What is AWS Config and Why it Matters?
AWS Config stands as a pivotal service within the Amazon Web Services ecosystem, designed to continuously evaluate and audit the configurations of your AWS resources. Its primary function involves meticulous tracking of resource changes, enabling you to maintain a comprehensive record of how your infrastructure evolves over time. This powerful capability facilitates the enforcement of organizational policies, ensuring that your AWS environment adheres to predefined security standards, governance requirements, and operational best practices. By continuously monitoring the state of your resources, AWS Config provides a crucial mechanism to identify deviations from established configurations, offering a significant advantage in risk mitigation and compliance management. The implications of implementing AWS Config extend far beyond mere tracking; it empowers organizations to proactively manage their cloud environments with confidence. This is essential for any organization seeking to maintain a robust security posture while optimizing resource allocation. The automation offered by AWS Config drastically reduces the need for manual audits, which can be both time-consuming and prone to error. Instead, AWS Config enables ongoing, automated auditing, significantly reducing operational overhead and enhancing the consistency of your security practices. By providing a centralized view of resource configurations, it fosters a clearer understanding of your operational landscape, thereby allowing quicker responses to compliance issues and security vulnerabilities. Through leveraging AWS Config, businesses can gain greater visibility into their resource deployments, ultimately leading to more agile and secure operations.
The benefits of adopting AWS Config are manifold, with a significant impact on the overall efficiency and security of cloud operations. The reduction in manual effort, afforded by the automated tracking and auditing processes, allows technical teams to focus on strategic initiatives rather than spending countless hours on manual configuration checks. Continuous auditing is another key benefit, providing an immediate feedback loop that alerts you to any non-compliant resources as soon as they appear. This near real-time compliance monitoring enables you to address issues promptly and avoid potentially costly or disruptive security breaches. Furthermore, the capacity for faster responses to compliance issues significantly improves an organization’s capacity to mitigate risks and maintain its operational integrity. AWS Config helps in this by simplifying the identification and resolution of issues, enabling IT teams to rectify issues more effectively and within smaller windows of time. The centralized visibility provided by AWS Config also reduces the chances of configuration drift, whereby resource settings deviate from their intended parameters. This drift can create vulnerabilities and inconsistent behaviors if not caught early. By integrating AWS Config into your operational workflow, you establish a proactive approach to governance and control over your cloud assets, ensuring continuous compliance and security. In addition, this proactive approach using aws config to monitor and enforce policy helps in building a more resilient infrastructure.
In conclusion, the adoption of AWS Config is a strategic step for organizations looking to achieve optimal security, governance, and operational efficiency. Its ability to automatically track and enforce compliance policies not only strengthens your security posture but also streamlines your operational workflows. The proactive auditing and near real-time alerts offered by aws config allows organizations to respond faster to compliance issues, mitigating the risks associated with misconfigurations. Leveraging the comprehensive tracking and continuous monitoring capabilities of AWS Config provides tangible benefits by reducing the manual effort involved in configuration management and improves the overall security of your AWS deployments. It offers a robust mechanism for maintaining compliance and security, supporting the development of reliable and dependable cloud infrastructure for modern businesses.
How to Set Up AWS Config for Resource Tracking
Setting up AWS Config involves several crucial steps to ensure accurate and efficient tracking of your AWS resources. The process begins with choosing the appropriate AWS regions where you want to monitor your resources, as AWS Config operates on a per-region basis. Once the regions are selected, configuring recording options is the next step, allowing you to specify whether to record all resources or specific types. This involves careful consideration of your needs, as recording all resources may incur higher costs but offers the broadest coverage. Conversely, selecting specific types can reduce costs but requires diligent management of changing needs. A delivery channel is then set up, typically directing the configuration data to an S3 bucket. This bucket must have the correct permissions to allow AWS Config to write data into it, which is a key step to ensure successful operation. Permissions are managed through IAM roles, requiring a role that grants AWS Config the necessary access to your resources and the ability to write to the S3 bucket. This includes permissions to read resource configurations, write to S3 and if used to deliver to other services. It is also critical to configure the resource types that need to be tracked. This requires careful planning and a clear understanding of which resources are important to your organization. Ensuring only relevant resource types are selected helps to optimize both performance and cost of your AWS Config implementation.
When setting up AWS Config, several best practices should be followed to ensure optimal performance and accuracy. First, it is vital to regularly review the configured resource types and adjust them as your infrastructure evolves. This is crucial for minimizing the cost and optimizing the overall efficiency. IAM roles should be meticulously crafted with the principle of least privilege, granting AWS Config only the necessary permissions, which is essential for security purposes. Also, setting up a dedicated S3 bucket for AWS Config data provides better organization and simplifies the management of the configurations. This bucket should also be secured with appropriate policies to ensure only authorized access is allowed. Another important best practice is to establish a clear naming convention for all resources that will be tracked, which aids in the identification of resources during analysis of rule violations. This consistency is vital for maintaining a clean and manageable environment. Moreover, configuring cross-region aggregation can enable a single view of the entire infrastructure of your organization which can be very helpful in larger deployments. Finally, when setting up the delivery channel, it is beneficial to set up also event notifications to be informed as resources change state, allowing for a more proactive approach to configuration management. The initial setup of AWS Config is a critical step to building a solid foundation for AWS infrastructure management, so careful planning is essential.
Following these steps will lead to an accurate and efficient AWS Config implementation. The careful planning of regions, resource types, delivery channels, permissions, and the implementation of best practices in setting up AWS config are vital to success. Proper management of AWS config can greatly enhance security, governance, and operational excellence within your AWS environment. An optimal configuration of AWS config is an important component in managing your cloud infrastructure efficiently.
Configuring Rules for Compliance and Security
AWS Config rules are at the heart of its compliance assessment capabilities, providing a mechanism to evaluate resource configurations against predefined or custom criteria. These rules are essential for ensuring that your AWS environment adheres to both internal security policies and external regulatory requirements. There are two primary types of rules: managed rules and custom rules. Managed rules are pre-built by AWS and offer a quick start for common compliance checks, such as ensuring that S3 buckets are encrypted, that all EBS volumes are encrypted, or that specific IAM policies are not used. Selecting from the extensive list of managed rules allows you to quickly apply best practices without extensive configuration. On the other hand, custom rules, provide the flexibility needed to address specific organizational requirements that aren’t covered by managed rules. These are built using AWS Lambda functions, which allow for intricate logic to determine compliance. When deciding between the two, consider the level of customization and complexity required; managed rules are best for standard, broadly applicable checks, while custom rules cater to more niche requirements that need particular logic or access to data outside the current configuration.
Setting up an AWS Config rule involves specifying a trigger that initiates rule evaluation, such as configuration changes or periodic checks. It is vital to select triggers that align with the desired monitoring frequency and compliance posture. For instance, a periodic check every 24 hours might be adequate for lower-priority policies, whereas continuous evaluation triggered by configuration changes is best for high-impact security checks. When configuring rules, also select the specific AWS resource type that the rule is intended to evaluate. For example, an S3 bucket encryption rule would apply to all S3 buckets in the designated region. It is also very important to define the evaluation parameters. These parameters are rule specific. For the S3 bucket encryption example, you may need to specify which encryption type should be enforced. Examples of security and compliance rules include ensuring that all EC2 instances have appropriate tags, security groups are not open to the world, or that root accounts do not have active API keys. These rules are crucial in strengthening your security posture and promoting good governance across your AWS environment. With AWS Config, you can continuously audit your environment using these established rules.
To effectively use AWS Config, consider creating an organized taxonomy for your rules. This organization will help to easily filter and identify the results of the rules in order to quickly spot violations. This will also help to keep track of which rules are applicable and if new rules are needed. The use of a logical naming system is advisable to prevent confusion and to streamline the troubleshooting process. Regular reviews of the effectiveness of current AWS Config rules and updates based on new threats and requirements are a good practice. Also, regularly test rule configurations to confirm they are functioning as intended and to validate if they are delivering desired security and compliance controls. This methodical approach to setting up and maintaining AWS Config rules ensures a robust and continuously compliant AWS environment. Remember that AWS Config facilitates the enforcement of your security policies, rather than doing it for you. It’s crucial to properly set up and continuously monitor the rules to keep the AWS environment secure and compliant.
Analyzing and Interpreting AWS Config Results
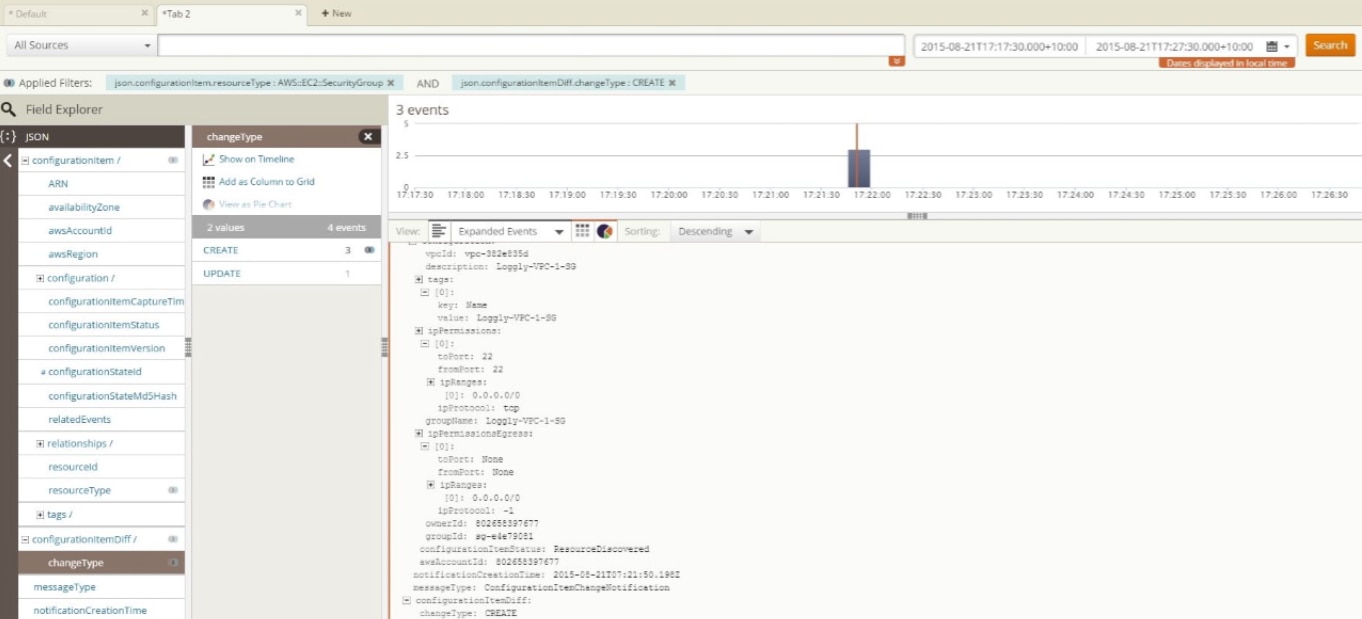
Understanding how to analyze and interpret the results generated by AWS Config is crucial for maintaining a secure and compliant AWS environment. The service evaluates resource configurations against predefined or custom rules, providing valuable insights into the current state of your infrastructure. The AWS Console serves as the primary interface for viewing this compliance data. Within the console, you can access detailed information about each rule evaluation, including which resources are compliant, non-compliant, or not applicable. Filtering capabilities allow users to narrow down results based on resource types, rule names, and compliance status, thereby allowing for prioritized attention to issues needing immediate remediation. Dashboards offer a quick overview of the overall compliance posture, displaying summaries and visualizations of the data. It is essential to move beyond the dashboard and analyze detailed findings, understanding the specific reasons for a resource’s non-compliance. This includes carefully examining each resource’s configuration against the specific criteria defined in the rule. This allows for a deeper understanding of the underlying issues and effective remediation strategies.
Interpreting the various states reported by AWS Config is key to effective resource management. A ‘compliant’ state signifies that the resource meets the requirements set by the configured rule. Conversely, a ‘non-compliant’ status indicates that a resource violates the rule criteria and requires action to rectify the issue. A ‘not applicable’ state means the resource is not subject to the specific rule due to it not being within its scope. Understanding these statuses allows teams to prioritize their efforts, focusing first on remediating non-compliant resources. The results from AWS Config can be used to drive operational changes, allowing for the continuous adjustment of your AWS configurations to meet your evolving compliance and security requirements. The ability to drill down into specific findings, understand the reason behind compliance failures, and differentiate between these states is essential for effective use of AWS config as an integral tool within AWS infrastructure management.
Effectively leveraging the findings from aws config is about using the detailed information provided to develop appropriate remediation actions. These insights should guide changes in infrastructure configuration to restore compliance. For example, if aws config reports an S3 bucket as non-compliant due to lack of encryption, this clearly indicates the need to enable encryption on that specific bucket. Or if an EC2 instance is flagged for missing specific tags, you know to either apply them, or create a rule that auto-applies them moving forward. This approach turns the audit data from aws config into practical steps toward a more secure, compliant, and well-managed AWS environment. Understanding and acting on these findings is what separates a good infrastructure setup from a great one. This proactive response based on the information in AWS Config helps to enforce internal and external governance standards.
Automating Remediation with AWS Config
Automating remediation actions based on findings from AWS Config is crucial for maintaining a robust and compliant AWS environment. AWS Config, while powerful for detecting non-compliance, becomes even more effective when coupled with automated response mechanisms. One common approach involves integrating AWS Config with AWS Systems Manager Automation. When AWS Config identifies a resource violating a defined rule, it can trigger a Systems Manager Automation document. This document contains predefined steps to remediate the issue. For example, if an S3 bucket is detected as not encrypted, an automation document can automatically enable encryption. Another powerful integration is with AWS Lambda. When a non-compliant resource is detected by AWS Config, it can trigger a Lambda function. This Lambda function can then execute custom logic to address the non-compliance. For instance, a function might modify resource tags to adhere to organizational standards, or apply network settings based on the resource type. Furthermore, AWS Config can send events to CloudWatch Events, which can further trigger notifications, initiate other automation workflows, or even raise alerts for manual intervention. The power of combining AWS config with automated workflows resides in the ability to reduce manual toil and speed up response times, ensuring that resources remain compliant with policies continuously, and drastically enhancing the security posture of the AWS infrastructure.
Implementing automated remediation strategies with aws config requires a careful design of workflows. It’s important to thoroughly test each remediation action in a non-production environment to avoid unintended consequences. The use of infrastructure as code (IaC) tools like AWS CloudFormation or Terraform can greatly improve automation efforts. They allow defining and versioning resources, which creates consistency and predictability in the remediation processes. For example, if a non-compliant resource setting needs to be modified, Infrastructure as code will apply these changes uniformly and predictably across all resources in the specified environment. Consider using AWS Step Functions to orchestrate complex workflows that involve multiple services and steps. They allow to chain together different remediation actions, enabling handling multi-stage fixes. This approach enhances the robustness and reliability of the overall automation, making it possible to handle more sophisticated compliance violations. Moreover, logging each automation execution helps with auditing and future improvements. By leveraging these best practices, organizations can achieve a high level of automation in their compliance efforts, significantly reducing the burden of manual intervention, and reducing time needed to fix security and compliance issues. Automated remediation with aws config not only ensures compliance but also drastically improves operational efficiency.
In designing these automated workflows, it’s also crucial to adopt a progressive implementation approach. Start with less critical remediation actions and gradually extend the automation to more complex scenarios. This way, the effectiveness and safety of the remediation logic can be tested and verified. It’s also advisable to establish a system of checks and balances to ensure that automated actions do not lead to new problems. For instance, before triggering a major change, there should be a process in place to verify if that change aligns with current configuration and security policy. Remember that the goal is to enhance compliance and improve security posture by implementing a robust remediation strategy with AWS Config in a smart and efficient way. By making judicious use of the services and following best practices, a complete solution that significantly enhances the speed and effectiveness of AWS resource remediation can be created. This level of automation not only provides a stable and reliable environment, but it also greatly frees up resources, so your team can focus on more strategic initiatives. The ability to consistently enforce security policies greatly reduces risk and costs, and allows for further growth and innovation.
Leveraging AWS Config for Specific Use Cases
AWS Config proves to be a versatile tool applicable across various scenarios, enhancing infrastructure management and security. For compliance reporting, AWS Config provides a detailed audit trail of resource configurations, crucial for demonstrating adherence to industry standards like HIPAA or PCI DSS. This functionality streamlines the auditing process, allowing organizations to easily generate reports that showcase compliance postures over time. In troubleshooting, AWS Config helps to quickly pinpoint the source of infrastructure issues by tracking configuration changes. By reviewing past configurations, teams can identify when a change introduced a problem, thereby accelerating the debugging process. Furthermore, AWS Config is instrumental in enforcing consistent policies for resource provisioning and updates, ensuring that all resources adhere to predefined standards. When a new resource is launched or an existing one is modified, AWS Config evaluates it against specified rules, automatically flagging any deviations for correction. This promotes consistency across the AWS environment, reducing risk and enhancing overall management.
Consider the use case of enforcing tagging policies. Using AWS Config, a business can set up a rule that requires all EC2 instances to have specific tags, for example, `Environment`, `CostCenter`, and `Application`. If an instance is created or updated without the required tags, AWS Config will flag it as non-compliant. This ensures that every resource can be tracked, managed, and cost allocated according to specific requirements. Another compelling scenario is change management. Every change to resources is tracked with AWS Config, offering a clear audit trail. This helps teams keep tabs on the who, what, and when of infrastructure modifications, making change management safer and more auditable. AWS Config provides a complete history of resource configurations over time and is essential for both security and operational efficiency. For example, if an access policy is changed that opens up a security risk, the team can use the history and remediate the change quickly.
Case studies illustrate the practical effectiveness of AWS Config. A large financial institution used AWS Config to automate compliance checks for sensitive data, reducing the time spent on manual audits by 60% and catching potential security vulnerabilities proactively. Another example is a technology startup that leveraged AWS Config to enforce tagging policies across their AWS resources. This approach gave them better insight into cost management. AWS Config’s capacity to automatically monitor and enforce desired states enables teams to streamline compliance efforts, accelerate incident response, and consistently maintain their AWS infrastructure. These examples highlight how AWS config can significantly enhance an organization’s management and compliance strategy. The detailed visibility and control afforded by AWS Config are invaluable for teams managing complex AWS environments.
Best Practices for Effective AWS Config Usage
To maximize the effectiveness of aws config, several key best practices should be considered. Firstly, when setting up aws config, it is crucial to define clear objectives for its use. This involves deciding which resources are most critical to track, which compliance rules are essential, and the specific metrics to monitor. This targeted approach avoids over-burdening aws config and keeps costs manageable. Proper planning before implementation will ensure that the service is focused on the most important needs. Another key aspect is related to performance and efficiency. It is recommended to regularly assess the scope of the configurations that aws config is recording. Restricting the tracked resources to only those that are required helps reduce the load and, consequently, the cost. Regularly review the rules set in aws config and identify ones that are no longer needed or those that can be optimized. By regularly auditing your compliance policies, you can help ensure that aws config is providing value without incurring unnecessary expenses.
Effective cost management is another critical element when using aws config. Understanding the pricing model is essential, and setting budget alarms is a proactive way of controlling costs. The cost can quickly increase with large environments, and managing it requires constant oversight. It’s also a good practice to implement resource tagging which helps in allocating cost to each department or team using this service. In addition, managing data retention with aws config is also necessary. A detailed assessment of how long to retain configuration history must be done considering compliance and storage costs. This ensures that compliance needs are met without creating excessive storage burdens. It’s beneficial to create backups of compliance data and delete old ones that are no longer necessary. Permissions management is also important; adhere to the principle of least privilege to avoid misconfigurations or accidental changes to the rules configuration. Implement IAM policies that restrict permissions to only what is necessary to perform their jobs, both to individuals and services using aws config.
Finally, ongoing maintenance and monitoring are necessary for long-term success using aws config. Regularly updating compliance policies and rulesets to reflect changes in business or security needs is very important. Set up alerts and notifications to quickly respond to compliance violations and keep the environment secure. Leverage dashboards to gain a comprehensive view of the compliance status, and create a feedback loop to constantly improve configurations based on aws config results. When it comes to scalability, plan for the growth of the AWS environment and scale the AWS Config setup accordingly. Properly manage logs to have detailed information for troubleshooting and make sure that the data collection is consistent. By combining these best practices, aws config can provide valuable benefits in compliance, security, and operational efficiency.
Troubleshooting Common AWS Config Issues
When working with AWS Config, users may encounter several challenges that can hinder its effectiveness. One common issue revolves around delivery channels. If the Simple Storage Service (S3) bucket designated for storing AWS Config data is not properly configured or lacks the necessary permissions, AWS Config may fail to deliver configuration snapshots and history, leading to incomplete or missing data. Ensuring the S3 bucket policy grants aws config sufficient read and write permissions is vital; a misconfiguration here will result in logs not being delivered, which impacts the entire audit trail. Another frequent problem relates to rule evaluation. If AWS Config rules are not functioning as expected, it is crucial to verify the rule’s configuration, including its scope and parameters. For example, a custom AWS Config rule that has incorrect logic, or a managed rule misconfigured could trigger unintended behavior. It’s necessary to double check the Lambda function tied to a custom rule and to ensure that the parameters specified for managed rules are aligned with the resources under assessment. Furthermore, issues with IAM roles and permissions can also cause problems; if the role assumed by AWS Config lacks permissions for the resources it needs to evaluate, rule results may be incomplete. Therefore, always review IAM policies attached to the configuration recorder’s role and be sure that it can access all the regions and resources.
Performance delays are another area where AWS Config users may experience issues. Large and complex environments with many resources can result in extended processing times for configuration evaluations and delivery. The use of AWS Config in very large AWS deployments can lead to delayed configurations, for that reason it’s important to understand the limits of the service and to implement appropriate scaling, such as configuring resource types to be tracked to only the relevant ones. Another scenario that can lead to performance issues is having too many AWS config rules defined, especially those with high complexity and the use of complex custom rules might also add to delays, therefore having a rule strategy is key. It’s important to review rule sets and eliminate unnecessary and/or redundant ones. Analyzing CloudTrail logs can provide insights into errors related to AWS Config, specifically logs will pinpoint issues with the delivery channel or the resource configuration; the logs will provide detailed information about configuration changes, rule evaluations, and error messages. In addition, check the configuration recorder’s status in the AWS console to see if there are specific error messages or if it’s not working correctly. In the case of performance delays, consider optimizing the resources AWS Config is monitoring, the rules being applied, and the general configuration, to maintain an efficient and functioning system. In essence, systematic troubleshooting of aws config involves careful checks of delivery, rules, permissions, and performance.