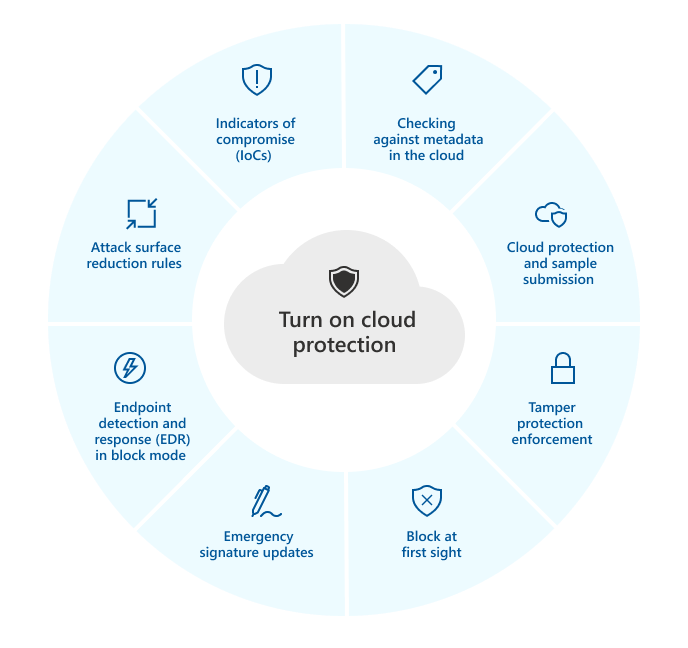
Understanding Microsoft’s Security Offering for Cloud Environments
The digital landscape is rapidly shifting, with more businesses moving their operations to the cloud. This migration introduces new security challenges that traditional methods often fail to address effectively. Cloud environments, by their nature, are complex and distributed, presenting a wider attack surface. Organizations face sophisticated threats such as data breaches, malware, and unauthorized access, which necessitate a robust and proactive security strategy. Microsoft understands these challenges and offers a comprehensive suite of security products designed to protect cloud resources. While we will delve into the specifics of microsoft cloud defender later, it’s important to recognize the broader context of the company’s security solutions. These tools are engineered to address critical areas like threat detection and prevention, identity and access management, and data protection. Securing the cloud is not just about implementing a single product but adopting a comprehensive, multi-layered approach that considers the entire ecosystem. This strategy is crucial for ensuring the confidentiality, integrity, and availability of sensitive data.
A truly effective cloud security strategy involves proactive measures rather than reactive responses. It’s about anticipating potential threats and having systems in place to mitigate them before they can cause harm. Microsoft’s security offerings include advanced threat intelligence capabilities that constantly monitor the threat landscape and identify emerging risks. These solutions are designed to learn and adapt, enhancing the overall security posture of an organization. The core objective is to provide a unified view of security across the cloud environment, allowing security teams to have complete visibility and control over their assets. This approach enables faster incident response and reduces the potential impact of security breaches. Organizations must ensure that they are building security into their cloud operations from the ground up, rather than as an afterthought. This mindset is vital for creating a resilient and secure cloud infrastructure that is adaptable to the evolving security challenges of today’s digital world. The need for a comprehensive solution like Microsoft’s becomes ever more important as threats get more sophisticated.
How to Implement Robust Cloud Protection with Microsoft
Implementing robust cloud protection with Microsoft involves a structured approach. The process begins with understanding your specific cloud environment. This includes whether you utilize SaaS, IaaS, or PaaS models. Microsoft provides flexibility in deploying its security solutions across these different models. A key component of this implementation is adopting Microsoft Cloud Defender. This solution is often part of a broader suite of Microsoft security tools. The initial setup involves configuring the security settings. This ensures the solution aligns with your security policies. Ongoing management is essential for maintaining a robust security posture. This involves regularly reviewing configurations. It also includes updating security policies as needed. The deployment model chosen directly influences the specific implementation steps. For instance, a SaaS environment may require a different approach compared to an IaaS environment.
Configuration is a crucial stage in implementing Microsoft Cloud Defender. This step involves setting up alerts and notifications. The system can be customized to notify your security team of potential threats. It also includes integrating it with other security tools you might be using. Regular updates are paramount. This ensures your cloud security tools are up-to-date with the latest threat intelligence. The ongoing management also entails monitoring security dashboards. This helps track your security posture over time. The flexibility of the solution allows organizations to adapt to changing security needs. This makes microsoft cloud defender an ideal choice for diverse environments. The entire process emphasizes a proactive approach to security. This ensures your cloud resources are protected from various threats. It is about adapting to your individual organizational needs.
The process of implementing Microsoft’s cloud security solution is not a one-time task. Instead, it is an iterative process. It involves continuous learning. It requires adapting to the evolving threat landscape. Organizations must prioritize regular security assessments. They must perform penetration testing to identify vulnerabilities. A strong security posture is achieved through consistent efforts. This involves utilizing Microsoft cloud defender’s full range of capabilities. This proactive approach provides the best overall results. Microsoft Cloud Defender is a crucial part of a layered security strategy. It helps organizations to maintain continuous protection. This protection ensures the security of cloud-based assets over time.
Key Features and Benefits of Microsoft’s Cloud Defense Tools
Microsoft Cloud Defender offers a suite of powerful features designed to bolster cloud security. It leverages advanced threat intelligence to identify known malicious actors and patterns. Anomaly detection capabilities allow the system to learn normal behavior. This enables it to flag deviations that could indicate an active attack. Automated incident response is a crucial element. It allows for quick containment and mitigation of threats. This reduces the potential impact of security incidents. Furthermore, regulatory compliance is streamlined. Cloud Defender provides tools and insights to meet industry-specific requirements. These features collectively contribute to an improved security posture. They also significantly reduce the workload of security teams. The benefits are tangible, providing real-time protection against a variety of cloud-based threats. The platform is engineered to handle the complex security challenges of modern cloud environments.
The practical applications of Microsoft Cloud Defender are numerous. For example, it can help prevent account compromise through continuous monitoring. The platform can detect unusual login attempts and alert security personnel. It can also prevent data exfiltration. If suspicious network activity is detected, access can be blocked automatically. Cloud Defender can also defend against malware uploads into cloud storage. The platform can also scan files in real-time for threats. Moreover, it enhances network security by detecting potential intrusions. It utilizes behavioral analysis to identify unusual traffic patterns. This allows for rapid responses to ongoing attacks. In essence, the platform provides a proactive approach to security. The goal is to prevent problems before they become significant breaches. The flexibility of the platform allows it to adapt to the unique challenges of different businesses.
Microsoft Cloud Defender’s ability to integrate with other Microsoft products allows it to bring unified security. This integrated approach simplifies security management. The result is a comprehensive and more effective security system. Businesses can use the platform to monitor all their cloud resources. This comprehensive visibility allows for better incident detection and response. The automated response and intelligence reduce the response times for incidents. This helps to minimize downtime and financial loss. Microsoft Cloud Defender is more than just security software. It’s a complete defense system designed for the modern business.
Comparing Microsoft’s Security to Other Cloud Protection Platforms
Evaluating cloud security solutions requires a careful look at what different platforms offer. Microsoft Cloud Defender stands out for its deep integration within the Microsoft ecosystem. This seamless compatibility with other Microsoft services can simplify deployment and management for organizations already invested in the platform. When compared to other leading solutions like CrowdStrike Falcon or Palo Alto Networks Prisma Cloud, each has its own approach and strengths. CrowdStrike is often praised for its endpoint detection and response capabilities. Palo Alto Networks offers a broad range of security products and focuses on a platform approach. However, the tight integration of Microsoft’s security tools, including Microsoft Cloud Defender, is often cited as an advantage for businesses that rely heavily on Microsoft Azure, Microsoft 365, and other related services.
While Microsoft Cloud Defender excels in integration, it’s important to acknowledge areas where other platforms might have the upper hand. CrowdStrike’s strength in endpoint security and threat intelligence is noteworthy. Prisma Cloud often receives praise for its advanced cloud workload protection. The choice between these platforms ultimately depends on an organization’s specific security needs and infrastructure. If an organization relies mostly on non-Microsoft technology then the seamless integration might not be such a powerful advantage. Microsoft Cloud Defender provides very strong protection, but it’s not necessarily the best in every single category. Organizations should always consider a full evaluation before making a final decision. A trial run with each product can assist in getting a real-world understanding of each solution.
The overall strength of Microsoft Cloud Defender lies in its ability to protect cloud resources effectively within its existing environment. This also includes its ability to streamline security management for those already using Microsoft services. The platform’s focus on automated threat detection, compliance, and incident response provides a powerful set of tools. While its competitors may have unique features or specializations, the depth of integration and broad feature set of microsoft cloud defender makes it a very compelling option. When comparing the capabilities of all platforms, make sure to consider what aligns best with the business objectives. An informed approach helps to ensure a robust and effective cloud security framework.
Real-World Examples of Success with Microsoft’s Cloud Defense
Numerous organizations across diverse industries have significantly improved their security posture by implementing Microsoft Cloud Defender. A global financial institution, for example, faced frequent sophisticated cyberattacks targeting their sensitive customer data. By deploying Microsoft Cloud Defender, they gained enhanced threat detection capabilities. The platform’s real-time monitoring and automated incident response features allowed them to identify and neutralize threats far more rapidly. This resulted in a considerable reduction in successful security breaches and minimized potential financial losses. The implementation also streamlined their security operations, freeing up valuable time for the security team to focus on strategic initiatives. The platform demonstrated its effectiveness in a high-stakes environment, underscoring its capability to safeguard critical infrastructure and sensitive data.
In the healthcare sector, a large hospital network struggled to maintain compliance with stringent data privacy regulations, like HIPAA. The constant threat of ransomware attacks and data leaks created major operational challenges. Integrating Microsoft Cloud Defender offered them comprehensive visibility into their entire cloud environment. The platform provided automated compliance checks and policy enforcement. They could proactively identify vulnerabilities, implement necessary security controls, and significantly reduce the risk of data breaches. Microsoft Cloud Defender’s ability to offer tailored protection for different types of cloud deployments—including IaaS, PaaS, and SaaS—proved crucial for addressing this complex hospital network’s needs. This demonstrated the adaptability and versatility of the platform to handle varied and sensitive data landscapes.
A technology startup, another example, needed a robust yet scalable security solution as they rapidly expanded their cloud presence. Microsoft Cloud Defender provided the perfect mix of advanced features and ease of deployment. The startup benefited from enhanced threat intelligence and anomaly detection capabilities. These capabilities helped them to proactively identify and prevent potential threats. Automated incident response reduced their team’s workload and allowed them to focus on innovation. This real-world success highlights how Microsoft Cloud Defender can support both growing and established organizations, providing robust security without hindering productivity and growth. These use cases highlight how Microsoft Cloud Defender effectively protects different types of businesses and industries by using its comprehensive feature set.
Optimizing Your Cloud Security Deployment with Best Practices
Implementing Microsoft Cloud Defender effectively requires a strategic approach centered on best practices. One crucial aspect is establishing robust role-based access control. This ensures that only authorized personnel have the necessary permissions. Assigning roles based on the principle of least privilege minimizes the risk of unauthorized access or accidental misconfiguration. Regular audits of access permissions are equally important. This review process helps identify and rectify any potential security gaps.
Continuous monitoring is another cornerstone of a strong security posture. Microsoft Cloud Defender provides real-time threat detection and alerting capabilities. These features must be actively monitored and analyzed. Security teams should establish clear processes for incident response. The process should outline how to handle security alerts efficiently and effectively. This includes defining escalation paths and response timelines. Proactive planning enables quick mitigation. This reduces the impact of security incidents. Regular security audits are vital. These audits provide a thorough examination of your security controls. Identifying and addressing vulnerabilities reduces the attack surface. This includes evaluating configurations. It also evaluates policies to ensure they remain aligned with best practices. This commitment ensures continuous improvement. A well-defined strategy allows for adapting to new threats.
Proactive incident response planning is a critical element for successful implementation of microsoft cloud defender. A detailed incident response plan outlines the steps to take in the event of a security breach. The plan should specify the roles and responsibilities of the incident response team. Additionally, the plan must include a communication strategy for both internal and external stakeholders. Regular testing and updates of the plan are crucial. This ensures that your team is ready to respond effectively to any incident. The effectiveness of microsoft cloud defender is maximized. Through a well-defined, carefully planned and proactive response. This includes not only the tools and technology. But also the people and procedures that manage it. Following these best practices will enhance overall cloud security. It is not just about installing a security solution. It involves a continuous cycle of planning, implementation, monitoring, and improvement.
Future Trends and Innovations in Microsoft’s Cloud Security
The landscape of cloud security is perpetually evolving, demanding constant innovation and adaptation. Microsoft is deeply committed to meeting these challenges head-on, with Microsoft Cloud Defender at the forefront of its security strategy. The future will see an increased focus on AI-powered threat detection, moving beyond traditional signature-based methods to identify sophisticated and zero-day attacks. This involves machine learning algorithms that continuously analyze vast datasets to learn and predict potential threats, ensuring proactive defense mechanisms are in place. Furthermore, integration with emerging technologies like serverless computing and edge devices will be crucial, requiring security solutions that are both versatile and scalable. Microsoft Cloud Defender is being developed to extend its protection across all these modern deployments.
Microsoft envisions a future where security is not an afterthought, but rather a built-in feature of all cloud operations. This vision entails further automation of incident response, minimizing the time between threat detection and neutralization. Microsoft’s strategy includes streamlining security operations through enhanced analytics and actionable insights. This will provide security teams with a more granular understanding of their security posture and the tools to react swiftly and efficiently. Expect to see enhancements in Microsoft Cloud Defender related to simplified configuration, improved user interfaces, and greater ease of use for security professionals. The commitment from Microsoft also aims at better integration with other Microsoft security tools, creating a more cohesive and comprehensive security platform. Future planned updates will further incorporate compliance management functionalities that are vital to help organizations meet evolving regulatory standards.
Innovation in cloud security will also extend into the realm of data protection. Microsoft Cloud Defender will likely see expansions in its data loss prevention capabilities, with improved ways to identify and secure sensitive information residing in cloud environments. Moreover, Microsoft is dedicated to pushing the boundaries of threat intelligence, collaborating with industry partners and security researchers to stay ahead of malicious actors. This dedication to innovation ensures that Microsoft Cloud Defender is not just a solution for today, but a robust security platform for the future. Continuous improvements and proactive enhancements are at the core of Microsoft’s dedication to safeguarding cloud environments from new threats and challenges. The goal is to provide a comprehensive, intelligent, and adaptable Microsoft Cloud Defender for all types of business, ensuring a secure future in the cloud.
Conclusion: Is Microsoft’s Cloud Security a Worthy Investment?
In summary, this article has explored the capabilities of Microsoft’s cloud security solution, with a focus on Microsoft Cloud Defender. We have examined its role in the broader context of cloud security challenges. The implementation process of this security suite has also been discussed. We have also delved into the specific features and functionalities that contribute to a robust security posture. These tools like threat intelligence and automated incident response can significantly enhance protection. A comparative analysis highlighted the strengths of Microsoft Cloud Defender within the competitive landscape. The discussion included a balanced view of its unique offerings. Real-world examples illustrated the tangible benefits of implementing the solution. It provided valuable insight into how organizations across diverse industries have benefited from it.
The best practices for optimizing cloud security deployments were also reviewed. This included the importance of continuous monitoring and proactive incident response planning. Considering all aspects, it is clear that Microsoft Cloud Defender offers a compelling value proposition for businesses. It caters to both small and large organizations. It provides a comprehensive set of capabilities designed to protect cloud environments. The tool also has the flexibility to cater to diverse needs and deployment models. The commitment to ongoing innovation makes it a smart long-term investment. Microsoft Cloud Defender can be particularly beneficial for organizations already deeply embedded within the Microsoft ecosystem. Integration and familiar interfaces can streamline security operations.
Ultimately, the decision of choosing a cloud security solution is based on the individual needs of each organization. However, Microsoft Cloud Defender’s capabilities make it a strong contender in the market. Its potential to enhance security posture and reduce the impact of threats is apparent. The comprehensive feature set, integration capabilities, and real-world results demonstrate its overall effectiveness. The product delivers substantial value and warrants serious consideration for businesses of all sizes seeking to enhance their cloud security measures. Microsoft Cloud Defender offers a solid investment in protection. It can help create a more robust and reliable IT environment in today’s challenging cyber landscape.