Understanding AWS Service Control Policies (SCPs)
AWS Service Control Policies (SCPs) are a cornerstone of effective cloud security management, providing a centralized approach to managing permissions within an AWS Organization. At their core, SCPs function as guardrails, defining the maximum permissions that can be granted to accounts within an organization. They don’t grant permissions; rather, they restrict them, ensuring that even if an IAM user or role has permissions granted, those actions can be blocked by an SCP. These policies are crucial for establishing a strong security posture, enabling organizations to enforce consistent security standards across multiple AWS accounts. The implementation of effective aws scp best practices means that organizations can gain a significant advantage, enhancing their security and compliance measures. For instance, an organization might utilize an SCP to restrict the creation of resources in certain AWS regions, or to prevent the use of specific services. This high-level control is paramount for maintaining compliance with industry regulations and internal security policies, ensuring that all accounts within the organization adhere to a common security baseline. Implementing aws scp best practices helps prevent accidental or malicious actions that could compromise security, making it an essential component of any robust AWS security strategy. The benefits of implementing them include centralized control, improved security posture, and streamlined compliance adherence.
Think of SCPs like a gatekeeper for your AWS environment. While individual IAM policies might give a user the “key” to do something, an SCP can lock the gate, preventing that action from taking place. This is particularly useful for multi-account AWS environments managed using AWS Organizations, where consistent security policies are vital. Consider a scenario where you want to prevent any user from accidentally deleting critical data in your production account. You might have IAM policies which allow deletion of data, but a well-configured SCP can restrict the ‘Delete’ actions on specific services in the production account. This demonstrates the power of SCPs in limiting the blast radius of misconfigured IAM policies or compromised credentials, reducing potential security risks and helping implement aws scp best practices. The goal of these policies isn’t to create complexity but to create a simple, effective way to enforce security constraints at a higher level, complementing IAM policies. The ability to restrict access at an organizational level adds a critical layer of defense.
How to Create and Implement Effective AWS SCPs
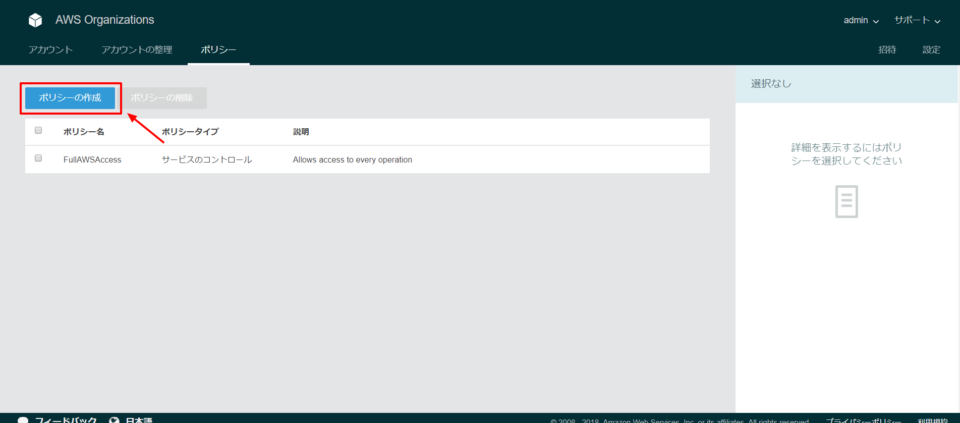
Creating and implementing effective AWS Service Control Policies (SCPs) is crucial for maintaining a strong security posture within your AWS environment. This process involves defining the permissions boundaries for your AWS accounts, ensuring that users and roles cannot perform actions outside of those boundaries. There are two primary methods for creating and deploying SCPs: using the AWS Management Console or the AWS Command Line Interface (CLI). To begin with the console, navigate to the AWS Organizations service. Select the specific organizational unit (OU) or individual account where you wish to apply the policy. Then, proceed to the “Policies” tab and choose “Create policy”. You will be presented with the option to visually construct the policy or directly input a JSON policy document. A practical example is creating an SCP that restricts the ability to launch EC2 instances in specific regions. In the JSON format this may look something like this: { "Version": "2012-10-17", "Statement": [{ "Effect": "Deny", "Action": "ec2:RunInstances", "Resource": "*", "Condition": { "StringNotEquals": { "ec2:Region": ["us-east-1", "us-west-2"] } } }] }. This policy, when applied, will prevent any user or role within that account from launching instances outside of the allowed regions. Remember that a key aspect of effective aws scp best practices is to start with a deny-by-default approach, and then incrementally allow necessary permissions.
When using the AWS CLI to create SCPs, the process involves using commands to create and attach policies. The aws organizations create-policy command is used to initially define the policy, followed by the aws organizations attach-policy command to link the policy to an organizational unit or a specific account. This command line interface method provides more flexibility and allows for automation and easier version control. For instance, to create a similar policy using the CLI, you would first save the policy document to a file (e.g., restrict_regions_policy.json), and then use the command: aws organizations create-policy --content file://restrict_regions_policy.json --name "RestrictRegions" --description "Deny EC2 instance launches outside of us-east-1 and us-west-2." --type "SERVICE_CONTROL_POLICY". Afterwards, you would obtain the policy ID and use: aws organizations attach-policy --policy-id , where the target ID refers to the OU or account to which you’re applying the policy. Effective aws scp best practices also include thoroughly testing any newly created policies to avoid unintended service disruptions or access restrictions. Always opt for a least privilege approach, granting only the necessary permissions to users and services to ensure optimal security and compliance.
It is important to understand different policy types that can be implemented. While the example above shows restriction of a service, other policy types include managing IAM permissions, restricting service access, or enforcing specific compliance requirements. Each of these policy types plays a different role in your security architecture. Furthermore, when applying any policy, it’s fundamental to review the policy impact, ensuring it doesn’t block authorized users and services from performing needed tasks. The key to successful implementation of aws scp best practices lies in diligent planning, detailed policy construction, and thorough impact analysis. This approach helps you prevent common errors and maintain optimal security with the least disruption. The use of version control for these policies is highly recommended.
Structuring Your SCPs for Maximum Impact
Effective management of aws scp best practices requires a well-defined organizational structure. The concept of hierarchical policy application is fundamental; policies are applied at the root level of an AWS Organization, and then cascaded down to organizational units (OUs) and individual accounts. This allows for centralized control while enabling customization at lower levels. For instance, a broad policy to restrict access to certain regions might be applied at the root level, while more specific policies for development or production environments can be enforced at the respective OU level. Employing a layered approach with aws scp best practices ensures that the most stringent security controls are always in effect while accommodating unique business requirements. Furthermore, the chosen naming conventions should be clear, descriptive, and consistently applied. For example, a policy restricting access to S3 could be named `scp-s3-access-restriction-ou-dev` or `scp-s3-access-restriction-account-prod`, clearly indicating its purpose, scope and organizational context. Documenting the purpose and implementation logic of each policy within the policy itself or in a separate document becomes vital for future auditing, troubleshooting, and updates. This practice will avoid any ambiguity and ensures that the reasoning behind each policy is easily understood. Consider it essential to integrate documentation as a core element of managing aws scp best practices.
A well-structured policy hierarchy directly impacts the ease of management and effectiveness of security controls. For example, a top-level organizational unit could have policies regarding compliance with legal requirements, while lower levels in the structure have more specialized policies restricting access to services that are not approved for that specific team or department. Imagine an organization with a Sales OU, an Engineering OU, and a Marketing OU. Each would have specific needs and therefore different access restrictions that can be configured for each one of them. The structure itself should mirror the organizational chart which would make applying and maintaining policies more straightforward. Documentation should include details like the objective of the policy, the specific services affected, any exceptions made, and the date the policy was last modified. This structured approach to aws scp best practices ensures that policies are easily understood, updated, and remain relevant. Without a clear naming convention and meticulous documentation, managing a growing number of SCPs would quickly become complex and prone to errors.
The creation and maintenance of policy hierarchies can also be simplified by using Infrastructure as Code (IaC) tools, like AWS CloudFormation or Terraform. IaC tools allow you to define and manage infrastructure including your aws scp best practices, using code, thus facilitating version control and repeatable deployments. When using IaC, it is essential to include all documentation with the code itself to maintain a consistent state for your infrastructure. This not only streamlines policy deployment but also ensures consistency across your organization. This strategy will save time and resources while also improving the overall reliability and security of the AWS environment. Overall, focusing on structure, naming, and documentation provides a significant improvement in the effectiveness of your aws scp best practices implementation.
Leveraging AWS Organizations for SCP Management
AWS Organizations offers a streamlined method for managing multiple AWS accounts, particularly beneficial for enterprises seeking centralized control. This service allows the application of Service Control Policies (SCPs) at the organizational level, guaranteeing that consistent security policies are enforced across all member accounts. This approach drastically reduces the administrative overhead that would be necessary if managing SCPs individually in each account. When using AWS Organizations for aws scp best practices, policies can be defined and deployed once at the root or organizational unit (OU) level, automatically applying to all accounts under that structure. This eliminates the need for repetitive configuration, ensuring a uniform security posture across the organization. The hierarchical nature of OUs enables customized SCPs to be applied based on the specific needs of different parts of the business. For example, a development OU might have slightly more relaxed permissions compared to a production OU, while still maintaining fundamental security guardrails defined at the root level. Such a setup is essential for effectively implementing aws scp best practices across a large AWS infrastructure.
The advantages of using AWS Organizations for SCP management extend beyond simplified deployment. It provides enhanced visibility into policy enforcement, enabling administrators to track which SCPs are in effect for each account. This visibility helps identify any non-compliant behavior and facilitate timely remediation. Centralized management also provides a more consistent auditing process. In contrast, managing SCPs on an account-by-account basis leads to inconsistencies, policy drift, and can create security gaps. With AWS Organizations, the control remains with the central team, and local account administrators are restricted from modifying or bypassing centrally defined policies. Moreover, aws scp best practices dictate leveraging AWS Organizations to simplify and accelerate changes or updates. Modifying a policy at the organization level instantly propagates changes down to all relevant accounts, facilitating agile responses to evolving security requirements. Therefore, adoption of AWS Organizations for aws scp best practices is crucial for enterprises managing numerous accounts, as it promotes security consistency, enhances visibility, reduces administrative overhead, and aids in agile security management. The ability to create a hierarchical structure allows for finely tuned security controls that cater to the specific needs of different teams or workloads within the enterprise, ensuring an effective aws scp best practices implementation.
Integrating SCPs with Other AWS Security Services for Enhanced Protection
AWS Service Control Policies (SCPs), a cornerstone of effective aws scp best practices, don’t operate in isolation. Their true power emerges when integrated with other AWS security services. IAM roles, for instance, enable granular permission control within accounts, aligning perfectly with SCPs’ centralized restriction capabilities. By defining narrow IAM roles and supplementing them with SCPs, organizations achieve a layered security approach, minimizing the blast radius of potential breaches. Identity federation extends this control beyond individual accounts, allowing organizations to manage access for users and applications from external identity providers while still maintaining the restrictions set by SCPs. This layered approach is a vital aspect of aws scp best practices.
AWS Config and CloudTrail provide essential monitoring and auditing capabilities that complement SCPs. AWS Config allows continuous monitoring of resource configurations, ensuring that they adhere to the policies defined by SCPs. Any deviation triggers alerts, enabling prompt remediation. CloudTrail, on the other hand, logs all API calls made within the AWS environment, offering a detailed audit trail that aids in investigating security incidents and compliance audits. By integrating SCPs with these services, organizations gain comprehensive visibility into their security posture, making proactive security management and incident response significantly more efficient. This integrated approach to security is crucial for effective aws scp best practices. The synergistic effect of these services, especially when considering aspects of aws scp best practices, significantly enhances the overall security posture and compliance efforts.
Implementing robust aws scp best practices involves leveraging the combined strengths of these services. For example, imagine an organization using SCPs to restrict access to sensitive S3 buckets. By integrating this with AWS Config, the organization can receive alerts if any changes are made to the bucket’s permissions that violate the SCPs. CloudTrail then provides a detailed log of all activities related to the bucket, allowing security teams to quickly identify and respond to suspicious behavior. This integrated security approach is far more effective than relying on SCPs alone and represents a significant advancement in aws scp best practices. The combination of these services allows for a proactive and reactive security model that consistently strengthens the organization’s overall security stance. This holistic perspective is essential for maintaining a robust and adaptable security posture in line with aws scp best practices.
Addressing Common AWS SCP Implementation Challenges
Implementing AWS Service Control Policies (SCPs) effectively requires careful planning and execution. One common challenge is encountering policy conflicts. This occurs when multiple SCPs are applied to the same account or organizational unit (OU), and their rules contradict each other. For example, one SCP might allow access to a specific AWS service, while another prohibits it. Resolving these conflicts requires careful analysis of the conflicting policies, prioritizing policies based on their importance, and modifying the policies to ensure they work harmoniously. Best practice dictates thorough testing of SCPs in a non-production environment before deploying them to production accounts to minimize disruption. Understanding the precedence order of policies applied is crucial in such scenarios to properly troubleshoot and debug. Following aws scp best practices will dramatically reduce conflicts.
Another common issue is encountering unexpected service restrictions. This often happens when a policy is overly restrictive or hasn’t accounted for all the necessary permissions required by existing applications. Before implementing new SCPs or modifying existing ones, it is vital to perform a comprehensive impact assessment. This involves identifying all the AWS services and resources used by your applications and ensuring that the SCPs do not inadvertently block access to them. Using tools like AWS Config and CloudTrail can help identify resource usage patterns, guiding the creation of precise and less restrictive SCPs. When employing aws scp best practices, one can avoid many of these issues.
The impact on existing applications is another important consideration. Deploying SCPs can sometimes break existing workflows or processes if the policies are not carefully crafted. This highlights the need for thorough testing and validation in a controlled environment before deploying them to production. It is strongly recommended to start with minimally restrictive policies and incrementally add more restrictions only after fully testing their impact. Implementing a robust change management process for SCPs, similar to other infrastructure changes, is crucial. Regularly reviewing and updating your policies according to aws scp best practices, including adding detailed documentation, minimizes the risks of unforeseen disruptions. Properly addressing these challenges through careful planning, thorough testing, and a strong change management process ensures that AWS SCPs enhance security without hindering operational efficiency.
Best Practices for Regular SCP Review and Updates
Maintaining effective security through AWS Service Control Policies (SCPs) requires a commitment to regular review and updates. The dynamic nature of cloud environments, evolving security threats, and the continuous introduction of new AWS services necessitate a proactive approach to policy management. A static set of SCPs can quickly become ineffective or, worse, create unforeseen roadblocks in operations. Therefore, it is imperative to establish a schedule for auditing and updating these critical security controls. This ensures that the aws scp best practices are consistently applied and adapted to the organization’s current needs and risk posture. Regularly scheduled reviews allow identification of outdated policies, potential conflicts, and opportunities to further strengthen security. Ignoring the need for updates leaves an organization vulnerable to emerging threats and potentially unable to fully utilize new AWS services. The goal is to ensure policies are relevant and effective at all times.
The process of reviewing and updating SCPs should be a collaborative effort, involving stakeholders from security, operations, and development teams. This ensures that changes are aligned with both security requirements and business needs. The review process should encompass several key areas, including analyzing the effectiveness of existing policies, identifying policy conflicts, and evaluating the impact of recent AWS service updates or organizational changes. Documentation plays a critical role in this process. All changes should be properly documented, including the reasons for the changes and the potential impact of such adjustments. Furthermore, the team should have a system in place to test policy changes in a non-production environment before applying them to live systems. This allows the detection of unintended consequences, helping avoid service disruptions. A recommended schedule for regular audits should be aligned with the pace of change within the organization. It might be beneficial to perform in depth reviews quarterly, in addition to smaller adjustments whenever a major security concern, service update, or change in compliance framework arises. Following aws scp best practices means being proactive, not reactive.
To facilitate efficient and effective policy updates, consider implementing version control for your SCPs, similar to how software development teams manage their code. This allows tracking of changes, reverting to previous versions if necessary, and facilitates understanding of policy evolution. Also, leverage AWS tools such as AWS Config to monitor compliance with your established policies. This helps with the identification of deviations or unexpected behavior, prompting investigation and necessary modifications to the SCPs. Regularly review AWS security advisories and adapt the SCPs to address identified vulnerabilities. Implementing this approach contributes to a well-rounded security strategy, ensuring policies are continuously updated to meet the organization’s evolving needs. This proactive approach to AWS SCP best practices enhances the security posture and allows the organization to operate with confidence in their cloud environment.
Enhancing Security Beyond SCPs: A Holistic Approach
While AWS Service Control Policies (SCPs) are a cornerstone of a robust AWS security strategy, it is crucial to recognize that they are one component of a much larger security ecosystem. Achieving true security requires a multifaceted approach that extends beyond the enforcement capabilities of SCPs. Consider the broader landscape, encompassing other vital security measures. Vulnerability management, for example, plays an essential role in identifying and remediating potential weaknesses within your AWS infrastructure, which complements the access controls established by SCPs. Regular security assessments, including penetration testing, can reveal security gaps that might not be evident through policy-based approaches alone. These assessments help validate the effectiveness of your entire security architecture, which includes but isn’t limited to, your aws scp best practices. Security Information and Event Management (SIEM) systems further augment security by providing real-time threat detection, monitoring for anomalous behavior, and enabling prompt incident response. Integrating log data from diverse sources, SIEM systems provide a comprehensive view of security events within your AWS environment, enhancing visibility and control.
Effective implementation of aws scp best practices should go hand-in-hand with careful consideration of identity and access management (IAM). IAM roles and policies provide granular control over user and application permissions within individual accounts, and when combined with SCPs at the organizational level, it creates a powerful security layer. Identity federation, which manages access through external identity providers, can extend the benefits of centralized control to users beyond the boundaries of your AWS accounts. A well-defined patching strategy is also crucial for minimizing vulnerabilities, ensuring that operating systems and applications are always up to date with the latest security patches. Continuous security awareness programs are vital to educate users about security threats and best practices. Ultimately, it must be underscored that while following aws scp best practices are essential, it is the cohesive interplay of all these elements that will determine the overall effectiveness of the security posture. To maximize AWS security effectiveness, an active, well-rounded strategy is critical.
The synergistic impact of multiple security layers can provide a much stronger defense. For instance, while SCPs can restrict service access, vulnerability management helps to ensure the security of those services being used. IAM and identity federation establish user access controls, and the SIEM system monitors for any irregular activity from these users. This layered approach minimizes the risk of a single point of failure and improves the security posture against potential threats, providing a flexible and comprehensive defense strategy. Therefore, while aws scp best practices contribute considerably to a security strategy, they must be viewed as an integral part of a much broader security framework, where each component enhances and supports the others.