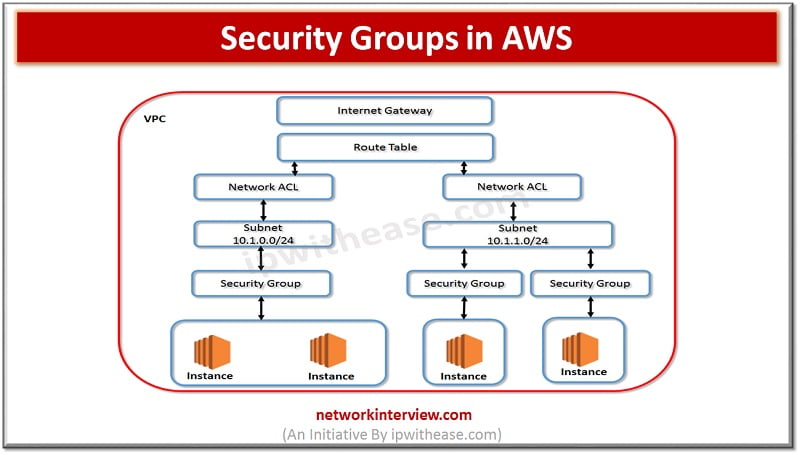
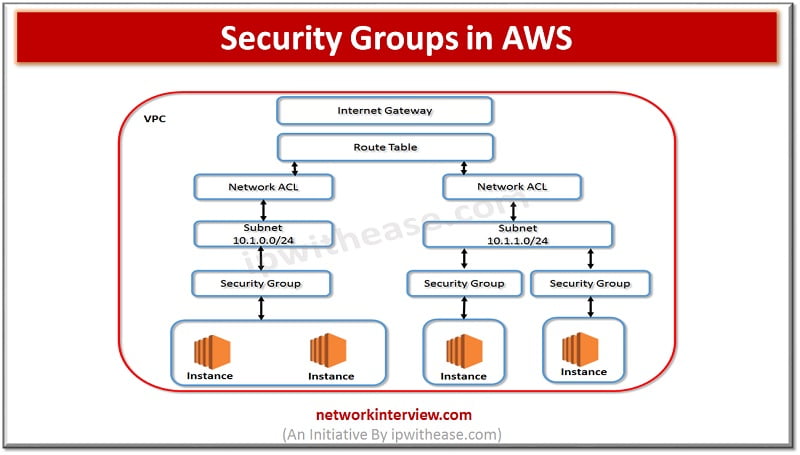
What is a Network Security Group?
A network security group (NSG) is a virtual firewall that controls inbound and outbound traffic to virtual machines (VMs) and other resources in a cloud environment. NSGs are an essential component of network security, providing a layer of protection against unauthorized access and malicious traffic. By defining security rules, network administrators can specify which traffic is allowed or denied based on various criteria, such as source and destination IP addresses, port numbers, and protocols.
NSGs are flexible and scalable, allowing administrators to create and apply security policies to individual resources or entire subnets. They can also be associated with network interfaces or subnets, enabling administrators to define security rules at different levels of the network. This granular control over network traffic is crucial for maintaining the security and integrity of cloud-based applications and services.
In addition to controlling traffic flow, NSGs also provide audit logs and security alerts, enabling administrators to monitor network activity and detect potential security threats. By integrating NSGs with other security tools and services, organizations can build a comprehensive defense strategy that protects their cloud infrastructure from a wide range of threats.
In summary, network security groups are a fundamental building block of network security in cloud environments. By providing fine-grained control over network traffic, NSGs enable administrators to enforce security policies, prevent unauthorized access, and detect potential threats. Understanding the role and functionality of NSGs is essential for any organization looking to deploy and manage secure cloud-based applications and services.
Key Components of a Network Security Group
A network security group (NSG) is a fundamental component of network security in cloud environments. At its core, an NSG consists of security rules that define how traffic is allowed or denied between resources in a virtual network. These security rules are the primary mechanism for controlling inbound and outbound traffic to virtual machines (VMs) and other network resources.
Security rules are the building blocks of NSGs. Each rule consists of several components, including the source and destination IP addresses, port numbers, protocols, and action (allow or deny). By defining these rules, administrators can specify which traffic is allowed or denied based on specific criteria. For example, an administrator might create a rule that allows traffic from a specific IP address to a specific port on a VM, while denying all other traffic.
NSGs also include default security group rules, which are predefined rules that apply to all NSGs in a virtual network. These rules allow or deny traffic based on common scenarios, such as allowing inbound traffic from anywhere to Remote Desktop Protocol (RDP) or Secure Shell (SSH) ports. Administrators can modify or delete these default rules to meet their specific security requirements.
In addition to security rules and default security group rules, NSGs also include other components, such as inbound and outbound traffic counters, which track the amount of traffic that matches each rule. This information can be used to monitor network activity and detect potential security threats. Administrators can also associate NSGs with network interfaces or subnets, enabling them to define security policies at different levels of the network.
In summary, network security groups are a crucial component of network security in cloud environments. By defining security rules and default security group rules, administrators can control inbound and outbound traffic to virtual machines and other network resources. Understanding the key components of NSGs is essential for any organization looking to deploy and manage secure cloud-based applications and services.
Benefits of Using Network Security Groups
Network security groups (NSGs) offer several benefits to organizations looking to enhance their network security in cloud environments. By providing fine-grained control over network traffic, NSGs enable administrators to implement security policies that are tailored to their specific needs. Here are some of the key benefits of using NSGs:
- Improved security: NSGs provide an additional layer of security to virtual machines (VMs) and other network resources. By defining security rules that allow or deny traffic based on specific criteria, administrators can prevent unauthorized access and mitigate the risk of cyber attacks.
- Simplified management: NSGs are easy to configure and manage, enabling administrators to define security policies for individual resources or entire subnets. This granular control over network traffic simplifies management and reduces the risk of misconfigurations.
- Flexibility: NSGs are highly flexible, allowing administrators to define security policies that are tailored to their specific needs. By defining security rules based on various criteria, such as source and destination IP addresses, port numbers, and protocols, administrators can implement security policies that are aligned with their business requirements.
- Scalability: NSGs are highly scalable, enabling administrators to apply security policies to large numbers of resources in a cloud environment. This scalability is essential for organizations that need to manage large and complex network environments.
- Auditability: NSGs provide audit logs and security alerts, enabling administrators to monitor network activity and detect potential security threats. By integrating NSGs with other security tools and services, organizations can build a comprehensive defense strategy that protects their cloud infrastructure from a wide range of threats.
NSGs can be used in a variety of scenarios to enhance network security. For example, an administrator might create an NSG that allows traffic from a specific IP address to a specific port on a VM, while denying all other traffic. This approach can be used to restrict access to sensitive resources, such as databases or application servers, and prevent unauthorized access.
In summary, network security groups offer several benefits to organizations looking to enhance their network security in cloud environments. By providing fine-grained control over network traffic, NSGs enable administrators to implement security policies that are tailored to their specific needs. Understanding the benefits of NSGs is essential for any organization looking to deploy and manage secure cloud-based applications and services.
How to Configure a Network Security Group
Configuring a network security group (NSG) is a straightforward process that involves several steps. By following these steps, administrators can define security policies that control inbound and outbound traffic to virtual machines (VMs) and other network resources. Here’s a step-by-step guide to configuring an NSG:
- Create a new NSG: In the cloud console, navigate to the NSG section and create a new NSG. Provide a name and description for the NSG, and select the subscription and resource group where it will be created.
- Create security rules: Once the NSG is created, navigate to the Security rules section and create new rules. Define the source and destination IP addresses, port numbers, and protocols for each rule. Specify whether the rule allows or denies traffic, and set the priority for each rule.
- Associate the NSG with a network interface: In the network interface section, select the network interface that you want to associate with the NSG. Click on the Network security group dropdown and select the NSG that you created in step 1.
- Test the configuration: Once the NSG is associated with the network interface, test the configuration by sending traffic to the VM or network resource. Verify that the traffic is allowed or denied based on the security rules that you defined in step 2.
Here are some tips and best practices for configuring NSGs effectively:
- Follow the principle of least privilege: Only allow traffic that is necessary for the operation of the VM or network resource. Deny all other traffic.
- Segment networks: Divide the network into smaller segments to reduce the attack surface and improve security.
- Regularly review security rules: Regularly review the security rules to ensure that they are up-to-date and aligned with the organization’s security policies.
- Use default security group rules: Use the default security group rules as a starting point for defining security policies. These rules provide a baseline level of security that can be customized to meet specific needs.
- Troubleshoot issues: If issues arise with network traffic, use the NSG audit logs and security alerts to troubleshoot the problem. These logs provide detailed information about the traffic that is allowed or denied, enabling administrators to identify and resolve issues quickly.
In summary, configuring a network security group is a straightforward process that involves creating security rules, associating the NSG with a network interface, and testing the configuration. By following best practices and tips, administrators can define security policies that improve network security and reduce the risk of cyber attacks. Understanding how to configure NSGs is essential for any organization looking to deploy and manage secure cloud-based applications and services.
Best Practices for Using Network Security Groups
Network security groups (NSGs) are a powerful tool for controlling network traffic in cloud environments. However, to use NSGs effectively, it’s essential to follow best practices and tips. Here are some best practices for using NSGs:
- Follow the principle of least privilege: Only allow traffic that is necessary for the operation of the virtual machine (VM) or network resource. Deny all other traffic. This principle reduces the attack surface and improves security.
- Segment networks: Divide the network into smaller segments to reduce the attack surface and improve security. NSGs can be used to control traffic between segments, ensuring that only authorized traffic is allowed.
- Regularly review security rules: Regularly review the security rules to ensure that they are up-to-date and aligned with the organization’s security policies. Remove any unnecessary rules and update rules that are no longer relevant.
- Use default security group rules: Use the default security group rules as a starting point for defining security policies. These rules provide a baseline level of security that can be customized to meet specific needs.
- Troubleshoot issues: If issues arise with network traffic, use the NSG audit logs and security alerts to troubleshoot the problem. These logs provide detailed information about the traffic that is allowed or denied, enabling administrators to identify and resolve issues quickly.
Here are some common mistakes to avoid when using NSGs:
- Allowing too much traffic: Allowing too much traffic increases the attack surface and reduces security. Ensure that only necessary traffic is allowed, and deny all other traffic.
- Not reviewing security rules regularly: Not reviewing security rules regularly can lead to outdated rules that are no longer relevant or necessary. Regularly reviewing security rules ensures that they are up-to-date and aligned with the organization’s security policies.
- Not segmenting networks: Not segmenting networks can increase the attack surface and reduce security. Segmenting networks ensures that only authorized traffic is allowed, reducing the risk of cyber attacks.
- Not testing the configuration: Not testing the configuration can lead to misconfigured NSGs that do not provide the desired level of security. Testing the configuration ensures that the NSGs are working as intended and providing the desired level of security.
In summary, following best practices and tips is essential for using network security groups effectively. Best practices include following the principle of least privilege, segmenting networks, regularly reviewing security rules, using default security group rules, and troubleshooting issues. Common mistakes to avoid include allowing too much traffic, not reviewing security rules regularly, not segmenting networks, and not testing the configuration. By following these best practices and avoiding common mistakes, administrators can define security policies that improve network security and reduce the risk of cyber attacks. Understanding best practices for using NSGs is essential for any organization looking to deploy and manage secure cloud-based applications and services.
Network Security Group vs. Firewall: What’s the Difference?
Network security groups (NSGs) and firewalls are both critical components of network security, but they serve different purposes. Understanding the differences between NSGs and firewalls is essential for defining a comprehensive network security strategy.
What is a Firewall?
A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on predetermined security rules. A firewall can be hardware-based or software-based and is typically placed at the network’s edge to protect the network from external threats.
What is a Network Security Group?
A network security group (NSG) is a virtual firewall that controls inbound and outbound traffic to virtual machines (VMs) and other resources in a cloud environment. NSGs are configured with security rules that define which traffic is allowed or denied based on various criteria, such as source and destination IP addresses, port numbers, and protocols.
Key Differences Between NSGs and Firewalls
- Placement: Firewalls are typically placed at the network’s edge, while NSGs are placed closer to the resources they protect, such as VMs and other network resources.
- Scope: Firewalls are designed to protect the entire network, while NSGs are designed to protect individual VMs and network resources.
- Configuration: Firewalls are typically configured with more complex rules that require advanced knowledge of network security, while NSGs are easier to configure and manage, with simpler rules that are based on specific criteria.
- Performance: NSGs are designed to provide high performance and low latency, making them ideal for cloud environments where resources are highly dynamic and scalable.
When to Use Each Technology
NSGs and firewalls serve different purposes, and organizations should use them together to provide comprehensive network security. NSGs should be used to control traffic to individual VMs and network resources, while firewalls should be used to protect the entire network from external threats.
For example, an organization might use an NSG to control traffic to a specific VM that hosts a critical application, while using a firewall to protect the entire network from external threats, such as malware and hacking attempts. By using both technologies together, organizations can define a comprehensive network security strategy that provides the necessary level of protection for their cloud-based resources.
Conclusion
Network security groups (NSGs) and firewalls are both critical components of network security, but they serve different purposes. Understanding the differences between NSGs and firewalls is essential for defining a comprehensive network security strategy. NSGs should be used to control traffic to individual VMs and network resources, while firewalls should be used to protect the entire network from external threats. By using both technologies together, organizations can define a comprehensive network security strategy that provides the necessary level of protection for their cloud-based resources.
Popular Network Security Group Solutions
Network security groups (NSGs) are an essential component of network security in cloud environments. There are several popular NSG solutions available on the market, each with its own features, pricing, and performance. Here are some of the most popular NSG solutions:
Azure Network Security Group
Azure Network Security Group (NSG) is a cloud-based network security solution that provides fine-grained control over inbound and outbound traffic to virtual machines (VMs) and other resources in an Azure environment. Azure NSGs are easy to configure and manage, with simple rules that are based on specific criteria, such as source and destination IP addresses, port numbers, and protocols. Azure NSGs also provide advanced security features, such as just-in-time access, which allows administrators to grant access to VMs only when it is needed, and network object tags, which enable administrators to apply security rules to groups of resources.
AWS Security Group
AWS Security Group is a cloud-based network security solution that provides fine-grained control over inbound and outbound traffic to virtual machines (EC2 instances) and other resources in an AWS environment. AWS Security Groups are easy to configure and manage, with simple rules that are based on specific criteria, such as source and destination IP addresses, port numbers, and protocols. AWS Security Groups also provide advanced security features, such as security group ingress rules, which allow administrators to specify the source of inbound traffic, and security group egress rules, which allow administrators to specify the destination of outbound traffic.
Google Cloud Security Group
Google Cloud Security Group (also known as VPC firewall rules) is a cloud-based network security solution that provides fine-grained control over inbound and outbound traffic to virtual machines (VM instances) and other resources in a Google Cloud environment. Google Cloud Security Groups are easy to configure and manage, with simple rules that are based on specific criteria, such as source and destination IP addresses, port numbers, and protocols. Google Cloud Security Groups also provide advanced security features, such as priority-based rules, which allow administrators to specify the order in which rules are applied, and target tags, which enable administrators to apply security rules to groups of resources.
Recommendations
When selecting a network security group solution, organizations should consider several factors, such as the size and complexity of their cloud environment, their security requirements, and their budget. For small to medium-sized organizations with simple cloud environments, Azure NSG or AWS Security Group may be a good fit. For larger organizations with more complex cloud environments, Google Cloud Security Group may be a better choice due to its advanced security features and scalability.
Conclusion
Network security groups (NSGs) are an essential component of network security in cloud environments. There are several popular NSG solutions available on the market, each with its own features, pricing, and performance. When selecting an NSG solution, organizations should consider several factors, such as the size and complexity of their cloud environment, their security requirements, and their budget. By selecting the right NSG solution, organizations can define a comprehensive network security strategy that provides the necessary level of protection for their cloud-based resources.
Future Trends in Network Security Groups
Network security groups (NSGs) have become an essential component of network security in cloud environments. As cloud computing continues to evolve, NSGs are also expected to undergo significant changes. Here are some of the future trends and developments in NSGs and how they are likely to impact network security:
Automation
Automation is becoming increasingly important in network security, and NSGs are no exception. With the help of automation, organizations can reduce the time and effort required to manage NSGs, minimize human errors, and improve network security. In the future, we can expect to see more advanced automation capabilities in NSGs, such as automated security rule creation, automated network segmentation, and automated threat detection and response.
Machine Learning
Machine learning (ML) is another area where NSGs are expected to see significant advancements. ML algorithms can analyze large amounts of network traffic data and identify patterns and anomalies that might indicate a security threat. By incorporating ML into NSGs, organizations can improve their threat detection capabilities, reduce false positives, and automate threat response. In the future, we can expect to see more NSG solutions that leverage ML to enhance network security.
Zero Trust Security
Zero trust security is a security model that assumes that any user or device trying to access a network is untrusted until proven otherwise. This model is becoming increasingly popular in cloud environments, where traditional perimeter-based security models are no longer effective. NSGs can play a critical role in implementing zero trust security by controlling access to network resources based on user identity, device identity, and other contextual factors. In the future, we can expect to see more NSG solutions that support zero trust security and help organizations implement this model in their cloud environments.
Recommendations
To stay ahead of the curve in network security, organizations should consider the following recommendations:
- Invest in NSG solutions that support automation and ML to improve threat detection and response capabilities.
- Implement zero trust security models to reduce the risk of security breaches in cloud environments.
- Regularly review and update NSG rules to ensure they are aligned with the organization’s security policies and requirements.
- Monitor NSG performance and make adjustments as needed to ensure optimal network security and performance.
Conclusion
Network security groups (NSGs) are an essential component of network security in cloud environments. As cloud computing continues to evolve, NSGs are also expected to undergo significant changes, such as automation, machine learning, and zero trust security. By staying informed about these trends and implementing the right NSG solutions, organizations can improve their network security, reduce the risk of security breaches, and stay ahead of the curve in cloud security.