distribution for Performance and Cost
Achieving an optimal balance between performance and cost when distributing traffic across Availability Zones (AZs) requires careful consideration of various factors. Strategies must be implemented to minimize expenses while maintaining acceptable levels of application responsiveness and availability. One of the primary considerations is cross-AZ data transfer costs, which can significantly impact the overall cost of running a multi-AZ architecture. By strategically routing traffic and leveraging caching mechanisms, these costs can be effectively reduced. Selecting the appropriate load balancing algorithm is also crucial. Algorithms like round-robin, least connections, or weighted distribution can influence how traffic is distributed across AZs, directly impacting performance and cost. Understanding the specific traffic patterns of your application is vital for choosing the most suitable algorithm. For example, if one AZ consistently handles more requests, a weighted distribution approach might be more efficient. A well-configured cross zone load balancer is the first line of defense, as it distributes requests efficiently.
Caching mechanisms play a significant role in reducing latency and minimizing cross-AZ data transfer. By caching frequently accessed data closer to the users or the application servers, the need to retrieve data from remote AZs can be reduced. This minimizes latency and lowers data transfer costs. The choice of caching strategy depends on the application’s specific needs and traffic patterns. Consider implementing a content delivery network (CDN) to cache static content and reduce the load on the application servers. Furthermore, optimizing network configurations can significantly improve performance. This includes using optimized network protocols, configuring appropriate network bandwidth, and minimizing network hops. The goal is to reduce latency and improve the overall efficiency of traffic distribution. Employing a cross zone load balancer helps in intelligently directing traffic and caching data.
Different traffic patterns can significantly impact the cost of running a multi-AZ architecture. For example, applications with a high volume of cross-AZ traffic will incur higher data transfer costs. Understanding these patterns is essential for optimizing traffic distribution and minimizing costs. Analyzing traffic patterns involves monitoring key metrics, such as the volume of traffic between AZs, the latency of cross-AZ communication, and the utilization of resources in each AZ. Based on this analysis, adjustments can be made to the load balancing configuration, caching strategy, and network configuration to achieve the desired balance between performance and cost. A carefully configured cross zone load balancer along with vigilant monitoring allows for rapid correction. Regular monitoring and analysis of traffic patterns are essential for identifying and addressing potential cost inefficiencies. This involves continuously evaluating the effectiveness of the current configuration and making adjustments as needed to optimize performance and cost.
Troubleshooting Common Issues with Zone-Aware Traffic Routing
Implementing traffic distribution across Availability Zones (AZs) can introduce complexities that require careful troubleshooting. One common issue involves misconfigured health checks. If health checks are not properly configured, instances may be incorrectly marked as unhealthy, leading to traffic being routed away from perfectly functional servers. This can result in unnecessary failovers and performance degradation. Ensure health checks accurately reflect the health of the application by verifying that they are targeting the correct endpoints and using appropriate response timeouts. A properly configured cross zone load balancer relies on accurate health checks.
Network connectivity problems also frequently plague multi-AZ deployments. Firewalls, security groups, or network ACLs might inadvertently block traffic between AZs, preventing instances from communicating with each other or with the cross zone load balancer. This can manifest as intermittent failures or complete unavailability of the application. Carefully review network configurations to ensure that traffic is allowed between all relevant AZs and that there are no restrictive rules that could be interfering with communication. Regularly test network connectivity between AZs to proactively identify and address any issues. Another potential bottleneck comes from capacity constraints. If one AZ becomes overloaded, the cross zone load balancer may attempt to shift traffic to other AZs, potentially overwhelming them as well. Monitor resource utilization in each AZ and ensure that sufficient capacity is provisioned to handle failover scenarios. Autoscaling groups can automatically scale instances in response to increased traffic, preventing overloads.
Furthermore, DNS resolution issues can disrupt traffic routing across AZs. Incorrect DNS records or propagation delays can cause traffic to be directed to the wrong instances or AZs. Verify that DNS records are correctly configured and that DNS propagation is complete before directing traffic to the cross zone load balancer. Caching issues can also lead to stale DNS information, so consider reducing DNS TTL values to minimize the impact of propagation delays. When troubleshooting, start by examining the logs of the cross zone load balancer and application instances. Look for error messages or anomalies that could indicate the root cause of the problem. Utilize monitoring tools to track key metrics such as latency, error rates, and resource utilization. By proactively monitoring and addressing these common issues, you can ensure the resilience and availability of your multi-AZ application. Identifying and mitigating potential failure points before they impact users is critical for maintaining a reliable and performant system.
Evaluating the Impact of Cross-Zone Load Balancing on Application Latency
Cross-Availability Zone (AZ) traffic can impact application latency, primarily due to increased network latency. Understanding the factors contributing to this latency is crucial for optimizing application performance. Distance between AZs plays a significant role; geographically dispersed AZs naturally introduce higher latency compared to closer ones. Network congestion within and between AZs is another critical factor. During peak hours or due to network issues, congestion can increase latency significantly. The performance overhead from a cross zone load balancer itself adds a degree of latency too.
Several strategies can minimize latency in cross-AZ deployments. Optimized network configurations are essential. Using high-bandwidth, low-latency network connections between AZs helps reduce the impact of distance. Minimizing cross-AZ data transfer is also critical. Design applications to keep data processing within the same AZ whenever possible. Implement caching mechanisms to reduce the need for frequent cross-AZ data retrieval. Content Delivery Networks (CDNs) can cache static content closer to users, reducing latency. Another important consideration is selecting appropriate instance types with sufficient network performance capabilities. Properly configured cross zone load balancer settings will contribute to the better latency results.
The choice of load balancing algorithm also affects latency. Algorithms like round-robin distribute traffic evenly, but might not consider the proximity of users to specific AZs. Algorithms that prioritize instances in the same AZ as the user can reduce latency. Monitoring network performance and application latency is crucial. Use monitoring tools to identify bottlenecks and areas for improvement. Regular performance testing under different traffic conditions helps identify and address potential latency issues. By understanding and addressing the factors that contribute to latency, you can optimize application performance in multi-AZ environments. The cross zone load balancer then becomes a tool that provides reliability without sacrificing speed, and ensuring a positive user experience. Therefore, organizations can build robust, high-performing applications using a well-architected cross zone load balancer.
Securing Cross-AZ Traffic: Best Practices for Network Security
Distributing traffic across Availability Zones (AZs) enhances application resilience, but it also introduces unique security considerations. Securing cross-AZ traffic is crucial to prevent unauthorized access and maintain data integrity. A robust security strategy should encompass network segmentation, access control, and data protection measures. Implementing a cross zone load balancer is a key strategy for efficiently manage the security across multiple AZs.
Network segmentation is fundamental to securing cross-AZ communication. Security Groups and Network Access Control Lists (ACLs) act as virtual firewalls, controlling inbound and outbound traffic at the instance and subnet levels. Security Groups operate at the instance level, filtering traffic based on rules that define allowed protocols and ports. NACLs, on the other hand, function at the subnet level, providing a broader level of control over network traffic. These controls should be configured to allow only necessary communication between AZs. For instance, instances in one AZ might need to communicate with a database in another AZ. In this case, the Security Groups and NACLs should be configured to permit traffic only on the specific port used by the database. Implementing a cross zone load balancer adds an extra layer of security. Using a cross zone load balancer centralizes and simplifies the process. The cross zone load balancer can be configured to manage the traffic in a secure way.
Encryption and authentication are paramount for protecting data transmitted across AZs. Encryption ensures that data is unreadable if intercepted, while authentication verifies the identity of communicating entities. Transport Layer Security (TLS) should be implemented to encrypt traffic between instances and load balancers. Mutual TLS (mTLS) provides an even stronger level of security by requiring both the client and server to authenticate each other. Additionally, consider using Virtual Private Cloud (VPC) peering with encrypted transit to secure communication between VPCs in different AZs. Regularly auditing security configurations and access logs is crucial for identifying and addressing potential vulnerabilities. Employing intrusion detection and prevention systems (IDS/IPS) can further enhance security by detecting and blocking malicious traffic. Properly configured, a cross zone load balancer acts as a first line of defense. This proactive approach helps to maintain a secure and resilient multi-AZ environment. Furthermore, a Web Application Firewall (WAF) can be integrated with a cross zone load balancer to protect applications from common web exploits.