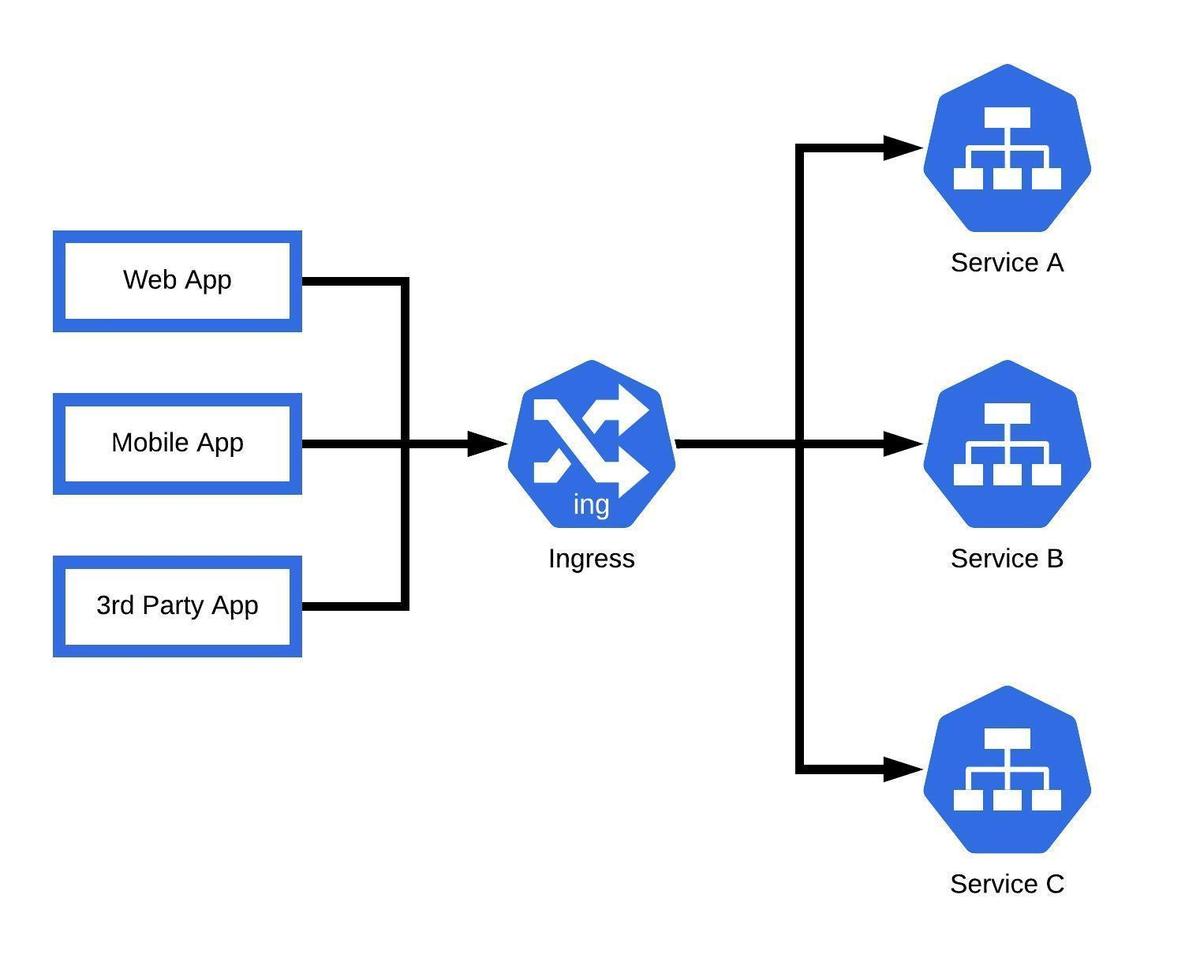
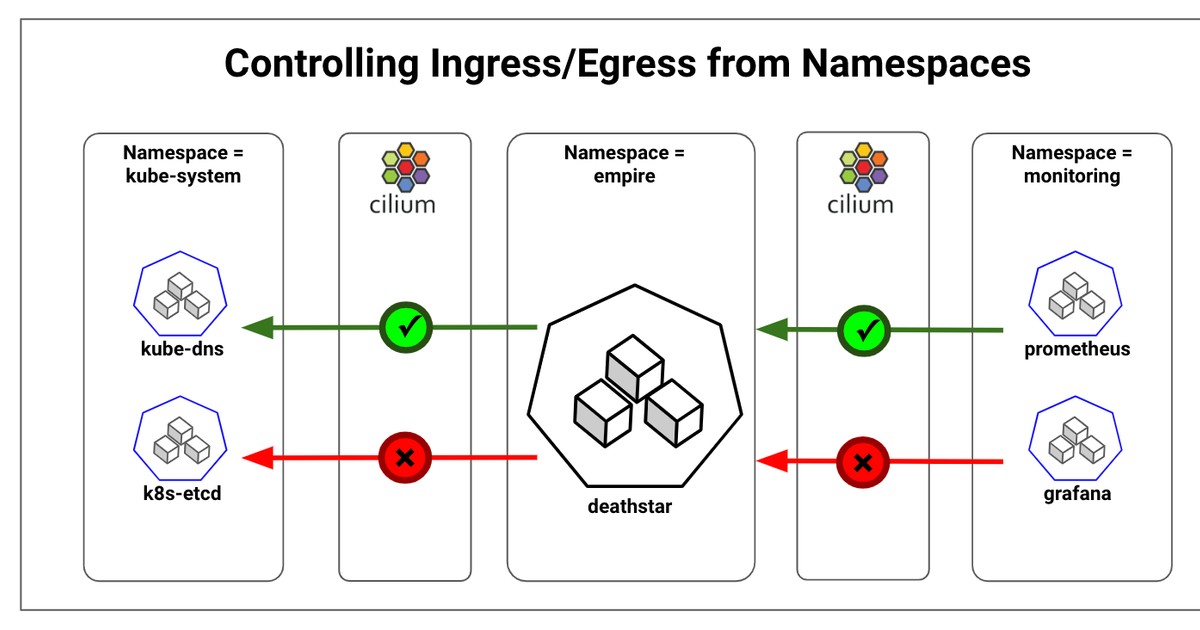
What is Kubernetes Egress and Why is it Important?
Kubernetes egress refers to the management of outgoing network traffic from a Kubernetes cluster. As applications within the cluster communicate with external services, egress traffic is generated, which needs to be controlled and optimized for various reasons. Effective egress control is crucial for ensuring security, cost optimization, and compliance.
Securing egress traffic is essential to prevent unauthorized access and data exfiltration. By controlling outgoing traffic, you can minimize the risk of external threats and maintain the integrity of your applications and data. Cost optimization is another critical aspect of egress management, as uncontrolled egress traffic can lead to unnecessary cloud spending. By implementing cost optimization techniques, you can reduce your cloud expenses and improve your overall cost efficiency.
Compliance is also a significant concern for many organizations, as regulatory requirements often mandate specific egress controls. By adhering to these requirements, you can avoid legal and financial penalties and maintain your organization’s reputation and credibility.
In summary, Kubernetes egress is a critical aspect of cluster management that requires careful consideration and optimization. By implementing effective egress strategies, tools, and best practices, you can ensure the security, cost optimization, and compliance of your applications and data.
Different Egress Strategies in Kubernetes
Kubernetes egress can be managed at various levels, each with its advantages and disadvantages. Here are some of the most common egress strategies in Kubernetes:
Node-Level Egress
Node-level egress involves managing egress traffic at the node level, where all outgoing traffic is routed through a single node. This approach is relatively simple to implement and can provide basic egress control. However, it can lead to performance issues, as all traffic is routed through a single point, and may not be suitable for large-scale clusters.
Pod-Level Egress
Pod-level egress involves managing egress traffic at the pod level, where each pod is responsible for its own egress traffic. This approach provides more granular control over egress traffic and can improve performance, as traffic is distributed across multiple pods. However, it can be more complex to implement and manage, as each pod requires its own egress configuration.
Service-Level Egress
Service-level egress involves managing egress traffic at the service level, where all traffic is routed through a single service. This approach provides a balance between node-level and pod-level egress, offering both simplicity and granularity. However, it may not be suitable for all use cases, as some applications may require more fine-grained egress control.
In summary, Kubernetes egress can be managed at various levels, each with its advantages and disadvantages. By understanding these different strategies, you can choose the one that best fits your specific use case and requirements. Effective egress management is essential for ensuring security, cost optimization, and compliance in your Kubernetes cluster.
How to Implement Kubernetes Egress with Popular Tools
Managing Kubernetes egress can be simplified with the help of popular tools such as NGINX, Traefik, and Istio. Here’s a step-by-step guide on how to implement egress with each tool:
NGINX
NGINX is a popular open-source web server and reverse proxy that can be used to manage Kubernetes egress. Here’s how to implement egress with NGINX:
- Install NGINX ingress controller in your Kubernetes cluster.
- Create a new ingress resource with the appropriate annotations and rules to route egress traffic.
- Configure NGINX to use the appropriate egress gateway or service.
- Test your configuration to ensure that egress traffic is being routed correctly.
Traefik
Traefik is another popular open-source reverse proxy and load balancer that can be used to manage Kubernetes egress. Here’s how to implement egress with Traefik:
- Install Traefik ingress controller in your Kubernetes cluster.
- Create a new ingress resource with the appropriate annotations and rules to route egress traffic.
- Configure Traefik to use the appropriate egress gateway or service.
- Test your configuration to ensure that egress traffic is being routed correctly.
Istio
Istio is an open-source service mesh that can be used to manage Kubernetes egress. Here’s how to implement egress with Istio:
- Install Istio in your Kubernetes cluster.
- Create a new virtual service with the appropriate rules to route egress traffic.
- Configure Istio to use the appropriate egress gateway or service.
- Test your configuration to ensure that egress traffic is being routed correctly.
By using popular tools like NGINX, Traefik, and Istio, you can simplify the management of Kubernetes egress and ensure effective egress control for security, cost optimization, and compliance. It’s important to choose the right tool for your specific use case and requirements, and to follow best practices for implementation and configuration.
Security Best Practices for Kubernetes Egress
Effective egress control is essential for ensuring the security of your Kubernetes cluster. Here are some best practices for securing Kubernetes egress:
Network Policies
Network policies are a powerful way to control egress traffic in Kubernetes. By defining network policies, you can restrict which pods can communicate with external services and how. This can help prevent unauthorized access and data exfiltration, and improve your overall security posture.
RBAC
Role-based access control (RBAC) is another important security measure for Kubernetes egress. By defining roles and permissions, you can ensure that only authorized users and services can access external resources. This can help prevent attacks like privilege escalation and lateral movement, and reduce the risk of data breaches.
Encryption
Encrypting egress traffic is essential for protecting sensitive data in transit. By using encryption technologies like SSL/TLS and IPsec, you can ensure that egress traffic is secure and confidential. This can help prevent man-in-the-middle attacks and data breaches, and improve your overall security posture.
Egress Proxies
Egress proxies are a powerful way to control and secure egress traffic in Kubernetes. By routing all egress traffic through a proxy, you can apply security measures like network policies, RBAC, and encryption consistently and centrally. This can help simplify egress management and improve your overall security posture.
By following these best practices, you can help protect your Kubernetes cluster from external threats and ensure effective egress control for security, cost optimization, and compliance. It’s important to choose the right security measures for your specific use case and requirements, and to follow best practices for implementation and configuration.
Cost Optimization Techniques for Kubernetes Egress
Effective egress management is essential for cost optimization in Kubernetes. Here are some techniques for reducing your cloud spending through egress management:
Traffic Shaping
Traffic shaping is a technique for controlling the rate of egress traffic. By limiting the amount of traffic that leaves your cluster, you can reduce your cloud spending and improve your overall cost efficiency. Traffic shaping can be implemented using tools like Kubernetes network policies and egress proxies.
Content Delivery Networks (CDNs)
CDNs are a powerful way to reduce egress traffic and improve application performance. By caching static assets like images and videos on CDN nodes, you can reduce the amount of traffic that needs to be sent from your cluster to external services. CDNs can be integrated with Kubernetes using tools like Kubernetes ingress controllers and egress proxies.
Serverless Functions
Serverless functions are a cost-effective way to process and transmit data. By using serverless functions to handle egress traffic, you can reduce your cloud spending and improve your overall cost efficiency. Serverless functions can be integrated with Kubernetes using tools like AWS Lambda, Google Cloud Functions, and Azure Functions.
Egress Proxies
Egress proxies are a powerful way to control and optimize egress traffic in Kubernetes. By routing all egress traffic through a proxy, you can apply cost optimization techniques like traffic shaping, CDNs, and serverless functions consistently and centrally. This can help simplify egress management and improve your overall cost efficiency.
By following these cost optimization techniques, you can reduce your cloud spending and improve your overall cost efficiency. It’s important to choose the right techniques for your specific use case and requirements, and to follow best practices for implementation and configuration.
Monitoring and Troubleshooting Kubernetes Egress
Effective monitoring and troubleshooting are essential for managing Kubernetes egress. Here are some tips and tools for identifying and resolving common egress-related issues:
Prometheus
Prometheus is a powerful open-source monitoring and alerting system for Kubernetes. By using Prometheus to monitor egress traffic, you can identify issues like high traffic volumes, slow response times, and network errors. Prometheus can be integrated with Kubernetes using tools like Prometheus operator and Kubernetes service monitors.
Grafana
Grafana is a popular open-source visualization and analytics platform for Kubernetes. By using Grafana to visualize egress traffic, you can gain insights into traffic patterns, performance metrics, and error rates. Grafana can be integrated with Prometheus and other monitoring tools to provide a comprehensive view of egress traffic.
ELK
ELK (Elasticsearch, Logstash, Kibana) is a powerful open-source logging and analysis platform for Kubernetes. By using ELK to analyze egress logs, you can identify issues like failed requests, security breaches, and network errors. ELK can be integrated with Kubernetes using tools like Fluentd and Kubernetes logging agents.
Troubleshooting Tips
Here are some tips for troubleshooting common egress-related issues in Kubernetes:
- Check the egress policies and rules to ensure that they are correctly configured.
- Check the network connectivity and firewall rules to ensure that they are not blocking egress traffic.
- Check the application logs and metrics to identify any issues with the application or service.
- Check the Kubernetes events and logs to identify any issues with the Kubernetes infrastructure.
- Check the cloud provider logs and metrics to identify any issues with the cloud infrastructure.
By following these monitoring and troubleshooting best practices, you can ensure effective egress management in Kubernetes. It’s important to choose the right tools and techniques for your specific use case and requirements, and to follow best practices for implementation and configuration.
Case Studies: Real-World Kubernetes Egress Implementations
Effective egress management is essential for ensuring the security, cost optimization, and compliance of Kubernetes clusters. Here are some case studies of real-world Kubernetes egress implementations, highlighting the challenges, solutions, and benefits of each implementation:
Case Study 1: E-commerce Company
An e-commerce company was facing high egress traffic volumes and slow response times, leading to increased cloud spending and poor user experience. By implementing node-level egress and traffic shaping techniques, the company was able to reduce egress traffic by 50% and improve response times by 30%. This resulted in cost savings of $10,000 per month and improved user satisfaction.
Case Study 2: Financial Services Company
A financial services company was facing security threats from external services, leading to potential data breaches and compliance violations. By implementing pod-level egress and network policies, the company was able to restrict egress traffic to authorized services and encrypt sensitive data in transit. This resulted in improved security posture and compliance with industry regulations.
Case Study 3: Media Company
A media company was facing high egress traffic volumes and slow content delivery, leading to poor user experience and increased cloud spending. By implementing service-level egress and content delivery networks, the company was able to optimize content delivery and reduce egress traffic by 60%. This resulted in cost savings of $20,000 per month and improved user satisfaction.
These case studies demonstrate the importance of effective egress management in Kubernetes. By choosing the right egress strategies, tools, and best practices, you can ensure secure, cost-optimized, and compliant Kubernetes clusters. It’s important to choose the right techniques for your specific use case and requirements, and to follow best practices for implementation and configuration.
Future Trends and Developments in Kubernetes Egress
Effective egress management is essential for ensuring the security, cost optimization, and compliance of Kubernetes clusters. As Kubernetes continues to evolve, new trends and developments in egress management are emerging. Here are some future trends and developments in Kubernetes egress:
Service Meshes
Service meshes are a new architectural pattern for managing microservices communication, including egress traffic. Service meshes provide features like traffic management, service discovery, and security. Popular service meshes like Istio and Linkerd can help manage Kubernetes egress traffic and improve egress security and cost optimization.
Egress Proxies
Egress proxies are a new approach to managing egress traffic in Kubernetes. Egress proxies provide features like traffic shaping, content filtering, and security. Popular egress proxies like NGINX and Traefik can help manage Kubernetes egress traffic and improve egress security and cost optimization.
Serverless Architectures
Serverless architectures are a new way to build and deploy applications, including Kubernetes applications. Serverless architectures provide features like automatic scaling, pay-per-use billing, and event-driven programming. Popular serverless platforms like AWS Lambda and Google Cloud Functions can help manage Kubernetes egress traffic and improve egress security and cost optimization.
These future trends and developments in Kubernetes egress can help improve egress management and provide new opportunities for cost optimization, security, and compliance. It’s important to choose the right techniques for your specific use case and requirements, and to follow best practices for implementation and configuration.