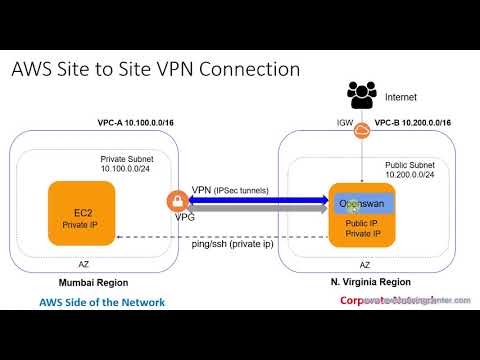
What is AWS IoT VPN?
AWS IoT VPN is a virtual private network (VPN) service specifically designed for securely connecting Internet of Things (IoT) devices to the AWS cloud. This fully-managed VPN service enables users to establish a secure and reliable communication channel between their IoT devices and AWS resources, ensuring data privacy and integrity. The benefits and features of AWS IoT VPN include:
- Data encryption: AWS IoT VPN uses industry-standard encryption protocols to protect data transmitted between IoT devices and the AWS cloud.
- Scalability: AWS IoT VPN can easily scale to accommodate a growing number of IoT devices, making it an ideal solution for both small-scale and large-scale IoT projects.
- Integration: AWS IoT VPN integrates seamlessly with other AWS services, such as AWS IoT Core, AWS IoT Analytics, and AWS IoT Device Defender, enabling users to build end-to-end IoT solutions.
- Ease of use: AWS IoT VPN offers a user-friendly interface and simple configuration options, allowing users to quickly set up and manage secure VPN connections for their IoT devices.
- Cost-effective: AWS IoT VPN operates on a pay-as-you-go pricing model, ensuring that users only pay for the resources they actually use.
How AWS IoT VPN Works
AWS IoT VPN operates by establishing secure connections between IoT devices and the AWS cloud using VPN technology. The underlying architecture of AWS IoT VPN consists of the following components:
- VPN clients: These are the IoT devices that connect to the AWS IoT VPN. VPN clients can be hardware devices, such as routers, or software applications running on IoT devices.
- VPN servers: AWS IoT VPN servers are responsible for managing and maintaining the VPN connections. These servers are fully managed by AWS and can be easily configured using the AWS Management Console or the AWS CLI.
- Certificate-based authentication: AWS IoT VPN uses certificate-based authentication to ensure that only authorized devices can connect to the VPN. This involves creating and managing X.509 certificates for each VPN client, which are then used to authenticate the devices during the VPN connection process.
To establish a secure connection between an IoT device and the AWS cloud using AWS IoT VPN, follow these steps:
- Create a VPN connection in the AWS Management Console.
- Configure the VPN client on the IoT device with the necessary VPN connection details, such as the VPN server address and the certificate-based authentication credentials.
- Initiate the VPN connection from the IoT device. The VPN client will authenticate with the VPN server using the provided credentials and establish a secure connection.
- Once the VPN connection is established, the IoT device can securely communicate with AWS services and resources over the VPN tunnel.
Key Components of AWS IoT VPN
AWS IoT VPN consists of several essential components that work together to provide secure and reliable VPN connections for IoT devices. Understanding these components is crucial for effectively using and managing AWS IoT VPN.
- VPN clients: VPN clients are the IoT devices that connect to the AWS IoT VPN. These clients can be hardware devices, such as routers, or software applications running on IoT devices. VPN clients must be configured with the necessary VPN connection details and authentication credentials to establish a secure connection with the VPN server.
- VPN servers: AWS IoT VPN servers are responsible for managing and maintaining the VPN connections. These servers are fully managed by AWS and can be easily configured using the AWS Management Console or the AWS CLI. VPN servers handle the authentication and encryption of data transmitted between the VPN clients and the AWS cloud.
- Certificate-based authentication: AWS IoT VPN uses certificate-based authentication to ensure that only authorized devices can connect to the VPN. This involves creating and managing X.509 certificates for each VPN client, which are then used to authenticate the devices during the VPN connection process. AWS IoT VPN supports both AWS-managed certificates and customer-provided certificates for authentication.
- IPsec tunneling: AWS IoT VPN uses IPsec tunneling to encrypt and secure the data transmitted between the VPN clients and the VPN server. IPsec provides strong encryption and authentication, ensuring that data cannot be intercepted or tampered with during transmission.
- AWS Management Console: The AWS Management Console is a web-based interface that allows users to easily create, configure, and manage their AWS IoT VPN connections. The console provides a user-friendly interface for managing VPN clients, certificates, and other VPN components.
- AWS CLI: The AWS Command Line Interface (CLI) is a powerful tool for managing AWS resources, including AWS IoT VPN. The AWS CLI allows users to automate various VPN management tasks, such as creating VPN connections, configuring VPN clients, and managing certificates, using simple command-line commands.
Setting Up AWS IoT VPN: A Step-by-Step Guide
Setting up AWS IoT VPN is a straightforward process that involves creating a VPN connection, configuring VPN clients, and managing certificates. Follow these steps to get started:
- Create a VPN connection:
- Log in to the AWS Management Console.
- Navigate to the AWS IoT VPN page.
- Click “Create a new VPN connection” and follow the on-screen instructions to configure your VPN connection settings.
- Configure VPN clients:
- Download the VPN client configuration file from the AWS Management Console.
- Install and configure the VPN client software on your IoT devices using the downloaded configuration file.
- Ensure that each VPN client is configured with the correct VPN connection details and authentication credentials.
- Manage certificates:
- Create and manage X.509 certificates for each VPN client using the AWS IoT Core or AWS Certificate Manager services.
- Assign the appropriate certificates to each VPN client and ensure that the certificates are up-to-date and valid.
- Monitor the certificate status and rotation to maintain the security of your VPN connections.
By following these steps, you can easily set up AWS IoT VPN and securely connect your IoT devices to the AWS cloud. Remember to always follow best practices for managing your VPN connections and certificates to ensure the security and reliability of your IoT infrastructure.
Integrating AWS IoT VPN with Real-World IoT Devices
AWS IoT VPN can be seamlessly integrated with a wide variety of IoT devices and platforms, enabling secure and reliable communication between your IoT infrastructure and the AWS cloud. Here are some examples of popular IoT devices and platforms that can be integrated with AWS IoT VPN:
- Amazon Echo: Amazon Echo devices, such as the Echo Dot and Echo Show, can be connected to AWS IoT VPN using a compatible VPN client. This enables secure voice control and automation of your IoT devices using Amazon Alexa.
- Raspberry Pi: The Raspberry Pi single-board computer can be configured as a VPN client, allowing it to securely connect to AWS IoT VPN. This enables remote access, monitoring, and control of your Raspberry Pi projects and applications.
- Arduino: Arduino boards and shields can be integrated with AWS IoT VPN using a compatible VPN client or a custom-built VPN solution. This enables secure communication between your Arduino projects and the AWS cloud, enabling remote monitoring, control, and data analysis.
- Smart Home Devices: Many smart home devices, such as smart thermostats, security cameras, and lighting systems, can be connected to AWS IoT VPN using compatible VPN clients or hubs. This enables secure and reliable communication between your smart home devices and the AWS cloud, enabling advanced automation, remote monitoring, and control features.
By integrating AWS IoT VPN with your IoT devices and platforms, you can ensure the security and reliability of your IoT infrastructure, while also enabling advanced features and capabilities. Always follow best practices for configuring and managing your VPN connections and certificates to maintain the security and performance of your IoT infrastructure.
Security Best Practices for AWS IoT VPN
AWS IoT VPN is designed to provide a secure and reliable communication channel between your IoT devices and the AWS cloud. However, it is important to follow best practices for configuring and managing your VPN connections and certificates to maintain the security and performance of your IoT infrastructure. Here are some security best practices for AWS IoT VPN:
- Use strong password policies: Ensure that all VPN users and administrators follow strong password policies, including the use of complex passwords, regular password changes, and two-factor authentication.
- Regularly update software: Regularly update the software and firmware of your VPN clients, servers, and other IoT devices to ensure that they are protected against the latest security threats and vulnerabilities.
- Monitor for suspicious activity: Regularly monitor your VPN connections and certificates for suspicious activity, such as unexpected connections, failed authentication attempts, and certificate revocations. Use AWS IoT Device Defender or other security tools to detect and respond to potential security threats.
- Implement certificate-based authentication: Use certificate-based authentication to ensure that only authorized devices can connect to your VPN. Regularly rotate and manage your certificates to maintain the security of your VPN connections.
- Use network segmentation: Use network segmentation to isolate your VPN traffic from other network traffic and reduce the risk of security threats and attacks. Use VPCs, subnets, and security groups to control access to your VPN and other AWS resources.
- Enable VPN logging and auditing: Enable VPN logging and auditing to track and monitor VPN activity and identify potential security threats. Use AWS CloudTrail, VPC Flow Logs, or other logging and auditing tools to monitor your VPN connections and certificates.
By following these security best practices, you can ensure the security and reliability of your AWS IoT VPN connections and certificates, and maintain the confidentiality, integrity, and availability of your IoT infrastructure.
Comparing AWS IoT VPN with Other IoT VPN Solutions
AWS IoT VPN is a powerful and flexible VPN solution for securely connecting IoT devices to the cloud. However, there are other IoT VPN solutions available in the market, each with its own strengths and weaknesses. Here is a comparison of AWS IoT VPN with other popular IoT VPN solutions:
- Azure IoT VPN: Azure IoT VPN is a VPN solution provided by Microsoft for securely connecting IoT devices to the Azure cloud. Azure IoT VPN offers similar features and capabilities as AWS IoT VPN, including certificate-based authentication, network segmentation, and VPN logging and auditing. However, Azure IoT VPN has a more limited range of supported devices and platforms compared to AWS IoT VPN.
- Google Cloud IoT VPN: Google Cloud IoT VPN is a VPN solution provided by Google for securely connecting IoT devices to the Google Cloud Platform. Google Cloud IoT VPN offers similar features and capabilities as AWS IoT VPN, including certificate-based authentication, network segmentation, and VPN logging and auditing. However, Google Cloud IoT VPN has a more limited range of supported devices and platforms compared to AWS IoT VPN, and has a steeper learning curve for new users.
- Cisco IoT VPN: Cisco IoT VPN is a VPN solution provided by Cisco for securely connecting IoT devices to the cloud or on-premises networks. Cisco IoT VPN offers advanced features and capabilities, such as dynamic routing, traffic segmentation, and Quality of Service (QoS). However, Cisco IoT VPN has a more complex configuration and management process compared to AWS IoT VPN, and requires more technical expertise to set up and maintain.
When comparing AWS IoT VPN with other IoT VPN solutions, it is important to consider your specific use case, requirements, and constraints. AWS IoT VPN offers a balance of features, capabilities, and ease of use, making it a suitable choice for a wide range of IoT applications and scenarios. Always evaluate and compare the strengths and weaknesses of each VPN solution to ensure that you choose the one that best meets your needs and goals.
Real-World Applications of AWS IoT VPN
AWS IoT VPN is a versatile and powerful VPN solution that can be used in a wide range of real-world applications and scenarios. Here are some examples of how AWS IoT VPN can be used to enhance the security, reliability, and performance of IoT systems and applications:
- Smart Homes: AWS IoT VPN can be used to securely connect smart home devices, such as thermostats, lights, and security cameras, to the cloud or on-premises networks. This enables remote access, monitoring, and control of smart home devices, while ensuring that sensitive data and communications are protected against unauthorized access and eavesdropping.
- Industrial Automation: AWS IoT VPN can be used to securely connect industrial automation systems, such as Programmable Logic Controllers (PLCs), Distributed Control Systems (DCSs), and Supervisory Control and Data Acquisition (SCADA) systems, to the cloud or on-premises networks. This enables remote monitoring, control, and maintenance of industrial automation systems, while ensuring that sensitive data and communications are protected against unauthorized access and eavesdropping.
- Remote Monitoring and Management: AWS IoT VPN can be used to securely connect remote devices, such as sensors, cameras, and machines, to the cloud or on-premises networks. This enables remote monitoring, control, and management of remote devices, while ensuring that sensitive data and communications are protected against unauthorized access and eavesdropping.
- Disaster Recovery: AWS IoT VPN can be used as part of a disaster recovery plan for IoT systems and applications. By establishing a secure VPN connection between the primary and secondary sites, AWS IoT VPN can ensure that data and communications are protected against disruptions, failures, and attacks, and that business continuity and disaster recovery objectives are met.
These are just a few examples of how AWS IoT VPN can be used in real-world applications and scenarios. By providing a secure, reliable, and flexible VPN solution for IoT devices and systems, AWS IoT VPN can help organizations enhance the security, reliability, and performance of their IoT infrastructure, and unlock the full potential of their IoT data and applications.