Keys: The Foundation of Encryption
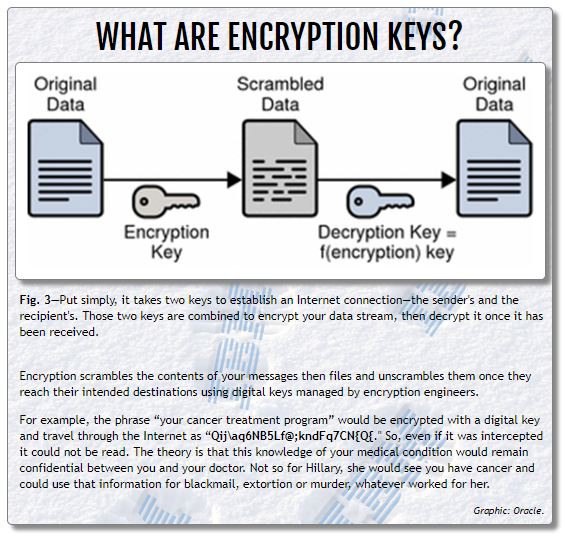
Keys are the backbone of encryption, serving as mathematical tools that scramble and unscramble data. They play a crucial role in maintaining data confidentiality and integrity, ensuring that sensitive information remains secure during transmission. In the context of encryption, keys are often interchangeable with the term ‘secrets,’ emphasizing the need to safeguard these sensitive pieces of information.
Keys come in various forms, with symmetric and asymmetric keys being the most common. Symmetric keys, also known as secret keys, use the same key for both encryption and decryption processes. This simplicity makes symmetric keys efficient but also poses a challenge in securely exchanging keys between communicating parties. On the other hand, asymmetric keys, also known as public keys, use different keys for encryption and decryption. These keys are inherently more secure in key exchange but are computationally intensive, making them less efficient than symmetric keys.
Understanding the differences between symmetric and asymmetric keys is essential for implementing robust encryption strategies. By utilizing the appropriate key type, organizations and individuals can ensure the secure transmission and storage of sensitive data, ultimately contributing to a safer digital landscape.
Secrets: Protecting Sensitive Information
Secrets, often interchangeable with keys, are sensitive pieces of information that must be safeguarded to ensure data confidentiality. They are used in encryption and decryption processes, making their protection vital for maintaining the security of digital assets. In many ways, secrets form the backbone of encryption, much like keys, and play a crucial role in secure data transmission.
The terms ‘keys’ and ‘secrets’ are sometimes used interchangeably, but they can have slightly different connotations depending on the context. In general, a secret refers to any sensitive information that must be protected, while a key is a specific type of secret used in encryption and decryption processes. However, the distinction between the two terms is not always clear-cut, and they are often used synonymously in the field of digital security.
To ensure the secure handling of secrets and keys, it is essential to implement robust security measures. This includes secure storage, access control, and regular rotation of secrets and keys. By adhering to best practices in secret and key management, organizations and individuals can significantly reduce the risk of unauthorized access to sensitive data, thereby strengthening their overall digital security posture.
Certificates: Verifying Identities in Digital World
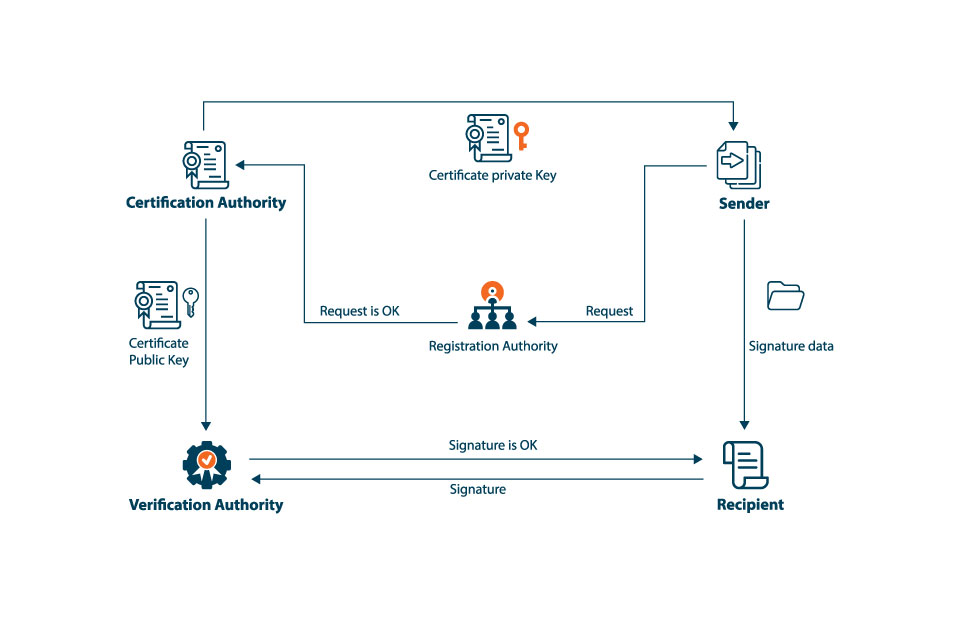
Certificates, also known as digital certificates, are electronic documents that authenticate the identity of entities in digital communications. They play a crucial role in establishing trust between parties and ensuring secure data transmission. In essence, certificates serve as digital passports, providing a means to verify the identity of users, devices, and services in the vast digital landscape.
Digital certificates typically contain various pieces of information, such as the certificate holder’s name, public key, expiration date, and the digital signature of a trusted third party, known as a certificate authority (CA). CAs are responsible for issuing, revoking, and managing digital certificates, thereby ensuring their integrity and trustworthiness.
Certificates are integral to many digital security protocols, such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL), which are commonly used to secure web communications. By utilizing digital certificates, organizations and individuals can protect their sensitive data from eavesdropping, tampering, and impersonation, thereby maintaining the confidentiality, integrity, and authenticity of their digital interactions.
Symmetric Keys vs. Asymmetric Keys: A Crucial Distinction
Symmetric keys and asymmetric keys are two primary categories of keys, each with unique characteristics and applications. Symmetric keys, also known as secret keys, use the same key for encryption and decryption processes. This simplicity makes symmetric keys efficient but poses a challenge in securely exchanging keys between communicating parties. Common symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
Asymmetric keys, also known as public keys, use different keys for encryption and decryption. These keys are inherently more secure in key exchange but are computationally intensive, making them less efficient than symmetric keys. Asymmetric key algorithms include Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC). Asymmetric keys are commonly used in public key infrastructure (PKI) and are essential for secure communication protocols, such as Transport Layer Security (TLS) and Secure Shell (SSH).
Understanding the differences between symmetric and asymmetric keys is crucial for implementing robust encryption strategies. By utilizing the appropriate key type, organizations and individuals can ensure the secure transmission and storage of sensitive data, ultimately contributing to a safer digital landscape.
How to Manage Secrets and Keys Securely
Effective secret and key management is paramount for maintaining digital security. Implementing best practices in this area can significantly reduce the risk of unauthorized access to sensitive data and ensure the integrity of encryption strategies. Here are some key aspects of secure secret and key management:
Storage
Secure storage of secrets and keys is crucial. Use hardware security modules (HSMs) or dedicated key management services (KMS) to store and manage encryption keys. These solutions provide a high level of security and ensure that encryption keys are not accessible to unauthorized users.
Access Control
Implement strict access control policies to ensure that only authorized users have access to encryption keys and secrets. Use role-based access control (RBAC) or attribute-based access control (ABAC) to define permissions and restrict access to sensitive information.
Rotation
Regularly rotate encryption keys and secrets to minimize the risk of unauthorized access. Schedule automatic key rotation using KMS or HSM solutions and ensure that old keys are securely destroyed.
Backup and Recovery
Maintain secure backups of encryption keys and secrets to ensure data availability in case of system failures or disasters. Implement redundancy and ensure that backup copies are stored in secure locations, such as offline storage devices or separate data centers.
Monitoring and Auditing
Monitor and audit secret and key usage to detect any suspicious activities or unauthorized access attempts. Use log analysis tools and intrusion detection systems (IDS) to track key usage and identify potential security threats.
The Role of Certificate Authorities in Digital Certificates
Certificate authorities (CAs) are trusted third-party organizations that play a crucial role in issuing, revoking, and managing digital certificates. By establishing and maintaining a chain of trust, CAs help ensure secure data transmission and verify the identity of entities in digital communications.
Issuing Digital Certificates
CAs issue digital certificates to entities, such as users, devices, and websites, after validating their identity. The certificate contains the entity’s public key and is digitally signed by the CA, providing a means to verify the certificate’s authenticity.
Revoking Digital Certificates
CAs can revoke digital certificates when they are compromised, expired, or no longer needed. Revocation ensures that compromised certificates are no longer trusted, preventing potential security threats.
Certificate Transparency
Certificate transparency is a mechanism that increases the visibility and accountability of the certificate issuance process. By maintaining publicly accessible logs of all issued certificates, certificate transparency enables monitoring and auditing of CA activities, thereby enhancing the overall security and trust of the digital certificate system.
Certificate Authority Best Practices
To maintain the integrity and trustworthiness of the digital certificate system, CAs must adhere to strict security best practices. These include secure certificate issuance, strong cryptographic algorithms, regular security audits, and incident response plans.
Practical Applications: Keys, Secrets, and Certificates in Real Life
The concepts of keys, secrets, and certificates are integral to various real-life applications, ensuring secure data transmission and protecting sensitive information in everyday digital interactions.
Secure Email Communication
Email communication is a common application where encryption keys and certificates are used to secure data in transit. Secure email protocols, such as S/MIME and PGP, rely on encryption keys and digital certificates to provide end-to-end encryption, ensuring that only the intended recipients can access the email content.
E-Commerce Transactions
E-commerce platforms use encryption keys and digital certificates to secure sensitive customer information, such as credit card details, during online transactions. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, which rely on digital certificates, encrypt data in transit, protecting it from eavesdropping and tampering.
Virtual Private Networks (VPNs)
VPNs use encryption keys and certificates to establish secure connections between remote devices and private networks. By encrypting data in transit, VPNs ensure that sensitive information, such as corporate data, remains confidential and secure, even when accessed from unsecured public networks.
Secure File Transfer
Secure file transfer protocols, such as SFTP and SCP, use encryption keys and digital certificates to protect sensitive files during transmission. By encrypting files and ensuring their integrity, these protocols prevent unauthorized access and data corruption during file transfer.
Code Signing
Code signing is the process of digitally signing software applications to ensure their authenticity and integrity. By using digital certificates, code signing verifies that the software has not been tampered with and comes from a trusted source, providing users with confidence in the software’s security and functionality.
Conclusion: The Interconnectedness of Keys, Secrets, and Certificates
While keys, secrets, and certificates serve distinct purposes in digital security, they are intricately connected, forming the foundation of secure digital communications. By understanding their differences and applications, individuals and organizations can better protect their digital assets and maintain secure communications.
Encryption keys, such as symmetric and asymmetric keys, are mathematical tools that scramble and unscramble data, ensuring data confidentiality and integrity. Secrets, often interchangeable with keys, are sensitive pieces of information that must be safeguarded to maintain data confidentiality. Digital certificates, or certificates, are electronic documents that verify the identity of entities in digital communications, establishing trust between parties and ensuring secure data transmission.
The secure management of encryption keys and secrets is paramount for maintaining digital security. Best practices for secret and key management include secure storage, access control, and regular rotation. Certificate authorities (CAs) play a crucial role in issuing, revoking, and managing digital certificates, ensuring the integrity and trustworthiness of the digital certificate system.
In real-life applications, keys, secrets, and certificates are integral to secure email communication, e-commerce transactions, virtual private networks (VPNs), and more. By understanding their roles and implementing robust security measures, individuals and organizations can better protect their digital assets and ensure secure communications in an increasingly connected world.