An Overview of Kubernetes Secrets: Definition and Key Concepts
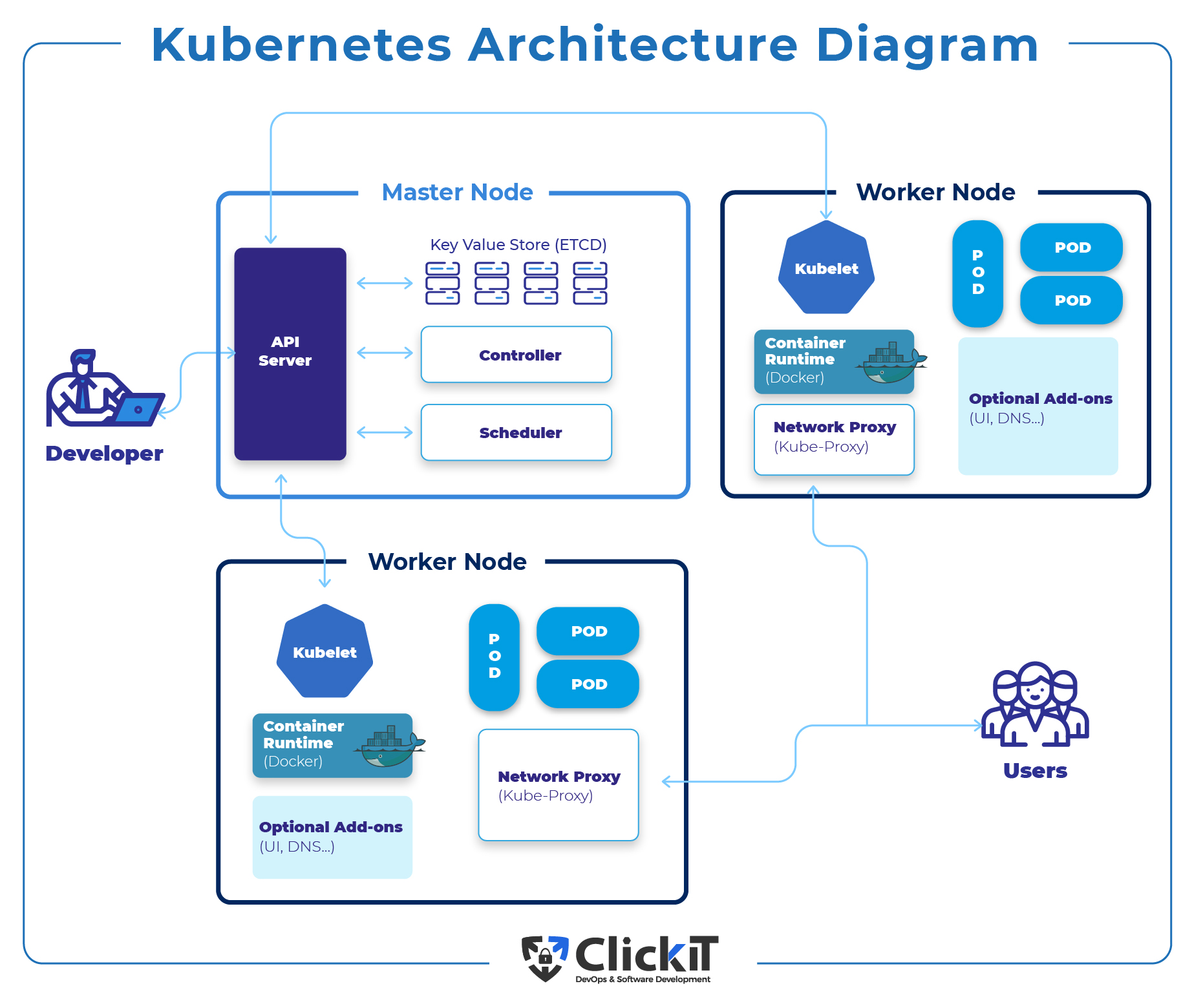
Kubernetes Secrets are objects that manage and store sensitive information, such as passwords, tokens, and SSH keys, ensuring clean and portable configuration files. These Secrets play a vital role in maintaining the security and integrity of your Kubernetes cluster. To create a Secret from a file, you can use the kubectl create secret command with the --from-file flag. This approach simplifies the process of managing sensitive data within your Kubernetes environment.
How to Create Secrets in Kubernetes using Files
To create a Secret in Kubernetes using a file, follow these steps:
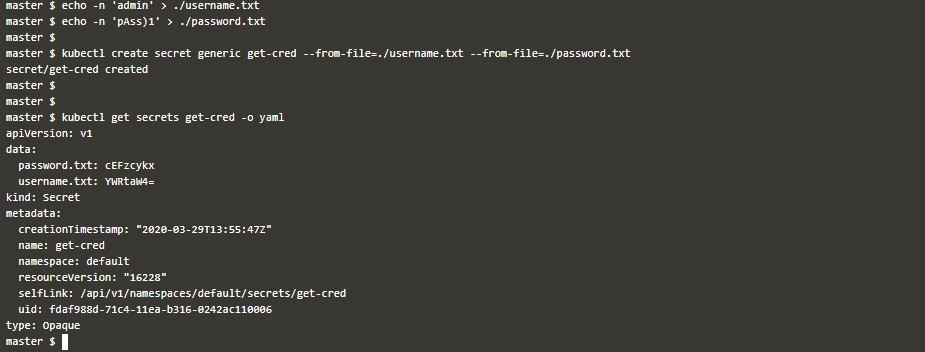
- First, ensure you have the necessary file containing the sensitive information you want to store as a Secret. For instance, you might have a
passwords.txtfile containing various passwords for different services. - Next, use the
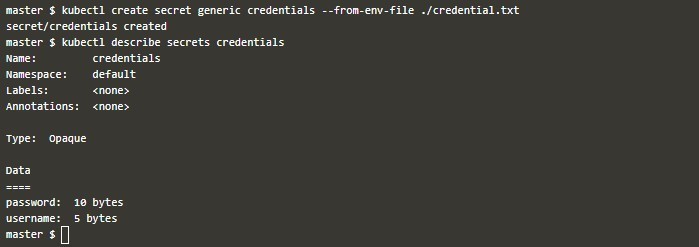
kubectl create secretcommand with the--from-fileflag to create a Secret from the file. The general format is as follows:kubectl create secret generic secret-name --from-file=path/to/fileFor example, if your
passwords.txtfile is located in the current directory, you can create a Secret namedmy-secretwith the following command:kubectl create secret generic my-secret --from-file=passwords.txt - After executing the command, Kubernetes will create a Secret named
my-secretwith the contents of thepasswords.txtfile. You can verify the Secret creation by running the following command:kubectl get secretsThis will display a list of all Secrets in your cluster, including the newly created
my-secret.
When creating Secrets from files, follow these best practices:
- Organize sensitive data in a logical and consistent manner, making it easier to manage and update.
- Limit the number of Secrets per namespace to maintain a clear overview of your sensitive data.
- Regularly review and update your Secrets to ensure they remain secure and relevant.
- Use role-based access control (RBAC) to restrict access to Secrets and protect sensitive information.
Alternatives to File-Based Secret Creation in Kubernetes
While the kubectl create secret command with the --from-file flag is a convenient method for creating Secrets in Kubernetes, alternative approaches can offer additional benefits and use cases. Here, we will explore two such methods: creating Secrets from literals and creating Secrets from encrypted data.
Creating Secrets from Literals
Instead of storing sensitive information in a file, you can create a Secret directly from a literal value using the kubectl create secret command with the --from-literal flag. This method is useful when you need to create a Secret containing a single value or when you want to avoid storing sensitive data in a file.
kubectl create secret generic secret-name --from-literal=key=value For example, to create a Secret named my-literal-secret with a key named password and the value s3cretP4ssw0rd, use the following command:
kubectl create secret generic my-literal-secret --from-literal=password=s3cretP4ssw0rd Creating Secrets from Encrypted Data
For enhanced security, you can create Secrets from encrypted data using tools like Sealed Secrets. This approach encrypts the Secret data on your local machine before sending it to the Kubernetes API server, ensuring that sensitive information is never transmitted in plaintext.
To create a Secret from encrypted data, follow these steps:
- Install the Sealed Secrets controller in your Kubernetes cluster.
- Create a Sealed Secret on your local machine using the
sealed-secretscommand-line tool:sealed-secrets convert --literal password=s3cretP4ssw0rd my-secret.yamlThis command generates an encrypted Sealed Secret that you can apply to your Kubernetes cluster:
kubectl apply -f my-secret- sealed.yaml
By using these alternatives to file-based Secret creation, you can tailor your Kubernetes Secret management strategy to better suit your specific use cases and security requirements.
Integrating Secrets into Your Kubernetes Deployments
Once you have created Secrets in Kubernetes, the next step is to integrate them into your applications, ensuring secure and efficient operations. This section provides practical tips and strategies for incorporating Secrets into your Kubernetes deployments.
Using Secrets as Environment Variables
One common method for integrating Secrets into your applications is by using them as environment variables. This approach allows you to inject sensitive data into your containers at runtime, without hardcoding the values in your application code or configuration files.
To use a Secret as an environment variable, first, create a Secret using the kubectl create secret command with the --from-file flag, as described in Context 2. Next, reference the Secret in your Kubernetes deployment configuration, specifying the environment variable name and the key from the Secret:
<!-- kubernetes-deployment.yaml --> apiVersion: apps/v1 kind: Deployment metadata: name: my-app spec: replicas: 1 selector: matchLabels: app: my-app template: metadata: labels: app: my-app spec: containers: - name: my-app image: my-app:latest env: - name: MY_SECRET_PASSWORD valueFrom: secretKeyRef: name: my-secret key: password Using Secrets as Volumes
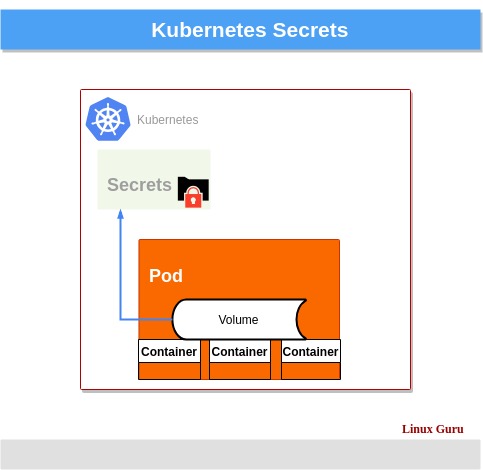
Another approach for integrating Secrets into your applications is by using them as volumes. This method enables you to mount the Secret as a file within your container’s filesystem, allowing your application to read the sensitive data directly from the file.
To use a Secret as a volume, first, create a Secret using the kubectl create secret command with the --from-file flag, as described in Context 2. Next, reference the Secret in your Kubernetes deployment configuration, specifying the volume name and the Secret name:
<!-- kubernetes-deployment.yaml --> apiVersion: apps/v1 kind: Deployment metadata: name: my-app spec: replicas: 1 selector: matchLabels: app: my-app template: metadata: labels: app: my-app spec: volumes: - name: my-secret-volume secret: secretName: my-secret containers: - name: my-app image: my-app:latest volumeMounts: - name: my-secret-volume mountPath: /etc/secrets By following these strategies, you can seamlessly integrate Secrets into your Kubernetes deployments, ensuring secure and efficient operations while maintaining the cleanliness and portability of your configuration files.
Best Practices for Managing Secrets in Kubernetes
Maintaining the security and integrity of your Kubernetes secrets is crucial for protecting sensitive data and ensuring the stability of your applications. This section outlines guidelines and recommendations for managing secrets in Kubernetes, covering aspects such as access control, rotation, and auditing.
Access Control
Implementing proper access control for your secrets is essential to prevent unauthorized access and maintain the security of your Kubernetes cluster. Use Kubernetes role-based access control (RBAC) or attribute-based access control (ABAC) to define and manage access policies for your secrets. Grant access only to the users and services that require it, and regularly review and update your access policies to ensure they remain up-to-date and aligned with your organization’s security requirements.
Rotation
Regularly rotating your secrets helps minimize the risk of unauthorized access and ensures that your secrets remain secure even if they are compromised. Implement a secret rotation strategy that includes automatic rotation using tools like Sealed Secrets or AWS K8s Secrets. Schedule regular audits to verify that your secrets are being rotated as planned and that no secrets have been overlooked.
Auditing
Auditing your secrets helps you track and monitor secret usage, identify potential security threats, and maintain compliance with your organization’s security policies. Implement a secret auditing strategy that includes logging and monitoring secret access and usage. Use tools like Audit Policy Manager or kube-audit to automate secret auditing and generate detailed audit logs.
Additional Best Practices
- Encrypt secrets at rest and in transit to protect sensitive data from unauthorized access.
- Limit the number of secrets stored in your cluster to reduce the attack surface and simplify management.
- Monitor your secrets for potential leaks or unauthorized access using tools like sops or sops-k8s.
- Educate your team members on best practices for managing secrets and maintaining security in Kubernetes.
By following these best practices, you can maintain the security and integrity of your Kubernetes secrets, ensuring that your sensitive data remains protected and your applications operate efficiently.
Troubleshooting Common Issues with Secret Management in Kubernetes
Creating, managing, and using secrets in Kubernetes can sometimes present challenges and pitfalls. This section offers practical solutions and workarounds to help users overcome common issues with secret management in Kubernetes.
Issue 1: Secrets Not Being Applied to Pods
If your secrets are not being applied to your pods, ensure that you have correctly referenced the secrets in your pod configuration. Double-check the secret name, namespace, and key to ensure they match the actual secret. Additionally, verify that the secret exists in the correct namespace and that there are no typos or errors in your configuration files.
Issue 2: Secrets Exposed in Kubernetes Dashboard
By default, the Kubernetes dashboard displays secrets in plaintext, which can pose a security risk. To mitigate this risk, configure the Kubernetes dashboard to hide secrets or use a third-party dashboard that supports secret masking. Alternatively, you can use role-based access control (RBAC) or attribute-based access control (ABAC) to limit access to the Kubernetes dashboard and other sensitive resources.
Issue 3: Secrets Not Being Rotated Regularly
If you are not rotating your secrets regularly, you risk exposing sensitive data to unauthorized users. Implement a secret rotation strategy that includes automatic rotation using tools like Sealed Secrets or AWS K8s Secrets. Schedule regular audits to verify that your secrets are being rotated as planned and that no secrets have been overlooked.
Issue 4: Secrets Leaked in Logs or Traces
Secrets that are accidentally logged or traced can expose sensitive data to unauthorized users. Implement a logging and tracing strategy that excludes secrets and other sensitive data. Use tools like kube-audit or Audit Policy Manager to monitor your logs and traces for potential leaks and unauthorized access.
Issue 5: Secrets Not Encrypted at Rest or in Transit
If your secrets are not encrypted at rest or in transit, they can be intercepted or accessed by unauthorized users. Implement encryption for your secrets using Kubernetes encryption at rest or in transit. Use tools like sops or sops-k8s to automate secret encryption and decryption.
By understanding and addressing these common issues, you can ensure that your Kubernetes secret management strategy is secure, efficient, and effective. Regularly review and update your secret management practices to maintain the highest level of security and integrity for your sensitive data.
Exploring Advanced Secret Management Techniques in Kubernetes
As you become more proficient in managing secrets in Kubernetes, you may want to explore advanced techniques to further enhance your Kubernetes security posture. This section delves into advanced secret management techniques, such as using external secret management systems or automating secret rotation.
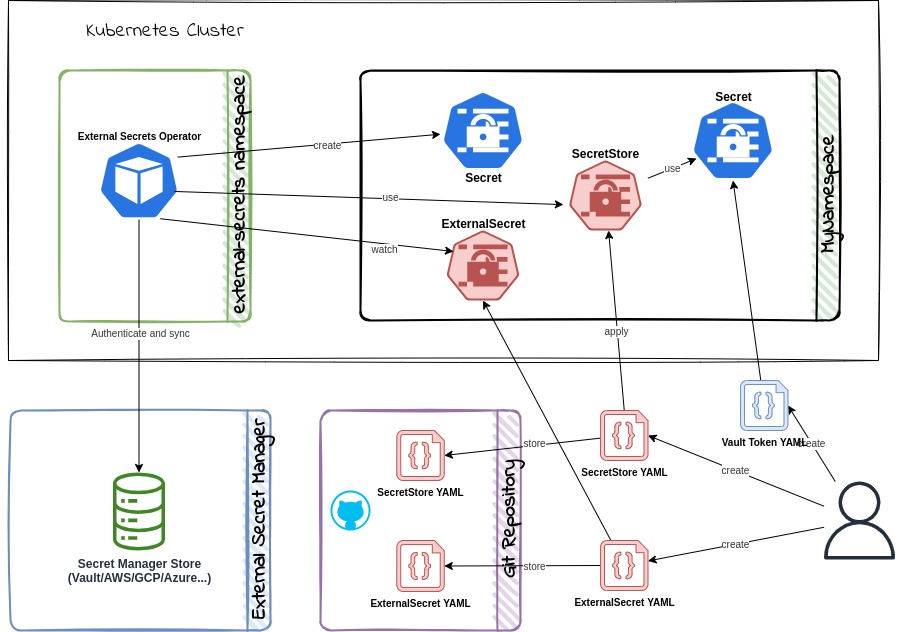
Using External Secret Management Systems
External secret management systems like Vault, HashiCorp Vault, or AWS Secrets Manager K8s Secrets Provider can help you manage secrets across multiple clusters and environments. These systems provide features like dynamic secret generation, secret rotation, and secret access control, enabling you to maintain a high level of security and integrity for your sensitive data.
Automating Secret Rotation
Automating secret rotation is essential for maintaining the security and integrity of your secrets. Tools like Sealed Secrets or AWS K8s Secrets can help you automate secret rotation, ensuring that your secrets are updated regularly and that your sensitive data remains protected.
Implementing a Multi-Layer Secret Management Strategy
Implementing a multi-layer secret management strategy can help you further enhance your Kubernetes security posture. This strategy involves using multiple layers of secret management, such as using Kubernetes secrets for managing application secrets, environment variables for managing infrastructure secrets, and external secret management systems for managing secrets across multiple clusters and environments.
Monitoring and Auditing Your Secrets
Monitoring and auditing your secrets is essential for maintaining the security and integrity of your sensitive data. Implement a monitoring and auditing strategy that includes logging and monitoring secret access and usage. Use tools like Audit Policy Manager or kube-audit to automate secret monitoring and generate detailed audit logs.
By exploring advanced secret management techniques, you can further enhance your Kubernetes security posture and ensure that your sensitive data remains protected and your applications operate efficiently. Regularly review and update your secret management practices to maintain the highest level of security and integrity for your sensitive data.
Continuous Learning: Enhancing Your Kubernetes Secret Management Skills
Staying up-to-date with the latest developments and best practices in Kubernetes secret management is essential for maintaining a secure and efficient Kubernetes environment. This section suggests resources and strategies for continuous learning and improvement.
Following Kubernetes Blogs and Newsletters
Following Kubernetes blogs and newsletters is an excellent way to stay informed about the latest developments and best practices in Kubernetes secret management. Some popular Kubernetes blogs and newsletters include the official Kubernetes blog, KubeDex, and K8s School.
Participating in Kubernetes Communities
Participating in Kubernetes communities is an excellent way to connect with other Kubernetes users, share knowledge, and learn from each other’s experiences. Some popular Kubernetes communities include the Kubernetes Slack community, the official Kubernetes community, and the Kubernetes Meetup groups.
Attending Kubernetes Conferences and Webinars
Attending Kubernetes conferences and webinars is an excellent way to learn about the latest developments and best practices in Kubernetes secret management. Some popular Kubernetes conferences and webinars include the KubeCon + CloudNativeCon, the Cloud Native Computing Foundation (CNCF) events, and the Red Hat virtual events.
Enrolling in Kubernetes Training Courses
Enrolling in Kubernetes training courses is an excellent way to gain in-depth knowledge and skills in Kubernetes secret management. Some popular Kubernetes training courses include the Kubernetes for the Absolute Beginner course by the Linux Foundation, the Microsoft Learn Kubernetes Fundamentals course by edX, and the Learn Kubernetes the Hard Way course by Udemy.
Practicing and Experimenting with Kubernetes Secrets
Practicing and experimenting with Kubernetes secrets is an excellent way to gain hands-on experience and improve your skills. Set up a test Kubernetes environment, create and manage secrets, and experiment with different secret management techniques. Use tools like Minikube or Kind to create a local Kubernetes environment for testing and experimentation.
By following these resources and strategies, you can enhance your Kubernetes secret management skills, stay up-to-date with the latest developments and best practices, and ensure that your sensitive data remains protected and your applications operate efficiently.