Deciphering the VPN Connection Process
The core of understanding a VPN lies in grasping its primary function: establishing a secure, encrypted tunnel between your device and the vast expanse of the internet. This digital tunnel is not merely a connection; it is a protective shield, safeguarding your online activities from prying eyes. Why is this security essential? In an increasingly interconnected world, data privacy is paramount. Without a VPN, your internet traffic travels across the web exposed, akin to a postcard that anyone can read. This vulnerability can lead to potential risks, including surveillance, data theft, and targeted advertising based on your browsing habits. A VPN works by creating an encrypted channel, making your data appear like undecipherable code to anyone intercepting it, thus ensuring that your online actions remain private. This section will serve as a foundation, laying the groundwork for understanding the upcoming visual aid, illustrating precisely how this secure tunnel functions and detailing the steps involved in this secure transfer. This knowledge of how vpn works diagram will empower you to comprehend the visual representation that will follow.
How to Understand the Elements of a VPN Setup
To fully grasp how a VPN works diagram, it’s essential to understand the core components involved in establishing a secure connection. The journey begins with the user’s device, be it a computer, smartphone, or tablet. This is the origin point for all data that will be transmitted through the VPN. Next, the VPN client software plays a crucial role. This software, installed on the user’s device, acts as the intermediary, managing the encryption and decryption of data. It is the tool that connects you to the VPN service, and it’s through this client that you choose a VPN server. Understanding that the VPN software is essential before visualizing the whole process in a diagram is important. The VPN server, another key element, is a remote computer operated by the VPN service provider. It serves as a gateway through which all your internet traffic is routed. When data reaches the VPN server, it undergoes decryption, so it can finally reach the destination website or service.
The destination website or service is the final element in this setup; it is the online resource you intend to access. This could be any website, application, or online service you’re using. In this whole process of a how vpn works diagram, each element plays a specific and crucial role. The user’s device initiates the request, the VPN client encrypts the data, the VPN server forwards the data while masking the user’s IP address, and finally, the destination server delivers the desired content. The flow is always from the user’s device to the VPN server and then to the final destination server. This understanding provides the foundation for an effective utilization of the VPN technology.
The interplay of these elements is central to how a VPN works diagram, where the user’s device communicates with the VPN server which then communicates with the destination website. It’s important to consider that the VPN server’s position acts as an intermediary and will mask the user’s original IP address, and it’s all this process that is depicted in any how vpn works diagram. This process ensures that your online activity is secured and private. Understanding these elements will be crucial when visualizing the next diagram.
Visualizing the VPN Tunnel: A Step-by-Step Breakdown
The journey of data through a VPN tunnel can be envisioned as a carefully orchestrated sequence. Imagine, for instance, a letter you’re sending across the world. Normally, this letter would be sent through a public postal service, with its contents visible to anyone who might intercept it. However, when using a VPN, your data is akin to sealing the letter in an encrypted envelope before placing it into the mail. This process starts when the user’s device, such as a computer or a smartphone, initiates a request to access a website or service. The VPN client software, installed on the user’s device, immediately takes the outgoing data, like the contents of our letter, and encrypts it. This transforms the data into an unreadable format, like a code only the intended recipient can decipher. The encrypted data then travels through the internet, resembling the letter being transported through the postal system. The next stop is the VPN server, acting as the designated receiving location, where the letter finally arrives.
Once the encrypted data reaches the VPN server, the server utilizes the correct cryptographic key to decrypt the information, effectively opening the encrypted envelope. After decryption, the VPN server is able to understand what the user is requesting and sends this request to the destination website or service, as a new letter, from the server itself. This means that to the outside world, the request appears to originate from the VPN server and not from the user’s personal IP address. This step is crucial because it masks the user’s actual location and online identity, adding a layer of anonymity to the process. The response from the destination website or service then follows the reverse pathway, being encrypted by the VPN server, sent through the internet to the user’s device, and finally decrypted by the VPN client. This establishes a secure data tunnel, effectively showing how vpn works diagrammatically by ensuring data privacy from when it leaves the user’s device until it reaches its final destination, and back.
This entire process happens in a matter of seconds, but it is fundamental to understanding how a VPN safeguards your online privacy. Each step, from data encryption to routing through the VPN server and decryption of the incoming data, demonstrates how a VPN acts as a protective shield for your digital activities. It is in this very process that the benefits of a VPN become obvious, from enhancing your privacy to ensuring the security of your online data. Understanding this process lays the groundwork for a deeper understanding of the technicalities behind VPNs, particularly when you come to visualize the entire operation in the upcoming how vpn works diagram.
The Encryption Process Explained: Securing Your Data
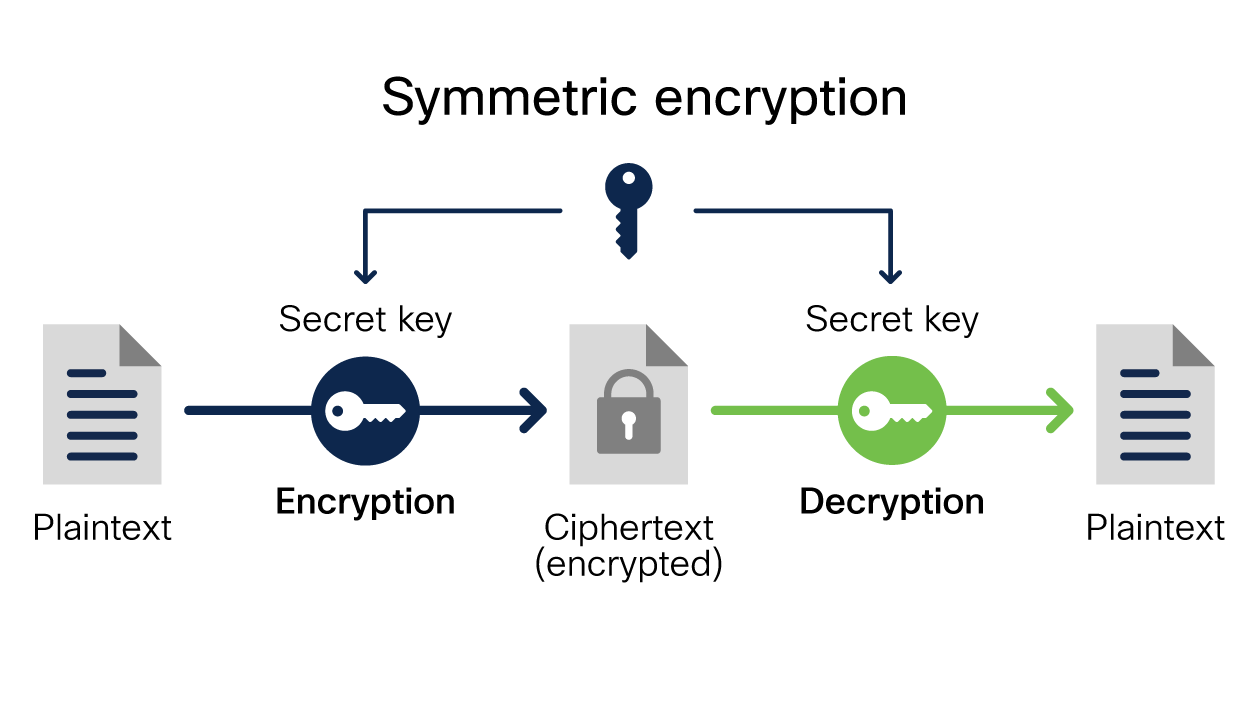
Encryption stands as the cornerstone of VPN security, forming an essential part of how a VPN works diagram. This process involves transforming readable data into an unreadable format, often referred to as ciphertext, through the application of complex algorithms. The primary purpose of encryption is to prevent unauthorized access to sensitive information as it travels across the internet, turning what would otherwise be easily intercepted data into a meaningless jumble of characters. The significance of this process cannot be overstated; without encryption, all data transmitted through a VPN would be vulnerable to eavesdropping, making the security offered by VPNs entirely ineffective. The encryption ensures that even if a third party intercepts data during transmission, they would not be able to decipher it. This layer of protection is critical in safeguarding user privacy and preventing data breaches. It’s useful to understand this when trying to understand how a vpn works diagram.
The mechanisms of encryption primarily revolve around using keys, which are complex codes that allow data to be both encrypted and decrypted. While there are different approaches to encryption, they generally fall into symmetric or asymmetric categories. In symmetric encryption, the same key is used to encrypt and decrypt data. This is like having a single key to unlock and lock a box; it’s efficient but requires secure key sharing. This process is crucial when thinking about how a vpn works diagram. Asymmetric encryption, on the other hand, uses a pair of keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, while the private key remains secret and secure, ensuring that only the intended recipient can decrypt the data. The choice of encryption method impacts performance and security differently, and they both make a fundamental part of how a vpn works diagram.
The use of these encryption methods adds a layer of complexity, but this complexity guarantees the privacy and security that users seek when using a VPN service. It’s not just about hiding data; it’s about ensuring that the data remains confidential and protected, even when traversing open or insecure networks. When visualizing how a vpn works diagram, it’s important to understand that the whole process is reliant on robust encryption methods to ensure the protection of user information from malicious threats. This encryption process is so important because without it, all the advantages that a VPN can provide are diminished, leaving users vulnerable to a host of cyber threats, which makes it a core element to understand how a vpn works diagram.
VPN Server Locations and Their Impact
The geographical location of a VPN server significantly influences the user’s perceived location and connection speed, factors that are important to understand when learning how vpn works diagram. When a user connects to a VPN, their internet traffic is routed through the chosen server. This means that to the outside world, the user’s internet activity appears to originate from the server’s location, not their actual location. For instance, a user physically located in London, connecting through a VPN server in New York, will appear to be browsing from New York. This change in IP address is one of the key functionalities of a VPN, allowing users to bypass geographical restrictions and access content that might be unavailable in their actual location. This also opens up possibilities for experiencing different browsing experiences based on the server’s location, since some websites may show content customized to the region of the IP address. This should be considered when analyzing a how vpn works diagram.
The impact on speed is another crucial aspect of server location. A server closer to the user’s actual location typically provides faster connection speeds due to lower latency and shorter data travel distances. Conversely, connecting to a server on the other side of the world might result in slower speeds. The speed can also be affected by the server’s load. A server with many users connected may experience slower speeds compared to a server with fewer users, even if it is geographically closer. Therefore, selecting a VPN server not only affects the perceived location but also the performance of the internet connection. The understanding of how different server locations work is paramount when analyzing any how vpn works diagram, allowing the user to fully understand the functionalities of the process and its potential.
Furthermore, understanding this aspect of VPNs allows users to appreciate the flexibility and control they have over their online experience. By selecting different servers, users can navigate the internet as if they are in various countries. This can unlock access to streaming services that are not available in their region or circumvent censorship imposed by their local government. However, it is also crucial to note that although it allows bypassing of location restrictions, this should be done in compliance with the terms of service of the website accessed or the local laws that applies. In addition to circumventing geo restrictions, connecting to different servers to access different IP addresses can add extra layers of security and anonymity to the overall process, which is one of the main reasons for using a VPN in the first place. With all of this, the user can analyze the how vpn works diagram with a better understanding of the multiple functionalities of the process.
Protocols that Power VPNs: The Technology Behind the Connection
The functionality of a VPN is underpinned by various protocols, each offering distinct approaches to establishing and maintaining a secure connection. Understanding these protocols provides a deeper insight into how a VPN works diagrammatically, though the actual technicalities might be invisible to the user. OpenVPN, for example, is a highly regarded open-source protocol known for its robust security and flexibility, making it a popular choice among VPN providers. It utilizes a combination of SSL/TLS for encryption, offering a strong defense against eavesdropping. However, OpenVPN might sometimes be slower compared to newer alternatives due to its complex encryption processes. IKEv2, or Internet Key Exchange version 2, is another prevalent protocol, often chosen for its stability and speed. IKEv2 is particularly favored on mobile devices, as it is known for its ability to seamlessly re-establish connections if interrupted by network changes. This makes it suitable for users who frequently switch between Wi-Fi and cellular data. Each protocol affects the overall user experience, impacting speed, security, and connection stability, which is why the selection of the right protocol based on needs is so important.
WireGuard represents a modern alternative, designed for simplicity and efficiency. This protocol is lauded for its lightweight codebase and impressive performance, often resulting in faster connection speeds and improved battery life on mobile devices. WireGuard is a relatively new protocol, but its rising popularity reflects its effectiveness. The core difference in these protocols lies in the encryption method they employ and how they manage the data tunnel. Some protocols focus on speed optimization while others lean more towards security. The protocol chosen by the user can impact the speed at which data is transmitted through the VPN, which can be important when trying to determine how vpn works diagrammatically. When considering how vpn works diagram, it is not only important to visualize the data flow but also to understand that the specific protocols used influence the speed and reliability of that data flow. Furthermore, it’s essential to remember that the protocol is a foundational element of a VPN service, which is one of the reasons to choose wisely when selecting a VPN.
Troubleshooting Common VPN Connection Problems
When utilizing a VPN, users might occasionally face difficulties such as sluggish speeds, inconsistent connections, or inability to access certain websites. Addressing these challenges proactively can enhance the overall VPN experience. For instance, slow speeds can often be attributed to the physical distance between the user and the chosen VPN server. To mitigate this, selecting a server closer to one’s actual location or the destination server can improve speed. It’s also important to understand how the chosen protocol might impact performance; some protocols might prioritize security over speed, which can affect the user’s browsing experience. Experimenting with different protocols, if the VPN client allows, can sometimes help to find a better balance. The stability of a VPN connection is also a crucial aspect, and dropped connections can stem from various reasons, including network interferences. In such instances, restarting the VPN software or trying a different server can be effective. Furthermore, difficulties accessing specific websites may arise due to VPN blocking measures implemented by the website. In this case, switching to a different server, or adjusting the VPN protocol, can be a viable strategy. Understanding that the functionality of a VPN is tied to all of these elements, and knowing what actions to take when something fails, is crucial. The underlying concept of how a VPN works diagram can also be useful to understand the connection process and identify where the problem might be occurring.
Another common challenge is resolving DNS leaks, which expose the user’s true IP address despite using a VPN. Checking the VPN software settings to ensure DNS leak protection is enabled, can safeguard the user’s anonymity. If these problems persist, it is also important to check the VPN’s software for updates to ensure compatibility with the operating system. Firewall or antivirus software may sometimes interfere with VPN connections, so temporarily disabling them (if safe to do so) can help to determine if they are the source of the problem. If the issue persists after all these troubleshooting steps, contacting the VPN provider’s customer support can be a good solution. These providers often have detailed guides and expert staff to assist with resolving any problems the user might encounter, and they can sometimes provide specialized solutions, or even specific insights, based on the user’s particular situation. It is important to note that the complexity of how a vpn works diagram can sometimes be a reason for a problem, making it essential to approach troubleshooting logically and methodically to ensure optimal performance and security.
Choosing a Reputable VPN Service: Safeguarding Your Online Privacy
Selecting a trustworthy VPN service is paramount to ensure your online activities remain private and secure, especially after understanding how a vpn works diagram. The market offers numerous VPN providers, each with its own set of features and promises. When evaluating a VPN service, begin by examining its privacy policy. A transparent policy should clearly state how the provider handles user data, with a preference for services that commit to no-logging practices. This commitment means the VPN does not retain any records of your browsing activities, providing an added layer of anonymity. The geographical distribution of the VPN’s server network is another crucial factor. A wide array of servers in numerous locations not only offers more choices for bypassing geo-restrictions but also enhances connection speeds by allowing users to select servers closer to their actual or desired location. The speed and stability of a VPN connection are heavily dependent on server quality and the protocols used. Opt for providers with fast, dependable servers and those offering a variety of secure protocols to meet different use cases.
Pricing models also warrant careful consideration. While some providers offer free VPN services, these often come with limitations such as speed caps, data limits, or may even involve selling user data, which undermines the primary goal of a VPN. Thus, paid VPN services tend to offer greater reliability, security, and privacy. Look for services that offer a free trial period or money-back guarantees to test their performance. User reviews provide invaluable insight into the real-world performance of VPN services. Analyze feedback on platforms such as technology blogs and user forums. Pay particular attention to comments about customer service, ease of use, and the consistency of performance. A well-regarded VPN provider will exhibit not only technical proficiency but also proactive and helpful customer support. In the process of visualizing how a vpn works diagram, remember to consider that several VPN services, like ExpressVPN, NordVPN, and Surfshark, are often recommended for their reliability and feature sets. However, it is always prudent to do your independent research before subscribing to any VPN service, ensuring that it aligns with your specific needs and priorities.
The understanding of how a vpn works diagram is crucial, but practical application through a trustworthy service is what will guarantee online security. This means the user will know the process of how data is encrypted and transferred, and at the same time the responsibility to choose wisely when opting for a VPN provider is part of this secure process. It is recommended that all the previous aspects are taken into account to avoid any vulnerabilities and to have a secure and private experience.