Demystifying AWS Security Posture: A Comprehensive Guide
The cloud landscape demands a strong understanding of security and compliance, especially within Amazon Web Services (AWS). Compliance refers to adhering to industry regulations and standards. Security involves protecting data and systems from unauthorized access. Governance establishes the framework for managing and controlling IT resources. These three elements are interconnected and crucial for maintaining a secure and compliant AWS environment. The shared responsibility model is a cornerstone of AWS security. AWS secures the underlying infrastructure, while users are responsible for securing what they put in the cloud. This includes data, applications, and operating systems. Proactively managing your “security posture” is vital for achieving and maintaining aws compliance. It’s not a one-time effort but a continuous process of assessment, remediation, and monitoring.
A strong security posture involves implementing security controls. These controls must align with relevant compliance frameworks. Examples include HIPAA for healthcare data and PCI DSS for payment card information. GDPR governs the privacy of European Union citizens’ data. Understanding these frameworks is the first step toward aws compliance. Organizations must identify the specific security controls required by each framework. These controls must then be implemented within the AWS environment. Tools like AWS Config and AWS Security Hub can help automate this process. A gap analysis helps identify areas where current security measures fall short of compliance requirements. Addressing these gaps is crucial for achieving a robust security posture and achieving aws compliance.
Successfully managing your security posture ensures aws compliance. This provides confidence to stakeholders and customers. Neglecting security posture can lead to data breaches and regulatory fines. It’s an investment that pays off in the long run by reducing risk. Moreover, it helps build trust with customers and partners. Demonstrating a strong commitment to aws compliance can be a competitive advantage. It shows that the organization takes security and data protection seriously. Regularly reviewing and updating security posture is essential. New threats emerge constantly, and compliance requirements evolve. By staying proactive and vigilant, organizations can ensure that their AWS environments remain secure and compliant.
How to Achieve AWS Compliance: A Step-by-Step Approach
Achieving aws compliance within the AWS environment requires a structured and methodical approach. The initial step involves gaining a thorough understanding of the relevant compliance frameworks that apply to your organization. These frameworks might include HIPAA for healthcare data, PCI DSS for credit card information, GDPR for data privacy of European Union citizens, or other industry-specific regulations. A comprehensive understanding of these frameworks is crucial for identifying the specific security controls that must be implemented. Neglecting this initial assessment can lead to significant gaps in your aws compliance posture.
Once the relevant frameworks are identified, the next step involves performing a detailed gap analysis. This analysis compares your current security posture against the requirements of the chosen compliance frameworks. It pinpoints areas where your existing security controls fall short and highlights the specific actions needed to bridge those gaps. A well-executed gap analysis provides a clear roadmap for achieving aws compliance. Following the gap analysis, the focus shifts to implementing the necessary security controls within your AWS environment. This involves configuring AWS services, implementing security policies, and deploying security tools to address the identified gaps. Ensure that each implemented control is properly documented and tested to verify its effectiveness. Proper documentation is key for demonstrating aws compliance to auditors.
The implementation phase also requires careful consideration of the AWS Shared Responsibility Model. AWS is responsible for the security of the cloud, while you are responsible for the security in the cloud. This means that while AWS provides a secure infrastructure, it is your responsibility to configure and manage your resources securely. Failure to understand and adhere to this model can significantly compromise your aws compliance efforts. Regularly review and update your security controls to ensure they remain effective in the face of evolving threats and changing compliance requirements. Staying proactive and informed is essential for maintaining a strong aws compliance posture and safeguarding your data in the cloud. Neglecting continuous monitoring can leave your environment exposed and non-compliant.
Leveraging AWS Services for Automated Regulatory Adherence
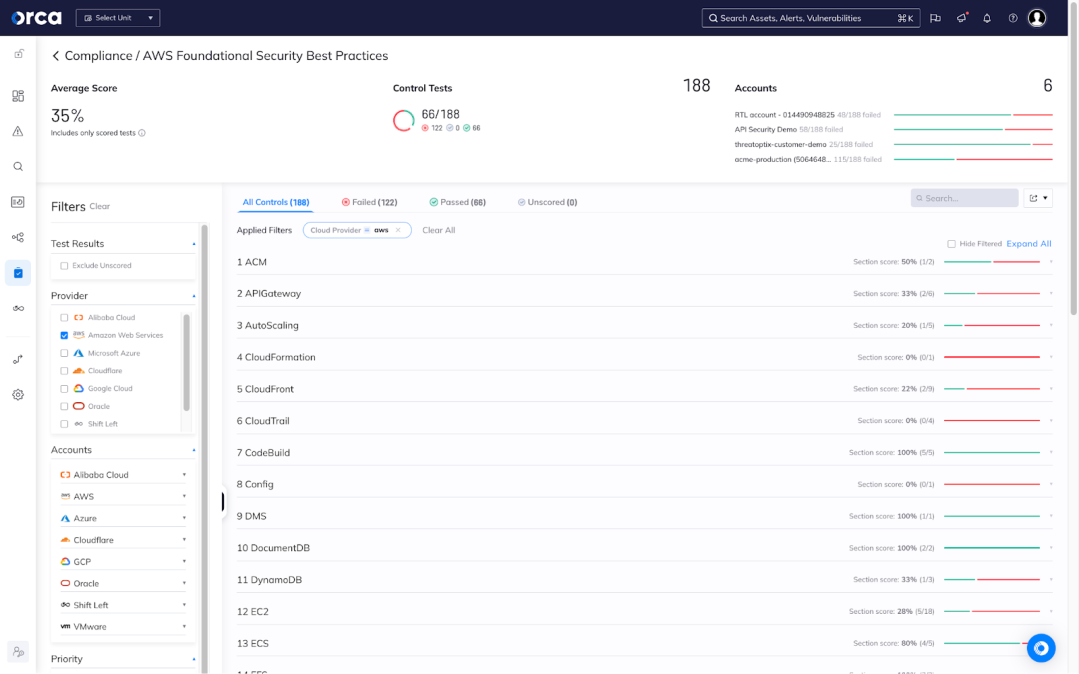
AWS offers a suite of powerful services designed to streamline and automate regulatory adherence, significantly reducing the manual effort involved in achieving and maintaining aws compliance. These services provide visibility into your security posture, automate assessments, and generate audit-ready reports. By strategically leveraging these tools, organizations can enhance their aws compliance and security while optimizing operational efficiency.
AWS Config is a key service for monitoring the configuration of your AWS resources. It enables you to track changes, detect deviations from desired configurations, and assess aws compliance against internal policies and regulatory standards. AWS CloudTrail records API calls made within your AWS account, providing an audit trail of user activity and resource modifications. This information is invaluable for security investigations, compliance audits, and operational troubleshooting. AWS Security Hub offers a centralized view of your security alerts and compliance status across multiple AWS accounts and regions. It aggregates findings from various AWS security services, such as AWS Inspector and Amazon GuardDuty, and provides actionable recommendations for improving your security posture and aws compliance. AWS Inspector automates vulnerability assessments of your applications and infrastructure. It identifies potential security vulnerabilities and provides detailed reports with remediation guidance, helping you proactively address security risks and meet aws compliance requirements.
AWS Audit Manager helps automate the process of collecting evidence and preparing for audits. It provides prebuilt frameworks for various compliance standards, such as HIPAA, PCI DSS, and GDPR, and automatically collects evidence from AWS services to demonstrate compliance. For example, to comply with HIPAA, you can use AWS Audit Manager to automatically gather evidence related to access controls, encryption, and audit logging. This drastically reduces the time and effort required to prepare for HIPAA audits and maintain aws compliance. Consider a scenario where you need to demonstrate PCI DSS compliance. You can use AWS Config to ensure that all your EC2 instances have the required security patches installed, AWS CloudTrail to track all API calls related to payment card data, and AWS Security Hub to monitor for potential security threats. By automating these tasks with AWS services, you can significantly simplify the process of achieving and maintaining aws compliance.
Building a Robust Compliance Framework for Your AWS Infrastructure
A well-defined compliance framework is crucial for navigating the complexities of AWS compliance and ensuring continuous security. This framework acts as the foundation upon which your organization builds its security posture, ensuring alignment with industry best practices and relevant compliance standards. It is essential for organizations seeking to achieve and maintain aws compliance within their AWS infrastructure. The key components of a robust compliance framework encompass policies, procedures, and controls, each playing a vital role in mitigating risks and maintaining a secure environment. The lack of a compliance framework makes aws compliance very hard to achieve.
Policies provide a high-level overview of your organization’s commitment to security and compliance. They define the rules and guidelines that govern how data is handled, accessed, and protected within your AWS environment. Procedures outline the specific steps and processes that employees must follow to adhere to these policies. This includes procedures for incident response, data encryption, and access control. Controls are the technical and administrative safeguards implemented to enforce policies and procedures. Examples include access controls, encryption, monitoring, and logging. These components should be aligned with industry best practices, such as the NIST Cybersecurity Framework or the CIS Controls, and tailored to the specific requirements of relevant compliance standards like HIPAA, PCI DSS, or GDPR. Selecting a framework is an important step to achieve aws compliance.
Documentation is paramount. Maintaining thorough records of your policies, procedures, and controls is essential for demonstrating compliance to auditors and stakeholders. Documentation should be readily accessible, regularly reviewed, and updated to reflect changes in your AWS environment or compliance requirements. Continuous monitoring is equally important. Implementing monitoring tools and processes allows you to track the effectiveness of your controls, identify potential security gaps, and respond promptly to security incidents. Regularly reviewing logs, conducting vulnerability scans, and performing penetration testing are all critical aspects of continuous monitoring. By investing in a well-defined compliance framework, organizations can streamline their aws compliance efforts, reduce the risk of security breaches, and maintain a strong security posture in the cloud. Proactive monitoring, well-defined policies, and strong documentation make aws compliance easier to achieve and maintain.
Selecting the Right Security Tools for AWS Compliance: A Practical Guide
Choosing the appropriate security tools is critical for achieving and maintaining aws compliance within your AWS environment. This section offers a practical guide to navigating the vast landscape of security solutions. Organizations must carefully evaluate their specific compliance requirements (HIPAA, PCI DSS, GDPR, etc.) and select tools that directly address those needs. Consider the different categories of security tools available. Vulnerability scanners identify weaknesses in your systems and applications. Intrusion detection systems (IDS) monitor network traffic for malicious activity. Data loss prevention (DLP) solutions prevent sensitive data from leaving your control. Security information and event management (SIEM) systems centralize security logs and provide real-time analysis.
When evaluating security tools for aws compliance, assess their capabilities in several key areas. First, ensure the tool offers comprehensive coverage of the AWS services you are using. Second, look for tools that provide automated compliance checks and reporting. This can significantly reduce the manual effort required to demonstrate compliance. Third, consider the tool’s integration capabilities with other security solutions. A well-integrated security ecosystem provides a more holistic view of your security posture. Fourth, evaluate the tool’s ease of use and the level of expertise required to operate it effectively. Some organizations may benefit from managed security services that provide expert support and guidance. For aws compliance, some third-party tools offer pre-built integrations and compliance templates to streamline the process. It is important to note that while third-party tools can be incredibly useful, adhering to the shared responsibility model is paramount. AWS secures the underlying infrastructure, while the customer is responsible for securing what they put on top of it.
Selecting the right tools for aws compliance is an ongoing process. As your AWS environment evolves and new compliance requirements emerge, you may need to re-evaluate your security toolset. Regularly assess the effectiveness of your existing tools and identify any gaps in your security coverage. Stay informed about the latest security threats and vulnerabilities and choose tools that can protect against them. Remember that achieving aws compliance is not just about implementing security tools. It also requires establishing strong security policies, procedures, and controls. By combining the right security tools with a robust compliance framework, organizations can confidently navigate the complexities of cloud security and regulatory adherence. Effective monitoring and continuous improvement are essential components of a successful aws compliance strategy.
Monitoring and Maintaining AWS Compliance: Ensuring Continuous Security
Continuous monitoring and maintenance are vital for sustained aws compliance. Establishing monitoring dashboards allows for a clear, real-time view of your security posture. Configure alerts to promptly notify you of deviations from established security policies. This proactive approach enables immediate responses to potential threats and vulnerabilities, strengthening your overall aws compliance. Tracking key security metrics provides data-driven insights into the effectiveness of your security controls. Regular security assessments are also an indispensable part of maintaining aws compliance. These assessments, coupled with vulnerability scans and penetration testing, identify weaknesses in your system that could be exploited. The findings of these tests inform remediation efforts, ensuring that your environment remains secure and compliant. A proactive security strategy is paramount. It goes beyond simply reacting to incidents; it involves anticipating potential threats and taking preventive measures. This includes staying informed about the latest security best practices and proactively addressing emerging vulnerabilities.
To effectively monitor and maintain aws compliance, several steps should be considered. First, implement automated monitoring tools to track configurations and detect deviations from established baselines. AWS Config, for example, allows you to continuously monitor and record AWS resource configurations. Second, create and maintain comprehensive documentation of your security controls and compliance procedures. This documentation is essential for audits and demonstrates your commitment to aws compliance. Third, conduct regular security awareness training for your employees. Human error is a significant source of security breaches, so educating your team about security best practices can significantly reduce your risk exposure. Fourth, establish a formal incident response plan. This plan should outline the steps to be taken in the event of a security incident, including containment, eradication, and recovery procedures. Regular testing of your incident response plan will ensure its effectiveness. Finally, ensure that your security controls are aligned with your specific compliance requirements. Different compliance frameworks have different requirements, so it is important to tailor your security controls accordingly.
Maintaining aws compliance is an ongoing process that requires continuous effort and attention. By implementing a robust monitoring and maintenance program, you can ensure that your AWS environment remains secure and compliant. This, in turn, builds trust with your customers and stakeholders, and helps you avoid costly penalties and reputational damage. The investment in continuous monitoring and maintenance is an investment in the long-term security and stability of your business. It’s also a way to ensure the ongoing effectiveness of your aws compliance efforts. Embrace the opportunity to strengthen your security posture, improve your operational efficiency, and achieve lasting aws compliance.
Addressing Common AWS Security and Compliance Challenges
Organizations frequently encounter various obstacles when striving to achieve and maintain aws compliance on Amazon Web Services (AWS). A prevalent challenge is a lack of in-house expertise. AWS environments can be intricate, and navigating the complexities of security configurations and compliance requirements necessitates specialized knowledge. Many organizations find it difficult to recruit or train personnel with the required skills in aws compliance, leading to misconfigurations and potential security vulnerabilities. To solve it, organizations should consider investing in training programs or seeking assistance from AWS partners with expertise in security and compliance.
Complex configurations pose another significant hurdle to aws compliance. AWS offers a wide array of services and configuration options, making it challenging to properly configure and secure all resources. Insufficient documentation exacerbates this issue. Without clear and comprehensive documentation of security policies, procedures, and configurations, it becomes difficult to demonstrate aws compliance to auditors and maintain a consistent security posture. Organizations should prioritize creating detailed documentation of their AWS environment, security controls, and compliance processes. This documentation should be regularly reviewed and updated to reflect changes in the environment or compliance requirements. Automation tools, such as AWS Config, can help automate the documentation process.
Keeping pace with evolving compliance requirements presents a continuous challenge. Compliance regulations are constantly evolving, and organizations must stay informed of these changes and adapt their security controls accordingly to achieve aws compliance. This requires ongoing monitoring of regulatory updates and a proactive approach to security management. Another issue is difficulty in ensuring consistent security across multiple AWS accounts and regions. Organizations often operate in multiple AWS environments for various reasons, such as disaster recovery or geographical proximity to customers. Maintaining consistent security policies and controls across all of these environments can be complex. Centralized management tools, like AWS Organizations and AWS Security Hub, can help organizations manage security and compliance across multiple AWS accounts and regions.
Future-Proofing Your AWS Environment: Adapting to Evolving Regulations
The digital landscape is in constant flux, with regulations and security threats evolving at an accelerated pace. Future-proofing your AWS environment is not merely a best practice; it’s a necessity for sustained success. This involves embracing a proactive approach to security and compliance, ensuring your infrastructure remains resilient and adaptable in the face of change. Maintaining AWS compliance requires constant vigilance.
One crucial aspect of future-proofing is continuous learning and adaptation. Stay informed about the latest industry best practices, regulatory updates, and emerging security threats. Regularly review and update your security policies, procedures, and controls to align with these changes. Embrace automation to streamline compliance processes and reduce the risk of human error. Leverage AWS services like AWS Config and AWS Security Hub to continuously monitor your environment and identify potential compliance gaps. These tools offer automation capabilities for managing aws compliance, giving time to focus on other important tasks. Consider implementing a robust change management process to ensure that any modifications to your AWS environment are properly assessed for their potential impact on security and compliance. Actively participate in industry forums and communities to share knowledge and learn from the experiences of others. This collaborative approach can provide valuable insights and help you stay ahead of the curve. Regularly conduct risk assessments to identify potential vulnerabilities and prioritize remediation efforts.
Investing in AWS compliance is an investment in the long-term health and stability of your organization. By proactively adapting to evolving regulations and security threats, you can minimize risk, maintain customer trust, and gain a competitive advantage. Remember that achieving and maintaining AWS compliance is an ongoing journey, not a destination. Embrace a culture of continuous improvement and foster a collaborative environment where security and compliance are everyone’s responsibility. By prioritizing security and compliance, your organization can confidently navigate the ever-changing digital landscape and achieve lasting success on AWS. Organizations should make aws compliance a priority to avoid any legal or financial issues.