Understanding Network Access Control Lists (NACLs) in AWS
Network Access Control Lists (NACLs) are a crucial part of AWS network security, acting as a firewall for Amazon Virtual Private Cloud (VPC) resources. NACLs are stateless, meaning they evaluate each incoming and outgoing request independently, without knowledge of previous requests. This is in contrast to Security Groups, which are stateful and maintain context between requests.
NACLs are associated with subnets, not individual EC2 instances or Elastic Network Interfaces (ENIs). When a request is made to a resource within a subnet, it first passes through the NACL before reaching the Security Group. NACLs provide an additional layer of security, allowing you to control traffic at the subnet level.
NACLs consist of a series of inbound and outbound rules, each with a corresponding number, protocol, and allow or deny action. These rules are evaluated in order, with lower-numbered rules taking precedence over higher-numbered ones. By default, NACLs allow all inbound and outbound traffic, but you can customize the rules to meet your specific security requirements.
When designing network security for AWS workloads, it is essential to understand the differences between NACLs and Security Groups. Both components have unique strengths and weaknesses, and a robust, multi-layered security strategy often involves leveraging the benefits of both.
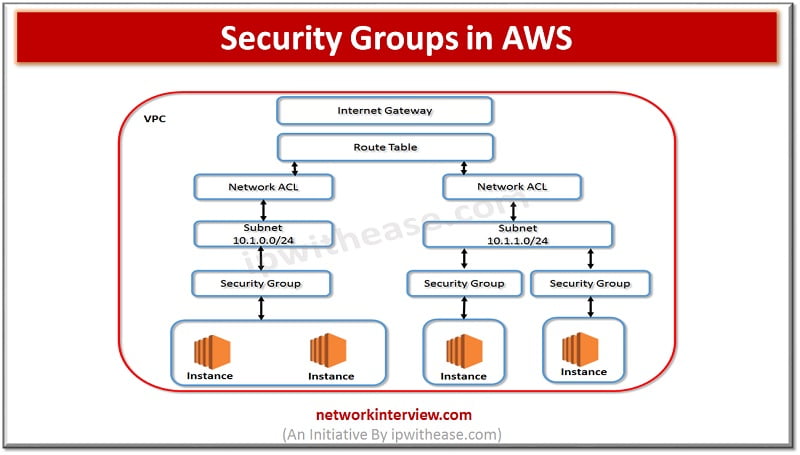
Exploring Security Groups in AWS
Security Groups are an essential part of AWS network security, functioning as a virtual firewall for EC2 instances and Elastic Network Interfaces (ENIs). Unlike NACLs, Security Groups are stateful, meaning they maintain context between requests. This allows Security Groups to automatically permit responses to requests that they allow, without explicitly configuring rules for those responses.
Security Groups are associated with specific network interfaces, such as EC2 instances or ENIs. When a request is made to a resource protected by a Security Group, the request is evaluated based on the Security Group’s rules. These rules determine whether the request should be allowed or denied, and the Security Group can also apply rules to outbound traffic.
Security Groups consist of inbound and outbound rules, similar to NACLs. However, Security Groups do not have a concept of rule numbers; instead, rules are evaluated based on their order within the Security Group. By default, Security Groups deny all inbound traffic and allow all outbound traffic, but you can customize the rules to meet your specific security requirements.
When designing network security for AWS workloads, it is crucial to understand the differences between NACLs and Security Groups. While both components serve similar purposes, their unique characteristics and application methods make them suitable for different use cases. A robust, multi-layered security strategy often involves leveraging the benefits of both NACLs and Security Groups.
Key Differences Between NACLs and Security Groups
NACLs and Security Groups are both crucial components of AWS network security, but they differ in several ways. Understanding these differences is essential when designing network security for AWS workloads.
Statefulness
One of the primary differences between NACLs and Security Groups lies in their statefulness. NACLs are stateless, meaning they evaluate each incoming and outgoing request independently, without knowledge of previous requests. In contrast, Security Groups are stateful, maintaining context between requests and automatically permitting responses to allowed requests without explicitly configuring rules for those responses.
Stateless Rules
NACLs use stateless rules, which are evaluated independently for each request. These rules consist of a rule number, protocol, and allow or deny action. In contrast, Security Groups do not have a concept of rule numbers; instead, rules are evaluated based on their order within the Security Group.
Default Rules
NACLs and Security Groups have different default rules. By default, NACLs allow all inbound and outbound traffic, while Security Groups deny all inbound traffic and allow all outbound traffic. These defaults can be customized to meet specific security requirements.
Association with Resources
NACLs are associated with subnets, while Security Groups are associated with specific network interfaces, such as EC2 instances or ENIs. This difference in association affects how each component is applied and managed within an AWS VPC.
When designing network security for AWS workloads, it is essential to understand the differences between NACLs and Security Groups. A robust, multi-layered security strategy often involves leveraging the benefits of both components. By understanding their unique characteristics and application methods, you can create a more secure and efficient network infrastructure.
How to Implement NACLs in AWS: A Step-by-Step Guide
Implementing Network Access Control Lists (NACLs) in AWS is a straightforward process. Follow these steps to create a new NACL, configure rules, and associate it with a subnet:
Step 1: Create a New NACL
Log in to the AWS Management Console and navigate to the VPC service. In the left-hand menu, click “Network Access Control Lists” and then click the “Create Network Access Control List” button. Provide a name and description for your NACL, and select the appropriate VPC. Click “Create” to proceed.
Step 2: Configure Rules
After creating the NACL, you will be taken to the “Inbound Rules” tab. Here, you can configure rules that control inbound traffic. Click the “Edit Rules” button, and then click the “Add Rule” button to create a new rule. Specify the rule number, protocol, and allow or deny action. You can also specify the source or destination for the rule. Click “Save Rules” when you are done configuring the inbound rules.
Next, navigate to the “Outbound Rules” tab and configure rules for outbound traffic using the same process. Remember that NACLs are stateless, so you will need to create separate rules for inbound and outbound traffic.
Step 3: Associate the NACL with a Subnet
Once you have configured the rules, you can associate the NACL with a subnet. Navigate to the “Subnets” menu and select the subnet you want to associate with the NACL. In the “Network Access Control List” section, select the NACL you created and click “Save” to apply the changes.
By following these steps, you can effectively implement NACLs in AWS to enhance your network security. Remember to periodically review and update your NACL rules to ensure they continue to meet your security requirements.
Visuals can greatly enhance the understanding of implementing NACLs in AWS. Consider adding screenshots or diagrams to illustrate each step of the process.
How to Configure Security Groups in AWS: A Comprehensive Tutorial
Security Groups are an essential aspect of AWS network security, functioning as a virtual firewall for EC2 instances and Elastic Network Interfaces (ENIs). This tutorial covers creating, editing, deleting Security Groups, and configuring rules, as well as associating them with EC2 instances or ENIs. Visuals will be included to enhance the explanation.
Step 1: Create a New Security Group
Log in to the AWS Management Console and navigate to the EC2 service. In the left-hand menu, click “Security Groups” and then click the “Create Security Group” button. Provide a name and description for your Security Group, and select the appropriate VPC. Click “Create” to proceed.
Step 2: Configure Inbound and Outbound Rules
After creating the Security Group, you will be taken to the “Inbound Rules” tab. Here, you can configure rules that control inbound traffic. Click the “Edit Rules” button, and then click the “Add Rule” button to create a new rule. Specify the protocol and port range, and choose the source for the rule. For outbound rules, specify the destination and follow the same process.
Remember that Security Groups are stateful, so you only need to create rules for inbound traffic. The Security Group will automatically permit responses to allowed requests without explicitly configuring rules for those responses.
Step 3: Associate the Security Group with an EC2 Instance or ENI
Once you have configured the rules, you can associate the Security Group with an EC2 instance or ENI. Navigate to the EC2 instance or ENI you want to associate with the Security Group, and select the Security Group from the list. Click “Save” to apply the changes.
By following these steps, you can effectively configure Security Groups in AWS to enhance your network security. Remember to periodically review and update your Security Group rules to ensure they continue to meet your security requirements.
Visuals can greatly enhance the understanding of configuring Security Groups in AWS. Consider adding screenshots or diagrams to illustrate each step of the process.
Strategies for Integrating NACLs and Security Groups in AWS
Integrating Network Access Control Lists (NACLs) and Security Groups in AWS is crucial for optimizing network security. By understanding the strengths of both components, you can create a robust, multi-layered security strategy. This section discusses best practices for integrating NACLs and Security Groups in AWS.
1. Leverage the strengths of both NACLs and Security Groups
NACLs and Security Groups serve different purposes and have unique strengths. NACLs are stateless, allowing you to control traffic at the subnet level, while Security Groups are stateful, maintaining context between requests. Utilize both components to create a comprehensive security strategy that covers inbound and outbound traffic at the subnet and instance levels.
2. Implement a deny-all NACL as a last line of defense
Create a deny-all NACL rule as the last rule in your NACL to block any unauthorized traffic. This rule will act as a safety net, ensuring that no unwanted traffic reaches your resources.
3. Use Security Groups for fine-grained control
Security Groups offer more granular control over traffic than NACLs. Use Security Groups to define specific inbound and outbound rules for your EC2 instances or ENIs, based on your application’s requirements.
4. Regularly review and update rules
Periodically review and update your NACL and Security Group rules to ensure they continue to meet your security requirements. Remove any unnecessary rules and add new ones as needed.
5. Implement least privilege access
Adhere to the principle of least privilege access when configuring NACLs and Security Groups. Only allow the minimum necessary traffic to reduce the attack surface of your AWS resources.
By following these best practices, you can effectively integrate NACLs and Security Groups in AWS to optimize network security. Remember that network security is an ongoing process, and regularly reviewing and updating your security strategy is essential to maintaining a secure environment.
Real-World Scenarios: NACLs vs. Security Groups
Choosing between Network Access Control Lists (NACLs) and Security Groups in AWS depends on specific network security requirements. This section presents real-world scenarios where NACLs or Security Groups would be more appropriate, demonstrating how to choose the right solution based on the use case.
Scenario 1: Subnet-level traffic control
Use NACLs when you need to control traffic at the subnet level. For example, if you have a DMZ subnet that requires strict inbound and outbound traffic control, NACLs can help you enforce security rules at the subnet boundary.
Scenario 2: Instance-level traffic control
Security Groups are more suitable when you need to control traffic at the instance level. For instance, if you have a multi-tier web application with separate front-end, back-end, and database tiers, Security Groups can help you define fine-grained rules for each tier, ensuring secure communication between instances.
Scenario 3: Stateless vs. stateful inspection
If your use case requires stateless inspection, NACLs are the better choice. For example, if you need to block incoming traffic from specific IP addresses without considering the response traffic, NACLs can handle this more efficiently. However, if your use case requires stateful inspection, Security Groups are more appropriate, as they maintain context between requests and responses.
Scenario 4: Dynamic environment
In a dynamic environment where instances frequently spin up and down, Security Groups are a better fit. Since Security Groups are associated with instances or ENIs, they can automatically adapt to changes in the environment. NACLs, on the other hand, are tied to subnets and require manual updates when the network topology changes.
By understanding these real-world scenarios, you can make informed decisions when designing network security for your AWS workloads. Remember that NACLs and Security Groups serve different purposes and should be used together to create a robust, multi-layered security strategy.
Monitoring and Troubleshooting NACLs and Security Groups in AWS
Monitoring and troubleshooting Network Access Control Lists (NACLs) and Security Groups in AWS is essential for maintaining optimal network security. This section explains how to use AWS tools such as VPC Flow Logs and CloudWatch to monitor and troubleshoot NACLs and Security Groups.
Using VPC Flow Logs
VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in your VPC. By creating and configuring Flow Logs, you can monitor and troubleshoot traffic patterns, ensuring that your NACLs and Security Groups are working as intended.
To create a Flow Log, navigate to the VPC dashboard in the AWS Management Console, select your VPC, and then click the “Create Flow Log” button. Choose the network interface you want to monitor, specify the log group and retention settings, and then click “Create.” The Flow Logs will start capturing traffic data, which you can analyze using CloudWatch or other third-party tools.
Using CloudWatch
CloudWatch is a monitoring and observability service that provides real-time insights into your AWS resources and applications. You can use CloudWatch to monitor NACLs and Security Groups by analyzing Flow Logs data or setting up alarms and notifications based on specific metrics.
To create a CloudWatch alarm for a NACL or Security Group, navigate to the CloudWatch dashboard, click “Alarms,” and then click “Create Alarm.” Choose the metric you want to monitor, such as “Rejected traffic” or “Denied traffic,” set the threshold and alarm conditions, and then configure the actions to be taken when the alarm state is triggered. This will help you proactively identify and resolve issues related to your NACLs and Security Groups.
By leveraging VPC Flow Logs and CloudWatch, you can effectively monitor and troubleshoot NACLs and Security Groups in AWS. Regularly reviewing and analyzing traffic patterns and alarm data will help you maintain optimal network security and quickly address any potential issues.