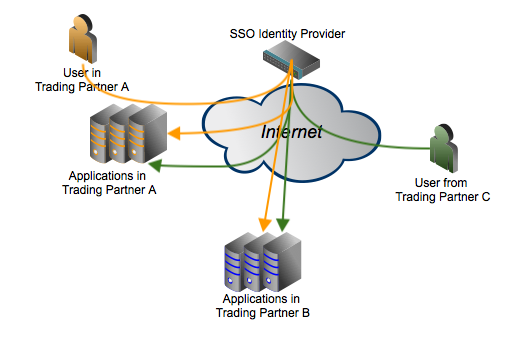
Understanding the Core Functionality of Single Sign-On Solutions
In today’s interconnected digital landscape, managing multiple application logins can be a significant challenge. Single sign-on solutions offer a streamlined approach. They allow users to access various applications using one set of credentials. This eliminates the need to remember numerous usernames and passwords. The concept of simplified access is crucial for modern IT environments. It enhances the user experience. Administrators benefit as well. They gain improved control over user access and security. This unified approach reduces the risk of compromised accounts. The core of a single sign-on system, or ssogen, is the authentication process. This verifies user identity one time. Once authenticated, users can access multiple resources. This happens seamlessly, without repeated logins. A robust ssogen solution simplifies the digital workflow. It provides a more secure and efficient user experience. For an organization, this translates to less time wasted on login issues. It also increases overall productivity. Adopting a single sign-on approach is essential for a streamlined IT infrastructure. It is a critical component for secure access management.
The benefits of implementing single sign-on solutions extend beyond user convenience. Security is a primary advantage. By reducing password fatigue, it minimizes weak password choices. It also minimizes the use of the same passwords across multiple accounts. This, in turn, decreases the risk of security breaches. With a ssogen system in place, IT teams have better oversight of access privileges. Centralized management simplifies the application of security policies. This helps to maintain compliance. Furthermore, such systems streamline user onboarding and offboarding processes. When a new employee joins the organization, they get immediate access to required resources. When an employee departs, access is revoked quickly and efficiently. The single sign-on approach is a cornerstone for improving overall security. It also enhances user and administrator productivity alike.
How to Implement a Single Sign-On System Effectively
Implementing a single sign-on (SSO) system requires careful planning and execution. Begin by assessing your organization’s specific needs. Identify all applications that should be included in the SSO environment. A crucial step involves choosing the right authentication protocol. SAML, OAuth2, and OpenID Connect are common choices. Each has its strengths and weaknesses. Select one that best suits your security requirements. Infrastructure is another key consideration. Ensure you have adequate server capacity. This will handle the authentication traffic. Also consider the storage for user directories. The chosen SSO solution should integrate with your current user directory. Consider options like Active Directory or LDAP. These can help centralize user management. Planning is essential to ensure a smooth implementation. A well thought out ssogen deployment will be much easier.
Next, think about user onboarding. How will users be added to the system? What procedures will be in place for offboarding? Detailed processes are necessary for security. These will also ensure compliance. When choosing an SSO solution, consider ease of use. The solution should be intuitive for both users and administrators. Start with a pilot program. Deploy it to a small group of users. Collect their feedback. Adjust your configurations based on that. Phased rollouts are often best to minimize disruption. Proper planning is critical for success. Also train your staff on how to manage the new system. This will help them better support users. Regular reviews of the system’s performance will make sure that everything is running smoothly. This includes monitoring for any security issues. A well managed ssogen setup reduces potential risks. Take time to address those in the implementation phase.
Consider the long term implications as well. How will the system scale as your organization grows? Will it be able to adapt to changing requirements? The ssogen you choose should be flexible and scalable. Test your chosen solution thoroughly before a full deployment. This should include various scenarios. For example, test different login methods. Verify user access rights. A thorough testing strategy ensures stability. Think about ongoing maintenance. Have a process for system updates and patches. A strong security posture is also important. Regular security audits help identify potential weaknesses. These can also prevent possible attacks. Prioritizing these steps, will help create an effective implementation. Proper implementation ensures a more secure and user-friendly environment.
Exploring Leading Single Sign-On Providers: Okta vs. Auth0
When evaluating single sign-on solutions, organizations often consider Okta and Auth0, two prominent players in the market. Both offer robust features, yet they cater to different needs and preferences. Okta is often seen as a comprehensive identity and access management platform, providing a wide array of functionalities beyond just single sign-on. It includes features like lifecycle management, advanced security policies, and extensive integration capabilities with various applications and services. This makes it a strong contender for larger enterprises needing an all-in-one solution. Okta’s pricing model can be more complex and may be better suited for organizations with larger budgets and complex requirements. It provides a very robust and secure infrastructure, which can be beneficial for companies with high security standards. This platform is a versatile ssogen, offering diverse deployment options.
Auth0, on the other hand, is known for its developer-centric approach and ease of integration. It provides a highly flexible and customizable solution that is well-suited for organizations that require granular control over the authentication process. Auth0 excels in supporting complex authentication scenarios, offering a wide range of authentication protocols and integration methods. It has a more straightforward and potentially cost-effective pricing structure, making it a viable option for smaller to medium-sized businesses, as well as startups. Furthermore, Auth0 stands out in its ability to handle various types of applications from web to mobile. Auth0’s flexible approach makes it a strong ssogen contender for agile development teams. Choosing between the two hinges on understanding the scale of implementation, the complexity of the required authentication processes, and the organization’s overall budget. A thorough analysis is crucial.
Ultimately, the choice between Okta and Auth0 depends on an organization’s specific needs and technical capabilities. Okta presents a broad and robust platform, while Auth0 offers a more flexible and developer-friendly environment, where custom ssogen solutions can be built with ease. Both are market leaders, and this comparison helps to make the best decision for any organization. It’s important to conduct a trial or demo of both platforms to gain hands-on experience and assess their suitability for your unique environment.
Key Benefits of Using a Single Sign-On System
Adopting a single sign-on (ssogen) approach offers numerous advantages for both users and organizations. For users, the most immediate benefit is a streamlined experience. They can access multiple applications with a single set of credentials. This eliminates the need to remember numerous usernames and passwords. This significantly reduces password fatigue. It also decreases the likelihood of password-related security breaches. Users experience a more fluid and efficient workflow. They can navigate different systems without interruption. This enhanced convenience translates to improved user satisfaction and adoption rates of company applications. This streamlined access improves overall efficiency and reduces the time spent on managing credentials.
From an organizational standpoint, the advantages of a single sign-on system are equally compelling. Implementing ssogen enhances security by centralizing access management. This makes it easier to enforce strong password policies. It also simplifies the process of revoking access when necessary. The reduced number of passwords decreases the risk of compromised credentials. This safeguards sensitive organizational data. Furthermore, ssogen boosts productivity by minimizing time spent on password-related issues. Staff spend less time locked out of accounts, increasing their working hours. Centralized management also translates to streamlined administrative processes. There is less time spent on help desk requests. The advantages for organizations are both security and cost efficiency.
Beyond the immediate gains in security and productivity, a ssogen implementation can also enhance compliance efforts. By providing centralized control over user access, organizations can more easily comply with security regulations and industry best practices. Reporting and auditing are also simplified, offering more comprehensive insights into user access and activity. Therefore, using a single sign-on system is beneficial for many aspects of the company. It is an investment in user experience, overall productivity, and robust security. This provides a strong foundation for long-term operational effectiveness.
Best Practices for Managing a Single Sign-On Environment
Effective management of a single sign-on (SSO) environment is essential for its long-term success and stability. User onboarding and offboarding procedures should be clearly defined and consistently followed. When new users join the organization, their access to the ssogen system should be promptly granted, based on their roles and responsibilities. Similarly, when employees leave, their access must be immediately revoked to prevent any unauthorized usage. Automated workflows can significantly streamline these processes. Regular security audits and monitoring are also critical. These practices help identify potential vulnerabilities and detect any suspicious activity. Logs should be thoroughly reviewed for any irregularities. Having clear guidelines for responding to security incidents helps reduce the risk. A comprehensive disaster recovery plan is required for any unforeseen disruptions. It’s important to have backup systems and procedures to ensure continuous access to the ssogen environment. Consider how to recover quickly from any system failure, or security compromise. These contingency plans are vital for business continuity.
Furthermore, compliance with relevant regulations is paramount. Many industries have stringent requirements regarding data protection and user privacy. These rules must be understood, and integrated into the ssogen setup and management practices. Regular compliance checks should be conducted. These checks ensure ongoing adherence to applicable laws and standards. Additionally, consider periodic training to users regarding security awareness and best practices for using the ssogen portal. A well-trained user base contributes significantly to overall security posture. Ensure that any changes to the system or its configurations are thoroughly tested in a staging environment before being implemented. This limits the potential of introducing unforeseen issues. It allows any changes to be validated before they affect the production system. Finally, maintain regular system updates and upgrades to protect against new vulnerabilities. Stay current with the latest security patches. This ensures that the implemented ssogen remains effective and reliable over time. Proper and meticulous management is key for a secure and well-functioning SSO solution.
Troubleshooting Common Issues with Single Sign-On Implementations
Single sign-on (SSO) implementations, while beneficial, can sometimes present challenges. Authentication errors are a common hurdle. These often stem from misconfigurations in the identity provider or the application. Carefully reviewing the configuration settings is essential for resolution. Another frequent issue involves integration conflicts between different applications. When various systems interact, compatibility problems can arise. Ensure that all applications are configured to communicate correctly with the ssogen. This may involve checking protocol compatibility or API endpoints. Access issues can also occur, preventing users from logging in. Verifying user permissions and group memberships in the directory should be the first step.
To effectively troubleshoot these problems, a systematic approach is helpful. Start by examining the logs of the SSO system and the integrated applications. These logs often provide specific error messages. They can guide the troubleshooting process. Use network analysis tools to ensure smooth communication. Check for any firewall restrictions that may be blocking connections. When making changes, perform thorough testing. This will help prevent new problems from arising. For example, when making a change to the ssogen configuration, test it thoroughly in a development environment before putting it into production. If you encounter issues, revert your changes. Review each step with attention to detail. Thorough testing will help ensure a seamless SSO implementation.
User-related issues often involve incorrect credentials or misconfigured browser settings. Encourage users to double-check their username and password. Furthermore, clear the browser cache and cookies. When users still face challenges, investigate account lockouts and password policies. Make sure the system complies with defined rules. Remember that ssogen should be designed with security in mind. It also needs to be user-friendly. Effective troubleshooting requires understanding both the system and the user’s experience. By following these practical steps, many of the common ssogen issues can be resolved efficiently. Ultimately, this provides a more robust and reliable environment.
The Future of Single Sign-On and Identity Management
The landscape of single sign-on and identity management is continuously evolving. The move towards passwordless authentication is gaining significant traction. This includes methods such as biometric identification (fingerprint, facial recognition). These advancements aim to enhance security and improve user experience. These changes will redefine how users interact with applications. The traditional password-centric approach will be progressively phased out. Expect to see a greater emphasis on risk-based authentication. This will involve analyzing user behavior and device context to determine access. This ensures a more secure environment by adapting to the level of risk detected during login attempts. These innovations will likely reduce security threats and improve user experiences. The integration of machine learning and artificial intelligence will improve threat detection. Such improvements will enhance security measures. Furthermore, expect to see greater adoption of decentralized identity solutions. This technology aims to give users more control over their digital identities. The future of identity management is centered on user-centric security models. This will simplify digital interactions while maintaining the highest levels of protection. The evolution of ssogen tools is leading us to a more secure digital landscape.
Emerging trends show a move towards enhanced interoperability between different ssogen solutions. The current identity management systems will adapt to multi-cloud environments. The goal is to create a unified user experience that is agnostic of the underlying technology. This transition requires tools and technologies to easily interact with different platforms. This makes identity access more seamless and user-friendly across different systems. The future will also see more integrated ssogen experiences. Expect identity management to be embedded more directly into applications and operating systems. This should make managing access permissions an organic part of the user journey. This evolution will shift the focus from just logging in to a more integrated secure identity model. This approach will ensure that security is a proactive, not reactive, part of the experience. There will also be more robust APIs and developer tools. This will empower organizations to integrate sophisticated authentication methods more easily. The future of single sign-on is a more dynamic and user-centric approach that strengthens overall security. Expect it to be highly adaptable to different security needs. The future ssogen solutions will provide a more frictionless and secure experience.
Selecting the Right Single Sign-On Generator for Your Organization
Choosing the appropriate single sign-on (SSO) solution requires careful consideration of various factors. Organizations must assess their specific needs before making a selection. The size of the company plays a crucial role. Larger enterprises may require more robust and scalable ssogen options. Smaller organizations might find simpler, more cost-effective solutions suitable. Evaluate your existing infrastructure. Consider compatibility with your current systems and applications. The chosen ssogen should integrate smoothly. This ensures a streamlined implementation process. Think about the complexity of your user base. Consider the level of technical expertise among your users. An easy-to-use interface can increase user adoption. It can also reduce the burden on your IT support team.
Security requirements should be a paramount concern. Look for solutions that offer strong authentication protocols. This might include multi-factor authentication and encryption. Compliance with industry regulations is essential. This is particularly true for organizations handling sensitive data. Evaluate different ssogen vendors. Compare features, pricing, and support services. It is vital to select a provider that meets your budget. It should also be able to provide ongoing support. Take advantage of free trials or demos. This allows you to test the solution in your environment. Consider the type of applications that need SSO access. Some systems might have specific integration requirements. Ensure the ssogen supports these necessary connections. Think about the long-term scalability of the solution. Will it be able to handle your projected growth and usage demands? Choosing a flexible system is important for sustainable use.
The process of selecting the right ssogen involves a deep understanding of internal requirements. Define your goals and desired outcomes before making a decision. The right system will improve security, streamline user access, and increase productivity. Evaluate the capabilities of the potential SSO solution. Select an ssogen that aligns with your business needs. Consider future trends. Choose a system that can adapt to industry changes. Select the ssogen after thoughtful analysis and planning. Evaluate user feedback and support resources. This comprehensive approach ensures success. It also will provide long-term value for your organization. Remember the key is alignment and functionality to be successful in the long run.