What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) is a modern approach to managing infrastructure in cloud-based deployments. IaC involves writing configuration files using a declarative language, which can be version-controlled, tested, and deployed automatically. This approach simplifies infrastructure management, increases efficiency, and reduces errors compared to traditional manual methods. By defining infrastructure as code, organizations can ensure consistent and reliable deployments, improve security and compliance, and accelerate the delivery of applications and services.
Terraform is a popular IaC tool that enables developers and infrastructure professionals to define, provision, and manage infrastructure resources using a simple and intuitive syntax. By using Terraform, teams can automate infrastructure provisioning, reduce manual errors, and ensure consistent and reliable deployments across different cloud providers and environments.
Introducing Terraform: A Popular IaC Tool
Terraform is an open-source Infrastructure as Code (IaC) tool developed by HashiCorp. It enables developers and infrastructure professionals to define, provision, and manage infrastructure resources using a simple and intuitive syntax. Terraform supports multiple cloud providers, including AWS, Azure, Google Cloud, and many others, making it a versatile and flexible tool for managing cloud-based infrastructure.
Terraform’s unique selling points include its agentless architecture, which enables it to manage infrastructure resources without requiring any software installation on the target machines. Terraform also supports a declarative configuration language, which allows users to define the desired state of their infrastructure resources, and automatically generates the necessary steps to achieve that state. This approach simplifies infrastructure management, reduces errors, and ensures consistent and reliable deployments.
Terraform’s features include resource graph creation, which enables users to visualize the dependencies between their infrastructure resources, and automatic resource updates, which ensures that the infrastructure resources are always in the desired state. Terraform also supports a modular architecture, which enables users to break down their infrastructure configurations into smaller, reusable modules, making it easier to manage and maintain complex infrastructure deployments.
Key Concepts and Terminology in Terraform
Terraform uses a set of key concepts and terminology to define and manage infrastructure resources. Understanding these concepts is essential for writing effective Terraform configuration files and managing infrastructure resources efficiently.
- Providers: Providers are plugins that enable Terraform to interact with different cloud providers and infrastructure platforms. Providers define the resources and data sources that Terraform can manage, as well as the actions that can be performed on those resources. For example, the AWS provider enables Terraform to manage resources on Amazon Web Services (AWS).
- Resources: Resources are the infrastructure components that Terraform manages, such as virtual machines, storage volumes, and network interfaces. Resources are defined using a declarative syntax, which specifies the desired state of the resource. Terraform automatically generates the necessary steps to create, update, or delete the resource to achieve the desired state.
- Variables: Variables are placeholders for input values that are used to customize the behavior of Terraform configuration files. Variables can be defined using a variety of data types, such as strings, numbers, and lists. Variables can be assigned values using command-line arguments, environment variables, or configuration files.
- Outputs: Outputs are the values that are returned by Terraform configuration files after they are applied. Outputs can be used to retrieve information about the infrastructure resources that were created or updated, such as IP addresses, hostnames, or resource IDs. Outputs can be accessed using command-line arguments or configuration files.
- State: State is a data file that stores the current state of the infrastructure resources that are managed by Terraform. The state file is used to track the dependencies between resources, as well as the current configuration and attributes of each resource. Managing the state file is essential for ensuring consistent and reliable infrastructure deployments.
Here’s an example of how these concepts are used in a Terraform configuration file:
provider "aws" { region = "us-west-2" } resource "aws_instance" "example" {
ami = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
tags = {
Name = "example-instance"
}
}
output "instance_id" {
value = aws_instance.example.id
}
In this example, the aws provider is used to manage resources on AWS. The aws\_instance resource is used to create a new virtual machine, with the specified AMI and instance type. The tags block is used to define metadata for the resource. The output block is used to retrieve the ID of the created resource.
How to Write Terraform Configuration Files
Writing Terraform configuration files is a straightforward process that involves defining resources, variables, and outputs using a simple and intuitive syntax. Here’s a step-by-step guide to writing Terraform configuration files, along with best practices for syntax, formatting, and organization.
Step 1: Define the Provider
The first step in writing a Terraform configuration file is to define the provider. Providers are plugins that enable Terraform to interact with different cloud providers and infrastructure platforms. To define a provider, use the provider block and specify the provider name and any required configuration options. For example:
provider "aws" { region = "us-west-2" } Step 2: Define the Resources
The next step is to define the resources that you want to manage using Terraform. Resources are the infrastructure components that Terraform manages, such as virtual machines, storage volumes, and network interfaces. To define a resource, use the resource block and specify the resource type and any required configuration options. For example:
resource "aws\_instance" "example" { ami = "ami-0c94855ba95c574c8" instance\_type = "t2.micro" tags = {
Name = "example-instance"
}
}
Step 3: Define the Variables
Variables are placeholders for input values that are used to customize the behavior of Terraform configuration files. Variables can be defined using a variety of data types, such as strings, numbers, and lists. To define a variable, use the variable block and specify the variable name, data type, and any default values or constraints. For example:
variable "instance\_type" { type = string default = "t2.micro" validation {
condition = can(regex("t2\..*", var.instance_type))
error_message = "Invalid instance type. Must start with 't2.'."
}
}
Step 4: Define the Outputs
Outputs are the values that are returned by Terraform configuration files after they are applied. Outputs can be used to retrieve information about the infrastructure resources that were created or updated, such as IP addresses, hostnames, or resource IDs. To define an output, use the output block and specify the output name and any required transformation or formatting. For example:
output "instance\_id" { value = aws\_instance.example.id } Best Practices for Syntax, Formatting, and Organization
- Use consistent indentation and spacing to improve readability and maintainability.
- Use descriptive and meaningful names for resources, variables, and outputs.
- Use comments to document the purpose and behavior of each resource, variable, and output.
- Use modules to break down complex configurations into smaller, reusable components.
- Use version control to track changes and collaborate with other team members.
- Use Terraform Cloud or other third-party tools to simplify collaboration and increase productivity.
Managing State in Terraform
State management is a critical aspect of using Terraform effectively and securely. State refers to the current state of the infrastructure resources that Terraform manages. The state file contains information about the resources, their dependencies, and their attributes. Properly managing the state file is essential for ensuring consistent and reliable infrastructure deployments.
Risks of State Drift and Inconsistencies
If the state file is not managed properly, it can lead to state drift and inconsistencies. State drift occurs when the actual state of the infrastructure resources deviates from the state specified in the configuration files. Inconsistencies can occur when multiple users or processes modify the state file simultaneously, leading to conflicts and errors. These issues can result in infrastructure resources that are out of sync, difficult to manage, and prone to failures.
Terraform’s Built-in State Management Features
Terraform provides several built-in state management features to help manage the state file and mitigate the risks of state drift and inconsistencies. These features include:
- Local State: By default, Terraform stores the state file locally on the user’s machine. This approach is suitable for small-scale projects or testing environments but is not recommended for production environments due to the risks of state drift and inconsistencies.
- Remote State Backends: Terraform supports several remote state backends, including Amazon S3, Azure Blob Storage, Google Cloud Storage, and HashiCorp Consul. Using a remote state backend enables multiple users or processes to access and modify the state file securely and reliably. Remote state backends also provide versioning, backup, and disaster recovery capabilities.
- State Locking: Terraform supports state locking to prevent conflicts and errors when multiple users or processes modify the state file simultaneously. State locking ensures that only one user or process can modify the state file at a time, preventing conflicts and ensuring consistency.
Best Practices for Managing State in Terraform
- Use a remote state backend to store the state file securely and reliably.
- Use state locking to prevent conflicts and ensure consistency.
- Use version control to track changes to the state file and collaborate with other team members.
- Regularly backup and test the state file to ensure data integrity and recoverability.
- Use Terraform’s built-in testing and validation features to ensure the state file is consistent and reliable.
- Monitor the state file for any signs of state drift or inconsistencies and take corrective action as needed.
Collaborating with Terraform in Teams
Collaboration is an essential aspect of using Terraform effectively in teams. Collaboration enables teams to work together on infrastructure deployments, share knowledge, and ensure consistency and reliability. Here are some best practices for collaborating with Terraform in teams:
Version Control
Version control is a critical aspect of collaborating with Terraform in teams. Version control enables teams to track changes to the Terraform configuration files, collaborate on infrastructure deployments, and revert to previous versions if necessary. Terraform supports integration with popular version control systems, such as Git.
Code Reviews
Code reviews are an essential best practice for ensuring the quality and consistency of Terraform configuration files. Code reviews enable teams to catch errors, ensure compliance with best practices, and share knowledge. Code reviews can be performed manually or using automated tools, such as linters and validators.
Access Control
Access control is essential for ensuring the security and integrity of infrastructure deployments. Access control enables teams to control who can access and modify the Terraform configuration files and state files. Access control can be implemented using tools, such as access control lists (ACLs) and role-based access control (RBAC).
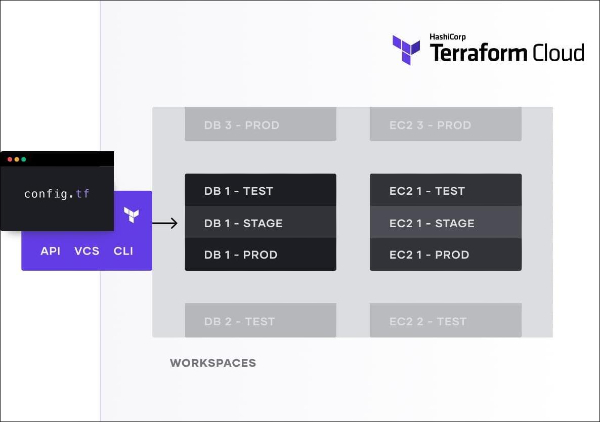
Terraform Cloud
Terraform Cloud is a popular third-party tool that simplifies collaboration and increases productivity. Terraform Cloud provides version control, code reviews, access control, and remote state backends out of the box. Terraform Cloud also provides a user-friendly web interface, command-line tools, and APIs for managing infrastructure deployments.
Best Practices for Collaborating with Terraform in Teams
- Use version control to track changes to the Terraform configuration files and collaborate with other team members.
- Perform code reviews to ensure the quality and consistency of Terraform configuration files.
- Implement access control to ensure the security and integrity of infrastructure deployments.
- Use Terraform Cloud or other third-party tools to simplify collaboration and increase productivity.
- Establish clear communication channels and processes to ensure alignment and consistency across the team.
Best Practices for Using Terraform in Production
Using Terraform in production requires careful planning, testing, and monitoring to ensure reliable and secure infrastructure deployments. Here are some best practices for using Terraform in production:
Testing
Testing is a critical aspect of using Terraform in production. Testing enables teams to catch errors, ensure compliance with best practices, and ensure consistency and reliability. Terraform provides several built-in testing and validation features, such as the terraform plan and terraform validate commands. Teams can also use third-party tools, such as InSpec, to perform more advanced testing and validation.
Validation
Validation is essential for ensuring the quality and consistency of Terraform configuration files. Validation can be performed manually or using automated tools, such as linters and validators. Terraform provides several built-in validation features, such as the terraform validate command, which checks the syntax and structure of the configuration files.
Monitoring
Monitoring is essential for ensuring the reliability and performance of infrastructure deployments. Monitoring enables teams to detect and troubleshoot issues, optimize performance, and ensure compliance with best practices. Teams can use tools, such as Prometheus and Grafana, to monitor Terraform infrastructure deployments.
Version Control
Version control is essential for tracking changes to the Terraform configuration files and collaborating with other team members. Version control enables teams to revert to previous versions if necessary, perform code reviews, and ensure consistency and reliability.
Access Control
Access control is essential for ensuring the security and integrity of infrastructure deployments. Access control enables teams to control who can access and modify the Terraform configuration files and state files. Access control can be implemented using tools, such as access control lists (ACLs) and role-based access control (RBAC).
Best Practices for Using Terraform in Production
- Use testing and validation to ensure the quality and consistency of Terraform configuration files.
- Monitor Terraform infrastructure deployments to ensure reliability and performance.
- Use version control to track changes to the Terraform configuration files and collaborate with other team members.
- Implement access control to ensure the security and integrity of infrastructure deployments.
- Establish clear communication channels and processes to ensure alignment and consistency across the team.
Comparing Terraform to Other IaC Tools
Terraform is a popular IaC tool, but it is not the only one available. Here is a comparison of Terraform to other IaC tools, such as AWS CloudFormation, Azure Resource Manager, and Google Cloud Deployment Manager, highlighting their strengths and weaknesses and providing guidance on when to use each tool in different scenarios:
AWS CloudFormation
AWS CloudFormation is a native IaC tool provided by Amazon Web Services (AWS). It enables users to define and deploy AWS infrastructure resources using YAML or JSON templates. CloudFormation supports a wide range of AWS resources and provides built-in validation and testing features. However, it has some limitations, such as a steep learning curve, limited customization options, and a lack of support for non-AWS resources.
Azure Resource Manager
Azure Resource Manager (ARM) is a native IaC tool provided by Microsoft Azure. It enables users to define and deploy Azure infrastructure resources using JSON templates. ARM supports a wide range of Azure resources and provides built-in validation and testing features. However, it has some limitations, such as a steep learning curve, limited customization options, and a lack of support for non-Azure resources.
Google Cloud Deployment Manager
Google Cloud Deployment Manager (GCDM) is a native IaC tool provided by Google Cloud Platform (GCP). It enables users to define and deploy GCP infrastructure resources using YAML or JSON templates. GCDM supports a wide range of GCP resources and provides built-in validation and testing features. However, it has some limitations, such as a steep learning curve, limited customization options, and a lack of support for non-GCP resources.
Terraform vs. Other IaC Tools
Terraform has several advantages over other IaC tools, such as its support for multiple cloud providers, including AWS, Azure, and GCP, and its flexible and customizable syntax. Terraform also provides built-in state management features, such as remote state backends and state locking, which are not available in other IaC tools. However, Terraform also has some limitations, such as a steeper learning curve and a more complex syntax compared to other IaC tools.
When to Use Each Tool
- Use AWS CloudFormation if you are deploying infrastructure exclusively on AWS and require built-in validation and testing features.
- Use Azure Resource Manager if you are deploying infrastructure exclusively on Azure and require built-in validation and testing features.
- Use Google Cloud Deployment Manager if you are deploying infrastructure exclusively on GCP and require built-in validation and testing features.
- Use Terraform if you are deploying infrastructure on multiple cloud providers, require customization options, or need built-in state management features.