What is Infrastructure as Code and Why is it Crucial?
In the modern world of Information Technology, managing infrastructure can be complex. Traditionally, configuring servers and network devices involved manual processes, often leading to inconsistencies and errors. Infrastructure as Code (IaC) emerges as a solution, treating infrastructure configuration like software code. This means that configurations are defined in files, versioned, and can be automatically provisioned and managed. This approach significantly reduces manual labor and human errors, making infrastructure management more reliable and scalable. IaC is not just a trend but a fundamental shift in how we approach IT. Tools like Ansible come into the picture to enable the automation and consistent application of these configurations. When we talk about ansible config management, we mean using Ansible to enforce these desired configurations across your systems. It ensures that all servers are set up the same way, eliminating inconsistencies and providing a more streamlined and reliable system.
Ansible is a powerful tool within the IaC framework, allowing you to define your infrastructure’s desired state through simple, readable playbooks. Instead of logging into each server and making changes by hand, you write an Ansible playbook that describes what each server should look like. This playbook is then applied automatically, ensuring that configurations are consistent and reproducible. Imagine setting up a web server; instead of running through commands manually on each machine, Ansible will follow the playbook instructions to install the necessary software, create directories, and configure firewalls all by itself and in the same way across multiple servers. For any IT professional, the value of automated configuration management with Ansible is undeniable. It allows for faster deployments, easier rollback processes, and most importantly, more consistent and error-free environments. Ansible config management empowers teams to manage complex infrastructures with ease and confidence. The goal of Infrastructure as Code, with Ansible at its heart, is to make IT infrastructure more manageable, scalable, and reliable. It’s about setting up servers and applications in a controlled, repeatable, and auditable manner, eliminating the chaos of manual configurations and ensuring that IT teams can focus on innovation rather than firefighting.
In essence, ansible config management is not about just writing code but writing repeatable and automatable processes for managing and configuring your infrastructure. This provides better control and faster deployments and is a key component for any modern IT environment that seeks to operate efficiently and reduce risks. For a non-expert reader, this translates to understanding that using Ansible is like having a set of instructions you give to a computer that does all the setup work for you, rather than you doing it manually over and over again. This process reduces errors, saves time and provides a higher level of consistency. So, rather than going to each server and setting things up, you write instructions for Ansible and let it handle everything. This is what is meant by automation with configuration management using ansible.
How to Implement Configuration Automation with Ansible
Getting started with Ansible for automated configuration management is simpler than you might think. First, you need to install Ansible on your control machine. This is typically done using package managers like pip for Python. For example, on a Debian-based system, you would use the command `sudo apt install ansible`. Once Ansible is installed, the next step involves setting up your inventory file. This file lists the target machines that Ansible will manage, specifying their IP addresses or hostnames, along with any group assignments. A basic inventory file could look like this: `[webservers] server1 ansible_host=192.168.1.10 server2 ansible_host=192.168.1.20`. This is the first step of your ansible config management journey. Now, you’re ready to write your first simple playbook. Ansible playbooks use YAML format and define the desired state of your infrastructure. A basic playbook might install a web server like Apache. It involves defining tasks that describe the actions to be taken, such as installing packages or starting services, all with the goal of effective ansible config management. Here is an example:
Key Benefits of Ansible for Configuration Management
Ansible stands out as a powerful tool for ansible config management, offering several key advantages that simplify and enhance the automation process. One of its most significant benefits is its agentless architecture. Unlike other configuration management tools that require software agents to be installed on managed nodes, Ansible operates over SSH or WinRM. This eliminates the overhead of installing and maintaining agents on each server, reducing complexity and potential security risks. The absence of agents also makes Ansible significantly easier to implement and manage, particularly in environments with a large number of nodes. The communication is secured through these known protocols and it integrates seamlessly with existing security systems, providing a smoother overall experience for ansible config management. Another powerful feature of Ansible is its idempotency. This means that when a playbook is executed, it only makes changes to the system if necessary to bring it into the desired state. If a system is already configured correctly, Ansible will detect that and will not make any alterations. This prevents unintended modifications and makes it safe to re-run playbooks multiple times without risking data corruption or configuration conflicts, which is particularly useful in a dynamic environment where changes need to be made and applied multiple times for ansible config management.
The simplicity and ease of use are also key attributes of Ansible for ansible config management. Its language is based on YAML, which is very human readable and easy to learn, allowing administrators to quickly start writing playbooks and managing complex infrastructure. This reduces the learning curve and makes automation accessible to a wider range of users, not just expert developers or infrastructure engineers. Moreover, Ansible boasts a vast collection of modules that cover a wide range of tasks, from installing software and configuring services to managing cloud resources and databases. This abundance of modules makes it very simple to automate almost any process without the need to write complex code from scratch. The large and active community behind Ansible also means that users can find extensive support, resources and ready-to-use playbooks for almost any task. This active community also helps continuously improve and expand the tool, making it more robust and useful. The modules provided and the easy to use approach make it an ideal tool for a great ansible config management.
Furthermore, Ansible’s ability to scale effortlessly from small deployments to large infrastructures makes it a flexible and reliable solution for configuration management. Its approach, focusing on simplicity without compromising on power, enables both small teams and large organizations to quickly and effectively implement complex automation processes. The advantages are very clear: Ansible’s agentless model, its idempotency, user-friendly approach, vast community, and scalability provide a comprehensive solution for many different environments. These benefits have made Ansible a very popular choice for infrastructure automation and configuration management for many teams all over the world, and a tool that every team can easily implement for great results with ansible config management.
Comparing Ansible with Other Configuration Management Tools
While Ansible stands out as a powerful tool for ansible config management, it’s not the only option available. Several other configuration management tools exist, each with its strengths and weaknesses. Puppet, for example, is a mature tool known for its strong declarative language and client-server architecture, meaning agents need to be installed on the managed nodes. This contrasts with Ansible’s agentless approach, which simplifies initial setup and reduces the overhead on target machines. Chef is another popular option that also utilizes a client-server model, where recipes and cookbooks define configurations. Chef is known for its flexibility and scalability but often requires more in-depth programming knowledge compared to the more straightforward YAML syntax used in Ansible. SaltStack, or simply Salt, takes a different approach focused on speed and efficiency, employing a push-based model for configuration deployment and offers a robust event-driven infrastructure. Salt is powerful but can have a steeper learning curve than ansible config management.
The choice between these tools often depends on the specific needs and scale of your infrastructure. For organizations that prioritize simplicity, ease of use, and quick setup, ansible config management is a great choice. Its agentless nature is particularly beneficial for environments where installing and managing agents is not desirable. Puppet and Chef, with their client-server architectures and stronger emphasis on code, are often preferred by larger organizations with more complex and heterogeneous infrastructures, where a more programmatic approach to configuration is desired. Salt is useful where performance and rapid execution are important. Each tool offers a unique approach to solving configuration challenges. A proper evaluation, based on the existing infrastructure and needs, is necessary to pick the right option, and understanding their differences is a vital part of that process. For example, Puppet, with its extensive reporting capabilities, might be preferred in environments where detailed logging and compliance reports are critical, while the simplicity of Ansible might make it ideal for smaller setups or teams who prefer easier and faster ansible config management implementation.
In essence, while Ansible provides a user-friendly experience with its YAML-based playbooks and agentless architecture, the other tools offer specific advantages in different scenarios. The crucial point is that every tool offers similar capabilities in a different way. Deciding which tool to use really depends on the context and situation. A good understanding of their differences enables informed decisions aligned with unique infrastructure and team expertise. Ansible config management’s strength lies in its simplicity and agentless nature which is a very different approach to the one presented by Puppet, Chef or Saltstack, allowing for quick and easy implementation, and is especially useful in dynamic environments. Choosing the right tool can greatly impact the speed and efficiency of your configuration management strategy.
Ansible Playbooks: The Heart of Configuration Automation
At the core of ansible config management lies the concept of playbooks. These are YAML files that define the desired state of your systems. Think of a playbook as a recipe for your infrastructure; it specifies a series of tasks that Ansible executes to bring your servers into the required configuration. Playbooks are structured using a simple, readable syntax, making them accessible even to those without extensive programming experience. A typical playbook contains a list of plays, each of which targets a specific group of servers. Within each play, you’ll find a series of tasks. Tasks are the individual actions Ansible performs, such as installing packages, starting services, or copying files. These tasks are defined using Ansible modules, which are pre-written snippets of code that handle the heavy lifting of interacting with different systems. Furthermore, playbooks can utilize variables, allowing you to parameterize your configurations and make them reusable across different environments. For example, you can define a variable for the name of a package to install, and then easily change the package based on the environment where the playbook runs. This makes playbooks extremely flexible and powerful for ansible config management.
Playbooks also support the concept of roles, which are a way to organize tasks and variables into reusable units. Roles allow you to encapsulate common configuration patterns, making your playbooks easier to maintain and extend. For example, a “webserver” role might include tasks for installing a webserver package, configuring virtual hosts, and starting the webserver service. By structuring your playbooks using roles, you can build up a library of reusable components that can be combined to create more complex configurations. Understanding how to create effective playbooks is essential for anyone looking to use Ansible for ansible config management. For instance, a simple task might involve using the “yum” module to install a specific software package on a server. A more complex task might involve using the “template” module to generate configuration files from Jinja2 templates. The order of tasks in a playbook is important as Ansible executes them in sequence, which is vital for correctly configuring systems. Therefore, the way you write your playbook impacts how your whole infrastructure will be automated, making it the fundamental piece of ansible config management and automation.
Mastering playbooks is crucial because they’re the primary method for automating configuration with Ansible. They provide a clear, declarative way to define the state of your infrastructure. By carefully structuring your playbooks with clear task definitions, appropriate variables, and well-defined roles, you can create robust and maintainable automation. Playbooks serve as the single source of truth for your infrastructure’s configuration. Each playbook reflects the desired state, and Ansible ensures that your systems match that state, making infrastructure management more consistent and less prone to human error. Whether you’re configuring a single server or a large-scale infrastructure, Ansible playbooks are the heart of ansible config management, and it’s vital to comprehend how they operate.
Advanced Ansible Techniques: Roles, Modules and Handlers
To truly harness the power of Ansible for effective ansible config management, it’s essential to move beyond basic playbooks and delve into more advanced techniques. Roles, custom modules, and handlers are critical tools in an Ansible practitioner’s arsenal. Ansible roles facilitate the organization and reuse of configuration tasks. A role is essentially a directory with a predefined structure for tasks, variables, handlers, and other components, making playbooks more modular, maintainable, and scalable. For example, instead of repeating tasks for installing a database, configuring network settings, and setting user permissions, one can create separate roles for each and then incorporate these roles into any playbook needing that specific set of configurations. This ensures consistency across different machines, promotes code reuse, and reduces redundancy. Furthermore, roles can be shared across projects making ansible config management significantly more efficient in a real-world scenario.
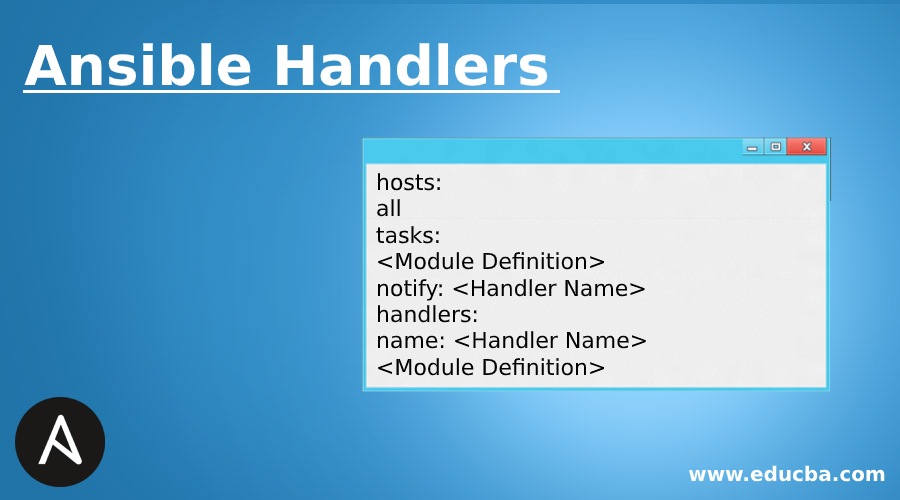
Custom Ansible modules, on the other hand, enable extending Ansible’s core functionalities. While Ansible ships with a vast library of modules, there are cases where specific tasks might require interaction with systems or APIs not readily available. In these instances, custom modules can be created using languages such as Python. These modules can then be used within playbooks, just like the built-in modules, providing the same level of convenience and integration. Imagine a scenario where you have an in-house cloud provider or a proprietary application for which there are no native Ansible modules available. Creating a custom module allows full control over how Ansible interacts with those custom interfaces, thus providing ansible config management capabilities to any type of system. Handlers, in comparison, offer a way to trigger actions based on changes. Unlike regular tasks that run every time, handlers are executed only when triggered by other tasks that have reported a change. This allows specific operations, such as restarting a service after configuration updates, to be executed efficiently. For example, you could have a handler that restarts Apache only after the httpd.conf configuration file has been altered by an Ansible task. This feature is critical in avoiding unnecessary service restarts and maintaining stable server operations. These three advanced techniques contribute to a powerful and well-structured configuration management system using Ansible.
Consider a real-world application of these concepts; imagine a complex deployment scenario where you need to deploy a full stack application including load balancers, web servers, databases, and caches. By using roles to handle each of these individual components, you can ensure consistency and repeatability. Then if, for some reason, there is a custom monitoring system that is not natively supported by Ansible, you can create a custom module that allows Ansible to interact with that monitoring system directly. This shows the value of custom modules in ansible config management. Lastly, handlers can be used to restart the services when code changes have been deployed to the web servers, guaranteeing that the application is running with the latest changes and that resources are only restarted when absolutely needed. Combining these techniques demonstrates the capabilities of Ansible beyond the basics, enabling efficient and effective automation of complex real-world infrastructures. These examples illustrate that roles, modules, and handlers provide the required tools to manage and organize complex infrastructure using Ansible for large-scale projects and that by using them, ansible config management can be achieved in a scalable and effective way.
Best Practices for Effective Ansible Configuration Management
Effective ansible config management hinges on a set of best practices that ensure reliability, security, and maintainability. When organizing playbooks, it is essential to adopt a structured approach. This means breaking down complex configurations into smaller, manageable roles. Each role should handle a specific component or service, like web server configurations, database setups, or user management. This modularity makes playbooks easier to read, modify, and reuse. Furthermore, consistently naming roles, tasks, and variables will improve the overall understanding. It is also very beneficial to implement a clear folder structure that matches the different environments you intend to control. Another key aspect of ansible config management is related to handling secrets. Hardcoding sensitive data directly into playbooks or Ansible configuration files is a major security vulnerability. Instead, use Ansible Vault to encrypt sensitive information, like passwords, API keys, and certificates. Ansible Vault allows you to keep your secrets safely stored with the rest of your code. This way, secrets are protected while still being accessible by Ansible during deployment or configuration processes. In addition to that, ensure that only authorized users have access to the encrypted files.
Another very important practice when working with ansible config management is version controlling your playbooks and Ansible configuration files using Git. This is a must for several reasons: it allows you to track changes, revert to previous states if things go wrong, and enables collaboration among team members. Every change to the infrastructure must go through version control in order to avoid unforeseen problems in production. It is also recommended to create different branches for different features or environments, ensuring a well-structured and stable workflow. Once your playbooks are written, it is important to test them rigorously before deploying them to a production environment. Never deploy automation changes directly to production. Ansible provides testing options through check mode and various testing tools. Always use these features to identify potential issues before making any actual changes. To have a stable and consistent ansible config management setup, testing should be part of a continuous integration pipeline where changes are tested automatically with every commit. This allows for problems to be detected early in the development process.
To ensure a smooth experience with ansible config management, it is crucial to keep the environment as simple as possible. Avoid using complex configurations when a simpler solution can do the same. By keeping things simple, you will reduce the probability of making mistakes, and the time it takes to understand a specific configuration will be reduced. Moreover, when working with ansible and large environments, it is a good practice to keep the inventory organized by grouping hosts based on roles or environments. This will allow you to target specific systems using host groups. In summary, implementing a structured approach in playbooks and inventories, securing sensitive data, using version control, and testing automation are the foundations of a robust ansible config management practice, which will lead to more consistent, reliable and secure automation.
Integrating Ansible with CI/CD Pipelines
Continuous Integration and Continuous Deployment (CI/CD) pipelines are pivotal in modern software development, and integrating Ansible into these pipelines enhances the automation of infrastructure deployments. Ansible config management seamlessly fits into this ecosystem, allowing for consistent and reliable deployments across different environments. By using tools like Jenkins, GitLab CI, or GitHub Actions, teams can automate the execution of Ansible playbooks as a part of their CI/CD workflow. For instance, after a successful build and testing phase, a CI/CD pipeline can trigger an Ansible playbook to deploy the latest version of an application to a staging or production server. This ensures that infrastructure configurations are automatically updated alongside application deployments. The benefit of automating this process is a reduced risk of human error, accelerated deployment cycles, and increased consistency in deployments. This integration also allows for infrastructure as code practices where configuration changes are version controlled alongside application code, promoting better collaboration between developers and operations teams. Ansible config management, therefore, becomes an essential component of the entire delivery pipeline, improving overall efficiency and ensuring a more robust and reliable deployment process.
To effectively integrate Ansible config management into a CI/CD pipeline, several best practices should be followed. Firstly, the Ansible playbooks themselves should be version controlled using Git or a similar system, aligning with general CI/CD best practices for tracking changes to infrastructure. Secondly, it’s vital to configure CI/CD pipeline to securely handle Ansible configuration secrets such as credentials for target machines and other sensitive information. Most CI/CD tools offer secure variable management capabilities designed to keep sensitive configuration data safe. Moreover, the deployment stage of the pipeline should be designed to trigger Ansible playbooks only after thorough testing and validation of the application. This is essential to prevent the deployment of faulty code and configurations. Proper feedback mechanisms should also be incorporated into the CI/CD process so that any failures of ansible config management executions during deployments can be immediately identified and addressed. When properly integrated, Ansible, becomes part of a modern, automated deployment strategy where both application and infrastructure components are released seamlessly and efficiently.
In a practical sense, the CI/CD pipeline can be set up to include steps such as: code checkout, unit testing, packaging, and then finally, deployment using Ansible. For example, after a developer commits a change, the CI/CD system automatically runs tests on that code. Upon success, the system can then execute an Ansible playbook that updates a virtual machine to include that new update. This pipeline can ensure that any new build can automatically be deployed to production, promoting a reliable process and significantly reducing manual processes. Utilizing Ansible for configuration management within a CI/CD pipeline not only streamlines deployments, but also helps ensure better consistency, reliability and efficiency in all steps of the software delivery lifecycle. By taking advantage of the strengths of Ansible with the power of CI/CD, organizations can achieve faster delivery times, greater consistency, and better overall management of their infrastructure.