Unraveling Docker: A Brief Overview
Docker is an open-source platform that has revolutionized the way developers and businesses handle software development and deployment. Its primary purpose is to simplify the process of creating, deploying, and managing applications using containerization technology. Docker achieves this by isolating applications and their dependencies into lightweight, portable containers.
Containerization, one of Docker’s main features, enables applications to run consistently across different computing environments, from local development machines to production servers. This ensures that applications function as expected, regardless of the underlying infrastructure. Additionally, Docker provides version control for containers, allowing developers to manage and track changes to their applications and dependencies over time.
Portability is another key benefit of Docker. With Docker, developers can package applications and their dependencies into a single container, making it easy to move the application between various environments, such as development, testing, and production. This reduces the risk of compatibility issues and ensures a smooth deployment process.
In summary, Docker has become an essential tool for developers and businesses due to its ability to simplify application development, deployment, and management. Its main features, including containerization, version control, and portability, make it a powerful and flexible solution for modern software development.
Docker Swarm: A Deep Dive into the World of Container Orchestration
Docker Swarm is a native container orchestration tool that is part of the Docker platform. Its primary role is to simplify the management of Docker containers, ensuring seamless deployment, scaling, and networking of applications.
One of the main benefits of Docker Swarm is its built-in orchestration capabilities. This feature allows users to manage multiple containers as a single entity, making it easier to deploy, update, and scale applications. Docker Swarm’s user-friendly interface and intuitive commands simplify the process of managing containers, even for users with limited experience in containerization.
Security is another critical aspect of Docker Swarm. The platform offers several security features, including role-based access control, which enables administrators to define and manage user roles and permissions. Additionally, Docker Swarm supports secure communication between nodes using Transport Layer Security (TLS) encryption and mutual authentication. These features help ensure that containerized applications remain secure and protected from potential threats.
Scalability is a key advantage of Docker Swarm. The platform allows users to create and manage large-scale containerized applications with ease. By leveraging Docker Swarm’s built-in load balancing and service discovery features, users can ensure that their applications remain performant and responsive, even as the number of containers and users increases.
In summary, Docker Swarm is an essential tool for managing Docker containers, offering built-in orchestration, security, and scalability features. Its intuitive interface and powerful commands make it an ideal solution for developers and businesses looking to streamline their container management processes.
How to Implement Docker and Docker Swarm: A Step-by-Step Guide
To get started with Docker and Docker Swarm, follow these steps to install and configure the platform:
Step 1: Install Docker
Begin by installing Docker on your local machine or server. Visit the official Docker website to download the appropriate package for your operating system. Follow the installation instructions provided by Docker to complete the setup process.
Step 2: Verify Docker Installation
After installation, open a terminal or command prompt and run the following command to verify that Docker is installed correctly:
docker --versionStep 3: Install Docker Compose
Docker Compose is a tool for defining and running multi-container Docker applications. Install Docker Compose by following the instructions on the official Docker website.
Step 4: Initialize Docker Swarm
To create a new Docker Swarm, run the following command on the machine that will act as the swarm manager:
docker swarm initStep 5: Join Worker Nodes to the Swarm
To add worker nodes to the swarm, run the command provided by the output of the docker swarm init command on each worker node. This command will look similar to the following:
docker swarm join --token SWMTKN-1-2abcdefghijklmnopqrstuvwxyzabcdefg 192.168.0.1:2377Step 6: Deploy a Service to the Swarm
Create a Docker Compose file to define the application services that you want to deploy to the swarm. Then, run the following command to deploy the services:
docker stack deploy -c docker-compose.yml myappIn this example, docker-compose.yml is the Docker Compose file, and myapp is the name of the application stack. This command will deploy the services to the Docker Swarm, ensuring that they are automatically replicated and load-balanced across the available nodes.
By following these steps, you can quickly and easily implement Docker and Docker Swarm on your local machine or server. This will enable you to take advantage of the powerful containerization and orchestration features offered by the platform.
Real-World Applications of Docker and Docker Swarm: Success Stories and Case Studies
Docker and Docker Swarm have been successfully implemented in various industries, enabling businesses to streamline their development and deployment processes. Here are some examples of successful Docker and Docker Swarm implementations:
Example 1: Netflix
Netflix, a leading entertainment company, uses Docker and Docker Swarm to manage its microservices architecture. By leveraging Docker’s containerization capabilities, Netflix has been able to improve its development and deployment speed, reduce costs, and enhance its security posture. Additionally, Docker Swarm’s built-in orchestration features have enabled Netflix to manage its large-scale containerized applications with ease.
Example 2: Goldman Sachs
Goldman Sachs, a global investment bank, has adopted Docker and Docker Swarm to modernize its development and deployment processes. By using Docker, Goldman Sachs has been able to reduce its infrastructure costs, improve its application portability, and enhance its security. Furthermore, Docker Swarm’s scalability features have enabled Goldman Sachs to manage its large-scale containerized applications with ease.
Example 3: GE Digital
GE Digital, a digital industrial company, has implemented Docker and Docker Swarm to manage its containerized applications. By using Docker, GE Digital has been able to improve its development and deployment speed, reduce costs, and enhance its security posture. Additionally, Docker Swarm’s built-in orchestration features have enabled GE Digital to manage its large-scale containerized applications with ease, ensuring high availability and scalability.
These examples demonstrate the potential benefits of using Docker and Docker Swarm in real-world applications. By adopting these technologies, businesses can streamline their development and deployment processes, reduce costs, and enhance their security posture. However, it is important to note that successful Docker and Docker Swarm implementations require careful planning, configuration, and management to ensure optimal performance and reliability.
Best Practices for Using Docker and Docker Swarm: Expert Recommendations
To get the most out of Docker and Docker Swarm, it is essential to follow best practices based on expert opinions and industry standards. Here are some best practices for using Docker and Docker Swarm:
1. Monitor Your Containers
Monitoring your containers is crucial for ensuring optimal performance and reliability. Use tools such as Prometheus, Grafana, and cAdvisor to monitor your Docker and Docker Swarm environments. These tools can help you track resource utilization, container health, and other critical metrics.
2. Implement Backups and Disaster Recovery
Implementing backups and disaster recovery is essential for ensuring business continuity. Use tools such as Docker Compose, Docker Volume Plugins, and Docker Swarm’s built-in backup and restore features to implement backups and disaster recovery for your Docker and Docker Swarm environments.
3. Implement Access Control
Implementing access control is crucial for ensuring the security of your Docker and Docker Swarm environments. Use tools such as Docker Secrets, Docker Configs, and Role-Based Access Control (RBAC) to implement access control for your Docker and Docker Swarm environments.
4. Implement Network Security
Implementing network security is essential for ensuring the security of your Docker and Docker Swarm environments. Use tools such as Docker Network, Docker Overlay Network, and Docker Macvlan Network to implement network security for your Docker and Docker Swarm environments.
5. Implement Image Vulnerability Management
Implementing image vulnerability management is crucial for ensuring the security of your Docker and Docker Swarm environments. Use tools such as Docker Content Trust, Docker Notary, and Docker Security Scanning to implement image vulnerability management for your Docker and Docker Swarm environments.
6. Implement Continuous Integration and Continuous Deployment (CI/CD)
Implementing CI/CD is essential for streamlining your development and deployment processes. Use tools such as Jenkins, Travis CI, and CircleCI to implement CI/CD for your Docker and Docker Swarm environments.
7. Implement Logging and Tracing
Implementing logging and tracing is crucial for debugging and troubleshooting your Docker and Docker Swarm environments. Use tools such as Docker Logging, Docker Events, and Docker Trace to implement logging and tracing for your Docker and Docker Swarm environments.
8. Implement Resource Optimization
Implementing resource optimization is essential for ensuring optimal performance and reliability. Use tools such as Docker System Resource Control, Docker Memory Limits, and Docker CPU Limits to implement resource optimization for your Docker and Docker Swarm environments.
9. Implement Service Discovery
Implementing service discovery is crucial for ensuring that your containers can communicate with each other. Use tools such as Docker DNS, Docker Links, and Docker Service Discovery to implement service discovery for your Docker and Docker Swarm environments.
10. Implement Load Balancing
Implementing load balancing is essential for ensuring high availability and scalability. Use tools such as Docker Swarm’s built-in load balancing, Nginx, and HAProxy to implement load balancing for your Docker and Docker Swarm environments.
By following these best practices, you can ensure optimal performance, reliability, and security for your Docker and Docker Swarm environments. Additionally, these best practices can help you streamline your development and deployment processes, reduce costs, and enhance your security posture.
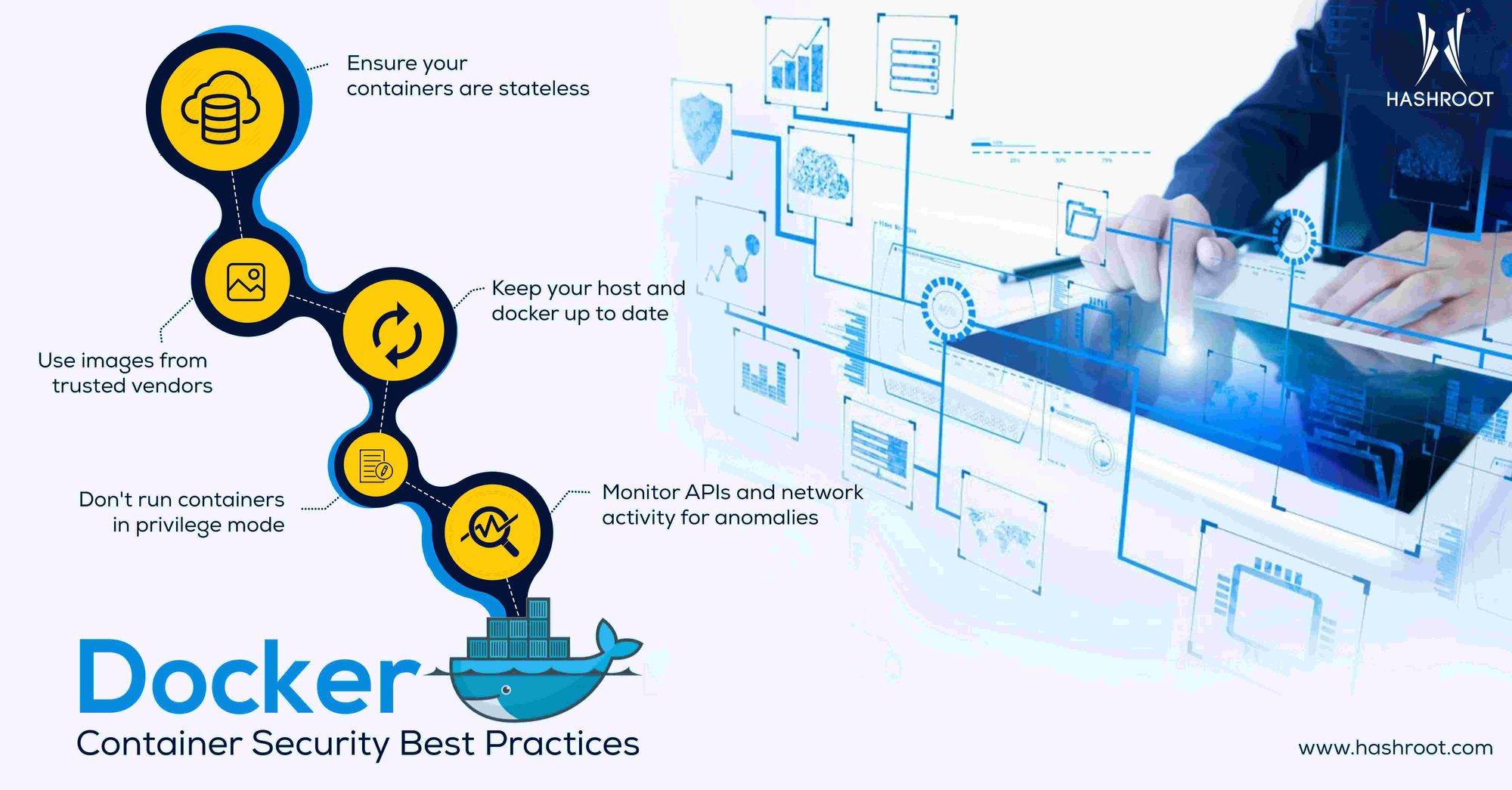
Security Considerations for Docker and Docker Swarm: Keeping Your Containers Safe
Docker and Docker Swarm offer numerous benefits, including containerization, version control, and portability. However, with these benefits come security risks that must be addressed to ensure the safety and integrity of your applications and data.
Network Security
Network security is a critical concern for Docker and Docker Swarm users. To mitigate network security risks, consider implementing the following best practices:
- Use Docker’s built-in firewall to restrict access to your containers.
- Implement network segmentation to isolate your containers from each other and from the host network.
- Use encryption to secure network traffic between your containers and between your containers and external services.
Access Control
Access control is another critical concern for Docker and Docker Swarm users. To mitigate access control risks, consider implementing the following best practices:
- Use role-based access control (RBAC) to restrict access to your containers and to Docker and Docker Swarm resources.
- Implement multi-factor authentication (MFA) to add an extra layer of security to your Docker and Docker Swarm environments.
- Regularly review access control policies and permissions to ensure that they are up-to-date and aligned with your organization’s security policies.
Image Vulnerabilities
Image vulnerabilities are a significant security risk for Docker and Docker Swarm users. To mitigate image vulnerabilities, consider implementing the following best practices:
- Regularly scan your Docker images for vulnerabilities using tools such as Docker Security Scanning or Clair.
- Use trusted Docker image repositories and avoid using images from untrusted sources.
- Implement a vulnerability management process to address identified vulnerabilities in a timely manner.
Container Escape
Container escape is a security risk for Docker and Docker Swarm users. To mitigate container escape risks, consider implementing the following best practices:
- Regularly update your Docker and Docker Swarm environments to ensure that you have the latest security patches and updates.
- Use the principle of least privilege (PoLP) to restrict the privileges of your containers and to limit the potential impact of a container escape.
- Implement a container escape detection and response process to quickly identify and respond to container escape incidents.
By following these best practices, you can mitigate the security risks associated with Docker and Docker Swarm and ensure the safety and integrity of your applications and data. Additionally, these best practices can help you meet compliance requirements and maintain your organization’s security posture.
Trends and Innovations in Docker and Docker Swarm: The Future of Containerization
Docker and Docker Swarm have revolutionized the way developers and businesses manage their applications and infrastructure. As containerization continues to grow in popularity, new trends and innovations are emerging that have the potential to shape the future of the industry.
Kubernetes Integration
Kubernetes has become the de facto standard for container orchestration, and many organizations are looking to integrate Kubernetes with Docker and Docker Swarm. Kubernetes provides advanced features such as automatic scaling, self-healing, and rolling updates, making it an attractive option for large-scale container deployments. Docker and Docker Swarm can be integrated with Kubernetes using tools such as Docker Enterprise and Docker Kubernetes Service (DKS).
Multi-Cloud Deployments
Multi-cloud deployments are becoming increasingly popular as organizations look to take advantage of the benefits of cloud computing while avoiding vendor lock-in. Docker and Docker Swarm provide a consistent and portable way to deploy applications across multiple clouds and on-premises environments. With Docker and Docker Swarm, developers can build applications once and deploy them anywhere, making it easier to manage complex multi-cloud deployments.
Edge Computing
Edge computing is a new trend that involves processing data and running applications on devices located at the edge of the network, closer to the source of the data. Docker and Docker Swarm are well-suited for edge computing, as they provide a lightweight and portable way to deploy applications on resource-constrained devices. With Docker and Docker Swarm, developers can build applications once and deploy them on a variety of edge devices, from IoT devices to gateways and edge servers.
Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are becoming increasingly important in many industries, and Docker and Docker Swarm are well-suited for building and deploying AI and ML applications. With Docker and Docker Swarm, developers can build and test AI and ML models in a consistent and reproducible way, and then deploy them to production environments with ease. Docker and Docker Swarm also provide a scalable and flexible way to deploy AI and ML applications, making it easier to handle large datasets and complex workflows.
Serverless Computing
Serverless computing is a new trend that involves running applications without managing servers or infrastructure. Docker and Docker Swarm can be used to build and deploy serverless applications, taking advantage of the benefits of containerization and microservices architecture. With Docker and Docker Swarm, developers can build and test serverless functions in a consistent and reproducible way, and then deploy them to production environments with ease.
In conclusion, Docker and Docker Swarm are at the forefront of the containerization revolution, and new trends and innovations are emerging that have the potential to shape the future of the industry. By staying up-to-date with the latest trends and innovations, developers and businesses can take advantage of the benefits of containerization and stay ahead of the competition.
Choosing the Right Containerization Solution: Docker and Docker Swarm vs. Other Options
When it comes to containerization, Docker and Docker Swarm are popular choices for developers and businesses. However, there are other options available, such as Kubernetes, Podman, and LXC. In this article, we will compare Docker and Docker Swarm with these other options, to help you make an informed decision.
Docker vs. Podman
Podman is a container engine that is similar to Docker, but with some key differences. Podman is designed to be more secure than Docker, as it does not require root privileges to run containers. Podman also supports systemd, making it easier to manage containers on Linux systems. However, Docker has a larger community and more third-party tools and integrations, making it a more popular choice for many developers.
Docker Swarm vs. Kubernetes
Kubernetes is a container orchestration platform that is often compared to Docker Swarm. Kubernetes is more complex than Docker Swarm, but it offers more advanced features, such as automatic scaling, self-healing, and rolling updates. Kubernetes is also more widely adopted than Docker Swarm, with a larger community and more third-party tools and integrations. However, Docker Swarm is simpler to set up and use than Kubernetes, making it a better choice for smaller-scale deployments.
Docker and Docker Swarm vs. LXC
LXC is a lightweight containerization solution that is similar to Docker, but with some key differences. LXC is more lightweight than Docker, and it provides a more complete operating system environment for containers. However, Docker is more popular than LXC, with a larger community and more third-party tools and integrations. Docker Swarm also provides more advanced features for container orchestration than LXC.
Choosing the Right Solution
When choosing a containerization solution, there are several factors to consider, such as the size and complexity of your deployment, your security requirements, and your budget. Docker and Docker Swarm are popular choices for many developers and businesses, but they may not be the best fit for every use case. By comparing Docker and Docker Swarm with other options, such as Kubernetes, Podman, and LXC, you can make an informed decision that meets your specific needs.
In conclusion, Docker and Docker Swarm are powerful containerization solutions, but they are not the only options available. By comparing Docker and Docker Swarm with other containerization solutions, such as Kubernetes, Podman, and LXC, you can make an informed decision that meets your specific needs. When choosing a containerization solution, consider factors such as the size and complexity of your deployment, your security requirements, and your budget.