Understanding Azure Web Application Firewall (WAF) and its Benefits
Azure Web Application Firewall (Azure WAF) is a crucial security service for web applications hosted on Azure. It acts as a robust defense mechanism against common web vulnerabilities. These include SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks. A proactive security approach is essential for any organization. Azure WAF significantly contributes to this. It helps maintain a secure environment by filtering malicious traffic before it reaches your web application. IP whitelisting, a key feature within Azure WAF, enhances this protection by allowing access only from specified IP addresses. Implementing a strong azure waf ip whitelist strategy is vital for optimal security.
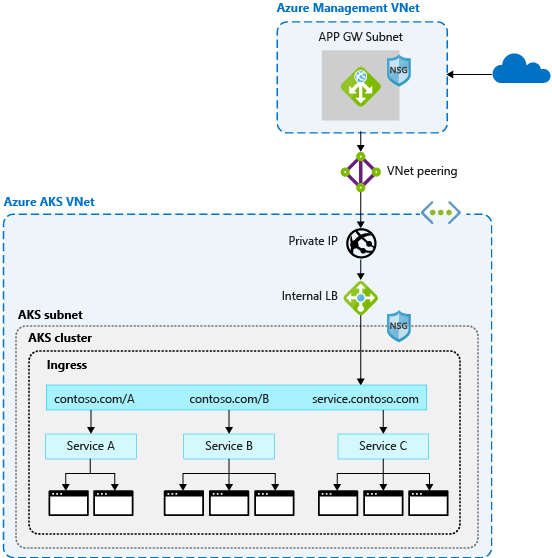
Azure WAF offers various protection levels. It actively monitors incoming traffic, identifying and blocking threats in real-time. This reduces the risk of breaches and data loss. The platform’s ability to integrate with other Azure security services, such as Azure Virtual Network and Network Security Groups (NSGs), creates a layered security architecture. This layered approach provides comprehensive protection for your web applications. The efficiency of Azure WAF in safeguarding against various attacks, coupled with the granular control provided by features like azure waf ip whitelist, establishes it as an indispensable tool for any business prioritizing web application security. This makes Azure WAF a powerful tool for organizations of all sizes.
By using Azure WAF, businesses can mitigate the risk of costly data breaches and downtime. The proactive nature of the platform allows for early detection and mitigation of threats. The azure waf ip whitelist functionality enhances this further by significantly reducing the attack surface. This focused approach ensures that only trusted sources access your web applications. Proper implementation of azure waf ip whitelist, combined with other Azure security measures, establishes a robust security posture that minimizes vulnerabilities and protects critical business assets. Regularly reviewing and updating your azure waf ip whitelist is vital for maintaining this security.
Why Use IP Whitelisting with Azure WAF?
Implementing an azure waf ip whitelist offers significant advantages for bolstering web application security. By restricting access to only trusted IP addresses, organizations dramatically reduce their attack surface. This targeted approach minimizes the risk of unauthorized access and malicious activities, enhancing the overall security posture. Azure WAF’s integration with IP whitelisting provides a powerful layer of defense against common threats like SQL injection and cross-site scripting (XSS).
The benefits of using azure waf ip whitelist extend beyond basic protection. It’s particularly valuable for securing internal applications or those handling sensitive data. This feature allows administrators to finely control network access, ensuring only authorized users and systems can interact with critical resources. Using IP whitelisting with Azure WAF helps meet regulatory compliance requirements where stringent security controls are mandatory. Regular review and updates of the azure waf ip whitelist are crucial for maintaining its effectiveness and preventing access from compromised or outdated IP addresses. This proactive security measure significantly reduces the likelihood of successful cyberattacks.
Consider scenarios where sensitive data is involved. With an azure waf ip whitelist in place, only pre-approved IP addresses can access the application. This effectively limits potential data breaches, protecting valuable assets from unauthorized access. For internal applications, using an azure waf ip whitelist prevents external actors from accessing internal resources. This added layer of security strengthens the overall security infrastructure. The combination of Azure WAF and IP whitelisting delivers a robust, efficient, and easily managed security solution. The granular control offered by the azure waf ip whitelist makes it a valuable addition to any organization’s security arsenal.
How to Implement IP Whitelisting in Azure WAF
Implementing azure waf ip whitelist involves several steps within the Azure portal. First, navigate to your Azure Web Application Firewall instance. Locate the “IP Restrictions” or similar section within the WAF settings. This section allows you to configure the azure waf ip whitelist. You’ll find options to add individual IP addresses or IP address ranges. Enter the IP addresses or ranges you wish to whitelist, ensuring accuracy to avoid unintended access restrictions. Clearly label each entry for easy management of your azure waf ip whitelist. Remember to save your changes after adding each IP address or range. The system will then enforce these rules, allowing only traffic from the specified IP addresses to access your web application through the Azure WAF.
For more dynamic IP address management, consider integrating your Azure Virtual Network (VNet) with your azure waf ip whitelist. Azure WAF allows you to associate your VNet’s subnet with the IP whitelist. This automatically updates your azure waf ip whitelist with the current IP addresses associated with the subnet. This method simplifies management, especially if your internal IP addresses change frequently. Alternatively, utilize Azure CLI or PowerShell to automate the process of adding and removing IP addresses to your azure waf ip whitelist. Scripting streamlines this process, especially for managing many IP addresses or frequent updates. Using automation helps maintain an efficient and accurate azure waf ip whitelist. This automated approach reduces the risk of human error and maintains your security posture.
Azure provides several methods to efficiently implement and maintain your azure waf ip whitelist. You can manually add individual IP addresses or ranges directly through the Azure portal. This is suitable for static IP addresses. For dynamic IP address ranges or large-scale management, consider using Azure Virtual Networks for automatic IP address integration with your azure waf ip whitelist. This automated solution leverages the capabilities of your Azure environment. This dynamic approach is highly recommended. Finally, explore scripting solutions using Azure CLI or PowerShell for advanced automation and streamlined management of your azure waf ip whitelist. These methods provide multiple options depending on your needs, ensuring you have a tailored solution for your organization’s security requirements.
Managing Your Azure WAF IP Whitelist Effectively: Best Practices
Effective management of your azure waf ip whitelist is crucial for maintaining optimal security and minimizing disruption. Regularly review and update the list. Remove outdated IP addresses promptly. This prevents unauthorized access and streamlines security protocols. Use descriptive naming conventions for IP addresses or ranges. This improves organization and simplifies troubleshooting within the azure waf ip whitelist. For instance, use names like “Internal-Network-192.168.1.0/24” instead of generic labels. Carefully consider the implications before adding or removing IP addresses from your azure waf ip whitelist. Unexpected outages can occur if incorrect configurations are implemented. Document all changes made to the azure waf ip whitelist, including the date, time, and reason for the alteration. This creates an audit trail, assisting in identifying and resolving issues. Automation tools like Azure CLI or PowerShell can assist with managing the azure waf ip whitelist, particularly for large-scale deployments or frequent updates. These tools enable the automation of addition, removal, and verification of IP addresses, reducing the potential for manual errors.
Implementing a robust change management process for your azure waf ip whitelist is recommended. This process should define who can make changes, what steps are required for approval, and how changes are rolled out. This ensures control over changes and minimizes the risk of security breaches. Regularly test your azure waf ip whitelist to ensure it’s functioning correctly. This involves periodically trying to access your application from IP addresses both inside and outside the whitelist. This verification process helps identify any configuration errors. Consider using a dedicated monitoring system to track access attempts and potential breaches. Immediate alerts for unusual activity allow for quicker responses to security threats. This real-time visibility improves the overall responsiveness of your security posture. The azure waf ip whitelist should be integrated into your broader security strategy. This includes coordination with other security measures like Azure AD authentication and Network Security Groups. This layered approach provides more comprehensive protection for your applications.
When managing your azure waf ip whitelist, prioritize security best practices. Regularly review and update the list, using clear naming conventions. Automation tools can improve efficiency. Document all changes. Integrate the whitelist into a wider security strategy. This ensures a secure and efficient configuration of your azure waf ip whitelist. Remember, a well-managed azure waf ip whitelist contributes to a strong security posture. Proactive management minimizes vulnerabilities. Regular testing and monitoring improve overall protection. The use of descriptive names for IP address ranges within your azure waf ip whitelist enhances organization and maintainability. The azure waf ip whitelist should not be viewed as a standalone solution. Integrate it with other security measures. This creates a layered approach to protect your web applications. Automation offers efficiency. Remember that the azure waf ip whitelist is only one aspect of your overall application security. Consistent review and proactive management are essential.
Troubleshooting Common Azure WAF IP Whitelist Issues
Implementing an azure waf ip whitelist can sometimes present challenges. Incorrectly configured IP addresses are a frequent problem. Double-check the accuracy of all entered IP addresses and ranges. Ensure you’re using the correct CIDR notation for IP ranges. A simple typo can block legitimate access. Verify your IP address is correctly listed. Consult your network administrator for assistance if needed. Incorrectly configured IP addresses are a frequent cause of access issues after implementing the azure waf ip whitelist.
Another common issue arises when users experience access problems after enabling the azure waf ip whitelist. This often stems from misconfiguration. Carefully review the whitelist settings and ensure all required IP addresses are included. Consider temporarily disabling the whitelist to rule out configuration issues as a source of the problem. If the issue is resolved after disabling the whitelist, then the problem lies in the azure waf ip whitelist configuration itself. Users can use the Azure portal’s logging capabilities to investigate access attempts, further aiding in troubleshooting.
Managing dynamic IP addresses presents a unique set of challenges for azure waf ip whitelist implementation. If your application uses dynamic IPs, integrating Azure Virtual Network can help. This allows for automatic updates of the whitelist as IP addresses change within the network. Consider using Azure’s automation features, such as Azure CLI or PowerShell, to manage the IP whitelist dynamically. These tools can efficiently handle regular updates and reduce the manual effort needed for managing the list. Properly managing dynamic IP addresses prevents disruption to access.
Integrating Azure WAF IP Whitelisting with Other Security Features
Implementing an azure waf ip whitelist is a crucial step, but it’s even more effective when integrated with other Azure security services. A layered security approach provides robust protection for your web applications. Combining azure waf ip whitelist with Azure Active Directory (Azure AD) authentication adds another layer of verification. Only authenticated users can access your application, even if their IP address is whitelisted. This prevents unauthorized access, even from trusted sources.
Azure Virtual Networks (VNets) and Network Security Groups (NSGs) further enhance the security provided by an azure waf ip whitelist. VNets provide a secure, isolated network for your resources. NSGs act as firewalls, controlling network traffic in and out of your VNet. By combining these with an azure waf ip whitelist, you create a highly secure environment. Only traffic originating from the whitelisted IPs and passing through the VNet and NSG rules can reach your web application. This significantly reduces your attack surface and protects against unauthorized access attempts.
Consider the synergy between these security elements. Azure AD verifies user identity. The VNet isolates your network. NSGs control network access. The azure waf ip whitelist restricts access to specific IP addresses. This multi-layered approach provides comprehensive security. Each layer adds an extra hurdle for attackers to overcome. This proactive strategy significantly minimizes vulnerabilities and enhances the overall security posture of your web application. By strategically combining these Azure security features, you can create a robust defense against a wide range of threats, ensuring your applications remain secure and accessible only to authorized users and systems.
Choosing the Right Azure WAF Deployment Model for Your Needs
Azure Web Application Firewall (Azure WAF) offers different deployment models, each impacting how you implement azure waf ip whitelist. The primary models are Web Application Firewall Policy and Application Gateway WAF. A Web Application Firewall Policy provides a centralized management plane for WAF rules, allowing you to apply consistent security settings across multiple web apps. This approach simplifies management and offers flexibility, making it well-suited for larger deployments with complex security needs. Implementing azure waf ip whitelist within a WAF Policy involves configuring the rules within the policy itself, and associating the policy with your target web apps. This central management makes updates and changes easier.
Conversely, Application Gateway WAF integrates WAF functionality directly into the Application Gateway. This model is often preferred for its simpler integration and improved performance, particularly when the Application Gateway is already part of your infrastructure. Azure waf ip whitelist configuration is handled directly within the Application Gateway settings. This deployment model offers a more integrated approach and can streamline your existing network setup. Consider factors like existing infrastructure, management overhead, and scalability when deciding. The choice affects how easily you manage your azure waf ip whitelist and other WAF rules.
Selecting the optimal deployment model is crucial for efficient azure waf ip whitelist management. The Web Application Firewall Policy is ideal for organizations managing multiple web apps and needing centralized rule management. Application Gateway WAF, conversely, is suitable for simpler deployments where integration with an existing Application Gateway is preferred. Careful evaluation of your specific requirements — including scalability needs, existing infrastructure, and management complexity — will guide you to the model that best supports your azure waf ip whitelist strategy and overall security posture.
Beyond IP Whitelisting: Additional Azure WAF Security Measures
While azure waf ip whitelist offers a strong initial layer of security, Azure WAF provides a comprehensive suite of features to further enhance your web application’s protection. Consider integrating bot mitigation capabilities to identify and block malicious bots that often attempt to exploit vulnerabilities. These automated systems help prevent common attacks like credential stuffing and account takeover attempts, significantly reducing the risk to your applications. Azure WAF’s customizable rule sets allow you to tailor the security configurations to match your specific application’s needs. These rules can be adjusted based on your threat landscape and allow the blocking or logging of specific malicious traffic. You can easily manage these rules via the Azure portal.
For more granular control, Azure WAF supports custom rules. This advanced feature allows security professionals to create bespoke rules based on specific patterns and characteristics of malicious requests. Custom rules provide an extremely detailed level of security, letting you define and respond to threats that may evade standard rule sets. This powerful tool is excellent for organizations requiring exceptionally precise control over their web application security posture. Combining custom rules with an azure waf ip whitelist creates a robust, multi-layered defense.
Remember that a robust security strategy often involves multiple layers. Implementing an azure waf ip whitelist is a crucial first step, but integrating it with other advanced Azure WAF features such as bot mitigation, rule sets, and custom rules creates a holistic and highly effective approach. Regularly review and update your security configurations to adapt to the ever-evolving threat landscape. Proactive management ensures your web application remains protected against a wide range of threats, minimizing risks and maintaining optimal security.